本文介绍如何使用 VNet 到 VNet 连接类型来连接虚拟网络。 虚拟网络可位于相同或不同的区域,来自相同或不同的订阅。 从不同的订阅连接虚拟网络时,订阅不需要与相同的租户相关联。 如果已有要连接的 VNet,并且它们位于同一订阅中,则可以选择使用Azure 门户的步骤,因为过程更加简单。 请注意,无法使用 Azure 门户从不同的订阅连接 VNet。
在本练习中,你将创建所需的虚拟网络 (VNet) 和 VPN 网关。 我们提供一些步骤来连接同一订阅中的 VNet,还提供一些步骤和命令来处理更复杂的场景,即连接不同订阅中的 VNet。 用于创建连接的 PowerShell cmdlet 是 New-AzVirtualNetworkGatewayConnection。 -ConnectionType 为 Vnet2Vnet。
关于连接 VNet
可通过多种方式来连接 VNet。 以下部分介绍如何通过不同的方式连接虚拟网络。
VNet 到 VNet
配置一个 VNet 到 VNet 连接即可轻松地连接 VNet。 使用 VNet-to-VNet 连接类型将一个虚拟网络连接到另一个虚拟网络,这类似于创建一个站点到站点的 IPsec 连接到本地位置。 这两种连接类型都使用 VPN 网关来提供使用 IPsec/IKE 的安全隧道,二者在通信时使用同样的方式运行。 连接类型的差异在于本地网关的配置方式。 创建 VNet 到 VNet 连接时,看不到本地网关地址空间。 它会被自动创建并填充。 如果更新一个 VNet 的地址空间,另一个 VNet 会自动知道路由到更新的地址空间。 与在 VNet 之间创建站点到站点连接相比,创建 VNet 到 VNet 连接通常速度更快且更容易。
站点到站点 (IPsec)
如果您正在处理复杂的网络配置,您可能更倾向于使用站点到站点步骤来连接您的 VNets,而不是使用 VNet 到 VNet 步骤。 使用站点到站点步骤时,可以手动创建和配置本地网关。 每个 VNet 的本地网关都将其他 VNet 视为本地站点。 这样可以为本地网关指定路由流量所需的其他地址空间。 如果 VNet 的地址空间更改,则需根据更改更新相应的本地网关。 它不会自动更新。
VNet 对等互连
您可能要考虑使用 VNet 对等互连来连接您的 VNet。 VNet 对等互连无需使用 VPN 网关,并且有不同的限制条件。 另外,VNet 对等互连定价的计算不同于 VNet 到 VNet VPN 网关定价的计算。 有关详细信息,请参阅 虚拟网络对等互连。
为何创建 VNet 到 VNet 连接?
你可能会出于以下原因而使用 VNet 到 VNet 连接来连接虚拟网络:
跨区域地域冗余和地域存在
- 可以使用安全连接设置自己的异地复制或同步,而无需借助于面向 Internet 的终结点。
- 使用 Azure 流量管理器和负载均衡器,可以设置支持跨多个 Azure 区域实现异地冗余的高可用性工作负荷。 一个重要的示例就是对分布在多个 Azure 区域中的可用性组设置 SQL Always On。
具有隔离或管理边界的区域多层应用程序
- 在同一区域中,由于存在隔离或管理要求,可以设置具有多个虚拟网络的多层应用程序,这些虚拟网络相互连接在一起。
可以将 VNet 到 VNet 通信与多站点配置组合使用。 这样,便可以建立将跨界连接与虚拟网络间连接相结合的网络拓扑。
我应该使用哪些 VNet 到 VNet 的步骤?
