重要
网络安全组(NSG)流日志将于 2027 年 9 月 30 日停用。 2025 年 6 月 30 日之后,将无法再创建新的 NSG 流日志。 建议迁移到虚拟网络流日志,这些日志解决了 NSG 流日志的限制。 退休日期后,将不再支持 NSG 流日志中启用的流量分析功能,订阅中的现有 NSG 流日志资源也将被删除。 但是,不会从 Azure 存储中删除现有的 NSG 流日志记录,并且将继续遵循其配置的保留策略。 有关详细信息,请查看官方公告。
网络安全组 (NSG) 流日志记录是 Azure 网络观察程序的一项功能,可用于记录有关流经网络安全组的 IP 流量的信息。 流数据发送到 Azure 存储,你可以从那里访问它并将它导出到所选择的任何可视化工具、安全信息和事件管理 (SIEM) 解决方案或入侵检测系统 (IDS)。
为何使用流日志?
监视、管理和了解你自己的网络至关重要,这样你就可以保护和优化网络。 你需要知道网络的当前状态、正在连接的人员以及用户从何处进行连接。 你还需要知道哪些端口对 Internet 开放、预期网络行为、哪些网络行为异常,以及流量何时突然上升。
流日志是云环境中所有网络活动的事实来源。 无论是尝试优化资源的初创公司,还是尝试检测入侵的大型企业,流日志都可以提供帮助。 可以使用它们来优化网络流、监视吞吐量、验证合规性、检测入侵等等。
常见用例
网络监视
- 标识未知或不需要的流量。
- 监视流量水平和带宽消耗。
- 按 IP 和端口筛选流日志,以了解应用程序的行为。
- 将流日志导出到所选的分析和可视化工具,以设置监视仪表板。
使用情况监视和优化
- 标识网络中最活跃的通信方。
- 结合 GeoIP 数据来识别跨区域流量。
- 了解流量增长情况以进行容量预测。
- 使用数据删除过度严格的流量规则。
合规性
- 使用流数据来验证网络隔离和企业访问规则的合规性。
网络取证和安全分析
- 分析来自已遭入侵的 IP 和网络接口的网络流。
- 将流日志导出到所选的任何 SIEM 或 IDS 工具。
NSG 流日志的工作原理
NSG 流日志的重要属性包括:
- 流日志在开放式系统互连 (OSI) 模型的第 4 层运行,将记录传入和传出网络安全组的所有 IP 流。
- 日志每隔 1 分钟通过 Azure 平台收集一次。 它们不会对 Azure 资源或网络性能造成任何形式的影响。
- 日志以 JSON 格式写入,显示每个网络安全组规则的出站和入站流量。
- 每条日志记录包含流应用到的网络接口 (NIC)、5 元组信息、流量决策和(仅限版本 2)吞吐量信息。
- NSG 流日志具有保留功能,可以自动删除在创建后已保留一年的日志。
注意
仅当使用常规用途 v2 存储帐户时,才可以使用保留。
流日志的核心概念包括:
- 软件定义的网络是围绕虚拟网络和子网进行组织的。 可以使用网络安全组管理这些虚拟网络和子网的安全性。
- 网络安全组包含安全规则,这些规则允许或拒绝传入或传出网络安全组所连接的 Azure 资源的网络流量。 网络安全组可与虚拟机 (VM) 的子网或网络接口相关联。 有关详细信息,请参阅网络安全组概述。
- 网络中的所有流量流都通过适用网络安全组中的规则进行评估。 这些评估的结果就是 NSG 流日志。
- NSG 流日志是通过 Azure 平台收集的,无需对 Azure 资源进行任何更改。
- 有两种类型的网络安全组规则:终止和非终止。 每个都有不同的日志记录行为:
- “拒绝”规则是终止类型。 拒绝流量的网络安全组将流量记录在流日志中。 在这种情况下,任何 NSG 拒绝流量后,处理将停止。
- “允许”规则是非终止类型。 如果网络安全组允许流量,则继续进行下一个网络安全组的处理。 允许流量的最后一个网络安全组将流量记录到流日志。
- NSG 流日志将写入存储帐户。 可使用网络观察程序流量分析、Splunk、Grafana、Stealthwatch 等工具导出、处理、分析和可视化 NSG 流日志。
日志格式
NSG 流日志包括以下属性:
-
time:记录事件的时间 (UTC)。 -
systemId:网络安全组的系统 ID。 -
category:事件的类别。 类别始终是NetworkSecurityGroupFlowEvent。 -
resourceid:网络安全组的资源 ID。 -
operationName:始终为NetworkSecurityGroupFlowEvents。 -
properties:流属性的集合:-
Version:流日志的事件架构的版本号。 -
flows:流的集合。 此属性有多个针对不同规则的条目。-
