重要
Azure 磁盘加密计划于 2028 年 9 月 15 日停用。 在该日期之前,可以继续使用 Azure 磁盘加密,而不会中断。 2028 年 9 月 15 日,已启用 ADE 的工作负荷将继续运行,但 VM 重启后加密磁盘将无法解锁,从而导致服务中断。
使用 主机端加密 用于新 VM。 所有已启用 ADE 的 VM(包括备份)必须在停用日期之前迁移到主机上的加密,以避免服务中断。 有关详细信息,请参阅 从 Azure 磁盘加密迁移到主机加密 。
适用对象:✔️ Linux VM ✔️ 灵活规模集
本文分步介绍如何在加密设备上执行逻辑卷管理 (LVM) 和 RAID。 该过程适用于以下环境:
- Linux 分布
- Ubuntu 18.04+
- SUSE 12+
- Azure 磁盘加密单一传递扩展
- Azure 磁盘加密双重传递扩展
Scenarios
本文中的过程支持以下方案:
- 在加密设备上配置 LVM (LVM-on-crypt)
- 在加密设备上配置 RAID (RAID-on-crypt)
在加密基础设备或设备之后,就可以在该加密层上创建 LVM 或 RAID 结构。
物理卷 (PV) 在加密层上创建。 物理卷用于创建卷组。 创建卷并在 /etc/fstab 上添加所需的条目。
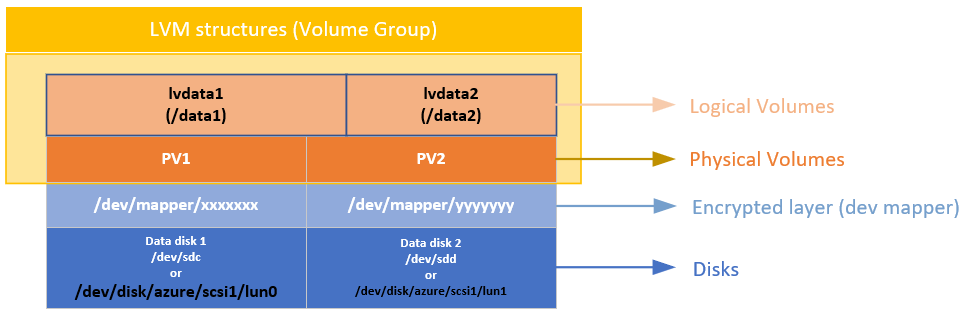
以类似的方式,在磁盘上的加密层上创建 RAID 设备。 在 RAID 设备上创建文件系统,并将其作为常规设备添加到 /etc/fstab。
注意事项
建议使用 LVM-on-crypt。 由于特定的应用程序或环境限制而无法使用 LVM 时,可以选择 RAID。
我们将使用“EncryptFormatAll”选项。 有关此选项的详细信息,请参阅将 EncryptFormatAll 功能用于 Linux VM 上的数据磁盘。
虽然在加密操作系统时也可以使用此方法,但在这里仅加密数据驱动器。
这些过程假定已检查 Linux VM 上的 Azure 磁盘加密方案和快速入门:使用 Azure CLI 创建 Linux VM 并对其进行加密中的先决条件。
Azure 磁盘加密双重传递版本位于弃用路径上,不应再用于新加密。
常规步骤
使用“on-crypt”配置时,请使用以下过程中概述的过程。
注释
我们将在本文中使用变量。 请相应地替换值。
部署 VM
以下命令可选,但建议将其应用于新部署的虚拟机 (VM)。
PowerShell:
New-AzVm -ResourceGroupName ${RGNAME} `
-Name ${VMNAME} `