在本文中,可以看到两组不同的步骤。 一组步骤适用于驻留在同一订阅中的虚拟网络,另一组步骤适用于驻留在不同订阅中的虚拟网络。 两组的主要差异是,配置位于不同订阅中的 VNet 的连接时,必须使用单独的 PowerShell 会话。
就本练习来说,可以将配置组合起来,也可以只是选择要使用的配置。 所有配置使用 VNet 到 VNet 连接类型。 网络流量在彼此直接连接的 VNet 之间流动。 在此练习中,来自 TestVNet4 的流量不会路由到 TestVNet5。
在同一订阅中驻留的 VNet:此配置的步骤使用 TestVNet1 和 TestVNet4。
驻留在不同订阅中的 VNet:此配置的步骤使用 TestVNet1 和 TestVNet5。 如果虚拟网络不在同一租户中,则你还必须遵循其他说明。 请先阅读这些说明,了解它们属于练习步骤中的位置。
如何连接相同订阅中的 VNet
可以在本地使用最新版本的 Azure PowerShell 模块完成以下步骤,详见如何安装和配置 Azure PowerShell。
步骤 1 - 规划 IP 地址范围
以下步骤将创建两个虚拟网络,以及它们各自的网关子网和配置。 然后在两个 VNet 之间创建 VPN 连接。 必须规划好网络配置的 IP 地址范围。 请记住,必须确保没有任何 VNet 范围或本地网络范围存在任何形式的重叠。 在这些示例中,我们没有包括 DNS 服务器。 如果需要虚拟网络的名称解析,请参阅名称解析。
示例中使用了以下值:
TestVNet1 的值:
- VNet 名称:TestVNet1
- 资源组:TestRG1
- 位置:中国东部
- TestVNet1:10.1.0.0/16
- 前端:10.1.0.0/24
- 网关子网: 10.1.255.0/27
- GatewayName:VNet1GW
- 公共 IP:VNet1GWIP
- VPN类型:RouteBased
- 连接(1 到 4):VNet1 到 VNet4
- Connection(1至5):VNet1至VNet5(适用于不同订阅中的 VNet)
- 连接类型:VNet2VNet
TestVNet4 的值:
- VNet 名称:TestVNet4
- TestVNet2:10.41.0.0/16
- FrontEnd:10.41.0.0/24
- GatewaySubnet:10.41.255.0/27
- 资源组:TestRG4
- 位置:中国北部
- GatewayName:VNet4GW
- 公共 IP:VNet4GWIP
- VPNType:RouteBased
- 连接:VNet4 到 VNet1
- 连接类型:VNet2VNet
步骤 2 - 创建并配置 TestVNet1
对于以下步骤,可以在本地运行 PowerShell。 有关详细信息,请参阅如何安装和配置 Azure PowerShell。
注意
可能会看到警告“将在未来发布中修改此 cmdlet 的输出对象类型”。 这是预期行为,可以放心地忽略这些警告。
声明变量。 此示例使用本练习中的值来声明变量。 在大多数情况下,您应该用您自己的值替换这些值。 但是,如果执行这些步骤的目的是熟悉这种类型的配置,可以直接使用这些变量。 根据需要修改变量,并将其复制并粘贴到 PowerShell 控制台中。
$RG1 = "TestRG1" $Location1 = "China East" $VNetName1 = "TestVNet1" $FESubName1 = "FrontEnd" $VNetPrefix1 = "10.1.0.0/16" $FESubPrefix1 = "10.1.0.0/24" $GWSubPrefix1 = "10.1.255.0/27" $GWName1 = "VNet1GW" $GWIPName1 = "VNet1GWIP" $GWIPconfName1 = "gwipconf1" $Connection14 = "VNet1toVNet4" $Connection15 = "VNet1toVNet5"创建资源组。
New-AzResourceGroup -Name $RG1 -Location $Location1创建 TestVNet1 的子网配置。 本示例会创建一个虚拟网络和两个子网,虚拟网络名为 TestVNet1,子网分别名为 GatewaySubnet 和 FrontEnd。 替换值时,请务必始终将网关子网特意命名为 GatewaySubnet。 如果命名为其他名称,网关创建会失败。 出于此原因,在本例中,不会通过变量来分配它。
以下示例使用前面设置的变量。 在本示例中,网关子网使用 /27。 虽然对于此配置,可使用 /28 创建网关子网,但建议至少选择 /27,创建包含更多地址的更大子网。 这样便可以留出足够多的地址,满足将来可能需要使用的其他配置。
$fesub1 = New-AzVirtualNetworkSubnetConfig -Name $FESubName1 -AddressPrefix $FESubPrefix1 $gwsub1 = New-AzVirtualNetworkSubnetConfig -Name "GatewaySubnet" -AddressPrefix $GWSubPrefix1创建 TestVNet1。
