适用于: ✔️ SMB Azure 文件共享
Azure 文件存储采用以下方法来支持使用 Kerberos 身份验证协议通过服务器消息块 (SMB) 对 Windows 文件共享进行基于标识的身份验证:
- 本地 Active Directory 域服务 (AD DS)
- Microsoft Entra 域服务
- 用于混合标识的 Microsoft Entra Kerberos
本文重点介绍如何启用 Microsoft Entra 域服务(以前为 Azure Active Directory 域服务),以实现基于标识的身份验证,从而访问 Azure 文件共享。 在此身份验证方案中,Microsoft Entra 凭据和Microsoft Entra 域服务凭据相同,可以互换使用它们。
建议查看 “工作原理”部分 ,为存储帐户选择正确的标识源。 设置因所选标识源而异。
如果你不熟悉 Azure 文件存储,我们建议在阅读本文之前先阅读规划指南。
注意
Azure 文件支持使用 Microsoft Entra 域服务和 AES-256 加密的 Kerberos 身份验证(推荐)。
Azure Files 支持 Microsoft Entra 域服务的身份验证,并与 Microsoft Entra ID 进行完全或部分(范围)同步。 对于具有作用域同步的环境,管理员应注意,Azure 文件仅遵循向同步的主体授予的 Azure RBAC 角色分配。 分配给那些未从 Microsoft Entra ID 同步到 Microsoft Entra 域服务的标识的角色分配,将被 Azure 文件服务忽略。
先决条件
在为 Azure 文件共享启用 Microsoft Entra 域服务之前,请确保完成以下先决条件:
选择或创建 Microsoft Entra 租户。
可以使用新的或现有的租户。 要访问的租户和文件共享必须与同一订阅相关联。
若要创建新的 Microsoft Entra 租户,可以添加 Microsoft Entra 租户和 Microsoft Entra 订阅。 如果已有一个 Microsoft Entra 租户,但想要创建新租户以便与 Azure 文件共享一同使用,请参阅创建 Azure Active Directory 租户。
在 Microsoft Entra 租户上启用 Microsoft Entra 域服务。
若要支持使用 Microsoft Entra 凭据进行身份验证,必须为 Microsoft Entra 租户启用 Microsoft Entra 域服务。 如果你不是 Microsoft Entra 租户的管理员,请与管理员联系并按照分步指南操作,以使用 Azure 门户启用 Microsoft Entra 域服务。
Microsoft Entra 域服务部署通常需要大约 15 分钟才能完成。 在继续执行下一步之前,请验证 Microsoft Entra 域服务的运行状况状态是否显示“正在运行”,以及是否启用了密码哈希同步。
使用 Microsoft Entra 域服务将 VM 加入域。