-Location ${LOCATION} `
-Size ${VMSIZE} `
-Image ${OSIMAGE} `
-Credential ${creds} `
-Verbose
Azure CLI:
az vm create \
-n ${VMNAME} \
-g ${RGNAME} \
--image ${OSIMAGE} \
--admin-username ${username} \
--admin-password ${password} \
-l ${LOCATION} \
--size ${VMSIZE} \
-o table
将磁盘附加到 VM
对要附加到 VM 的 $N 个新磁盘重复以下命令。
PowerShell:
$storageType = 'Standard_LRS'
$dataDiskName = ${VMNAME} + '_datadisk0'
$diskConfig = New-AzDiskConfig -SkuName $storageType -Location $LOCATION -CreateOption Empty -DiskSizeGB 5
$dataDisk1 = New-AzDisk -DiskName $dataDiskName -Disk $diskConfig -ResourceGroupName ${RGNAME}
$vm = Get-AzVM -Name ${VMNAME} -ResourceGroupName ${RGNAME}
$vm = Add-AzVMDataDisk -VM $vm -Name $dataDiskName -CreateOption Attach -ManagedDiskId $dataDisk1.Id -Lun 0
Update-AzVM -VM ${VM} -ResourceGroupName ${RGNAME}
Azure CLI:
az vm disk attach \
-g ${RGNAME} \
--vm-name ${VMNAME} \
--name ${VMNAME}datadisk1 \
--size-gb 5 \
--new \
-o table
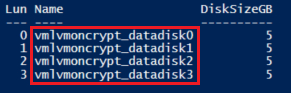
验证磁盘是否已附加到 VM
PowerShell:
$VM = Get-AzVM -ResourceGroupName ${RGNAME} -Name ${VMNAME}
$VM.StorageProfile.DataDisks | Select-Object Lun,Name,DiskSizeGB
