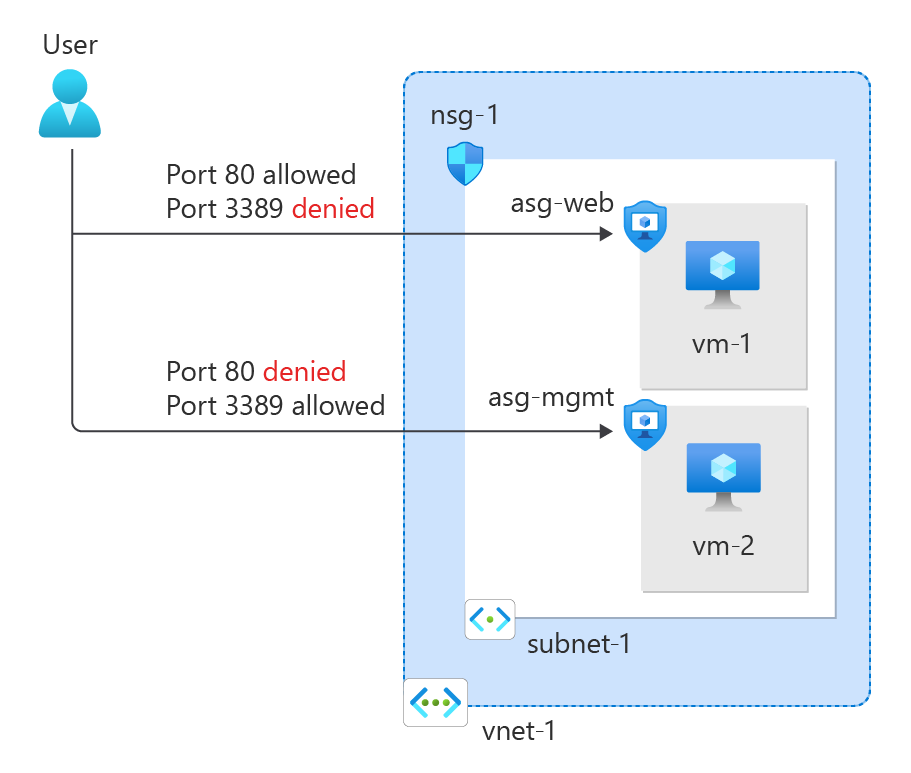
创建虚拟网络
下面的过程创建虚拟网络及资源子网。
在门户中,搜索并选择“虚拟网络”。
在“虚拟网络”页面上,选择“+ 创建”。
在创建虚拟网络的基本信息选项卡上输入或选择以下信息:
| 设置 |
值 |
| 项目详细信息 |
|
| 订阅 |
选择订阅。 |
| 资源组 |
选择“新建”。
在“名称”中输入“test-rg”。
选择“确定”。 |
| 实例详细信息 |
|
| 名称 |
输入“vnet-1”。 |
| 区域 |
选择“(亚太)中国东部 2”。 |
选择“下一步: IP 地址”,转到“IP 地址”选项卡。
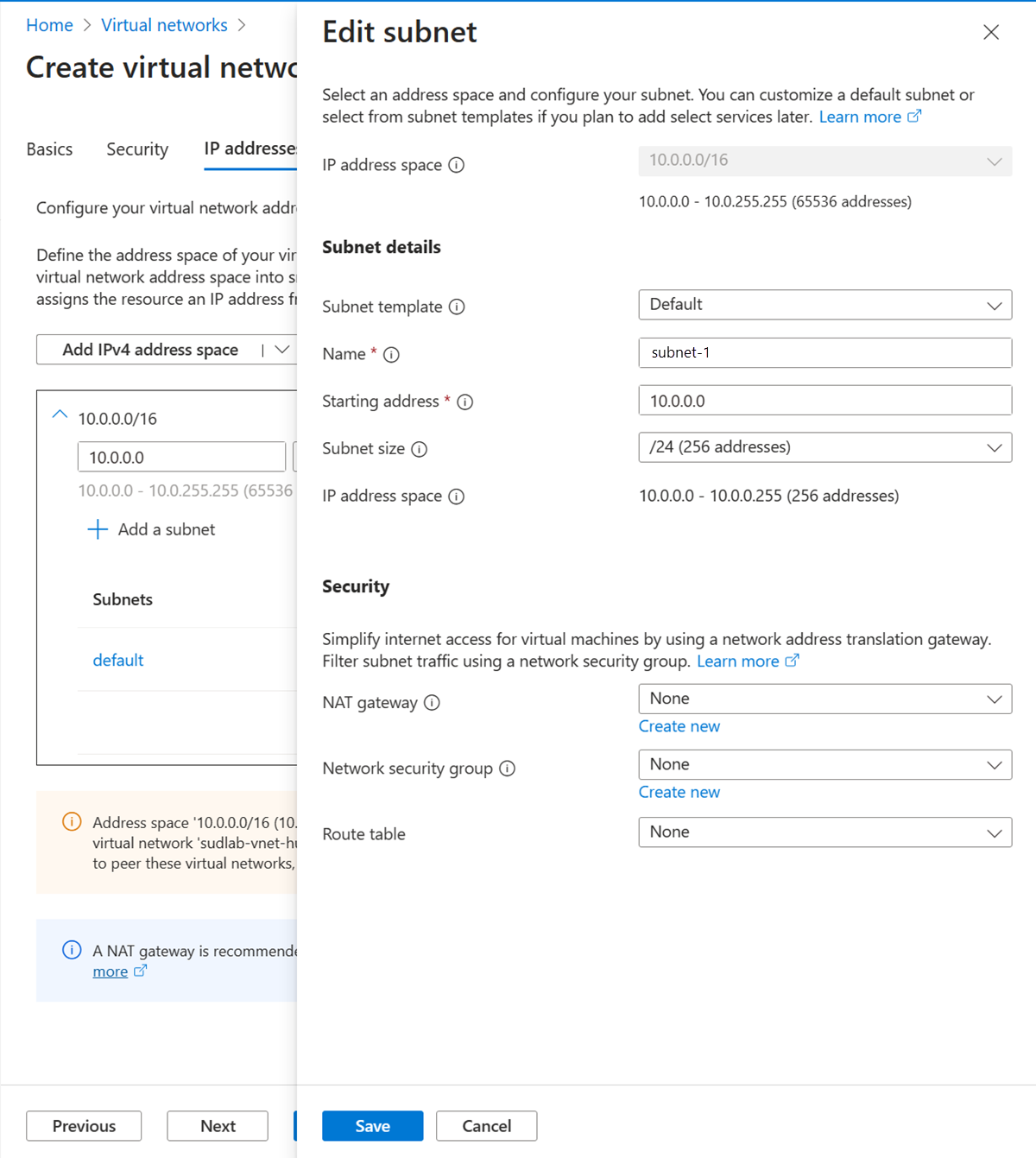
在“子网”的地址空间框中,选择“默认”子网。
在编辑子网中,输入或选择以下信息:
| 设置 |
值 |
| 子网名称 |
输入“subnet-1”。 |
| 子网地址范围 |
输入“10.0.0.0/24”。 |
选择“保存”。
选择屏幕底部的查看 + 创建,然后在验证通过时选择创建。
首先使用 New-AzResourceGroup 针对本文中创建的所有资源创建一个资源组。 以下示例在 westus2 位置创建了一个资源组:
$rg = @{
ResourceGroupName = "test-rg"
Location = "westus2"
}
New-AzResourceGroup @rg
使用 New-AzVirtualNetwork 创建虚拟网络。 以下示例创建了名为 vnet-1 的虚拟网络:
$vnet = @{
ResourceGroupName = "test-rg"
Location = "westus2"
Name = "vnet-1"
AddressPrefix = "10.0.0.0/16"
}
$virtualNetwork = New-AzVirtualNetwork @vnet
使用 New-AzVirtualNetworkSubnetConfig 创建子网配置,然后使用 Set-AzVirtualNetwork 将子网配置写入虚拟网络。 以下示例将名为 subnet-1 的子网添加到虚拟网络,并将 nsg-1 网络安全组关联到该虚拟网络:
$subnet = @{
Name = "subnet-1"
VirtualNetwork = $virtualNetwork
AddressPrefix = "10.0.0.0/24"
}
Add-AzVirtualNetworkSubnetConfig @subnet
$virtualNetwork | Set-AzVirtualNetwork
首先使用 az group create 针对本文中创建的所有资源创建一个资源组。 以下示例在 westus2 位置创建了一个资源组:
az group create \
--name test-rg \
--location westus2
使用 az network vnet create 创建虚拟网络。 以下示例创建了名为 vnet-1 的虚拟网络:
az network vnet create \
--name vnet-1 \
--resource-group test-rg \
--address-prefixes 10.0.0.0/16
使用 az network vnet subnet create 将子网添加到虚拟网络。 以下示例将名为 subnet-1 的子网添加到虚拟网络,并将 nsg-1 网络安全组关联到该虚拟网络:
az network vnet subnet create \
--vnet-name vnet-1 \
--resource-group test-rg \
--name subnet-1 \
--address-prefix 10.0.0.0/24
在门户顶部的搜索框中,输入应用程序安全组。 在搜索结果中选择“应用程序安全组”。
选择+ 创建。
在“创建应用程序安全组”的“基本信息”选项卡中,输入或选择以下信息:
| 设置 |
价值 |
| 项目详细信息 |
|
| 订阅 |
选择订阅。 |
| 资源组 |
选择“test-rg”。 |
| 实例详细信息 |
|
| 名称 |
输入“asg-web”。 |
| 区域 |
选择“(亚太)中国北部 2”。 |
选择“查看 + 创建”。
选择+ 新建。
重复上述步骤并指定以下值:
| 设置 |
价值 |
| 项目详细信息 |
|
| 订阅 |
选择订阅。 |
| 资源组 |
选择test-rg。 |
| 实例详细信息 |
|
| 名称 |
输入“asg-mgmt”。 |
| 区域 |
选择“(亚太)中国北部 2”。 |
选择“查看 + 创建”。
选择“创建”。
使用 New-AzApplicationSecurityGroup 创建应用程序安全组。 使用应用程序安全组可以分组具有类似端口筛选要求的服务器。 以下示例创建两个应用程序安全组。
$web = @{
ResourceGroupName = "test-rg"
Name = "asg-web"
Location = "chinanorth2"
}
$webAsg = New-AzApplicationSecurityGroup @web
$mgmt = @{
ResourceGroupName = "test-rg"
