为基于用户和组的访问配置 P2S - Microsoft Entra 身份验证
使用 Microsoft Entra ID 作为 P2S 的身份验证方法时,可以配置 P2S 以允许不同的用户和组进行不同的访问。 如果你希望一组不同的用户能够连接到不同的 VPN 网关,可以在 AD 中注册多个应用,并将这些应用链接到不同的 VPN 网关。 本文帮助你设置 Microsoft Entra 租户以进行 P2S Microsoft Entra 身份验证,并在 Microsoft Entra ID 中创建和注册多个应用,以允许不同的用户和组进行不同的访问。 有关点到站点 VPN 协议和身份验证的详细信息,请参阅关于点到站点 VPN。
注意
Microsoft Entra 身份验证仅支持 OpenVPN® 协议连接,并且需要 Azure VPN 客户端。
Microsoft Entra 租户
本文中的步骤需要一个 Microsoft Entra 租户。 如果你没有 Microsoft Entra 租户,可以按照创建新租户一文中的步骤创建一个。 创建目录时,请注意以下字段:
- 组织名称
- 初始域名
创建 Microsoft Entra 租户用户
在新建的 Microsoft Entra 租户中创建两个帐户。 有关步骤,请参阅添加新用户或删除用户。
- 全局管理员帐户
- 用户帐户
全局管理员帐户将用于向 Azure VPN 应用注册授权同意。 用户帐户可用于测试 OpenVPN 身份验证。