New-AzVirtualNetwork -Name $VNetName1 -ResourceGroupName $RG1 ` -Location $Location1 -AddressPrefix $VNetPrefix1 -Subnet $fesub1,$gwsub1VPN 网关必须具有分配的公共 IP 地址。 创建与 VPN 网关的连接时,这是你指定的 IP 地址。 使用下面的示例请求一个公共 IP 地址。
$gwpip1 = New-AzPublicIpAddress -Name $GWIPName1 -ResourceGroupName $RG1 ` -Location $Location1 -AllocationMethod Static -Sku Standard创建网关配置。 网关配置定义要使用的子网和公共 IP 地址。 使用该示例创建网关配置。
$vnet1 = Get-AzVirtualNetwork -Name $VNetName1 -ResourceGroupName $RG1 $subnet1 = Get-AzVirtualNetworkSubnetConfig -Name "GatewaySubnet" -VirtualNetwork $vnet1 $gwipconf1 = New-AzVirtualNetworkGatewayIpConfig -Name $GWIPconfName1 ` -Subnet $subnet1 -PublicIpAddress $gwpip1为 TestVNet1 创建网关。 本步骤为 TestVNet1 创建虚拟网络网关。 VNet 到 VNet 配置需要基于路由的 VPN 类型。 创建网关通常需要 45 分钟或更长的时间,具体取决于所选网关 SKU。
New-AzVirtualNetworkGateway -Name $GWName1 -ResourceGroupName $RG1 ` -Location $Location1 -IpConfigurations $gwipconf1 -GatewayType Vpn ` -VpnType RouteBased -GatewaySku VpnGw2 -VpnGatewayGeneration "Generation2"
完成命令后,创建此网关将需要 45 分钟或更长时间。
步骤 3:创建并配置 TestVNet4
创建 TestVNet4。 按照以下步骤操作,根据需要将值替换为你自己的值。
连接并声明变量。 请务必将值替换为要用于配置的值。
$RG4 = "TestRG4" $Location4 = "China North" $VnetName4 = "TestVNet4" $FESubName4 = "FrontEnd" $VnetPrefix4 = "10.41.0.0/16" $FESubPrefix4 = "10.41.0.0/24" $GWSubPrefix4 = "10.41.255.0/27" $GWName4 = "VNet4GW" $GWIPName4 = "VNet4GWIP" $GWIPconfName4 = "gwipconf4" $Connection41 = "VNet4toVNet1"创建资源组。
New-AzResourceGroup -Name $RG4 -Location $Location4创建 TestVNet4 的子网配置。
$fesub4 = New-AzVirtualNetworkSubnetConfig -Name $FESubName4 -AddressPrefix $FESubPrefix4 $gwsub4 = New-AzVirtualNetworkSubnetConfig -Name "GatewaySubnet" -AddressPrefix $GWSubPrefix4创建 TestVNet4。
New-AzVirtualNetwork -Name $VnetName4 -ResourceGroupName $RG4 ` -Location $Location4 -AddressPrefix $VnetPrefix4 -Subnet $fesub4,$gwsub4请求公共 IP 地址。
$gwpip4 = New-AzPublicIpAddress -Name $GWIPName4 -ResourceGroupName $RG4 ` -Location $Location4 -AllocationMethod Static -Sku Standard创建网关配置。
$vnet4 = Get-AzVirtualNetwork -Name $VnetName4 -ResourceGroupName $RG4 $subnet4 = Get-AzVirtualNetworkSubnetConfig -Name "GatewaySubnet" -VirtualNetwork $vnet4 $gwipconf4 = New-AzVirtualNetworkGatewayIpConfig -Name $GWIPconfName4 -Subnet $subnet4 -PublicIpAddress $gwpip4创建 TestVNet4 网关。 创建网关通常需要 45 分钟或更长的时间,具体取决于所选网关 SKU。