Name = "asg-mgmt"
Location = "chinanorth2"
}
$mgmtAsg = New-AzApplicationSecurityGroup @mgmt
使用 az network asg create 创建应用程序安全组。 使用应用程序安全组可以分组具有类似端口筛选要求的服务器。 以下示例创建两个应用程序安全组。
az network asg create \
--resource-group test-rg \
--name asg-web \
--location chinanorth2
az network asg create \
--resource-group test-rg \
--name asg-mgmt \
--location chinanorth2
在门户顶部的搜索框中,输入“网络安全组”。 在搜索结果中选择“网络安全组”。
选择nsg-1。
在nsg-1的设置部分选择子网。
在“子网”页中,选择“+ 关联”:
在“关联子网”下,为“虚拟网络”选择“vnet-1 (test-rg)”。
为“子网”选择“subnet-1”,然后选择“确定”。
使用 Get-AzVirtualNetwork 检索虚拟网络对象,然后使用 Set-AzVirtualNetworkSubnetConfig 将网络安全组与子网相关联。 以下示例检索虚拟网络对象并更新子网配置以关联网络安全组:
# Retrieve the virtual network
$vnet = Get-AzVirtualNetwork -Name "vnet-1" -ResourceGroupName "test-rg"
# Update the subnet configuration to associate the network security group
$subnetConfigParams = @{
VirtualNetwork = $vnet
Name = "subnet-1"
AddressPrefix = $vnet.Subnets[0].AddressPrefix
NetworkSecurityGroup = Get-AzNetworkSecurityGroup -Name "nsg-1" -ResourceGroupName "test-rg"
}
Set-AzVirtualNetworkSubnetConfig @subnetConfigParams
# Update the virtual network with the new subnet configuration
$vnet | Set-AzVirtualNetwork
使用 az network vnet subnet update 将网络安全组与子网相关联。 以下示例将 nsg-1 网络安全组与 subnet-1 子网相关联:
az network vnet subnet update \
--resource-group test-rg \
--vnet-name vnet-1 \
--name subnet-1 \
--network-security-group nsg-1
从 nsg-1 的“设置”部分选择“入站安全规则”。
在“入站安全规则”页中,选择“+ 添加”。
创建一项允许端口 80 和 443 与 asg-web 应用程序安全组通信的安全规则。 在“添加入站安全规则”中,输入或选择以下信息:
| 设置 |
值 |
| 源 |
保留默认值“任意”。 |
| 源端口范围 |
保留默认值(*)。 |
| 目标 |
选择“应用程序安全组”。 |
| 目标应用程序安全组 |
选择“asg-web”。 |
| 服务 |
保留"自定义"的默认值。 |
| 目标端口范围 |
输入“80,443”。 |
| 协议 |
选择TCP。 |
| 行动 |
保留默认值“允许”。 |
| 优先级 |
保留默认值“100”。 |
| 名称 |
输入“allow-web-all”。 |
选择 添加 。
使用以下信息完成前面的步骤:
| 设置 |
值 |
| 源 |
保留默认值“任意”。 |
| 源端口范围 |
请保留默认选项(*)。 |
| 目标 |
选择“应用程序安全组”。 |
| 目标应用程序安全组 |
选择“asg-mgmt”。 |
| 服务 |
选择 RDP。 |
| 行动 |
保留默认值“允许”。 |
| 优先级 |
保留默认值“110”。 |
| 名称 |
输入“allow-rdp-all”。 |
选择 添加 。
注意
在本文中,将在 Internet 上为分配给“asg-mgmt”应用程序安全组的 VM 公开 RDP(端口 3389)。
在生产环境中,建议使用 VPN、专用网络连接或 Azure Bastion 来连接到要管理的 Azure 资源,而不要向 Internet 公开端口 3389。
有关 Azure Bastion 的详细信息,请参阅什么是 Azure Bastion?。
使用 New-AzNetworkSecurityRuleConfig 创建安全规则。 以下示例创建了一个规则,该规则允许通过端口 80 和 443 将来自 Internet 的入站流量发往 asg-web 应用程序安全组:
$webAsgParams = @{
Name = "asg-web"
ResourceGroupName = "test-rg"
