可以通过 Azure 基于角色的访问控制 (Azure RBAC) 管理对 Azure 资源的访问权限。 在本教程中,请授予组访问权限,以便通过 Azure PowerShell 查看订阅中的所有内容并管理资源组中的一切。
在本教程中,你将了解如何执行以下操作:
- 在不同范围为某个组授予访问权限
- 列出访问权限
- 删除访问权限
如果没有 Azure 订阅,可在开始前创建一个试用帐户。
注意
建议使用 Azure Az PowerShell 模块与 Azure 交互。 若要开始,请参阅安装 Azure PowerShell。 若要了解如何迁移到 Az PowerShell 模块,请参阅 将 Azure PowerShell 从 AzureRM 迁移到 Az。
先决条件
若要完成本教程,需要:
- 在 Microsoft Entra ID 中创建组的权限(或拥有已存在的组)
- Microsoft Graph PowerShell SDK
角色分配
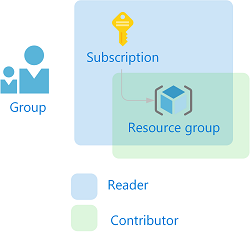
在 Azure RBAC 中,若要授予访问权限,请创建角色分配。 角色分配包含三个要素:安全主体、角色定义和范围。 在本教程中,您将执行以下两个角色分配:
| 安全主体 | 角色定义 | Scope |
|---|---|---|
| 组 (RBAC 教程组) |
读者 | 订阅 |
| 组 (RBAC 教程组) |
参与者 | 资源组 (rbac-tutorial-resource-group) |
创建组
若要分配角色,需要一个用户、组或服务主体。 如果还没有组,可以创建一个。
在 Azure powershell 中,使用 New-MgGroup 命令创建一个新组。
New-MgGroup -DisplayName "RBAC Tutorial Group" -MailEnabled:$false ` -SecurityEnabled:$true -MailNickName "NotSet"DisplayName Id MailNickname Description GroupTypes ----------- -- ------------ ----------- ---------- RBAC Tutorial Group aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb NotSet {}
如果你无权创建组,可以尝试改用教程:使用 Azure PowerShell 授予用户对 Azure 资源的访问权限。
创建资源组
请使用资源组来演示如何在资源组范围分配角色。
使用 Get-AzLocation 命令获取区域位置的列表。
Get-AzLocation | select Location选择附近的一个位置,将其分配给某个变量。
$location = "chinanorth"使用 New-AzResourceGroup 命令创建新的资源组。
New-AzResourceGroup -Name "rbac-tutorial-resource-group" -Location $locationResourceGroupName : rbac-tutorial-resource-group Location : chinanorth ProvisioningState : Succeeded Tags : ResourceId : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/rbac-tutorial-resource-group
授予访问权限
若要为组授予访问权限,请使用 New-AzRoleAssignment 命令分配一个角色。 必须指定安全主体、角色定义和范围。
使用 Get-MgGroup 命令获取组的对象 ID。
Get-MgGroup -Filter "DisplayName eq 'RBAC Tutorial Group'"DisplayName Id MailNickname Description GroupTypes ----------- -- ------------ ----------- ---------- RBAC Tutorial Group aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb NotSet {}在变量中保存组对象 ID。
$groupId = "aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb"使用 Get-AzSubscription 命令获取订阅的 ID。