向这些帐户之一分配全局管理员角色。 有关步骤,请参阅向具有 Microsoft Entra ID 的用户分配管理员和非管理员角色。
为 Azure VPN 应用程序授权
以拥有“全局管理员”角色的用户身份登录到 Azure 门户。
下一步,向组织授予管理员同意。 这样,Azure VPN 应用程序就能够登录和读取用户配置文件了。 在浏览器的地址栏中复制并粘贴与部署位置相关的 URL:
由世纪互联运营的 Microsoft Azure
https://login.chinacloudapi.cn/common/oauth2/authorize?client_id=49f817b6-84ae-4cc0-928c-73f27289b3aa&response_type=code&redirect_uri=https://portal.azure.cn&nonce=1234&prompt=admin_consent注意
如果你使用对于 Microsoft Entra 租户并非本机的全局管理员帐户来提供同意,请在 URL 中将“common”替换为 Microsoft Entra 租户 ID。 在某些其他情况下,可能还需要将“common”替换为租户 ID。 有关查找租户 ID 的帮助,请参阅如何查找 Microsoft Entra 租户 ID。
如果出现提示,请选择具有全局管理员角色的帐户。
在“请求的权限”页上,选择“接受”。
转到“Microsoft Entra ID”。 在左侧窗格中,单击“企业应用程序”。 随后会列出“Azure VPN”。
注册其他应用程序
在本部分,你可以为各种用户和组注册其他应用程序。 重复这些步骤,以根据安全要求创建所需数量的应用程序。 每个应用程序都将关联到一个 VPN 网关,并且可以有不同的用户集。 只能将一个应用程序关联到一个网关。
添加作用域
在 Azure 门户中,选择“Microsoft Entra ID”。
在左侧窗格中,选择“应用注册”。
在“应用注册”页面顶部,选择“+ 新建注册”。
在“注册应用程序”页上,输入名称 。 例如 MarketingVPN。 以后随时可以更改此名称。
- 选择所需的“支持的帐户类型”。
- 在页面底部,单击“注册”。
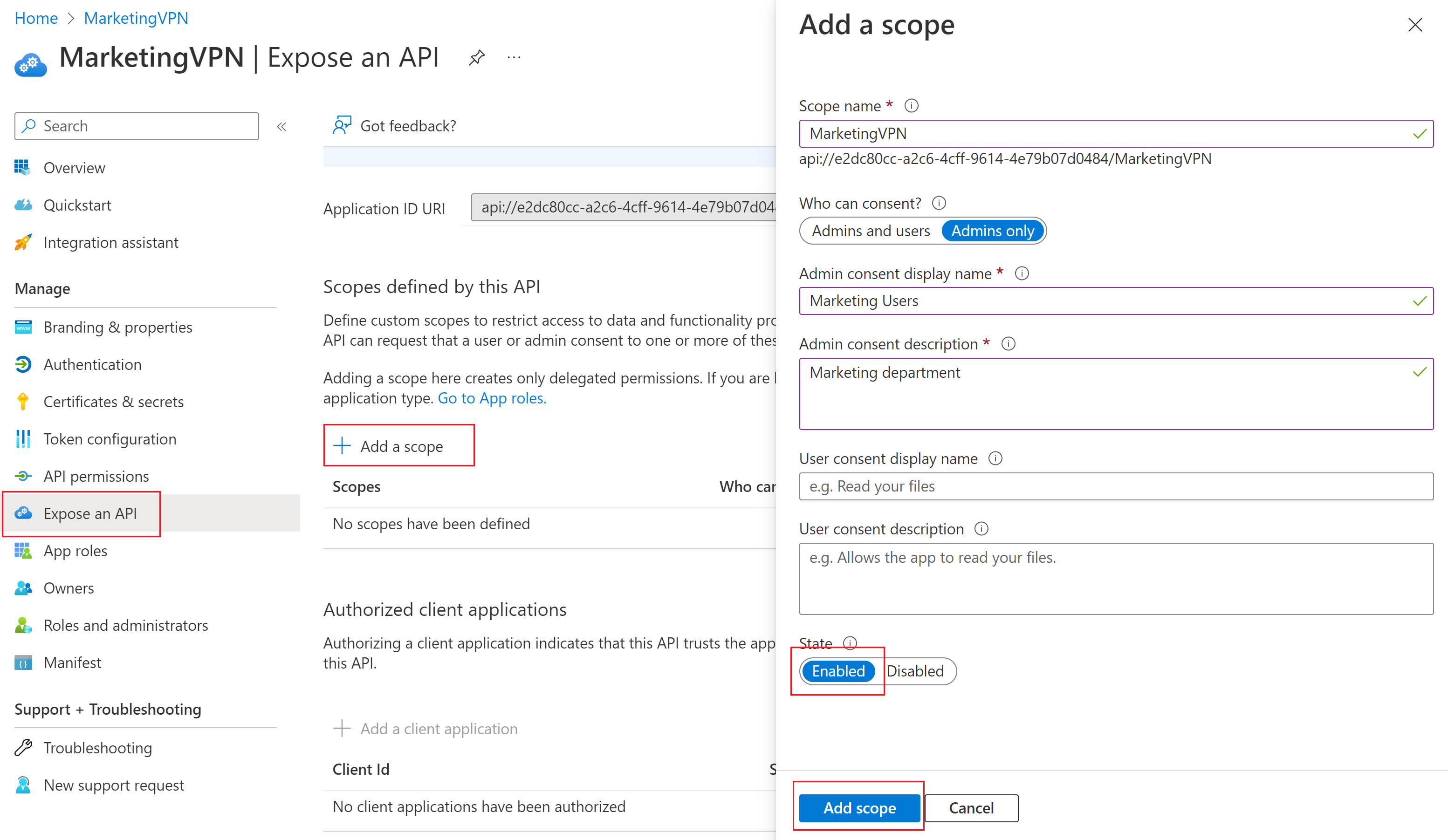
注册新应用后,在左侧窗格中单击“公开 API”。 然后单击“+ 添加范围”。
- 在“添加范围”页上,保留默认的“应用程序 ID URI”。
- 单击“保存并继续”。
页面随后会返回到“添加范围”页。 填写必填字段,确保“状态”为“已启用”。
填写完字段后,单击“添加范围”。
添加客户端应用程序
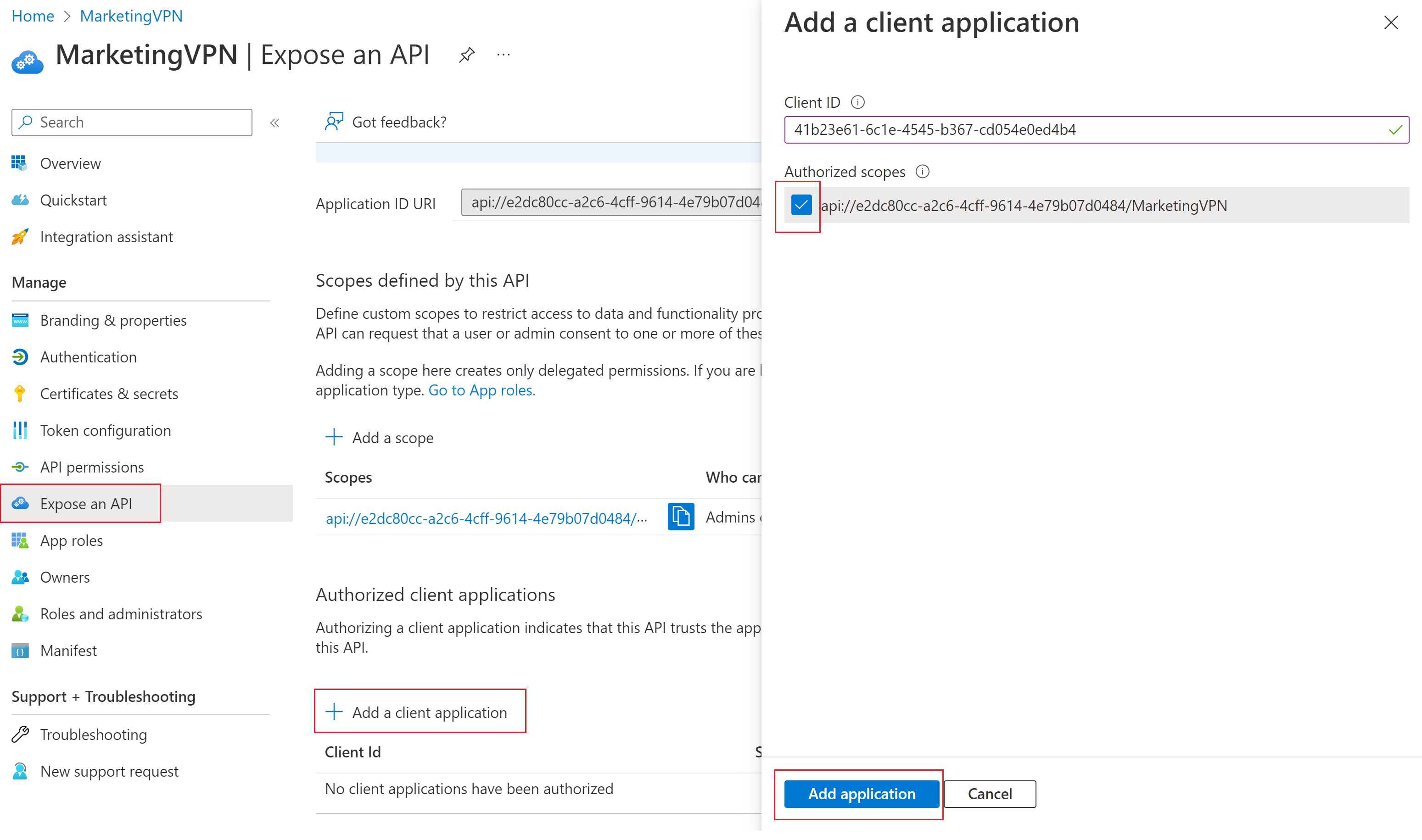
在“公开 API”页上,单击“+ 添加客户端应用程序”。