}
$webAsg = Get-AzApplicationSecurityGroup @webAsgParams
$webRuleParams = @{
Name = "Allow-Web-All"
Access = "Allow"
Protocol = "Tcp"
Direction = "Inbound"
Priority = 100
SourceAddressPrefix = "Internet"
SourcePortRange = "*"
DestinationApplicationSecurityGroupId = $webAsg.id
DestinationPortRange = 80,443
}
$webRule = New-AzNetworkSecurityRuleConfig @webRuleParams
以下示例创建了一个规则,该规则允许通过端口 3389 将来自 Internet 的入站流量发往 asg-mgmt 应用程序安全组:
$mgmtAsgParams = @{
Name = "asg-mgmt"
ResourceGroupName = "test-rg"
}
$mgmtAsg = Get-AzApplicationSecurityGroup @mgmtAsgParams
$mgmtRuleParams = @{
Name = "Allow-RDP-All"
Access = "Allow"
Protocol = "Tcp"
Direction = "Inbound"
Priority = 110
SourceAddressPrefix = "Internet"
SourcePortRange = "*"
DestinationApplicationSecurityGroupId = $mgmtAsg.id
DestinationPortRange = 3389
}
$mgmtRule = New-AzNetworkSecurityRuleConfig @mgmtRuleParams
使用 Get-AzNetworkSecurityGroup 检索现有网络安全组,然后使用 += 运算符添加新规则。 最后,使用 Set-AzNetworkSecurityGroup 更新网络安全组:
# Retrieve the existing network security group
$nsg = Get-AzNetworkSecurityGroup -Name "nsg-1" -ResourceGroupName "test-rg"
# Add the new rules to the security group
$nsg.SecurityRules += $webRule
$nsg.SecurityRules += $mgmtRule
# Update the network security group with the new rules
Set-AzNetworkSecurityGroup -NetworkSecurityGroup $nsg
注意
在本文中,将在 Internet 上为分配给“asg-mgmt”应用程序安全组的 VM 公开 RDP(端口 3389)。
在生产环境中,建议使用 VPN、专用网络连接或 Azure Bastion 来连接到要管理的 Azure 资源,而不要向 Internet 公开端口 3389。
有关 Azure Bastion 的详细信息,请参阅什么是 Azure Bastion?。
使用 az network nsg rule create 创建安全规则。 以下示例创建了一个规则,该规则允许通过端口 80 和 443 将来自 Internet 的入站流量发往 asg-web 应用程序安全组:
az network nsg rule create \
--resource-group test-rg \
--nsg-name nsg-1 \
--name Allow-Web-All \
--access Allow \
--protocol Tcp \
--direction Inbound \
--priority 100 \
--source-address-prefix Internet \
--source-port-range "*" \
--destination-asgs "asg-web" \
--destination-port-range 80 443
以下示例创建了一个规则,该规则允许通过端口 22 将来自 Internet 的入站流量发往 asg-mgmt 应用程序安全组:
az network nsg rule create \
--resource-group test-rg \
--nsg-name nsg-1 \
--name Allow-SSH-All \
--access Allow \
--protocol Tcp \
--direction Inbound \
--priority 110 \
--source-address-prefix Internet \
--source-port-range "*" \
--destination-asgs "asg-mgmt" \
--destination-port-range 22
注意
在本文中,将在 Internet 上为分配给“asg-mgmt”应用程序安全组的 VM 公开 SSH(端口 22)。