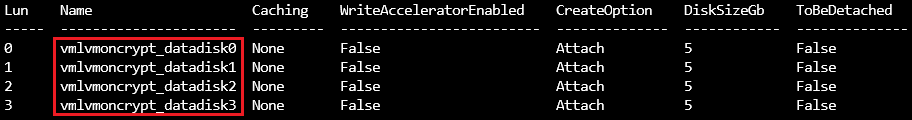
Azure CLI:
az vm show -g ${RGNAME} -n ${VMNAME} --query storageProfile.dataDisks -o table
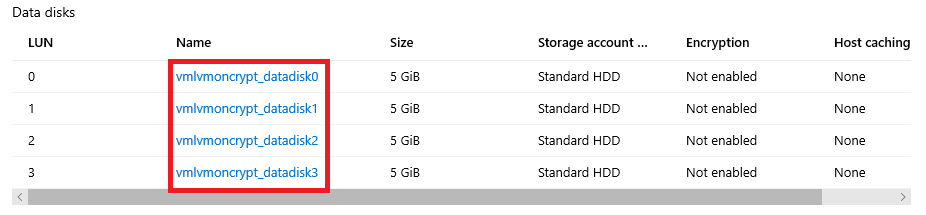
门户:
OS:
lsblk
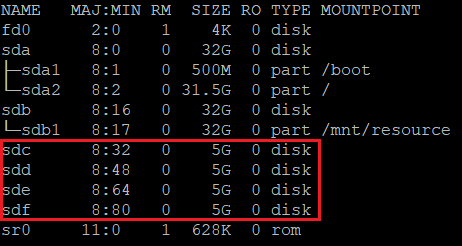
配置要加密的磁盘
此配置在操作系统级别完成。 将相应的磁盘配置为通过 Azure 磁盘加密进行传统加密:
- 文件系统是在磁盘上创建的。
- 创建临时装入点以装载文件系统。
- 文件系统在 /etc/fstab 上配置为在启动时装载。
检查分配给新磁盘的设备号。 在此示例中,使用四个数据磁盘。
lsblk

在每个磁盘上创建文件系统
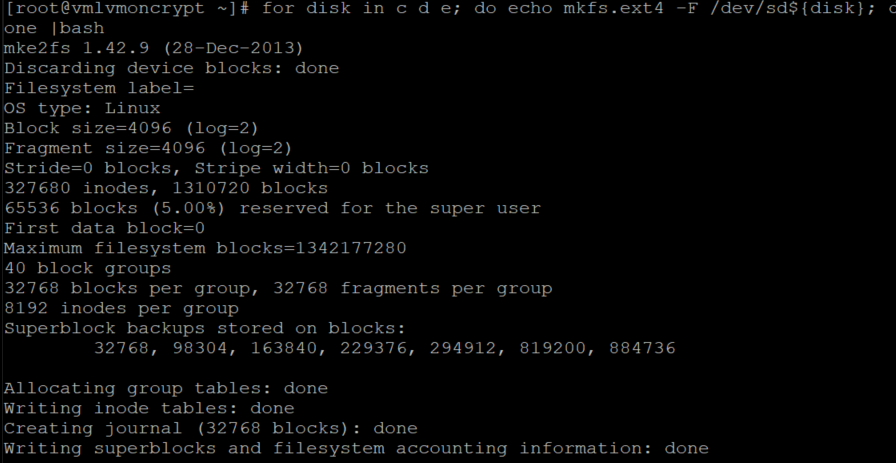
此命令在“for”循环的“in”部分中定义的每个磁盘上迭代创建 ext4 文件系统。
for disk in c d e f; do echo mkfs.ext4 -F /dev/sd${disk}; done |bash
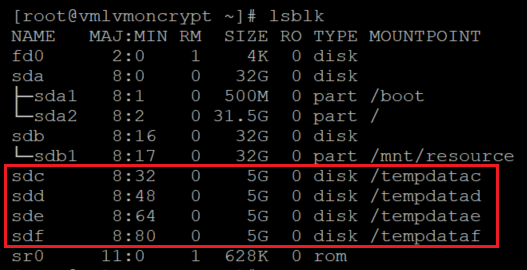
查找最近创建的文件系统的通用唯一标识符 (UUID),创建临时文件夹,在 /etc/fstab 上添加相应的条目,然后装载所有文件系统。
此命令还会在“for”循环的“in”部分中定义的每个磁盘上进行迭代:
for disk in c d e f; do diskuuid="$(blkid -s UUID -o value /dev/sd${disk})"; \
mkdir /tempdata${disk}; \
echo "UUID=${diskuuid} /tempdata${disk} ext4 defaults,nofail 0 0" >> /etc/fstab; \
mount -a; \
done
验证磁盘是否已正确装载
lsblk
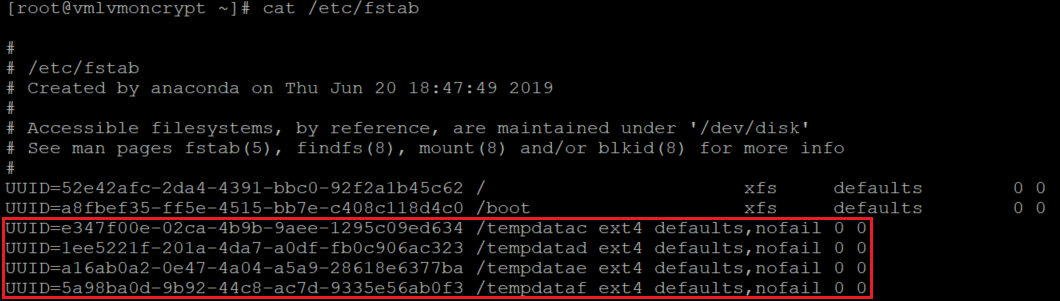
还要验证磁盘是否已配置:
cat /etc/fstab
加密数据磁盘
使用密钥加密密钥 (KEK) 的 PowerShell:
$sequenceVersion = [Guid]::NewGuid()
Set-AzVMDiskEncryptionExtension -ResourceGroupName $RGNAME `
