数据包捕获是一个重要组件,可以实施网络入侵检测系统 (IDS) 并执行网络安全监视。 多种开源 IDS 工具可以处理数据包捕获,并检查潜在网络入侵和恶意活动的签名。 使用 Azure 网络观察程序提供的数据包捕获,可以分析网络中是否存在有害入侵或漏洞。
Suricata 就是这样的一种开源工具,它是一个 IDS 引擎,可使用规则集来监视网络流量,每当出现可疑事件时,它会触发警报。 Suricata 提供多线程引擎,以更高的速度和效率执行网络流量分析。 有关 Suricata 及其功能的详细信息,请转到 Suricata 网站。
场景
本文介绍如何将环境设置为使用网络观察程序、Suricata 和 Elastic Stack 执行网络入侵检测。
网络观察程序提供用于执行网络入侵检测的数据包捕获。 Suricata 处理数据包捕获,并根据与其威胁规则集匹配的数据包触发警报。 Suricata 将这些警报存储在本地计算机上的日志文件中。
通过使用 Elastic Stack,可以为 Suricata 生成的日志编制索引,然后使用它们创建 Kibana 仪表板。 仪表板提供了日志的可视化表示,并提供了一种快速了解潜在网络漏洞的方法。
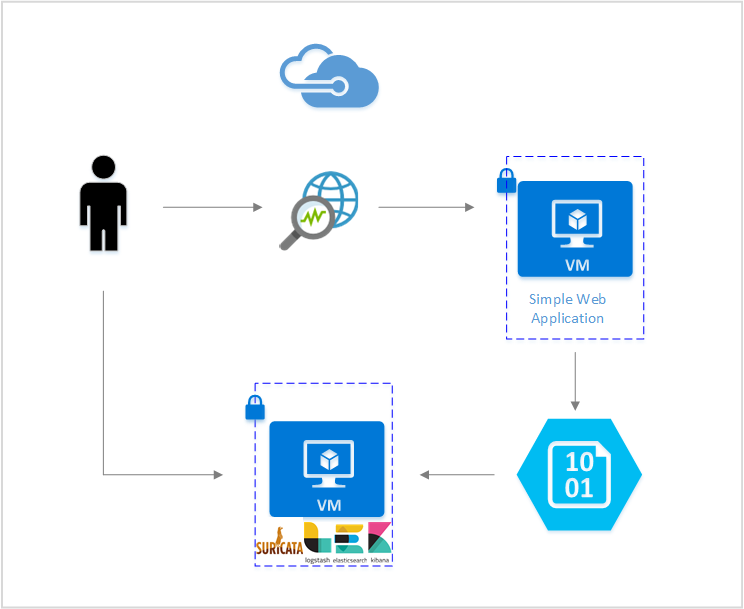
可以在 Azure 虚拟机 (VM) 上设置这两种开源工具,这样就可以在自己的 Azure 网络环境中执行此分析。
安装 Suricata
在 VM 的命令行终端中运行以下命令:
sudo add-apt-repository ppa:oisf/suricata-stable sudo apt-get update sudo apt-get install suricata若要验证安装,请运行命令
suricata -h查看命令的完整列表。
有关其他安装方法,请参阅 Suricata 安装快速入门指南。
下载 Emerging Threats 规则集
在这个阶段,你没有任何运行 Suricata 的规则。 如果要检测对网络的特定威胁,可以创建你自己的规则。 还可以使用各种提供商的已开发规则集,如 Snort 的 Emerging Threats 或 Talos 规则。 在本文中,你将使用免费提供的 Emerging Threats 规则集。
下载该规则集,并将其复制到目录:
wget https://rules.emergingthreats.net/open/suricata/emerging.rules.tar.gz
tar zxf emerging.rules.tar.gz
sudo cp -r rules /etc/suricata/
使用 Suricata 处理数据包捕获
若要使用 Suricata 处理数据包捕获,请运行以下命令:
sudo suricata -c /etc/suricata/suricata.yaml -r <location_of_pcapfile>
若要检查生成的警报,请阅读 fast.log 文件:
tail -f /var/log/suricata/fast.log
设置 Elastic Stack
虽然 Suricata 生成的日志包含有关网络情况的重要信息,但这些日志文件并不是很容易阅读和理解。 通过将 Suricata 与 Elastic Stack 相连接,可以创建一个 Kibana 仪表板,以搜索、绘制图表、分析日志并从中获得见解。
安装 Elasticsearch
Elastic Stack 版本 5.0 及更高版本需要 Java 8。 运行命令
java -version可以检查版本。 如果尚未安装 Java,请参阅有关支持 Azure 的 Java 开发工具包的文档。下载适用于系统的正确二进制程序包:
curl -L -O https://artifacts.elastic.co/downloads/elasticsearch/elasticsearch-5.2.0.deb sudo dpkg -i elasticsearch-5.2.0.deb sudo /etc/init.d/elasticsearch start可以在用于安装 Elasticsearch 的 Elastic 网页上找到其他安装方法。