若要使用 Microsoft Entra 凭据从 VM 访问 Azure 文件共享,你的 VM 必须已加入 Microsoft Entra 域服务域。 有关如何将 VM 加入域的详细信息,请参阅将 Windows Server 虚拟机加入托管域。 Microsoft Entra 域服务通过 SMB 进行身份验证仅受支持于运行 Windows 7 或 Windows Server 2008 R2 以上版本操作系统的 Windows VM,或运行 Ubuntu 18.04+ 或等效 RHEL 或 SLES 的 Linux VM 上,并且使用 Azure 文件共享。
注意
仅当 VM 对 Microsoft Entra 域服务的域控制器具有畅通无阻的网络连接时,未加入域的 VM 才能使用 Microsoft Entra 域服务身份验证访问 Azure 文件共享。 通常,此连接需要站点到站点或点到站点 VPN。
选择或创建 SMB Azure 文件共享。
选择与 Microsoft Entra 租户相同的订阅关联的新或现有 SMB Azure 文件共享。 请参阅 创建 SMB Azure 文件共享。 为获得最佳性能,建议将文件共享与计划访问共享的 VM 放置在同一区域。
区域可用性
Microsoft Entra 域服务的 Azure 文件身份验证在所有区域中都可用。
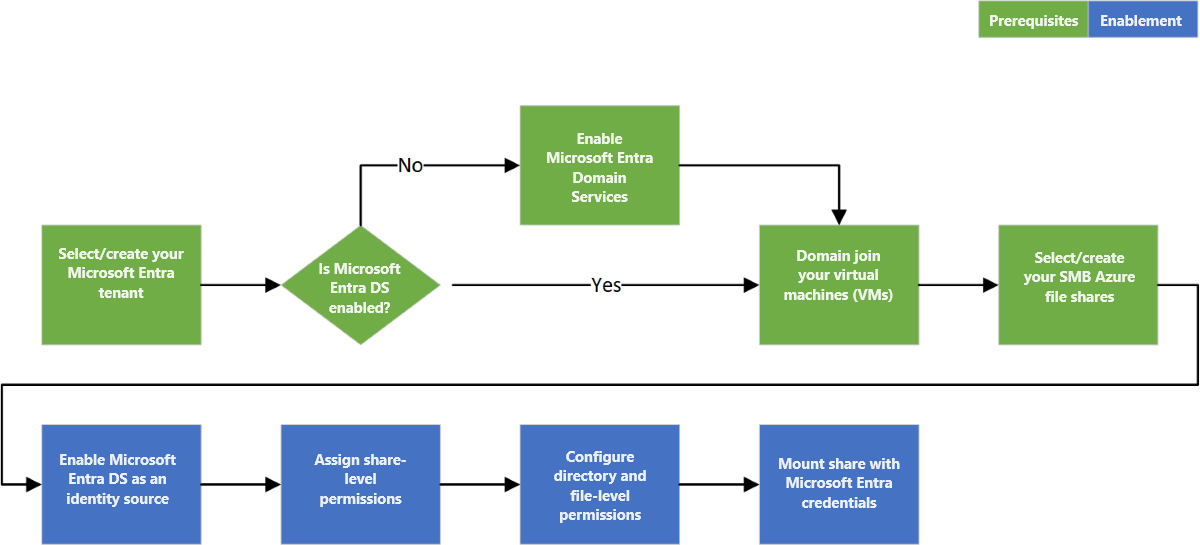
工作流概述
下图显示了用于通过 SMB 为 Azure 文件启用 Microsoft Entra 域服务身份验证的端到端工作流。
为帐户启用 Microsoft Entra 域服务身份验证
若要通过 SMB 为 Azure 文件存储启用 Microsoft Entra 域服务身份验证,可以使用 Azure 门户、Azure PowerShell 或 Azure CLI 为存储帐户设置属性。 设置此属性会通过关联的 Microsoft Entra 域服务部署将存储帐户隐式“加入域”。 然后,为存储帐户中的所有新文件和现有文件共享启用通过 SMB 的 Microsoft Entra 域服务身份验证。
只有在成功将 Microsoft Entra 域服务部署到 Microsoft Entra 租户后之后,才能通过 SMB 启用 Microsoft Entra 域服务身份验证。 有关详细信息,请参阅先决条件。
若要使用 Azure 门户通过 SMB 启用 Microsoft Entra 域服务身份验证,请执行以下步骤:
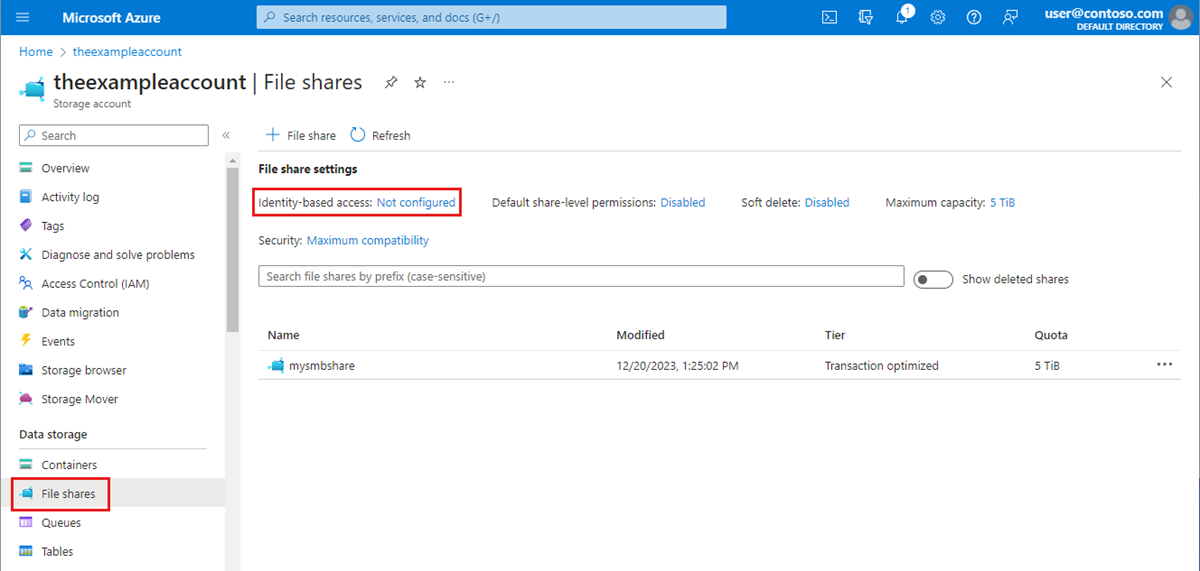
在 Azure 门户中,转到现有的存储帐户或创建存储帐户。
选择“数据存储”“文件共享”。
在“文件共享设置”部分中,选择“基于标识的访问: 未配置”。
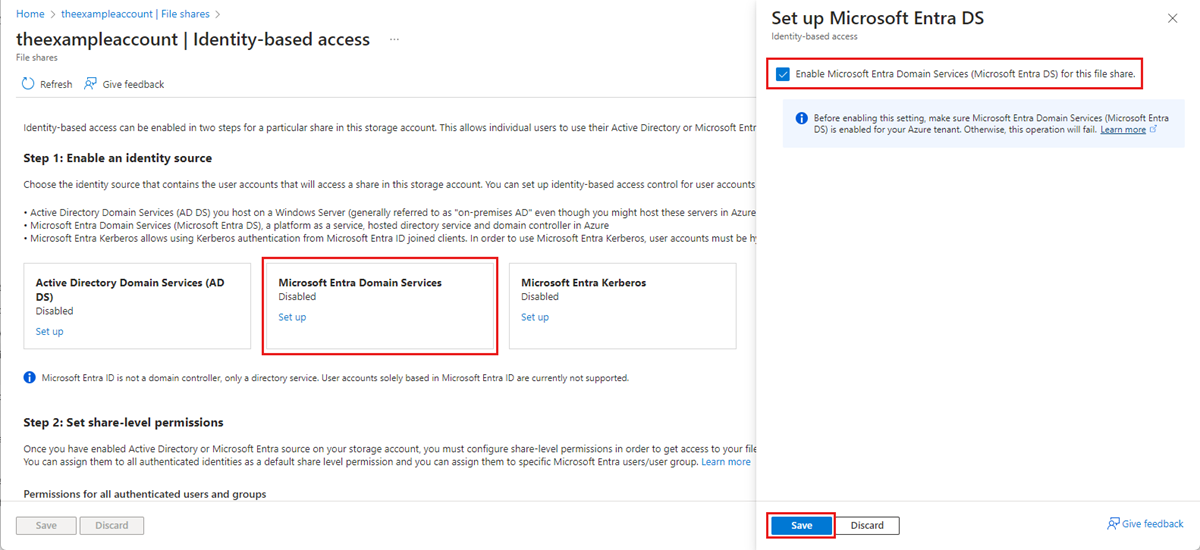
在 “Microsoft Entra 域服务”下,选择“ 设置”,然后选中复选框来启用该功能。
选择“保存”。
建议:使用 AES-256 加密
建议按照以下说明将存储帐户配置为使用 Kerberos AES-256 加密。
此作需要在由 Microsoft Entra 域服务管理的域上运行作才能访问域控制器并请求对域对象进行属性更改。 下面的 cmdlet 是 Windows Server Active Directory PowerShell cmdlet,而不是 Azure PowerShell cmdlet。 由于这种区别,必须从已加入 Microsoft Entra 域服务域的客户端计算机运行这些 PowerShell 命令。
重要
本部分的 Windows Server Active Directory PowerShell cmdlet 必须在 Windows PowerShell 5.1 中从加入 Microsoft Entra 域服务域的客户端计算机运行。 PowerShell 7.x 在此方案中不起作用。
以具有所需权限的 Microsoft Entra 域服务用户身份登录到已加入域的客户端计算机。 你必须对域对象的 msDS-SupportedEncryptionTypes 属性具有写入访问权限。 通常, AAD DC 管理员 组的成员具有必要的权限。 打开普通(未提升的)PowerShell 会话,并执行以下命令。
# 1. Find the service account in your managed domain that represents the storage account.
$storageAccountName= "<InsertStorageAccountNameHere>"
$searchFilter = "Name -like '*{0}*'" -f $storageAccountName
$userObject = Get-ADUser -filter $searchFilter
if ($userObject -eq $null)
{
Write-Error "Cannot find AD object for storage account:$storageAccountName" -ErrorAction Stop
}
# 2. Set the KerberosEncryptionType of the object
Set-ADUser $userObject -KerberosEncryptionType AES256
# 3. Validate that the object now has the expected (AES256) encryption type.
Get-ADUser $userObject -properties KerberosEncryptionType
重要
如果以前使用 RC4 加密并更新了存储帐户以使用 AES-256(建议), klist purge 请在客户端上运行,然后重新装载文件共享以获取 AES-256 的新 Kerberos 票证。
下一步
- 若要向用户授予对文件共享的访问权限,请按照分配共享级权限中的说明进行操作。