在生产环境中,建议使用 VPN、专用网络连接或 Azure Bastion 来连接到要管理的 Azure 资源,而不要向 Internet 公开端口 22。
有关 Azure Bastion 的详细信息,请参阅什么是 Azure Bastion?。
在门户中,搜索并选择虚拟机。
在虚拟机中,选择+ 创建,然后选择Azure 虚拟机。
在创建虚拟机的基本信息选项卡中,输入或选择以下信息 :
| 设置 |
值 |
| 项目详细信息 |
|
| 订阅 |
选择订阅。 |
| 资源组 |
选择test-rg。 |
| 实例详细信息 |
|
| 虚拟机名称 |
输入“vm-web”。 |
| 区域 |
选择“(亚太)中国北部 2”。 |
| 可用性选项 |
保留默认值不需要基础结构冗余。 |
| 安全类型 |
选择“标准”。 |
| 映像 |
选择“Windows Server 2022 Datacenter - x64 Gen2”。 |
| Azure Spot 实例 |
保留默认值“未选中”。 |
| 大小 |
选择大小。 |
| 管理员帐户 |
|
| 用户名 |
输入用户名。 |
| 密码 |
输入密码。 |
| 确认密码 |
重新输入密码。 |
| 入站端口规则 |
|
| 选择入站端口 |
选择“无”。 |
选择“下一步: 磁盘”,然后选择“下一步: 网络”。
在“网络”中,输入或选择以下信息:
| 设置 |
价值 |
| 网络接口 |
|
| 虚拟网络 |
选择“vnet-1”。 |
| 子网 |
选择“subnet-1 (10.0.0.0/24)”。 |
| 公共 IP |
保留默认值“新建公共 IP”。 |
| NIC 网络安全组 |
选择“无”。 |
选择“查看 + 创建”选项卡,或选择页面底部的“查看 + 创建”按钮 。
选择“创建”。 部署 VM 可能需要几分钟时间。
重复上述步骤以创建名为 vm-mgmt 的第二个虚拟机。
在创建 VM 之前,使用 Get-AzVirtualNetwork 检索包含子网的虚拟网络对象:
$virtualNetworkParams = @{
Name = "vnet-1"
ResourceGroupName = "test-rg"
}
$virtualNetwork = Get-AzVirtualNetwork @virtualNetworkParams
使用 New-AzPublicIpAddress 为每个 VM 创建一个公共 IP 地址:
$publicIpWebParams = @{
AllocationMethod = "Static"
ResourceGroupName = "test-rg"
Location = "chinanorth2"
Name = "public-ip-vm-web"
}
$publicIpWeb = New-AzPublicIpAddress @publicIpWebParams
$publicIpMgmtParams = @{
AllocationMethod = "Static"
ResourceGroupName = "test-rg"
Location = "chinanorth2"
Name = "public-ip-vm-mgmt"
}
$publicIpMgmt = New-AzPublicIpAddress @publicIpMgmtParams
使用 New-AzNetworkInterface 创建两个网络接口,并将公共 IP 地址分配给网络接口。 以下示例创建一个网络接口,将 public-ip-vm-web 公共 IP 地址关联到该网络接口。
$webNicParams = @{
Location = "chinanorth2"
Name = "vm-web-nic"
ResourceGroupName = "test-rg"
SubnetId = $virtualNetwork.Subnets[0].Id
PublicIpAddressId = $publicIpWeb.Id
}
$webNic = New-AzNetworkInterface @webNicParams
以下示例创建一个网络接口,将 public-ip-vm-mgmt 公共 IP 地址关联到该网络接口。
$mgmtNicParams = @{
Location = "chinanorth2"
Name = "vm-mgmt-nic"
ResourceGroupName = "test-rg"
SubnetId = $virtualNetwork.Subnets[0].Id
PublicIpAddressId = $publicIpMgmt.Id
}
$mgmtNic = New-AzNetworkInterface @mgmtNicParams
在虚拟网络中创建两个 VM,以便在后续步骤中可以验证流量筛选。
使用 New-AzVMConfig 创建 VM 配置,然后使用 New-AzVM 创建 VM。 以下示例创建了充当 Web 服务器的 VM。 -AsJob 选项会在后台创建 VM,因此可继续执行下一步:
# Create user object
$cred = Get-Credential -Message "Enter a username and password for the virtual machine."