-VMName ${VMNAME} `
-DiskEncryptionKeyVaultUrl $diskEncryptionKeyVaultUrl `
-DiskEncryptionKeyVaultId $KeyVaultResourceId `
-KeyEncryptionKeyUrl $keyEncryptionKeyUrl `
-KeyEncryptionKeyVaultId $KeyVaultResourceId `
-VolumeType 'DATA' `
-EncryptFormatAll `
-SequenceVersion $sequenceVersion `
-skipVmBackup;
使用 KEK 的 Azure CLI:
az vm encryption enable \
--resource-group ${RGNAME} \
--name ${VMNAME} \
--disk-encryption-keyvault ${KEYVAULTNAME} \
--key-encryption-key ${KEYNAME} \
--key-encryption-keyvault ${KEYVAULTNAME} \
--volume-type "DATA" \
--encrypt-format-all \
-o table
验证加密状态
仅当所有磁盘都已加密后,才继续下一步。
PowerShell:
Get-AzVmDiskEncryptionStatus -ResourceGroupName ${RGNAME} -VMName ${VMNAME}
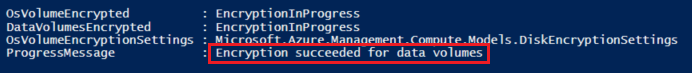
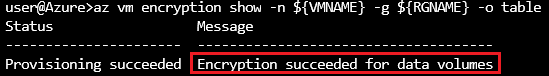
Azure CLI:
az vm encryption show -n ${VMNAME} -g ${RGNAME} -o table
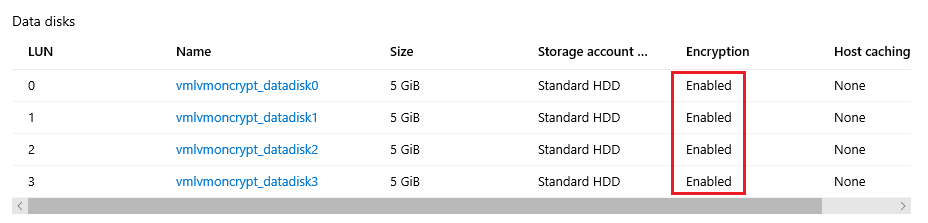
门户:
OS 级别:
lsblk
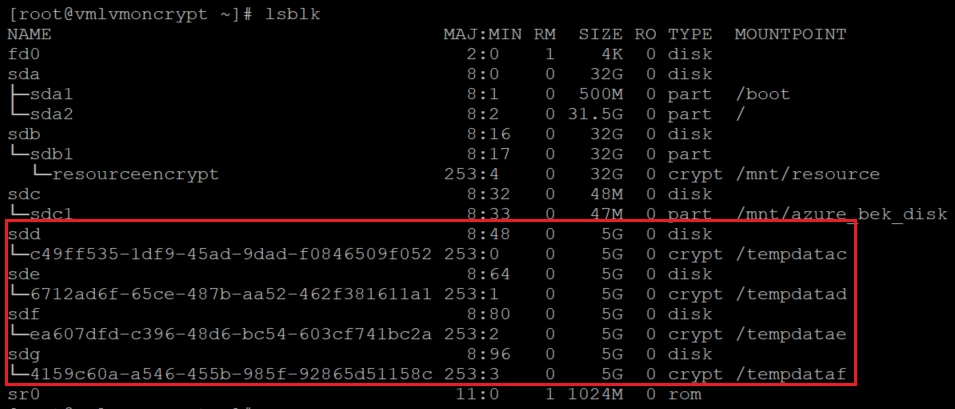
扩展会将文件系统添加到 /var/lib/azure_disk_encryption_config/azure_crypt_mount(旧加密)或 /etc/crypttab(新加密)。
注释
请不要修改任何其他文件。
此文件将负责在启动过程中激活这些磁盘,以便 LVM 或 RAID 以后可以使用这些磁盘。