rule:列出流时所依据的规则。 -
flows:流的集合。-
mac:VM 的 NIC 的 MAC 地址,用于收集流。 -
flowTuples:一个字符串,包含逗号分隔格式的流元组的多个属性:-
Time stamp:表示流发生时间的时间戳,采用 UNIX epoch 格式。 -
Source IP:源 IP 地址。 -
Destination IP:目标 IP 地址。 -
Source port:源端口。 -
Destination port:目标端口。 -
Protocol:流的协议。 有效值为T(表示 TCP)和U(表示 UDP)。 -
Traffic flow:流量流的方向。 有效值为I(表示入站)和O(表示出站)。 -
Traffic decision:是允许还是拒绝了流。 有效值为A(表示已允许)和D(表示已拒绝)。 -
Flow State - Version 2 Only:流的状态。 可能的状态包括:-
B:创建流时开始。 未提供统计信息。 -
C:继续执行正在进行的流。 以 5 分钟的时间间隔提供统计信息。 -
E:在流终止时结束。 已提供统计信息。
-
-
Packets sent - Version 2 Only:自上次更新以来,从源发送到目标的 TCP 数据包总数。 -
Bytes sent - Version 2 Only:自上次更新以来,从源发送到目标的 TCP 数据包字节总数。 数据包字节包括数据包标头和有效负载。 -
Packets received - Version 2 Only:自上次更新以来,从目标发送到源的 TCP 数据包总数。 -
Bytes received - Version 2 Only:自上次更新以来,从目标发送到源的 TCP 数据包字节总数。 数据包字节包括数据包标头和有效负载。
-
-
-
-
NSG 流日志版本 2 引入了流状态的概念。 可以配置要接收的流日志的版本。
启动流时记录流状态 B。 流状态 C 和流状态 E 是分别标记流的延续和终止的状态。 状态 C 和 E 都包含流量带宽信息。
示例日志记录
在下面的 NSG 流日志示例中,多条记录遵循前面所述的属性列表。
注意
flowTuples 属性中的值为逗号分隔列表。
版本 1
下面是版本 1 NSG 流日志的示例格式:
{
"records": [
{
"time": "2017-02-16T22:00:32.8950000Z",
"systemId": "55ff55ff-aa66-bb77-cc88-99dd99dd99dd",
"category": "NetworkSecurityGroupFlowEvent",
"resourceId": "/SUBSCRIPTIONS/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/RESOURCEGROUPS/FABRIKAMRG/PROVIDERS/MICROSOFT.NETWORK/NETWORKSECURITYGROUPS/FABRIAKMVM1-NSG",
"operationName": "NetworkSecurityGroupFlowEvents",
"properties": {
"Version": 1,
"flows": [
{
"rule": "DefaultRule_DenyAllInBound",
"flows": [
{
"mac": "000D3AF8801A",
"flowTuples": [
"1487282421,192.0.2.95,10.1.0.4,51529,5358,T,I,D"
]
}
]
},
{
"rule": "UserRule_default-allow-rdp",
"flows": [
{
"mac": "000D3AF8801A",
"flowTuples": [
"1487282370,192.0.2.17,10.1.0.4,61771,3389,T,I,A",
"1487282393,203.0.113.34,10.1.0.4,58596,3389,T,I,A",
"1487282393,192.0.2.154,10.1.0.4,61540,3389,T,I,A",
"1487282423,203.0.113.229,10.1.0.4,53163,3389,T,I,A"
]
}
]
}
]
}
},
{
"time": "2017-02-16T22:01:32.8960000Z",