$webVmConfigParams = @{
VMName = "vm-web"
VMSize = "Standard_DS1_V2"
}
$vmOSParams = @{
ComputerName = "vm-web"
Credential = $cred
}
$vmImageParams = @{
PublisherName = "MicrosoftWindowsServer"
Offer = "WindowsServer"
Skus = "2022-Datacenter"
Version = "latest"
}
$webVmConfig = New-AzVMConfig @webVmConfigParams | Set-AzVMOperatingSystem -Windows @vmOSParams | Set-AzVMSourceImage @vmImageParams | Add-AzVMNetworkInterface -Id $webNic.Id
$webVmParams = @{
ResourceGroupName = "test-rg"
Location = "chinanorth2"
VM = $webVmConfig
}
New-AzVM @webVmParams -AsJob
创建充当管理服务器的 VM:
# Create user object
$cred = Get-Credential -Message "Enter a username and password for the virtual machine."
$webVmConfigParams = @{
VMName = "vm-mgmt"
VMSize = "Standard_DS1_V2"
}
$vmOSParams = @{
ComputerName = "vm-mgmt"
Credential = $cred
}
$vmImageParams = @{
PublisherName = "MicrosoftWindowsServer"
Offer = "WindowsServer"
Skus = "2022-Datacenter"
Version = "latest"
}
$mgmtVmConfig = New-AzVMConfig @webVmConfigParams | Set-AzVMOperatingSystem -Windows @vmOSParams | Set-AzVMSourceImage @vmImageParams | Add-AzVMNetworkInterface -Id $mgmtNic.Id
$mgmtVmParams = @{
ResourceGroupName = "test-rg"
Location = "chinanorth2"
VM = $mgmtVmConfig
}
New-AzVM @mgmtVmParams
创建虚拟机需花费几分钟的时间。 在 Azure 完成创建 VM 之前,请不要继续下一步。
在虚拟网络中创建两个 VM,以便在后续步骤中可以验证流量筛选。
使用 az vm create 创建 VM。 以下示例创建了充当 Web 服务器的 VM。 指定 --nsg "" 选项可防止 Azure 为创建 VM 时创建的网络接口创建默认的网络安全组。 该命令提示你为 VM 创建密码。 本例中不使用 SSH 密钥,以方便本文后面的步骤。 在生产环境中,请使用 SSH 密钥增强安全性。
az vm create \
--resource-group test-rg \
--name vm-web \
--image Ubuntu2204 \
--vnet-name vnet-1 \
--subnet subnet-1 \
--nsg "" \
--admin-username azureuser \
--authentication-type password \
--assign-identity
创建 VM 需要几分钟时间。 创建 VM 后,将返回以下示例所示的输出:
{
"fqdns": "",
"id": "/subscriptions/00000000-0000-0000-0000-000000000000/resourceGroups/test-rg/providers/Microsoft.Compute/virtualMachines/vm-web",
"location": "chinanorth2",
"macAddress": "00-0D-3A-23-9A-49",
"powerState": "VM running",
"privateIpAddress": "10.0.0.4",
"publicIpAddress": "203.0.113.24",
"resourceGroup": "test-rg"
}