不用担心此文件上的装入点。 当在这些加密设备上创建物理卷或 RAID 设备之后,Azure 磁盘加密将无法将磁盘作为普通文件系统安装。 (这将删除在准备过程中使用的文件系统格式。)
删除临时文件夹和临时 fstab 条目
在将用作 LVM 一部分的磁盘上卸载文件系统。
for disk in c d e f; do umount /tempdata${disk}; done
同时删除 /etc/fstab 条目:
vi /etc/fstab
验证是否未装载磁盘以及是否已删除 /etc/fstab 上的条目
lsblk
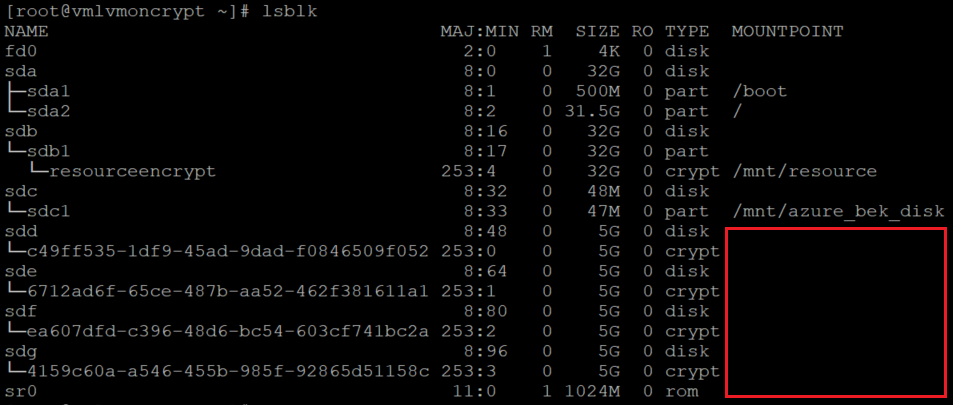
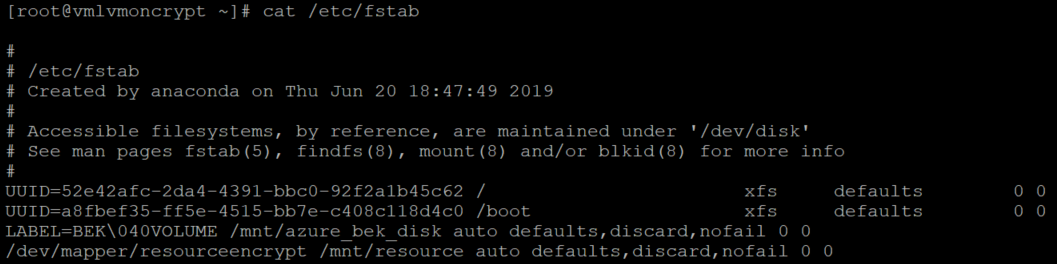
同时验证是否已配置磁盘:
cat /etc/fstab
LVM-on-crypt 的步骤
加密基础磁盘之后,接下来即可创建 LVM 结构。
不要使用设备名称,而是使用每个磁盘的 /dev/mapper 路径来创建物理卷(在磁盘上的加密层上,而不是磁盘本身上)。
在加密层上配置 LVM
创建物理卷
你将收到一条警告,询问是否可以擦除文件系统签名。 输入 y 继续操作,或使用回显“y”,如下所示 :
echo "y" | pvcreate /dev/mapper/c49ff535-1df9-45ad-9dad-f0846509f052
echo "y" | pvcreate /dev/mapper/6712ad6f-65ce-487b-aa52-462f381611a1
echo "y" | pvcreate /dev/mapper/ea607dfd-c396-48d6-bc54-603cf741bc2a
echo "y" | pvcreate /dev/mapper/4159c60a-a546-455b-985f-92865d51158c
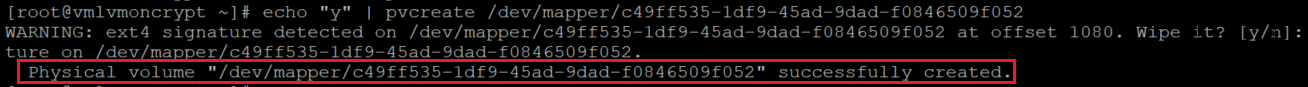
注释
需要根据 lsblk 的输出,将此处的 /dev/mapper/device 名称替换为实际值。
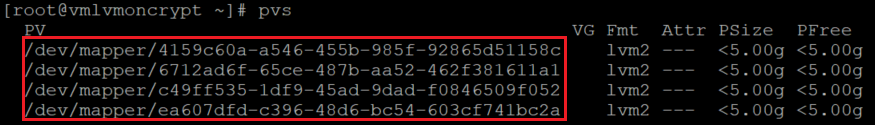
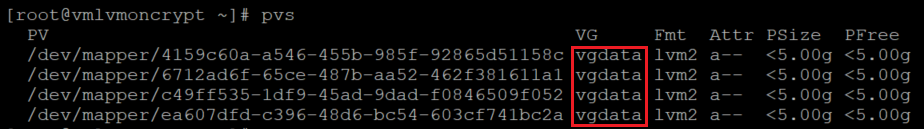
验证物理卷的信息
pvs
创建卷组
使用已初始化的相同设备创建卷组:
vgcreate vgdata /dev/mapper/
检查卷组的信息
vgdisplay -v vgdata
pvs
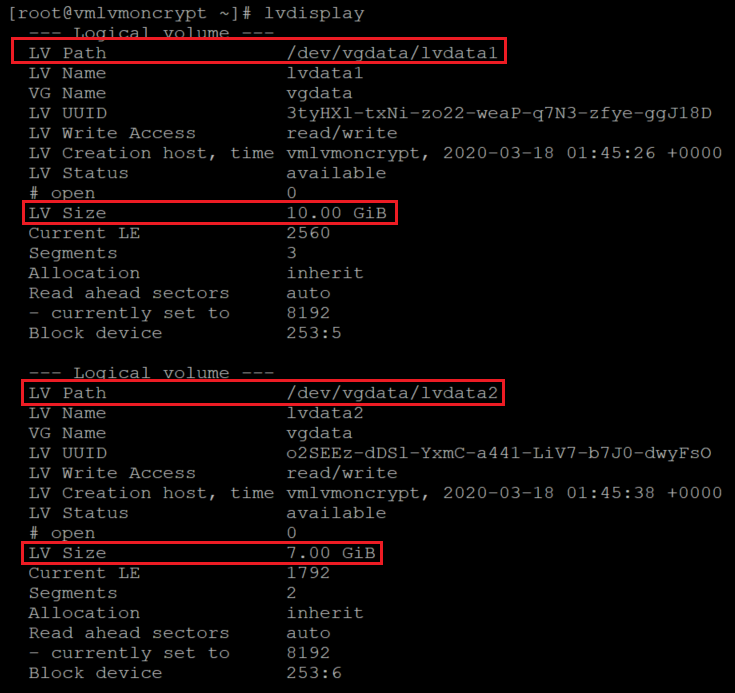
