本文可帮助你使用 PowerShell 创建 Azure VPN 网关。 创建与本地网络的 VPN 连接时使用 VPN 网关。 还可以使用 VPN 网关连接虚拟网络。 有关本文中某些设置的更全面信息,请参阅创建 VPN 网关 - 门户。
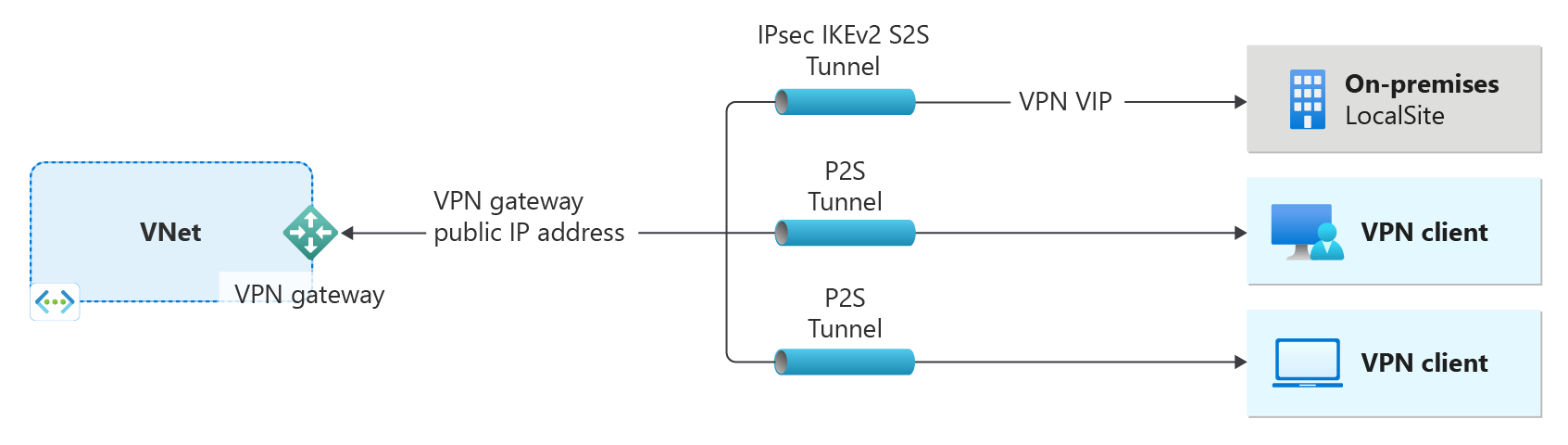
- 关系图左侧显示了使用本文中的步骤创建的虚拟网络和 VPN 网关。
- 你稍后可以添加不同类型的连接,如关系图右侧所示。 例如,可以创建站点到站点连接和点到站点连接。 若要查看可以构建的不同设计体系结构,请参阅 VPN 网关设计。
本文中的步骤使用第 2 代 VpnGw2AZ SKU 创建虚拟网络、子网、网关子网和基于路由的、区域冗余的主动-主动模式 VPN 网关(虚拟网络网关)。 创建网关后,可以配置连接。
- 如果要改用基本 SKU 创建 VPN 网关,请参阅创建基本 SKU VPN 网关。
- 建议尽可能创建主动-主动模式 VPN 网关。 与标准模式 VPN 网关相比,主动-主动模式 VPN 网关可提供更好的可用性和性能。 有关主动-主动网关的详细信息,请参阅关于主动-主动模式网关。
- 有关可用性区域和区域冗余网关的详细信息,请参阅什么是可用性区域?
注意
本文中的步骤使用支持 Azure 可用性区域的网关 SKU“VpnGw2AZ”。 从 2025 年 5 月开始,所有区域都将接受 AZ SKU,无论该区域中是否支持可用性区域。 有关网关 SKU 的详细信息,请参阅《关于网关 SKU》。
开始之前
执行这些步骤需要 Azure 订阅。 如果没有 Azure 订阅,可在开始前创建一个试用帐户。
可以在计算机本地安装并运行 Azure PowerShell cmdlet。 PowerShell 命令经常更新。 如果尚未安装最新版本,说明中指定的值可能会失败。 若要查找计算机上安装的 Azure PowerShell 版本,请使用 Get-Module -ListAvailable Az cmdlet。 若要进行安装或更新,请参阅安装 Azure PowerShell 模块。
创建资源组
使用 New-AzResourceGroup 命令创建 Azure 资源组。 资源组是在其中部署和管理 Azure 资源的逻辑容器。 使用提升的权限打开 PowerShell 控制台,并使用 Connect-AzAccount -Environment AzureChinaCloud 命令连接到 Azure。
New-AzResourceGroup -Name TestRG1 -Location ChinaNorth3
创建虚拟网络
如果还没有虚拟网络,请使用 New-AzVirtualNetwork 创建一个。 创建虚拟网络时,请确保指定的地址空间不与本地网络的任一个地址空间相重叠。 如果 VPN 连接的两侧存在重复的地址范围,则流量不会按预期的方式路由。 此外,如果要将此虚拟网络连接到另一个虚拟网络,则地址空间不能与其他虚拟网络重叠。 请注意对网络配置进行相应的计划。
以下示例在“ChinaNorth 3”位置创建一个名为“VNet1”的虚拟网络:
$virtualnetwork = New-AzVirtualNetwork `
-ResourceGroupName TestRG1 `
-Location ChinaNorth3 `
-Name VNet1 `
-AddressPrefix 10.1.0.0/16
使用 New-AzVirtualNetworkSubnetConfig cmdlet 创建子网配置。 本练习中不使用 FrontEnd 子网。 可以替换你自己的子网名称。
$subnetConfig = Add-AzVirtualNetworkSubnetConfig `
-Name FrontEnd `
-AddressPrefix 10.1.0.0/24 `
-VirtualNetwork $virtualnetwork
使用 Set-AzVirtualNetwork cmdlet 设置虚拟网络的子网配置。
$virtualnetwork | Set-AzVirtualNetwork
添加网关子网
虚拟网络网关资源部署到一个名为“GatewaySubnet”的特定子网。 网关子网是虚拟网络 IP 地址范围的一部分,该范围是在配置虚拟网络时指定的。
如果在创建 VPN 网关时没有名为GatewaySubnet的子网,则创建将失败。 我们建议创建使用 /27(或更大)的网关子网。 例如 /27 或 /26。 有关网关子网的详细信息,请参阅 VPN 网关设置 - 网关子网。
重要
网关子网上的 NSG 不受支持。 将网络安全组关联到此子网可能会导致虚拟网络网关(VPN 和 ExpressRoute 网关)停止按预期方式工作。 有关网络安全组的详细信息,请参阅 什么是网络安全组?