使用 az vm create 创建 VM。 以下示例创建了一个用作管理服务器的 VM。
以下示例将创建 VM 并添加用户帐户。 --generate-ssh-keys 参数会导致 CLI 在 ~/.ssh 中查找可用的 ssh 密钥。 如果找到一个,则使用此密钥。 否则,将会生成一个密钥并存储在 ~/.ssh 中。 最后,我们将部署最新的 Ubuntu 22.04 映像。
az vm create \
--resource-group test-rg \
--name vm-mgmt \
--image Ubuntu2204 \
--vnet-name vnet-1 \
--subnet subnet-1 \
--nsg "" \
--admin-username azureuser \
--generate-ssh-keys \
--assign-identity
创建 VM 需要几分钟时间。 在 Azure 完成创建 VM 之前,请不要继续下一步。
当你创建 VM 时,Azure 已经为每个 VM 创建了一个网络接口,并已将该接口附加到 VM。
请将每个 VM 的网络接口添加到前面创建的应用程序安全组:
在门户顶部的搜索框中,输入“虚拟机”。 在搜索结果中选择“虚拟机”,然后选择“vm-web”。
从 vm-web 的“网络”部分选择“应用程序安全组”。
选择“添加应用程序安全组”,然后在“添加应用程序安全组”选项卡中,选择 asg-web。 最后选择“添加” 。
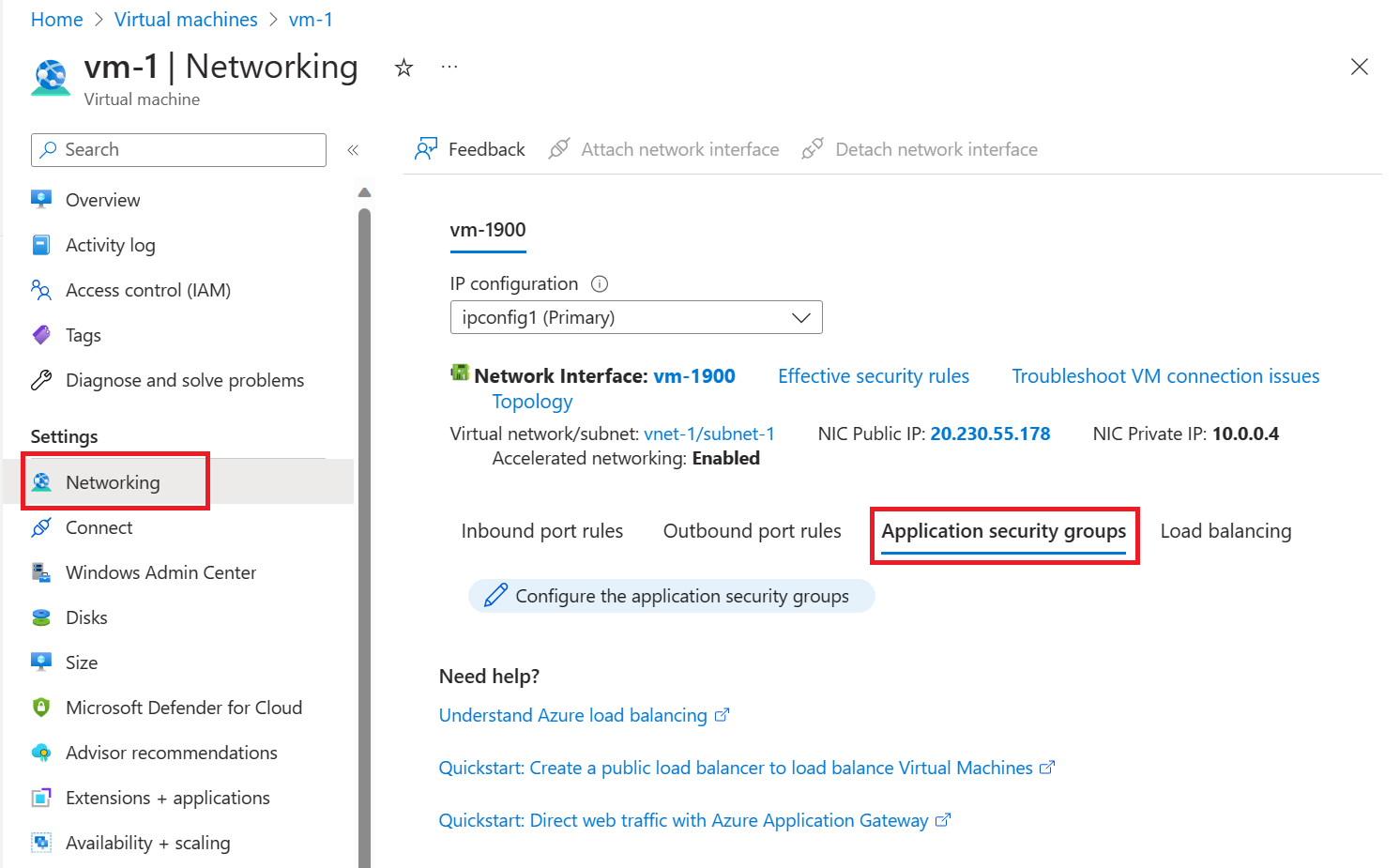
对 vm-mgmt 重复前面的步骤,在“添加应用程序安全组”选项卡中选择“asg-mgmt”。
使用 Get-AzNetworkInterface 检索虚拟机的网络接口,然后使用 Get-AzApplicationSecurityGroup 检索应用程序安全组。 最后,使用 Set-AzNetworkInterface 将应用程序安全组与网络接口相关联。 以下示例将 asg-web 应用程序安全组与 vm-web-nic 网络接口相关联:
$params1 = @{
Name = "vm-web-nic"
ResourceGroupName = "test-rg"
}
$nic = Get-AzNetworkInterface @params1
$params2 = @{
Name = "asg-web"
ResourceGroupName = "test-rg"
}
$asg = Get-AzApplicationSecurityGroup @params2
$nic.IpConfigurations[0].ApplicationSecurityGroups = @($asg)
$params3 = @{
NetworkInterface = $nic
}
Set-AzNetworkInterface @params3
重复该命令,以将 asg-mgmt 应用程序安全组与 vm-mgmt-nic 网络接口相关联。
$params1 = @{
Name = "vm-mgmt-nic"
ResourceGroupName = "test-rg"
}
$nic = Get-AzNetworkInterface @params1
$params2 = @{
Name = "asg-mgmt"
ResourceGroupName = "test-rg"
}
$asg = Get-AzApplicationSecurityGroup @params2
$nic.IpConfigurations[0].ApplicationSecurityGroups = @($asg)
$params3 = @{
NetworkInterface = $nic
}
Set-AzNetworkInterface @params3
使用 az network nic update 将网络接口与应用程序安全组相关联。 以下示例将 asg-web 应用程序安全组与 vm-web-nic 网络接口相关联:
# Retrieve the network interface name associated with the virtual machine
nic_name=$(az vm show --resource-group test-rg --name vm-web --query 'networkProfile.networkInterfaces[0].id' -o tsv | xargs basename)
# Associate the application security group with the network interface
az network nic ip-config update \
--name ipconfigvm-web \
--nic-name $nic_name \