"systemId": "55ff55ff-aa66-bb77-cc88-99dd99dd99dd",
"category": "NetworkSecurityGroupFlowEvent",
"resourceId": "/SUBSCRIPTIONS/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/RESOURCEGROUPS/FABRIKAMRG/PROVIDERS/MICROSOFT.NETWORK/NETWORKSECURITYGROUPS/FABRIAKMVM1-NSG",
"operationName": "NetworkSecurityGroupFlowEvents",
"properties": {
"Version": 1,
"flows": [
{
"rule": "DefaultRule_DenyAllInBound",
"flows": [
{
"mac": "000D3AF8801A",
"flowTuples": [
"1487282481,198.51.100.194,10.1.0.4,53,1732,U,I,D"
]
}
]
},
{
"rule": "UserRule_default-allow-rdp",
"flows": [
{
"mac": "000D3AF8801A",
"flowTuples": [
"1487282435,198.51.100.68,10.1.0.4,57776,3389,T,I,A",
"1487282454,203.0.113.170,10.1.0.4,59085,3389,T,I,A",
"1487282477,192.0.2.50,10.1.0.4,65078,3389,T,I,A"
]
}
]
}
]
}
},
{
"records": [
{
"time": "2017-02-16T22:00:32.8950000Z",
"systemId": "55ff55ff-aa66-bb77-cc88-99dd99dd99dd",
"category": "NetworkSecurityGroupFlowEvent",
"resourceId": "/SUBSCRIPTIONS/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/RESOURCEGROUPS/FABRIKAMRG/PROVIDERS/MICROSOFT.NETWORK/NETWORKSECURITYGROUPS/FABRIAKMVM1-NSG",
"operationName": "NetworkSecurityGroupFlowEvents",
"properties": {
"Version": 1,
"flows": [
{
"rule": "DefaultRule_DenyAllInBound",
"flows": [
{
"mac": "000D3AF8801A",
"flowTuples": [
"1487282421,192.0.2.95,10.1.0.4,51529,5358,T,I,D"
]
}
]
},
{
"rule": "UserRule_default-allow-rdp",
"flows": [
{
"mac": "000D3AF8801A",
"flowTuples": [
"1487282370,192.0.2.17,10.1.0.4,61771,3389,T,I,A",
"1487282393,203.0.113.34,10.1.0.4,58596,3389,T,I,A",
"1487282393,192.0.2.154,10.1.0.4,61540,3389,T,I,A",
"1487282423,203.0.113.229,10.1.0.4,53163,3389,T,I,A"
]
}
]
}
]
}
},
{
"time": "2017-02-16T22:01:32.8960000Z",
"systemId": "55ff55ff-aa66-bb77-cc88-99dd99dd99dd",
"category": "NetworkSecurityGroupFlowEvent",
"resourceId": "/SUBSCRIPTIONS/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/RESOURCEGROUPS/FABRIKAMRG/PROVIDERS/MICROSOFT.NETWORK/NETWORKSECURITYGROUPS/FABRIAKMVM1-NSG",
"operationName": "NetworkSecurityGroupFlowEvents",
"properties": {
"Version": 1,
"flows": [
{
"rule": "DefaultRule_DenyAllInBound",
"flows": [
{
"mac": "000D3AF8801A",
"flowTuples": [
"1487282481,198.51.100.194,10.1.0.4,53,1732,U,I,D"
]
}
]
},
{
"rule": "UserRule_default-allow-rdp",
"flows": [
{
"mac": "000D3AF8801A",
"flowTuples": [
"1487282435,198.51.100.68,10.1.0.4,57776,3389,T,I,A",
"1487282454,203.0.113.170,10.1.0.4,59085,3389,T,I,A",
"1487282477,192.0.2.50,10.1.0.4,65078,3389,T,I,A"
]
}
]
}
]
}
},
{
"time": "2017-02-16T22:02:32.9040000Z",
"systemId": "55ff55ff-aa66-bb77-cc88-99dd99dd99dd",
"category": "NetworkSecurityGroupFlowEvent",
"resourceId": "/SUBSCRIPTIONS/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/RESOURCEGROUPS/FABRIKAMRG/PROVIDERS/MICROSOFT.NETWORK/NETWORKSECURITYGROUPS/FABRIAKMVM1-NSG",
"operationName": "NetworkSecurityGroupFlowEvents",
"properties": {
"Version": 1,
"flows": [
{
"rule": "DefaultRule_DenyAllInBound",
"flows": [
{
"mac": "000D3AF8801A",
"flowTuples": [
"1487282492,203.0.113.29,10.1.0.4,28918,5358,T,I,D",
"1487282505,192.0.2.55,10.1.0.4,8080,8080,T,I,D"
]
}
]
},
{
"rule": "UserRule_default-allow-rdp",
"flows": [
{
"mac": "000D3AF8801A",
"flowTuples": [
"1487282512,192.0.2.154,10.1.0.4,59046,3389,T,I,A"
]
}
]
}
]
}
}
]
}
]
}
版本 2
下面是版本 2 NSG 流日志的示例格式:
{
"records": [
{
"time": "2018-11-13T12:00:35.3899262Z",
"systemId": "66aa66aa-bb77-cc88-dd99-00ee00ee00ee",
"category": "NetworkSecurityGroupFlowEvent",
"resourceId": "/SUBSCRIPTIONS/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/RESOURCEGROUPS/FABRIKAMRG/PROVIDERS/MICROSOFT.NETWORK/NETWORKSECURITYGROUPS/FABRIAKMVM1-NSG",
"operationName": "NetworkSecurityGroupFlowEvents",
"properties": {
"Version": 2,
"flows": [
{
"rule": "DefaultRule_DenyAllInBound",
"flows": [
{
"mac": "000D3AF87856",
"flowTuples": [
"1542110402,192.0.2.190,10.5.16.4,28746,443,U,I,D,B,,,,",
"1542110424,203.0.113.10,10.5.16.4,56509,59336,T,I,D,B,,,,",
"1542110432,198.51.100.8,10.5.16.4,48495,8088,T,I,D,B,,,,"
]
}
]
},
{
"rule": "DefaultRule_AllowInternetOutBound",
"flows": [
{
"mac": "000D3AF87856",
"flowTuples": [
"1542110377,10.5.16.4,203.0.113.118,59831,443,T,O,A,B,,,,",
"1542110379,10.5.16.4,203.0.113.117,59932,443,T,O,A,E,1,66,1,66",
"1542110379,10.5.16.4,203.0.113.115,44931,443,T,O,A,C,30,16978,24,14008",
"1542110406,10.5.16.4,198.51.100.225,59929,443,T,O,A,E,15,8489,12,7054"
]
}
]
}
]
}
},
{
"time": "2018-11-13T12:01:35.3918317Z",
"systemId": "66aa66aa-bb77-cc88-dd99-00ee00ee00ee",
"category": "NetworkSecurityGroupFlowEvent",
"resourceId": "/SUBSCRIPTIONS/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/RESOURCEGROUPS/FABRIKAMRG/PROVIDERS/MICROSOFT.NETWORK/NETWORKSECURITYGROUPS/FABRIAKMVM1-NSG",
"operationName": "NetworkSecurityGroupFlowEvents",
"properties": {
"Version": 2,
"flows": [
{
"rule": "DefaultRule_DenyAllInBound",
"flows": [
{
"mac": "000D3AF87856",
"flowTuples": [
"1542110437,125.64.94.197,10.5.16.4,59752,18264,T,I,D,B,,,,",
"1542110475,80.211.72.221,10.5.16.4,37433,8088,T,I,D,B,,,,",
"1542110487,46.101.199.124,10.5.16.4,60577,8088,T,I,D,B,,,,",
"1542110490,176.119.4.30,10.5.16.4,57067,52801,T,I,D,B,,,,"
]
}
]
}
]
}
}
]
}
日志元组和带宽计算
下面是 203.0.113.105:35370 和 10.0.0.5:443 之间的 TCP 对话流元组的示例带宽计算:
1708978215,203.0.113.105,10.0.0.5,35370,443,T,I,A,B,,,,
1708978215,203.0.113.105,10.0.0.5,35370,443,T,I,A,C,1021,588096,8005,4610880
1708978215,203.0.113.105,10.0.0.5,35370,443,T,I,A,E,52,29952,47,27072
对于延续 (C) 和结束 (E) 流状态,字节和数据包计数是上一个流的元组记录的聚合计数。 在上一示例对话中,传输的数据包总数是 1021+52+8005+47 = 9125。 传输的字节总数是 588096+29952+4610880+27072 = 5256000。
使用流日志
读取和导出流日志
若要了解如何读取和导出 NSG 流日志,请查看以下指南之一:
NSG 流日志文件存储到以下路径的存储帐户中:
https://{storageAccountName}.blob.core.chinacloudapi.cn/insights-logs-networksecuritygroupflowevent/resourceId=/SUBSCRIPTIONS/{subscriptionID}/RESOURCEGROUPS/{resourceGroupName}/PROVIDERS/MICROSOFT.NETWORK/NETWORKSECURITYGROUPS/{nsgName}/y={year}/m={month}/d={day}/h={hour}/m=00/macAddress={macAddress}/PT1H.json
可视化流日志
若要了解如何可视化 NSG 流日志,请查看以下指南之一:
- 使用网络观察程序流量分析可视化 NSG 流日志
- 使用 Power BI 可视化 NSG 流日志
- 使用 Elastic Stack 可视化 NSG 流日志
- 使用 Grafana 管理和分析 NSG 流日志
- 使用 Graylog 管理和分析 NSG 流日志
NSG 流日志的注意事项
存储帐户
- 位置:存储帐户必须与网络安全组位于同一区域中。
- 订阅:存储帐户必须位于网络安全组的同一订阅或与网络安全组订阅的同一个 Microsoft Entra 租户关联的订阅中。
- 性能层:存储帐户必须为标准帐户。 不支持高级存储帐户。
- 自我管理密钥轮换:如果你更改或轮换存储帐户的访问密钥,则 NSG 流日志将停止工作。 若要解决此问题,必须禁用并重新启用 NSG 流日志。
成本
NSG 流日志记录按生成的日志量计费。 流量较高可能会造成大型流日志量,增加相关成本。
NSG 流日志定价不包括基本的存储成本。 永久保留 NSG 流日志数据或使用保留策略功能意味着在较长时间内会产生存储成本。
非默认入站 TCP 规则
网络安全组是作为有状态防火墙实现的。 但由于当前的平台限制,影响入站 TCP 流的网络安全组非默认安全规则是以无状态方式实现的。
受非默认入站规则影响的流将变为非终止类型。 此外,不会记录这些流的字节和数据包计数。 由于这些因素,NSG 流日志中报告的字节数和数据包数(和网络观察程序流量分析)可能与实际数字不同。
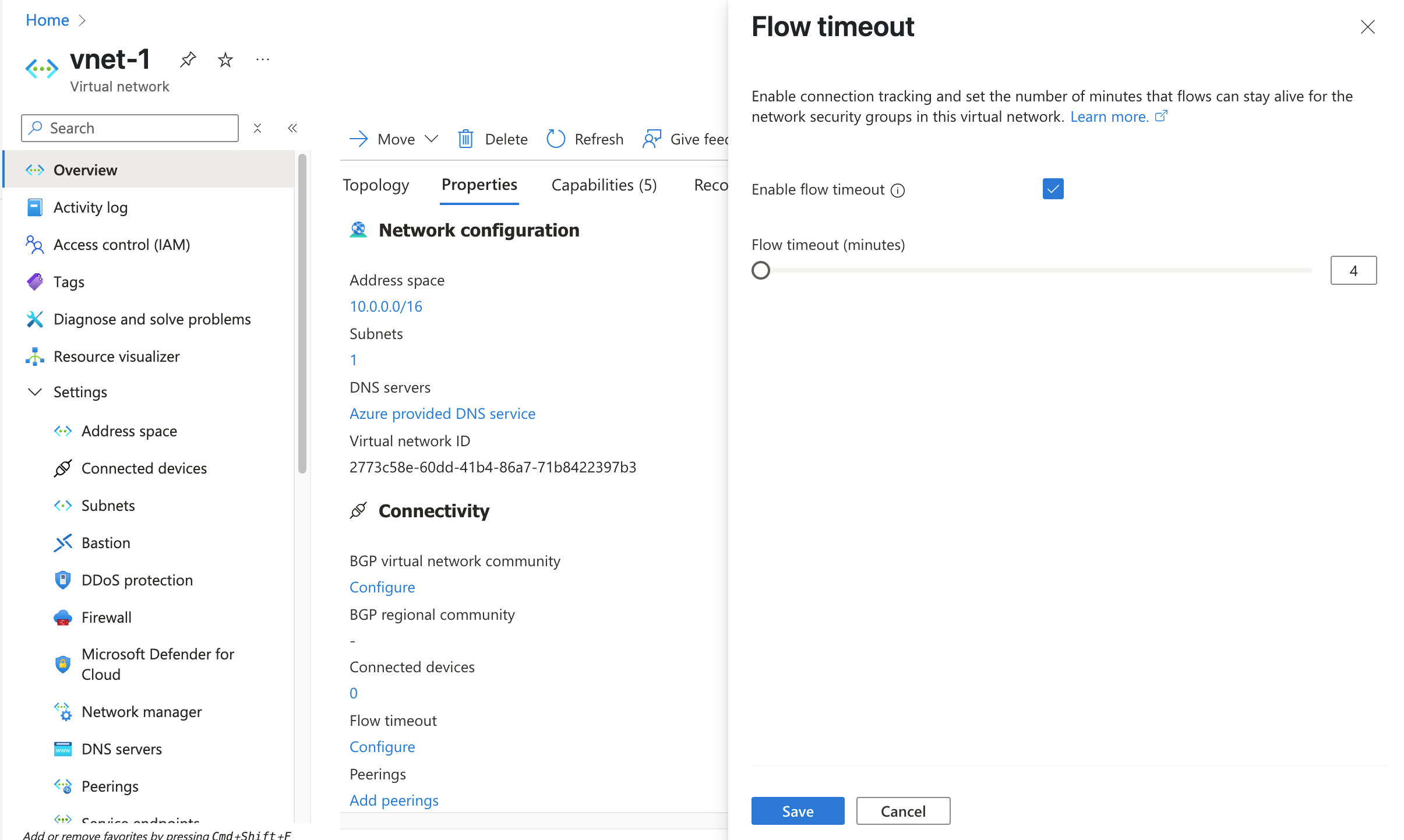
你可以通过将关联虚拟网络上的 FlowTimeoutInMinutes 属性设置为非空值来解决此差异。 可以通过将 FlowTimeoutInMinutes 设置为 4 分钟来实现默认有状态行为。 对于长时间运行的连接,如果不希望流与服务或目标断开连接,则可以将 FlowTimeoutInMinutes 的值设置为最长 30 分钟。 使用 Set-AzVirtualNetwork 设置 FlowTimeoutInMinutes 属性:
$virtualNetwork = @{
Name = 'myVNet'
ResourceGroupName = 'myResourceGroup'
}
$virtualNetworkConfig = Get-AzVirtualNetwork @virtualNetwork
$virtualNetworkConfig.FlowTimeoutInMinutes = 4
$virtualNetworkConfig | Set-AzVirtualNetwork
还可以使用 Azure 门户设置流超时:
从 Internet IP 记录到没有公共 IP 的虚拟机的入站流
如果虚拟机 (VM) 没有与 NIC 关联的公共 IP 地址作为实例级公共 IP,或者是基本负载均衡器后端池的一部分,请使用默认 SNAT。 Azure 会为这些 VM 分配 IP 地址,以促进出站连接。 因此,如果流的目的地是分配给 SNAT 的端口范围内的端口,你可能会看到来自 Internet IP 地址的流的流日志条目。
虽然 Azure 不允许将这些流传输到 VM,但是按照设计,该尝试会被记录并显示在网络观察程序的 NSG 流日志中。 我们建议使用网络安全组来显式阻止不需要的入站 Internet 流量。
ExpressRoute 网关子网上的网络安全组
不建议在 Azure ExpressRoute 网关子网上记录流,因为流量可以绕过该类型的网关。 如果 NSG 已链接到 ExpressRoute 网关子网并且 NSG 流日志已启用,则可能无法捕获发往虚拟机的出站流。 必须在 VM 的子网或 NIC 中捕获此类流。
发送到专用终结点的流量
只能在源 VM 上捕获流向专用终结点的流量。 流量使用 VM 的源 IP 地址和专用终结点的目标 IP 地址进行记录。 由于平台限制,无法在专用终结点本身记录流量。
对关联到应用程序网关 v2 子网的网络安全组的支持
目前不支持对关联到 Azure 应用程序网关 V2 子网的网络安全组使用 NSG 流日志。 支持对关联到 Azure 应用程序网关 V1 子网的网络安全组使用 NSG 流日志。
不兼容的服务
目前,以下 Azure 服务不支持 NSG 流日志:
- Azure 容器实例