为虚拟网络设置变量。
$vnet = Get-AzVirtualNetwork -ResourceGroupName TestRG1 -Name VNet1
使用 Add-AzVirtualNetworkSubnetConfig cmdlet 创建网关子网。
Add-AzVirtualNetworkSubnetConfig -Name 'GatewaySubnet' -AddressPrefix 10.1.255.0/27 -VirtualNetwork $vnet
使用 Set-AzVirtualNetwork cmdlet 设置虚拟网络的子网配置。
$vnet | Set-AzVirtualNetwork
请求公共 IP 地址
VPN 网关必须使用公共 IP 地址。 创建与 VPN 网关的连接时,这是你指定的 IP 地址。 对于主动-主动模式网关,每个网关实例都有自己的公共 IP 地址资源。 请先请求 IP 地址资源,并在创建虚拟网关时参阅该资源。 此外,对于任何以 AZ 结尾的网关 SKU,还必须指定区域设置。 此示例指定了区域冗余配置,因为它指定了所有 3 个区域区域。
创建 VPN 网关时,将会向资源分配 IP 地址。 公共 IP 地址只在删除或重新创建网关时会更改。 该地址不会因您的 VPN 网关的大小调整、重置或其他内部维护/升级而发生变化。
使用以下示例为每个网关实例请求一个静态公共 IP 地址。
$gw1pip1 = New-AzPublicIpAddress -Name "VNet1GWpip1" -ResourceGroupName "TestRG1" -Location "ChinaNorth3" -AllocationMethod Static -Sku Standard -Zone 1,2,3
若要创建推荐的主动-主动网关,可请求第二个公共 IP 地址:
$gw1pip2 = New-AzPublicIpAddress -Name "VNet1GWpip2" -ResourceGroupName "TestRG1" -Location "ChinaNorth3" -AllocationMethod Static -Sku Standard -Zone 1,2,3
创建网关 IP 地址配置
网关配置定义要使用的子网和公共 IP 地址。 使用以下示例创建网关配置。
$vnet = Get-AzVirtualNetwork -Name VNet1 -ResourceGroupName TestRG1
$subnet = Get-AzVirtualNetworkSubnetConfig -Name 'GatewaySubnet' -VirtualNetwork $vnet
$gwipconfig1 = New-AzVirtualNetworkGatewayIpConfig -Name gwipconfig1 -SubnetId $subnet.Id -PublicIpAddressId $gw1pip1.Id
$gwipconfig2 = New-AzVirtualNetworkGatewayIpConfig -Name gwipconfig2 -SubnetId $subnet.Id -PublicIpAddressId $gw1pip2.Id
创建 VPN 网关
创建网关通常需要 45 分钟或更长的时间,具体取决于所选的网关 SKU。 创建网关后,可以创建虚拟网络与本地位置之间的连接。 您还可以在虚拟网络与其他虚拟网络之间创建连接。
使用 New-AzVirtualNetworkGateway cmdlet 创建 VPN 网关。 请注意,这些示例引用了两个公共 IP 地址,并且通过使用 EnableActiveActiveFeature 开关将网关配置为了主动-主动模式。 在本示例中,我们添加了可选的 -Debug 开关。 如果要使用不同的 SKU 创建网关,请参阅关于网关 SKU,以确定最符合你配置要求的 SKU。
New-AzVirtualNetworkGateway -Name VNet1GW -ResourceGroupName TestRG1 `
-Location "ChinaNorth3" -IpConfigurations $gwipconfig1,$gwipconfig2 -GatewayType "Vpn" -VpnType RouteBased `
-GatewaySku VpnGw2AZ -VpnGatewayGeneration Generation2 -EnableActiveActiveFeature -Debug
查看 VPN 网关
可使用 Get-AzVirtualNetworkGateway cmdlet 查看 VPN 网关。
Get-AzVirtualNetworkGateway -Name Vnet1GW -ResourceGroup TestRG1
查看网关 IP 地址
为每个 VPN 网关实例分配一个公共 IP 地址资源。 要查看与资源关联的 IP 地址,请使用 Get-AzPublicIpAddress。 对每个网关实例重复此操作。 双活网关为每个实例分配了不同的公共IP地址。
Get-AzPublicIpAddress -Name VNet1GWpip1 -ResourceGroupName TestRG1
清理资源
如果不再需要所创建的资源,请使用 Remove-AzResourceGroup 命令删除资源组。 这会删除资源组及其包含的所有资源。
Remove-AzResourceGroup -Name TestRG1
后续步骤
创建网关后,可以配置连接。