--resource-group test-rg \
--application-security-groups asg-web
重复该命令,以将 asg-mgmt 应用程序安全组与 vm-mgmt-nic 网络接口相关联。
# Retrieve the network interface name associated with the virtual machine
nic_name=$(az vm show --resource-group test-rg --name vm-mgmt --query 'networkProfile.networkInterfaces[0].id' -o tsv | xargs basename)
# Associate the application security group with the network interface
az network nic ip-config update \
--name ipconfigvm-mgmt \
--nic-name $nic_name \
--resource-group test-rg \
--application-security-groups asg-mgmt
在门户顶部的搜索框中,输入“虚拟机”。 在搜索结果中,选择“虚拟机”。
选择“vm-mgmt”。
在“概述”页上选择“连接”按钮,然后选择“本地 RDP”。
选择“下载 RDP 文件”。
打开下载的 rdp 文件,然后选择“连接”。 输入在创建 VM 时指定的用户名和密码。
选择“确定”。
在连接过程中可能会收到证书警告。 如果收到警告,请选择“是”或“继续”以继续连接 。
连接会成功,因为允许通过端口 3389 将来自 Internet 的入站流量发送到 asg-mgmt 应用程序安全组。
vm-mgmt 的网络接口与 asg-mgmt 应用程序安全组相关联,并允许连接。
在 vm-mgmt 上打开一个 PowerShell 会话。使用以下命令连接到 vm-web:
mstsc /v:vm-web
从 vm-mgmt 到 vm-web 的 RDP 连接会成功,因为同一网络中的虚拟机默认情况下可以通过任何端口相互通信。
不能创建从 Internet 到 vm-web 虚拟机的 RDP 连接。 “asg-web”的安全规则阻止从 Internet 连接到端口 3389 入站。 默认情况下,拒绝来自 Internet 的入站流量到所有资源。
若要在 vm-web 虚拟机上安装 Microsoft IIS,请通过 PowerShell 会话在 vm-web 虚拟机上输入以下命令:
Install-WindowsFeature -name Web-Server -IncludeManagementTools
完成 IIS 安装后,断开与 vm-web 虚拟机的连接,这会使您停留在 vm-mgmt 虚拟机的远程桌面连接中。
断开与 vm-mgmt VM 的连接。
在门户搜索框中搜索“vm-web”。
在“vm-web”的“概述”页上,记下 VM 的“公共 IP 地址”。 以下示例中显示的地址为 203.0.113.103。 你的地址不同:
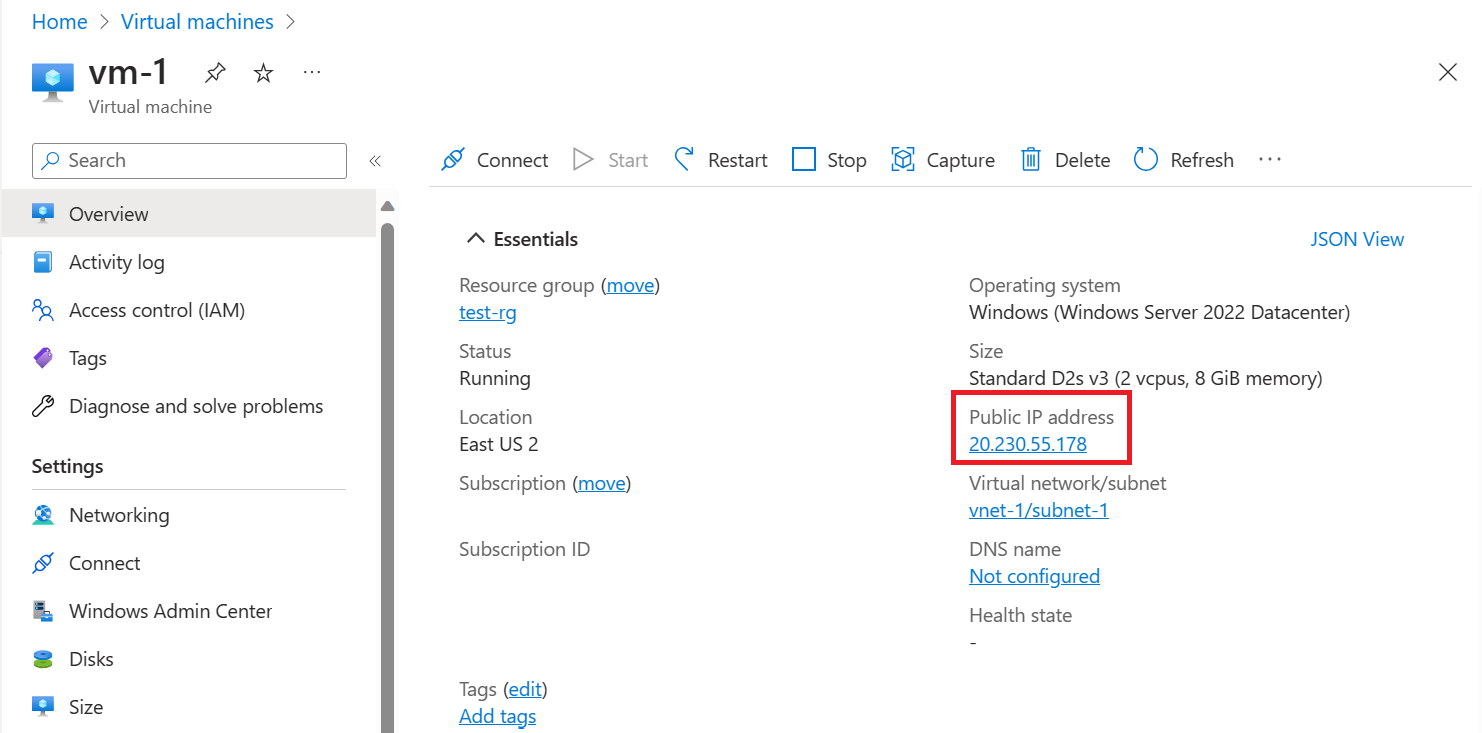
若要确认可以从 Internet 访问 vm-web Web 服务器,请在计算机上打开 Internet 浏览器并浏览到 http://<public-ip-address-from-previous-step>。
你将看到 IIS 默认页,因为允许通过端口 80 将来自 Internet 的入站流量发送到 asg-web 应用程序安全组。
为 vm-web 附加的网络接口与 asg-web 应用程序安全组相关联,并允许连接。
使用 Get-AzPublicIpAddress 返回 VM 的公共 IP 地址。 以下示例返回 vm-mgmt VM 的公共 IP 地址:
$params = @{
Name = "public-ip-vm-mgmt"
ResourceGroupName = "test-rg"
}
$publicIP = Get-AzPublicIpAddress @params | Select IpAddress
从本地计算机使用以下命令创建与 vm-mgmt VM 的远程桌面会话。
mstsc /v:$publicIP
输入在创建 VM 时指定的用户名和密码(可能需要选择“更多选择”,然后选择“使用其他帐户”,以便指定在创建 VM 时输入的凭据),然后选择“确定”。 你可能会在登录过程中收到证书警告。 选择“是”以继续进行连接。
连接成功。 允许从 Internet 到 asg-mgmt 应用程序安全组的入站端口 3389 流量。 附加到 vm-mgmt VM 的网络接口在此组中。