在“添加客户端应用程序”页上,对于“客户端 ID”,请根据云输入以下值:
- 由世纪互联运营的 Microsoft Azure:
49f817b6-84ae-4cc0-928c-73f27289b3aa
- 由世纪互联运营的 Microsoft Azure:
选中要包含的“已授权范围”对应的复选框。 然后单击“添加应用程序”。
单击“添加应用程序”。
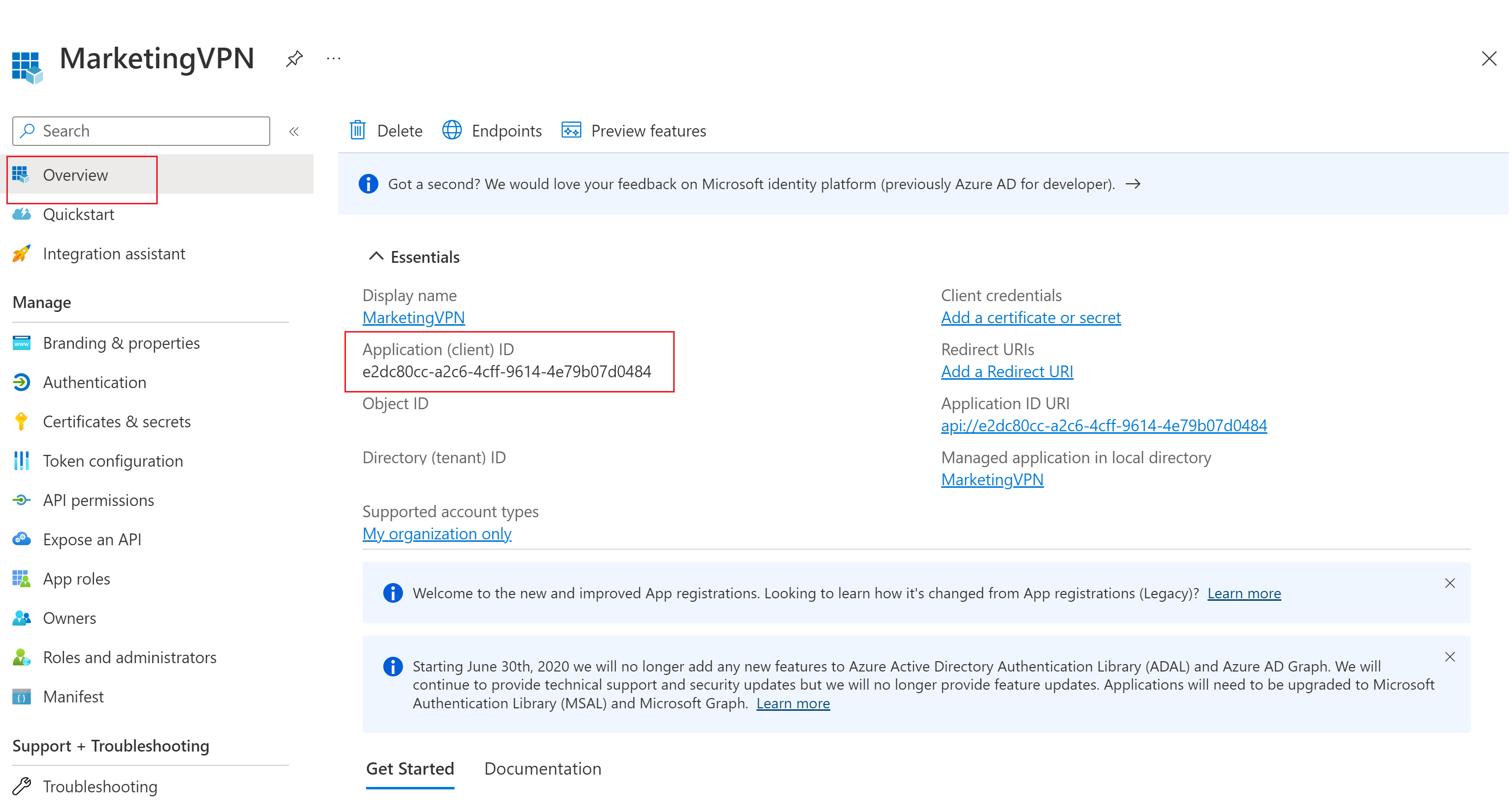
复制“应用程序(客户端) ID”
在 VPN 网关上启用身份验证时,需要输入“应用程序(客户端) ID”值以填写点到站点配置的“受众”值。
将用户分配给应用程序
将用户分配到应用程序。 如果要指定组,则用户必须是组的直接成员。 不支持嵌套组。
- 转到你的 Microsoft Entra ID 并选择“企业应用程序”。
- 在列表中,找到刚刚注册的应用程序并单击以将其打开。
- 单击 “属性”。 在“属性”页上,确认“启用以供用户登录”设置为“是”。 否则,将值更改为“是”。
- 对于“需要分配”,请将值更改为“是”。 有关此设置的详细信息,请参阅应用程序属性。
- 如果已经进行了更改,请单击“保存”以保存设置。
- 在左窗格中,单击“用户和组”。 在“用户和组”页上,单击“+ 添加用户/组”打开“添加分配”页。
- 单击“用户和组”下面的链接打开“用户和组”页。 选择要分配的用户和组,然后单击“选择”。
- 选择用户和组后,单击“分配”。