Get-AzSubscriptionName : Pay-As-You-Go Id : 00000000-0000-0000-0000-000000000000 TenantId : aaaabbbb-0000-cccc-1111-dddd2222eeee State : Enabled在变量中保存订阅范围。
$subScope = "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e"将读者角色分配给订阅范围内的组。
New-AzRoleAssignment -ObjectId $groupId ` -RoleDefinitionName "Reader" ` -Scope $subScopeRoleAssignmentId : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/providers/Microsoft.Authorization/roleAssignments/00000000-0000-0000-0000-000000000000 Scope : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e DisplayName : RBAC Tutorial Group SignInName : RoleDefinitionName : Reader RoleDefinitionId : acdd72a7-3385-48ef-bd42-f606fba81ae7 ObjectId : aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb ObjectType : Group CanDelegate : False将参与者角色分配给资源组范围内的组。
New-AzRoleAssignment -ObjectId $groupId ` -RoleDefinitionName "Contributor" ` -ResourceGroupName "rbac-tutorial-resource-group"RoleAssignmentId : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/rbac-tutorial-resource-group/providers/Microsoft.Authorization/roleAssignments/00000000-0000-0000-0000-000000000000 Scope : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/rbac-tutorial-resource-group DisplayName : RBAC Tutorial Group SignInName : RoleDefinitionName : Contributor RoleDefinitionId : b24988ac-6180-42a0-ab88-20f7382dd24c ObjectId : aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb ObjectType : Group CanDelegate : False
列出访问权限
若要验证订阅的访问权限,请使用 Get-AzRoleAssignment 命令列出角色分配。
Get-AzRoleAssignment -ObjectId $groupId -Scope $subScopeRoleAssignmentId : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/providers/Microsoft.Authorization/roleAssignments/ffffffff-eeee-dddd-cccc-bbbbbbbbbbb0 Scope : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e DisplayName : RBAC Tutorial Group SignInName : RoleDefinitionName : Reader RoleDefinitionId : acdd72a7-3385-48ef-bd42-f606fba81ae7 ObjectId : aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb ObjectType : Group CanDelegate : False在输出中,你可以看到“读者”角色已被分配给订阅层级的“RBAC 教程组”。
若要验证资源组的访问权限,请使用 Get-AzRoleAssignment 命令列出角色分配。