New-AzVirtualNetworkGateway -Name $GWName4 -ResourceGroupName $RG4 ` -Location $Location4 -IpConfigurations $gwipconf4 -GatewayType Vpn ` -VpnType RouteBased -GatewaySku VpnGw2 -VpnGatewayGeneration "Generation2"
步骤 4:创建连接
等待两个网关完成创建。
获取两个虚拟网关。
$vnet1gw = Get-AzVirtualNetworkGateway -Name $GWName1 -ResourceGroupName $RG1 $vnet4gw = Get-AzVirtualNetworkGateway -Name $GWName4 -ResourceGroupName $RG4创建 TestVNet1 到 TestVNet4 的连接。 本步骤创建从 TestVNet1 到 TestVNet4 的连接。 示例中引用了共享密钥。 可以对共享密钥使用自己的值。 共享密钥必须与两个连接匹配,这一点非常重要。 创建连接可能需要简短的一段时间才能完成。
New-AzVirtualNetworkGatewayConnection -Name $Connection14 -ResourceGroupName $RG1 ` -VirtualNetworkGateway1 $vnet1gw -VirtualNetworkGateway2 $vnet4gw -Location $Location1 ` -ConnectionType Vnet2Vnet -SharedKey 'AzureA1b2C3'创建 TestVNet4 到 TestVNet1 的连接。 此步骤与上述步骤类似,只不过是创建 TestVNet4 到 TestVNet1 的连接。 确保共享密钥匹配。 几分钟后会建立连接。
New-AzVirtualNetworkGatewayConnection -Name $Connection41 -ResourceGroupName $RG4 ` -VirtualNetworkGateway1 $vnet4gw -VirtualNetworkGateway2 $vnet1gw -Location $Location4 ` -ConnectionType Vnet2Vnet -SharedKey 'AzureA1b2C3'验证连接。 请参阅如何验证连接部分。
如何连接不同订阅中的 VNet
在此方案中,连接 TestVNet1 和 TestVNet5。 TestVNet1 和 TestVNet5 驻留在不同订阅中。 订阅不需要与相同的租户相关联。
这些步骤与上一组的差别在于,一些配置步骤需要在第二个订阅的环境的单独 PowerShell 会话中执行。 尤其是当两个订阅属于不同的组织时。
步骤 5:创建并配置 TestVNet1
必须完成前述部分的步骤 1 和步骤 2,才能创建并配置 TestVNet1 及其 VPN 网关。 对于此配置,不需创建上一部分中的 TestVNet4,虽然即使创建了它,也不会与这些步骤冲突。 完成步骤 1 和步骤 2 后,继续执行步骤 6,创建 TestVNet5。
步骤 6:验证 IP 地址范围
必须确保新虚拟网络 TestVNet5 的 IP 地址空间不与任何 VNet 范围或局域网网关范围重叠。 在本示例中,虚拟网络可能属于不同的组织。 对于本练习,可以对 TestVNet5 使用以下值:
TestVNet5 的值:
- VNet 名称:TestVNet5
- 资源组:TestRG5
- 位置:中国东部 2
- TestVNet5:10.51.0.0/16
- FrontEnd:10.51.0.0/24
- GatewaySubnet:10.51.255.0.0/27
- GatewayName: VNet5GW
- 公共 IP:VNet5GWIP
- VPNType:RouteBased
- 连接:VNet5toVNet1
- 连接类型:VNet2VNet
步骤 7:创建并配置 TestVNet5
必须在新订阅环境中完成此步骤。 此部分可能由拥有订阅的不同组织的管理员执行。
声明变量。 请务必将值替换为要用于配置的值。