创建逻辑卷
lvcreate -L 10G -n lvdata1 vgdata
lvcreate -L 7G -n lvdata2 vgdata
检查创建的逻辑卷
lvdisplay
lvdisplay vgdata/lvdata1
lvdisplay vgdata/lvdata2
在逻辑卷的结构上创建文件系统
echo "yes" | mkfs.ext4 /dev/vgdata/lvdata1
echo "yes" | mkfs.ext4 /dev/vgdata/lvdata2
创建新文件系统的装入点
mkdir /data0
mkdir /data1
将新文件系统添加到 /etc/fstab 并对其进行装载
echo "/dev/mapper/vgdata-lvdata1 /data0 ext4 defaults,nofail 0 0" >>/etc/fstab
echo "/dev/mapper/vgdata-lvdata2 /data1 ext4 defaults,nofail 0 0" >>/etc/fstab
mount -a
验证是否已装载新文件系统
lsblk -fs
df -h
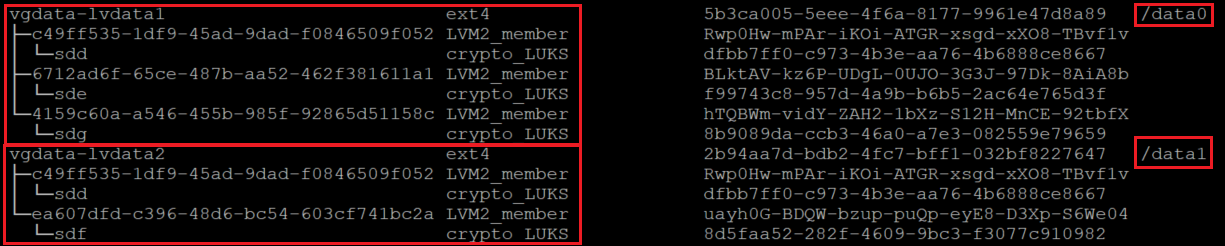
在 lsblk 的这种变体中,我们将按相反顺序列出显示依赖项的设备。 此选项有助于标识按逻辑卷(而不是原始的 /dev/sd[磁盘] 设备名称)分组的设备。
务必确保将 nofail 选项添加到在通过 Azure 磁盘加密进行加密的设备上创建的 LVM 卷的装入点选项中。 它可以防止 OS 在启动过程中(或处于维护模式)停滞。
如果不使用 nofail 选项:
- OS 将永远不会进入启动 Azure 磁盘加密以及解锁和装载数据磁盘的阶段。
- 启动过程结束时,将解锁加密的磁盘。 LVM 卷和文件系统会自动装载,直到 Azure 磁盘加密将其解锁。
可以测试重启 VM 的过程,并验证启动后是否还自动装载了文件系统。 此过程可能需要几分钟时间,具体取决于文件系统的数量和大小。
重启 VM 并在重启后对其进行验证
shutdown -r now
lsblk
df -h
RAID-on-crypt 的步骤
现在,基础磁盘已加密,可以继续创建 RAID 结构。 此过程与 LVM 的过程相同,但使用的是每个磁盘的 /dev/mapper 路径,而不是设备名称。
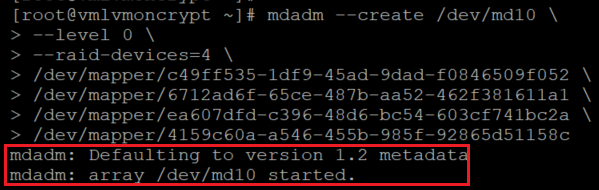
在磁盘的加密层上配置 RAID
mdadm --create /dev/md10 \
