通过 Azure 虚拟网络中的应用程序安全组,可以将网络安全配置为应用程序结构的自然扩展,使你能够基于这些组对虚拟机进行分组和定义网络安全策略。 可以大量重复使用安全策略,而无需手动维护显式 IP 地址。 平台会处理显式 IP 地址和多个规则集存在的复杂性,让你专注于业务逻辑。 若要更好地理解应用程序安全组,请考虑以下示例:
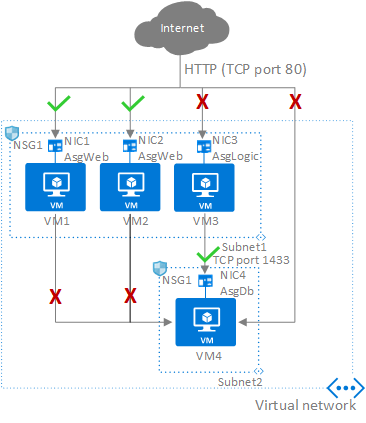
在上图中,NIC1 和 NIC2 是 AsgWeb 应用程序安全组的成员。 NIC3 是 AsgLogic 应用程序安全组的成员。 NIC4 是 AsgDb 应用程序安全组的成员。 尽管此示例中的每个网络接口(NIC)只是一个应用程序安全组的成员,但网络接口可以是多个应用程序安全组的成员,直到 Azure 限制。 这些网络接口都没有关联的网络安全组。 NSG1 关联到两个子网,包含以下规则:
允许-HTTP-Inbound-Internet
若要让流量从 Internet 流到 Web 服务器,此规则是必需的。 由于 DenyAllInbound 默认安全规则拒绝了来自 Internet 的入站流量,因此 AsgLogic 或 AsgDb 应用程序安全组无需使用额外的规则。
| 优先度 | 来源 | 源端口 | 目的地 | 目标端口 | 协议 | 访问 |
|---|---|---|---|---|---|---|
| 100 | Internet | * | AsgWeb | 80 | TCP | 允许 |
拒绝-Database-All
由于 AllowVNetInBound 默认安全规则允许同一虚拟网络中资源之间的所有通信,因此需要此规则来拒绝来自所有资源的流量。
| 优先度 | 来源 | 源端口 | 目的地 | 目标端口 | 协议 | 访问 |
|---|---|---|---|---|---|---|
| 120 | * | * | AsgDb | 1433 | 任意 | 否认 |
允许-Database-BusinessLogic
此规则允许从 AsgLogic 应用程序安全组到 AsgDb 应用程序安全组的流量。 此规则的优先级高于 Deny-Database-All 规则的优先级。 因此,此规则在 Deny-Database-All 规则之前处理,这样系统就会允许来自 AsgLogic 应用程序安全组的流量,而阻止所有其他流量。
| 优先度 | 来源 | 源端口 | 目的地 | 目标端口 | 协议 | 访问 |
|---|---|---|---|---|---|---|
| 110 | AsgLogic | * | AsgDb | 1433 | TCP | 允许 |
作为应用程序安全组成员的网络接口应用网络安全组规则,这些规则将其指定为源或目标。 网络安全组规则不会影响其他网络接口。 如果网络接口不是应用程序安全组的成员,则规则不适用于网络接口,即使网络安全组关联到子网。
约束
应用程序安全组具有以下约束:
可以在一个订阅中配置的应用程序安全组存在数量限制,并且存在与应用程序安全组相关的其他限制。 有关详细信息,请参阅 Azure 限制。
分配给应用程序安全组的所有网络接口必须存在于分配给应用程序安全组的第一个网络接口所在的同一虚拟网络中。 例如,如果分配给名为 AsgWeb 的应用程序安全组的第一个网络接口位于名为 VNet1 的虚拟网络中,则分配给 ASGWeb 的所有后续网络接口都必须存在于 VNet1 中。 不能向同一应用程序安全组添加来自不同虚拟网络的网络接口。
如果将应用程序安全组指定为网络安全组规则中的源和目标,则两个应用程序安全组中的网络接口必须存在于同一虚拟网络中。
- 例如, AsgLogic 包含 来自 VNet1 的网络接口, AsgDb 包含 VNet2 中的网络接口。 在这种情况下,不可能将 AsgLogic 指定为源, AsgDb 作为同一网络安全组规则中的目标。 源和目标应用程序安全组的所有网络接口必须存在于同一虚拟网络中。
小窍门
若要最大程度地减少所需的安全规则数,请规划所需的应用程序安全组。 尽可能使用服务标记或应用程序安全组(而不是单个 IP 地址或 IP 地址范围)创建规则。
后续步骤
- 连接如何创建网络安全组。