使用以下命令验证 Elasticsearch 是否正在运行:
curl http://127.0.0.1:9200应获得类似于以下示例的响应:
{ "name" : "Angela Del Toro", "cluster_name" : "elasticsearch", "version" : { "number" : "5.2.0", "build_hash" : "8ff36d139e16f8720f2947ef62c8167a888992fe", "build_timestamp" : "2016-01-27T13:32:39Z", "build_snapshot" : false, "lucene_version" : "6.1.0" }, "tagline" : "You Know, for Search" }
有关安装 Elasticsearch 的更多说明,请参阅有关安装的 Elastic 网页。
安装 Logstash
运行以下命令安装 Logstash:
curl -L -O https://artifacts.elastic.co/downloads/logstash/logstash-5.2.0.deb sudo dpkg -i logstash-5.2.0.deb将 Logstash 配置为从 eve.json 文件的输出中读取。 使用以下命令创建 logstash.conf 文件:
sudo touch /etc/logstash/conf.d/logstash.conf将以下内容添加到该文件。 确保 eve.json 文件的路径正确。
input { file { path => ["/var/log/suricata/eve.json"] codec => "json" type => "SuricataIDPS" } } filter { if [type] == "SuricataIDPS" { date { match => [ "timestamp", "ISO8601" ] } ruby { code => " if event.get('[event_type]') == 'fileinfo' event.set('[fileinfo][type]', event.get('[fileinfo][magic]').to_s.split(',')[0]) end " } ruby{ code => " if event.get('[event_type]') == 'alert' sp = event.get('[alert][signature]').to_s.split(' group ') if (sp.length == 2) and /\A\d+\z/.match(sp[1]) event.set('[alert][signature]', sp[0]) end end " } } if [src_ip] { geoip { source => "src_ip" target => "geoip" #database => "/opt/logstash/vendor/geoip/GeoLiteCity.dat" add_field => [ "[geoip][coordinates]", "%{[geoip][longitude]}" ] add_field => [ "[geoip][coordinates]", "%{[geoip][latitude]}" ] } mutate { convert => [ "[geoip][coordinates]", "float" ] } if ![geoip.ip] { if [dest_ip] { geoip { source => "dest_ip" target => "geoip" #database => "/opt/logstash/vendor/geoip/GeoLiteCity.dat" add_field => [ "[geoip][coordinates]", "%{[geoip][longitude]}" ] add_field => [ "[geoip][coordinates]", "%{[geoip][latitude]}" ] } mutate { convert => [ "[geoip][coordinates]", "float" ] } } } } } output { elasticsearch { hosts => "localhost" } }提供对 eve.json 文件的适当权限,使 Logstash 能够引入文件:
sudo chmod 775 /var/log/suricata/eve.json通过运行以下命令启动 Logstash:
sudo /etc/init.d/logstash start
有关安装 Logstash 的更多说明,请参阅 Elastic 正式文档。
安装 Kibana
运行以下命令以安装 Kibana:
curl -L -O https://artifacts.elastic.co/downloads/kibana/kibana-5.2.0-linux-x86_64.tar.gz tar xzvf kibana-5.2.0-linux-x86_64.tar.gz使用以下命令运行 Kibana:
cd kibana-5.2.0-linux-x86_64/ ./bin/kibana转到
http://localhost:5601查看 Kibana Web 界面。对于本方案,用于 Suricata 日志的索引模式为
logstash-*。如果要远程查看 Kibana 仪表板,请创建允许访问端口 5601 的入站网络安全组 (NSG) 规则。
创建 Kibana 仪表板
本文提供了一个示例仪表板,用于查看警报中的趋势和详细信息。 使用方式:
在 Kibana 的“Management”(管理)选项卡上,转到“Saved Objects”(已保存的对象)并导入所有三个文件。 然后,在“仪表板”选项卡上打开并加载示例仪表板。
还可以创建自己的可视化效果,以及根据感兴趣的指标定制的仪表板。 阅读 Kibana 的正式文档,详细了解如何创建 Kibana 可视化效果。
可视化 IDS 警报日志
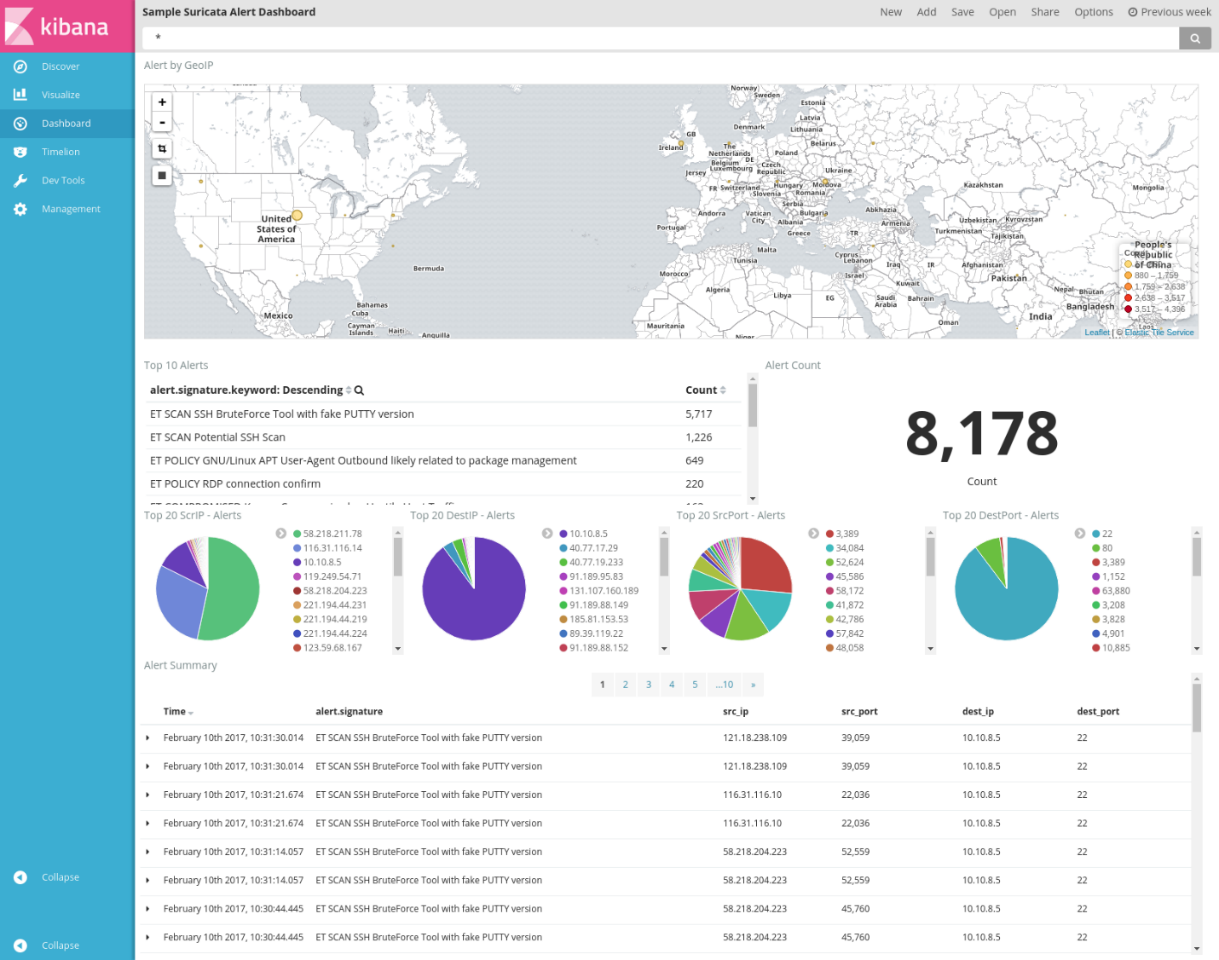
示例仪表板提供了 Suricata 警报日志的多种可视化效果:
按 GeoIP 划分的警报:基于地理位置,按来源国家/地区(由 IP 确定)显示警报分布的地图。
排名靠前的 10 条警报:最常触发的 10 条警报的摘要及其说明。 选择单个警报可以筛选仪表板中的内容,以只显示与该特定警报相关的信息。
警报数:规则集触发的警报总数。
前 20 个 ScrIP - 警报,前 20 个 DestIP - 警报,前 20 个 SrcPort - 警报,前 20 个 DestPort - 警报:饼图,显示触发警报的前 20 个 IP 和端口的源和目标。 可以筛选特定的 IP 或端口,以查看触发了多少以及哪些类型的警报。
警报摘要:汇总每个警报的特定详细信息的表。 可以自定义此表,以显示每条警报的其他想要了解的参数。
有关创建自定义可视化效果和仪表板的更多信息,请参阅 Kibana 的正式文档。
结束语
通过将网络观察程序提供的数据包捕获与 Suricata 等开源 IDS 工具相结合,可以针对各种威胁执行网络入侵检测。
仪表板可帮助你快速发现网络中的趋势和异常。 还可以使用仪表板来检查数据,以发现警报的根本原因,例如恶意用户代理或易受攻击的端口。 有了这些提取的数据,可以针对以下方面做出明智的决定:
- 对有害的入侵企图做出反应并保护网络。
- 创建规则,防止未来的网络入侵。
下一步
了解如何基于警报触发数据包捕获: