流量分析是一种基于云的解决方案,可用于了解云网络上的用户和应用程序活动。 具体而言,流量分析可以分析 Azure 网络观察程序流日志,帮助洞察 Azure 云中的流量流。 使用流量分析可以:
可视化各个 Azure 订阅中的网络活动。
识别热点。
使用有关以下组件的信息来识别威胁,以保护网络:
- 打开端口
- 尝试访问 Internet 的应用程序
- 连接到恶意网络的虚拟机 (VM)
了解 Azure 区域与 Internet 中的流量流模式,优化网络部署以提高性能和容量。
查明可能导致网络连接失败的不当网络配置。
为何要使用流量分析?
在监视、管理自己的网络,以及识别网络中是否存在安全性、合规性和性能问题时,流量分析非常关键。 在保护和优化自己的环境之前,了解该环境至关重要。 你通常需要知道网络的当前状态,包括以下信息:
- 谁正在连接到网络?
- 他们从哪个位置进行连接?
- 向 Internet 开放了哪些端口?
- 预期的网络行为是什么?
- 是否存在异常网络行为?
- 流量是否突然增长?
云网络不同于本地企业网络。 在本地网络中,路由器和交换机支持 NetFlow 和其他类似协议。 当 IP 网络流量进入或退出网络接口时,你可以使用这些设备来收集其相关数据。 通过分析流量流数据,可以生成网络流量流和流量大小的分析数据。
使用 Azure 虚拟网络时,流日志会收集有关网络的数据。 这些日志提供有关通过网络安全组或虚拟网络的传入和传出 IP 流量的信息。 流量分析分析原始流日志,并将日志数据与有关安全性、拓扑和地理位置的情报相结合。 然后,流量分析会提供环境中流量流的见解。
流量分析提供以下信息:
- 通信最活跃的主机
- 通信最活跃的应用程序协议
- 对话最活跃的主机对
- 允许和阻止的流量
- 入站和出站流量
- 开放的 Internet 端口
- 阻止最多流量的规则
- 每个 Azure 数据中心、虚拟网络、子网或恶意网络的流量分布
关键组件
要使用流量分析,需要以下组件:
网络观察程序:一个区域性服务,可用于在 Azure 中监视和诊断网络方案级别的状况。 可以使用网络观察程序在订阅中启用和禁用流日志。 有关详细信息,请参阅什么是 Azure 网络观察程序?和启用或禁用 Azure 网络观察程序。
Log Analytics:Azure 门户中一个用于处理 Azure Monitor 日志数据的工具。 Azure Monitor 日志是一个用于收集监视数据,并将数据存储在中心存储库中的 Azure 服务。 这些数据可能包括事件、性能数据或通过 Azure API 提供的自定义数据。 收集数据后,可以分析、导出数据,或根据数据发出警报。 网络性能监视器和流量分析等监视应用程序使用 Azure Monitor 日志作为基础。 有关详细信息,请参阅 Azure Monitor 日志。 Log Analytics 提供了针对日志编辑和运行查询的方式。 还可以使用此工具分析查询结果。 有关详细信息,请参阅 Azure Monitor 中的 Log Analytics 概述。
Log Analytics 工作区:用于存储与 Azure 帐户相关的 Azure Monitor 日志数据的环境。 有关 Log Analytics 工作区的详细信息,请参阅 Log Analytics 工作区概述和创建 Log Analytics 工作区。
此外,如果使用流量分析分析网络安全组流日志,需要为流日志记录启用网络安全组;如果使用流量分析分析虚拟网络流日志,需要为流日志记录启用虚拟网络:
网络安全组 (NSG):一个包含安全规则列表的资源,这些规则允许或拒绝发往或来自连接到 Azure 虚拟网络的资源的网络流量。 网络安全组可以与附加到 VM(资源管理器)或单个 VM(经典)的子网、网络接口 (NIC) 相关联。 有关详细信息,请参阅网络安全组概述。
网络安全组流日志:记录了有关通过网络安全组传入和传出 IP 流量的信息。 网络安全组流日志是以 JSON 格式写入的,其中包括:
- 根据规则写入的出站和入站流。
- 该流所适用的 NIC。
- 有关流的信息,例如源和目标 IP 地址、源和目标端口,以及协议。
- 流量的状态,例如允许或拒绝。
有关详细信息,请参阅网络安全组流日志概述和创建网络安全组流日志。
虚拟网络 (VNet):通过此资源,多种类型的 Azure 资源可彼此、与 Internet 并与本地网络安全通信。 有关详细信息,请参阅虚拟网络概述。
虚拟网络流日志:记录了有关通过虚拟网络传入和传出 IP 流量的信息。 虚拟网络流日志是以 JSON 格式写入的,其中包括:
- 出站流和入站流。
- 有关流的信息,例如源和目标 IP 地址、源和目标端口,以及协议。
- 流量的状态,例如允许或拒绝。
有关详细信息,请参阅虚拟网络流日志概述和创建虚拟网络流日志。 若要了解网络安全组流日志与虚拟网络流日志之间的差异,请参阅网络安全组流日志与虚拟网络流日志的对比。
注释
要使用流量分析,您必须具有所需的权限。 有关更多信息,请参阅 流量分析权限。
流量分析的工作原理
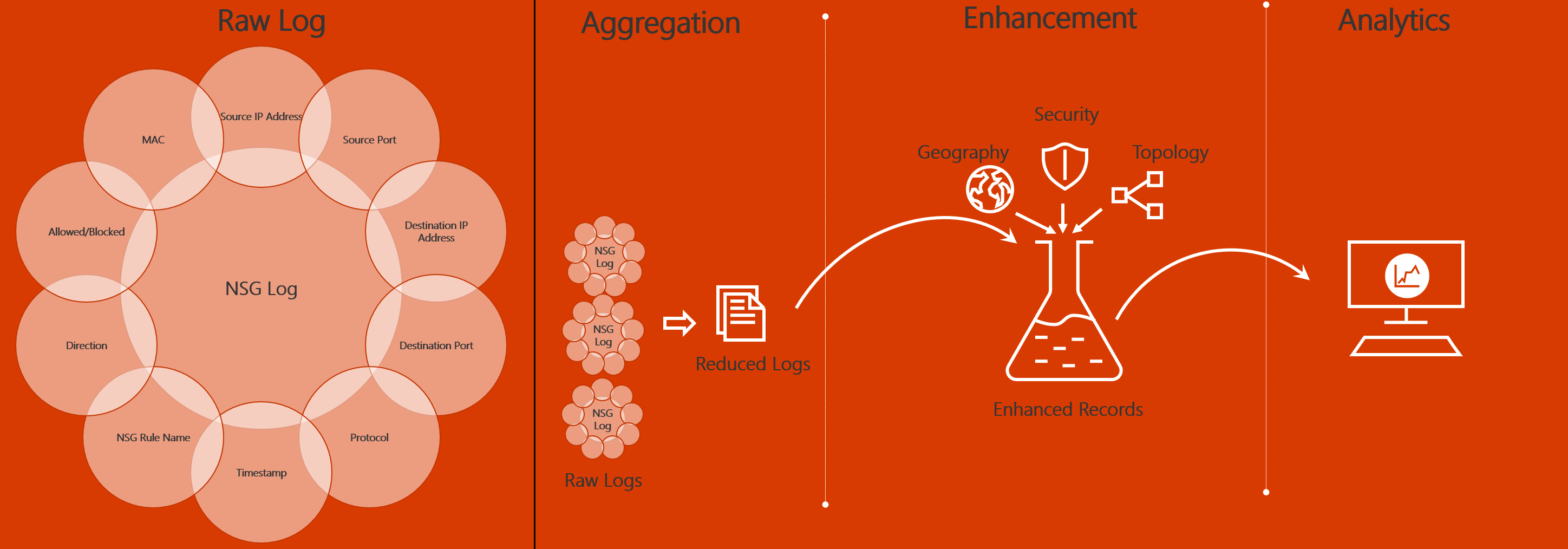
流量分析检查原始流日志。 然后,它通过聚合具有共同源 IP 地址、目标 IP 地址、目标端口和协议的流来减少日志量。
例如,主机 1 的 IP 地址为 10.10.10.10,主机 2 的 IP 地址为 10.10.20.10。 假设这两个主机在一小时内进行了 100 次通信。 在这种情况下,原始流日志将包含 100 个条目。 如果对于这 100 次交互中的每次交互,这两个主机在端口 80 上使用 HTTP 协议,则缩减后的日志只包含一个条目。 该条目指出,在一小时内,主机 1 和主机 2 在端口 80 上使用 HTTP 协议通信了 100 次。
系统会使用地理、安全和拓扑信息增强缩减的日志,然后将其存储在 Log Analytics 工作区中。 下图显示了数据流:
可用性
下表列出了支持的区域,你可在其中为你的流日志和你可以使用的 Log Analytics 工作区启用流量分析。
| 区域 | 网络安全组流日志 | 虚拟网络流日志 | 流量分析 | Log Analytics 工作区 |
|---|---|---|---|---|
| 中国东部 | ✓ | ✓ | ||
| 中国东部 2 | ✓ | ✓ | ✓ | ✓ |
| 中国东部 3 | ✓ | ✓ | ✓ | |
| 中国北部 | ✓ | ✓ | ✓ | ✓ |
| 中国北部 2 | ✓ | ✓ | ✓ | ✓ |
| 中国北部 3 | ✓ | ✓ | ✓ |
注释
如果某个区域支持流日志,但该区域的 Log Analytics 工作区不支持流量分析,则可以从任何其他受支持的区域使用 Log Analytics 工作区。 在这种情况下,使用另一个区域的 Log Analytics 工作区不会产生任何其他跨区域数据传输费用。
定价
有关定价详细信息,请参阅网络观察程序定价和Azure Monitor 定价。
流量分析 FAQ
要获取有关流量分析的最常见问题的解答,请参阅流量分析常见问题解答。