- Azure 容器应用
- Azure 逻辑应用
- Azure Functions
- Azure DNS 专用解析程序
- 应用服务
- Azure Database for MariaDB
- Azure Database for MySQL
- Azure Database for PostgreSQL
- Azure SQL 托管实例
注意
在 Azure 应用服务计划下部署的应用服务不支持 NSG 流日志。 若要了解详细信息,请参阅虚拟网络集成的工作原理。
不兼容的虚拟机
以下虚拟机大小不支持 NSG 流日志:
建议对这些虚拟机大小使用虚拟网络流日志。
注意
运行大量网络流量的虚拟机可能会遇到流日志记录失败。 建议将NSG 流日志迁移到此类工作负载的虚拟网络流日志。
最佳做法
在关键子网上启用 NSG 流日志:作为审核和安全方面的最佳做法,应在订阅中的所有关键子网上启用流日志。
在附加到资源的所有网络安全组上启用 NSG 流日志:NSG 流日志是在网络安全组上配置的。 一个流仅与一个网络安全组规则相关联。 如果你要使用多个网络安全组,我们建议对资源子网或网络接口 (NIC) 上应用的所有网络安全组启用 NSG 流日志,以确保记录所有流量。 有关详细信息,请参阅网络安全组如何筛选网络流量。
以下是一些常见方案:
- 一个虚拟机上有多个 NIC:如果有多个 NIC 附加到一个虚拟机,则必须在所有这些 NIC 上启用流日志。
- NIC 级别和子网级别的网络安全组:如果在 NIC 级别和子网级别配置了网络安全组,则必须在两个网络安全组上启用流日志。 网络安全组在 NIC 和子网级别处理规则的确切顺序取决于平台,并且因情况而异。 将根据最后处理的网络安全组记录流量流。 平台状态会更改处理顺序。 必须检查这两个流日志。
- Azure Kubernetes 服务 (AKS) 群集子网:AKS 在群集子网添加默认网络安全组。 必须在此网络安全组上启用 NSG 流日志。
存储预配:根据预期的流日志量预配存储。
命名:网络安全组名称最多只能包含 80 个字符,网络安全组规则名称最多只能包含 65 个字符。 如果名称超出其字符限制,则可能会在日志记录过程中截断这些名称。
常见问题故障排除
无法启用 NSG 流日志
如果在尝试启用 NSG 流日志之前未在订阅上启用 Microsoft.Insights 资源提供程序,那么你可能会收到 AuthorizationFailed 或 GatewayAuthenticationFailed 错误。 有关详细信息,请参阅注册 Insights 提供程序。
我启用了 NSG 流日志,但在我的存储帐户中看不到数据
此问题可能与以下方面相关:
设置时间:NSG 流日志可能需要长达 5 分钟才能显示在存储帐户中(如果配置正确)。 此时将显示 PT1H.json 文件。 有关详细信息,请参阅下载流日志。
网络安全组上缺少流量:有时,由于虚拟机处于非活动状态,或者应用程序网关或其他设备上的上游筛选器阻止流量发送到网络安全组,你将看不到日志。
定价
NSG 流日志按收集的网络流日志量(以兆字节为单位)收费,并为每个订阅附送 5 GB/月的免费层。
如果启用了 NSG 流日志的流量分析,则流量分析功能按每千兆字节处理价格收费。 免费层定价不提供流量分析功能。 有关详细信息,请参阅网络观察程序定价。
日志存储单独收费。 有关详细信息,请参阅 Azure Blob 存储定价 和以下注意事项:
- NSG 流日志工作流会定期 调用创建容器 业务,调用次数与关联的 MAC 地址数量直接成正比,并按存储写入操作进行收费。
- 导致上传尝试失败的任何配置更改或订阅策略仍会根据存储计费策略收取费用。
可用性
下表列出了可在其中启用 NSG 流日志的受支持区域。
| 区域 | 网络安全组流日志 | 虚拟网络流日志 | 流量分析 | Log Analytics 工作区 |
|---|---|---|---|---|
| 中国东部 | ✓ | ✓ | ||
| 中国东部 2 | ✓ | ✓ | ✓ | ✓ |
| 中国东部 3 | ✓ | ✓ | ✓ | |
| 中国北部 | ✓ | ✓ | ✓ | ✓ |
| 中国北部 2 | ✓ | ✓ | ✓ | ✓ |
| 中国北部 3 | ✓ | ✓ | ✓ |
相关内容
- 若要了解如何管理 NSG 流日志,请参阅 创建、更改、禁用或删除 NSG 流日志。
- 若要查找有关 NSG 流日志的一些最常见问题的解答,请参阅流日志常见问题解答。
- 若要了解流量分析,请参阅流量分析概述。