--level 0 \
--raid-devices=4 \
/dev/mapper/c49ff535-1df9-45ad-9dad-f0846509f052 \
/dev/mapper/6712ad6f-65ce-487b-aa52-462f381611a1 \
/dev/mapper/ea607dfd-c396-48d6-bc54-603cf741bc2a \
/dev/mapper/4159c60a-a546-455b-985f-92865d51158c
注释
需要根据 lsblk 的输出,将此处的 /dev/mapper/device 名称替换为实际值。
检查/监视 RAID 的创建过程
watch -n1 cat /proc/mdstat
mdadm --examine /dev/mapper/[]
mdadm --detail /dev/md10
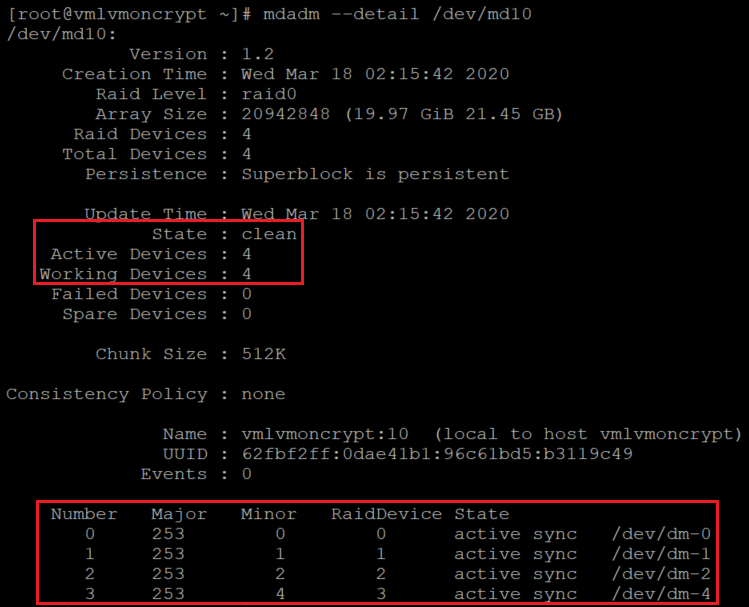
在新的 RAID 设备上创建文件系统
mkfs.ext4 /dev/md10
为文件系统创建新的装入点,将新的文件系统添加到 /etc/fstab 并装载该文件:
注释
在本特定示例中,此循环仅在一台设备上循环访问,采用这种构建方式以便在需要时用于多个 md 设备。
for device in md10; do diskuuid="$(blkid -s UUID -o value /dev/${device})"; \
mkdir /raiddata; \
echo "UUID=${diskuuid} /raiddata ext4 defaults,nofail 0 0" >> /etc/fstab; \
mount -a; \
done
验证是否已装载新文件系统:
lsblk -fs
df -h
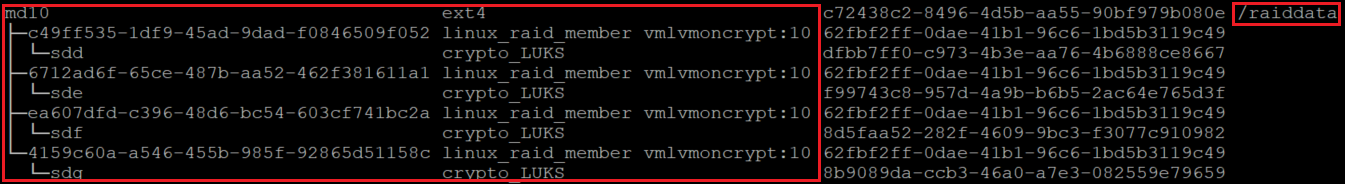
务必确保将 nofail 选项添加到在通过 Azure 磁盘加密进行加密的设备上创建的 RAID 卷的装入点选项中。 它可以防止 OS 在启动过程中(或处于维护模式)停滞。
如果不使用 nofail 选项:
- OS 将永远不会进入启动 Azure 磁盘加密以及解锁和装载数据磁盘的阶段。
- 启动过程结束时,将解锁加密的磁盘。 RAID 卷和文件系统会自动装载,直到 Azure 磁盘加密将其解锁。
可以测试重启 VM 的过程,并验证启动后是否还自动装载了文件系统。 此过程可能需要几分钟时间,具体取决于文件系统的数量和大小。
shutdown -r now
可以登录时:
lsblk
df -h