在 PowerShell 中使用以下命令,从 vm-mgmt VM 来与 vm-web VM 建立远程桌面连接:
mstsc /v:vm-web
连接将会成功,因为每个网络安全组中的默认安全规则允许通过虚拟网络中所有 IP 地址之间的所有端口发送流量。 由于 asg-web 的安全规则不允许来自互联网的入站访问通过端口 3389,因此无法从互联网创建到 vm-web VM 的远程桌面连接。
在 PowerShell 中使用以下命令将 Microsoft IIS 安装到 vm-web VM 上:
Install-WindowsFeature -name Web-Server -IncludeManagementTools
完成 IIS 安装后,从 vm-web VM 断开连接,从而保留 vm-mgmt 远程桌面连接。 若要查看 IIS 欢迎屏幕,请打开 Internet 浏览器并访问 http://vm-web.
断开与 vm-mgmt VM 的连接。
在你的计算机上的 PowerShell 中输入以下命令,以检索 vm-web 服务器的公共 IP 地址:
$params = @{
Name = "public-ip-vm-web"
ResourceGroupName = "test-rg"
}
Get-AzPublicIpAddress @params | Select IpAddress
若要确认可以从 Azure 外部访问 vm-web Web 服务器,请在计算机上打开 Internet 浏览器并浏览到 http://<public-ip-address-from-previous-step>。 连接成功。 允许从 Internet 到 asg-web 应用程序安全组的入站端口 80 流量。 附加到 vm-web VM 的网络接口在此组中。
使用所选的 SSH 客户端连接到之前创建的 VM。 例如,可从命令行接口(如 适用于 Linux 的 Windows 子系统)使用以下命令创建与 vm-mgmt VM 的 SSH 会话。 可使用 Microsoft Entra ID 凭据登录到虚拟机,也可使用用于创建 VM 的 SSH 密钥。 在以下示例中,我们使用 SSH 密钥登录到管理 VM,然后使用密码从管理 VM 登录到 Web VM。
有关如何通过 SSH 连接到 Linux VM 并使用 Microsoft Entra ID 登录的详细信息,请参阅使用 Microsoft Entra ID 和 OpenSSH 登录到 Azure 中的 Linux 虚拟机。
存储 VM 的 IP 地址,以通过 SSH 进行连接
运行以下命令以将 VM 的 IP 地址存储为环境变量:
export IP_ADDRESS=$(az vm show --show-details --resource-group test-rg --name vm-mgmt --query publicIps --output tsv)
ssh -o StrictHostKeyChecking=no azureuser@$IP_ADDRESS
连接成功,因为附加到 vm-mgmt VM 的网络接口位于 asg-mgmt 应用程序安全组中,该安全组允许来自 Internet 的端口 22 入站流量。
使用以下命令通过 SSH 从 vm-mgmt VM 连接到 vm-web VM:
ssh -o StrictHostKeyChecking=no azureuser@vm-web
连接将会成功,因为每个网络安全组中的默认安全规则允许通过虚拟网络中所有 IP 地址之间的所有端口发送流量。 无法通过 SSH 从 Internet 连接到 vm-web VM,因为 asg-web 的安全规则不允许通过端口 22 发送来自 Internet 的入站流量。
使用以下命令在 vm-web VM 上安装 nginx Web 服务器:
# Update package source
sudo apt-get -y update
# Install NGINX
sudo apt-get -y install nginx
由于默认安全规则允许所有出站流量发送到 Internet,因此允许 vm-web VM 向 Internet 发送出站流量以检索 nginx。 退出 vm-web SSH 会话,这会使你留在 username@vm-mgmt:~$ VM 的 提示符处。 若要从 vm-web VM 检索 nginx 欢迎屏幕,请输入以下命令:
curl vm-web
退出登录 vm-mgmt VM。 若要确认是否可以从 Azure 外部访问 vm-web Web 服务器,请在自己的计算机上输入 curl <publicIpAddress>。 连接之所以成功,是因为 asg-web 应用程序安全组(附加到 vm-web VM 的网络接口所在的安全组)允许来自 Internet 的端口 80 入站流量。