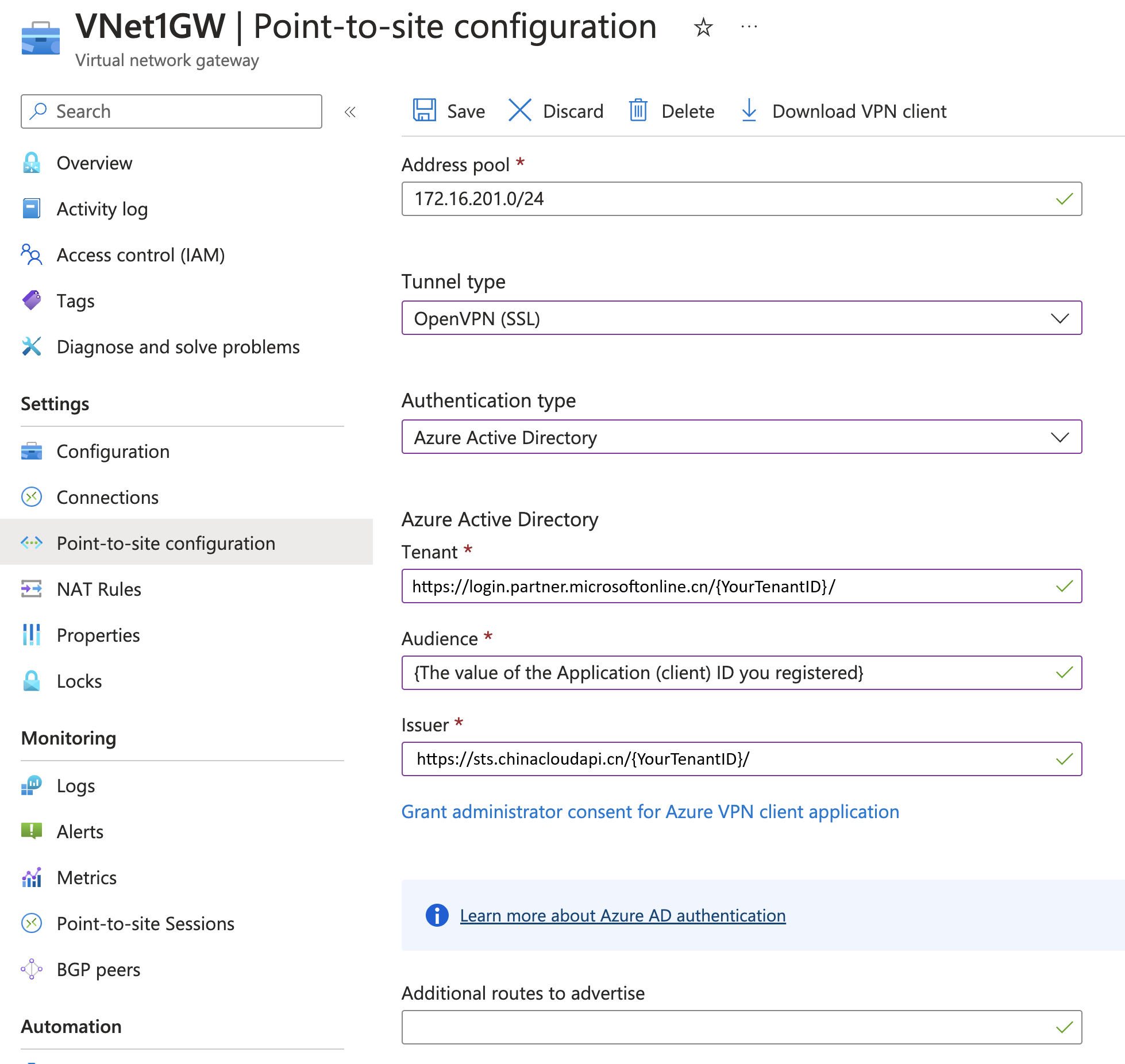
为网关配置身份验证
重要
Azure 门户正在将 Azure Active Directory 字段更新到 Entra。 如果你看到了引用的 Microsoft Entra ID,但尚未在门户中看到这些值,则可以选择 Azure Active Directory 值。
在此步骤中,你将为虚拟网络网关配置 P2S Microsoft Entra 身份验证。
转到虚拟网络网关。 在左侧窗格中,单击“点到站点配置”。
配置以下值:
- 地址池:客户端地址池
- 隧道类型:OpenVPN (SSL)
- 身份验证类型:Microsoft Entra ID
对于“Microsoft Entra ID”值,请根据以下准则指定“租户”、“受众”和“颁发者”值。
- 租户:
https://login.partner.microsoftonline.cn/{TenantID} - 受众 ID:使用在上一部分创建的对应于“应用程序(客户端) ID”的值。 不要将应用程序 ID 用于“Azure VPN”Microsoft Entra 企业应用 - 使用你创建并注册的应用程序 ID。 如果为“Azure VPN”Microsoft Entra 企业应用改用应用程序 ID,则会向所有用户授予对 VPN 网关的访问权限(这是设置访问权限的默认方式),而不是仅向你分配到所创建并注册的应用程序的用户授予访问权限。