Get-AzRoleAssignment -ObjectId $groupId -ResourceGroupName "rbac-tutorial-resource-group"RoleAssignmentId : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/rbac-tutorial-resource-group/providers/Microsoft.Authorization/roleAssignments/00000000-0000-0000-0000-000000000000 Scope : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/rbac-tutorial-resource-group DisplayName : RBAC Tutorial Group SignInName : RoleDefinitionName : Contributor RoleDefinitionId : b24988ac-6180-42a0-ab88-20f7382dd24c ObjectId : aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb ObjectType : Group CanDelegate : False RoleAssignmentId : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/providers/Microsoft.Authorization/roleAssignments/ffffffff-eeee-dddd-cccc-bbbbbbbbbbb0 Scope : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e DisplayName : RBAC Tutorial Group SignInName : RoleDefinitionName : Reader RoleDefinitionId : acdd72a7-3385-48ef-bd42-f606fba81ae7 ObjectId : aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb ObjectType : Group CanDelegate : False在输出中,可以看到“参与者”角色和“读者”角色已分配给“RBAC 教程组”。 “参与者”角色处于 rbac-tutorial-resource-group 范围,“读者”角色继承于订阅范围。
(可选)使用 Azure 门户列出访问权限
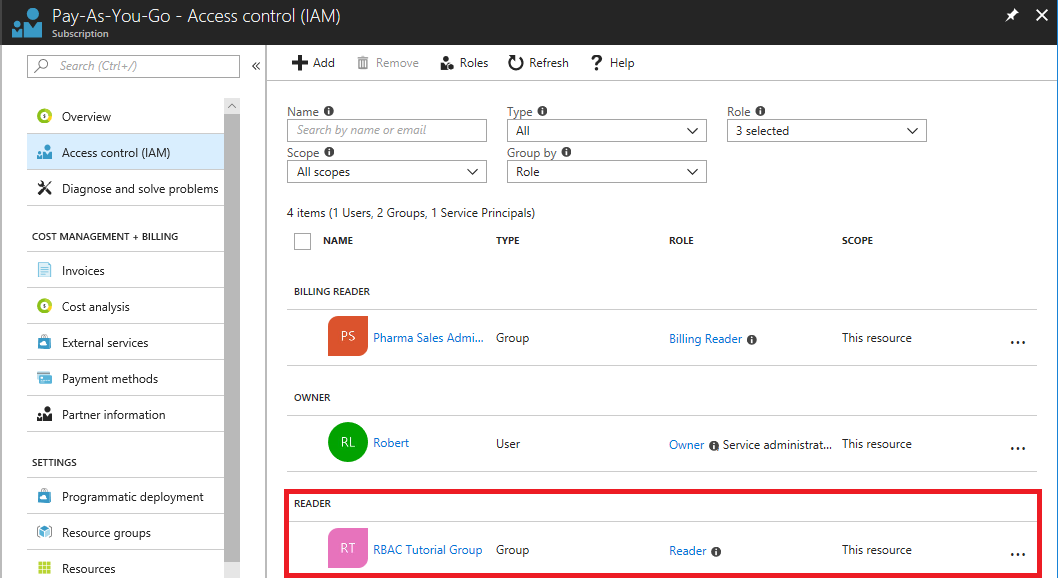
若要查看角色分配在 Azure 门户中的显示情况,请查看订阅的“访问控制 (IAM)”模块。
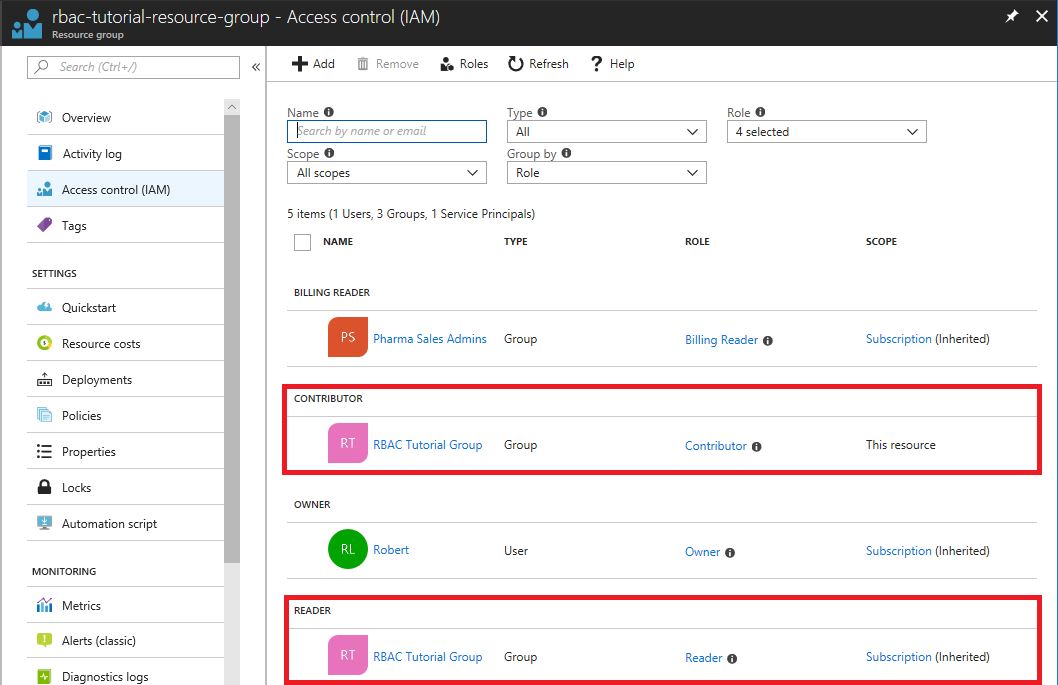
查看资源组的“访问控制(IAM)”界面。
删除访问权限
若要删除用户、组和应用程序的访问权限,请使用 Remove-AzRoleAssignment 删除角色分配。
使用以下命令,删除组在资源组范围的“参与者”角色分配。
Remove-AzRoleAssignment -ObjectId $groupId ` -RoleDefinitionName "Contributor" ` -ResourceGroupName "rbac-tutorial-resource-group"使用以下命令删除在订阅范围内组的“读者”角色分配。
Remove-AzRoleAssignment -ObjectId $groupId ` -RoleDefinitionName "Reader" ` -Scope $subScope
清理资源
若要清理本教程创建的资源,请删除资源组和组。
使用 Remove-AzResourceGroup 命令删除资源组。
Remove-AzResourceGroup -Name "rbac-tutorial-resource-group"Confirm Are you sure you want to remove resource group 'rbac-tutorial-resource-group' [Y] Yes [N] No [S] Suspend [?] Help (default is "Y"):系统要求确认时,请键入“Y”。只需数秒钟即可删除。
使用 Remove-MgGroup 命令删除组。
Remove-MgGroup -GroupID $groupId如果在尝试删除组时收到错误,也可在门户中删除组。