- 颁发者:
https://sts.chinacloudapi.cn/{TenantID}对于“颁发者”值,请确保在末尾包含一个尾部 /。
配置设置后,单击页面顶部的“保存”。
下载 Azure VPN 客户端配置文件配置包
在本部分,你将生成并下载 Azure VPN 客户端配置文件配置包。 此包包含可用于在客户端计算机上配置 Azure VPN 客户端配置文件的设置。
在“点到站点配置”页面顶部,单击“下载 VPN 客户端”。 需要几分钟才能生成客户端配置包。
浏览器会指示客户端配置 zip 文件可用。 其名称与网关名称相同。
解压缩已下载的 zip 文件。
浏览到解压缩后的“AzureVPN”文件夹。
记下“azurevpnconfig.xml”文件的位置。 azurevpnconfig.xml 包含 VPN 连接的设置。 还可以将此文件分发给需要通过电子邮件或其他方式建立连接的所有用户。 用户需要有效的 Microsoft Entra 凭据才能成功连接。 有关详细信息,请参阅用于 Microsoft Entra 身份验证的 Azure VPN 客户端配置文件。
后续步骤
- 若要连接到虚拟网络,必须在客户端计算机上配置 Azure VPN 客户端。 请参阅配置 VPN 客户端以建立 P2S VPN 连接。
- 有关常见问题解答,请参阅 VPN 网关常见问题解答的“点到站点”部分。