$Sub5 = "Replace_With_the_New_Subscription_Name" $RG5 = "TestRG5" $Location5 = "China East 2" $VnetName5 = "TestVNet5" $FESubName5 = "FrontEnd" $GWSubName5 = "GatewaySubnet" $VnetPrefix5 = "10.51.0.0/16" $FESubPrefix5 = "10.51.0.0/24" $GWSubPrefix5 = "10.51.255.0/27" $GWName5 = "VNet5GW" $GWIPName5 = "VNet5GWIP" $GWIPconfName5 = "gwipconf5" $Connection51 = "VNet5toVNet1"连接到订阅 5。 打开 PowerShell 控制台并连接到帐户。 使用下面的示例来帮助您进行连接:
Connect-AzAccount -Environment AzureChinaCloud检查该帐户的订阅。
Get-AzSubscription指定要使用的订阅。
Select-AzSubscription -SubscriptionName $Sub5创建新的资源组。
New-AzResourceGroup -Name $RG5 -Location $Location5创建 TestVNet5 的子网配置。
$fesub5 = New-AzVirtualNetworkSubnetConfig -Name $FESubName5 -AddressPrefix $FESubPrefix5 $gwsub5 = New-AzVirtualNetworkSubnetConfig -Name $GWSubName5 -AddressPrefix $GWSubPrefix5创建 TestVNet5。
New-AzVirtualNetwork -Name $VnetName5 -ResourceGroupName $RG5 -Location $Location5 ` -AddressPrefix $VnetPrefix5 -Subnet $fesub5,$gwsub5请求公共 IP 地址。
$gwpip5 = New-AzPublicIpAddress -Name $GWIPName5 -ResourceGroupName $RG5 ` -Location $Location5 -AllocationMethod Static -Sku Standard创建网关配置。
$vnet5 = Get-AzVirtualNetwork -Name $VnetName5 -ResourceGroupName $RG5 $subnet5 = Get-AzVirtualNetworkSubnetConfig -Name "GatewaySubnet" -VirtualNetwork $vnet5 $gwipconf5 = New-AzVirtualNetworkGatewayIpConfig -Name $GWIPconfName5 -Subnet $subnet5 -PublicIpAddress $gwpip5创建 TestVNet5 网关。
New-AzVirtualNetworkGateway -Name $GWName5 -ResourceGroupName $RG5 -Location $Location5 ` -IpConfigurations $gwipconf5 -GatewayType Vpn -VpnType RouteBased -GatewaySku VpnGw2 -VpnGatewayGeneration "Generation2"
步骤 8:创建连接
在本示例中,由于网关位于不同订阅中,因此将此步骤拆分为了两个 PowerShell 会话,分别标记为 [订阅 1] 和 [订阅 5]。
[订阅 1] 获取订阅 1 的虚拟网关。 登录并连接到订阅 1,然后运行以下示例:
$vnet1gw = Get-AzVirtualNetworkGateway -Name $GWName1 -ResourceGroupName $RG1复制以下元素的输出,并通过电子邮件或其他方式将输出发送给订阅 5 的管理员。
$vnet1gw.Name $vnet1gw.Id这两个元素的值类似于以下示例输出:
PS D:\> $vnet1gw.Name VNet1GW PS D:\> $vnet1gw.Id /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroupsTestRG1/providers/Microsoft.Network/virtualNetworkGateways/VNet1GW[订阅 5] 获取订阅 5 的虚拟网关。 登录并连接到订阅 5,然后运行以下示例:
$vnet5gw = Get-AzVirtualNetworkGateway -Name $GWName5 -ResourceGroupName $RG5复制以下元素的输出,并通过电子邮件或其他方式将输出发送给订阅 1 的管理员。
$vnet5gw.Name $vnet5gw.Id这两个元素的值类似于以下示例输出:
PS C:\> $vnet5gw.Name VNet5GW PS C:\> $vnet5gw.Id /subscriptions/bbbb1b1b-cc2c-dd3d-ee4e-ffffff5f5f5f/resourceGroups/TestRG5/providers/Microsoft.Network/virtualNetworkGateways/VNet5GW[订阅 1] 创建 TestVNet1 到 TestVNet5 连接。 在此步骤中,创建 TestVNet1 到 TestVNet5 的连接。 这里的不同之处在于无法直接获得 $vnet5gw,因为它位于不同的订阅中。 需要使用上述步骤中从订阅 1 传递的值来创建新的 PowerShell 对象。 使用以下示例。 将名称、ID 和共享密钥替换为自己的值。 共享密钥必须与两个连接匹配,这一点非常重要。 创建连接可能需要简短的一段时间才能完成。
先连接到订阅 1,然后运行以下示例:
$vnet5gw = New-Object -TypeName Microsoft.Azure.Commands.Network.Models.PSVirtualNetworkGateway $vnet5gw.Name = "VNet5GW" $vnet5gw.Id = "/subscriptions/bbbb1b1b-cc2c-dd3d-ee4e-ffffff5f5f5f/resourceGroups/TestRG5/providers/Microsoft.Network/virtualNetworkGateways/VNet5GW" $Connection15 = "VNet1toVNet5" New-AzVirtualNetworkGatewayConnection -Name $Connection15 -ResourceGroupName $RG1 -VirtualNetworkGateway1 $vnet1gw -VirtualNetworkGateway2 $vnet5gw -Location $Location1 -ConnectionType Vnet2Vnet -SharedKey 'AzureA1b2C3'[订阅5] 创建 TestVNet5 到 TestVNet1 连接。 此步骤与上述步骤类似,只不过是创建 TestVNet5 到 TestVNet1 的连接。 此处也适用基于从订阅 1 获取的值创建 PowerShell 对象这一相同过程。 在此步骤中,请确保共享密钥匹配。
在运行以下示例之前,连接到订阅 5。
$vnet1gw = New-Object -TypeName Microsoft.Azure.Commands.Network.Models.PSVirtualNetworkGateway $vnet1gw.Name = "VNet1GW" $vnet1gw.Id = "/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/TestRG1/providers/Microsoft.Network/virtualNetworkGateways/VNet1GW " $Connection51 = "VNet5toVNet1" New-AzVirtualNetworkGatewayConnection -Name $Connection51 -ResourceGroupName $RG5 -VirtualNetworkGateway1 $vnet5gw -VirtualNetworkGateway2 $vnet1gw -Location $Location5 -ConnectionType Vnet2Vnet -SharedKey 'AzureA1b2C3'
连接不同订阅和不同租户中的 VNet
此方案使用前面的方案步骤,但存在一些主要差异。 在此方案中,TestVNet5 驻留在订阅 1 租户 1 中。 TestVNet1 驻留在租户 2 的订阅 2 中。
在此场景中,创建 TestVNet1 网关时,需要使用以下命令连接到 Tenant2、Subscription2。 根据需要调整或声明任何变量。
Connect-AzAccount -TenantID $Tenant2 -Environment AzureChinaCloud
Select-AzSubscription -SubscriptionId $subscription2
<Other PS commandlets to create TestVNet1 gateway are same as above>
$vnet1gw = Get-AzVirtualNetworkGateway -Name $GWName1 -ResourceGroupName $RG1
创建和配置 TestVNet5 网关时,需要使用以下命令连接到 Tenant1 Subscription1,并根据需要调整任何变量。
Connect-AzAccount -TenantID $Tenant1 -Environment AzureChinaCloud
Select-AzSubscription -SubscriptionId $subscription1
$vnet5gw = Get-AzVirtualNetworkGateway -Name $GWName5 -ResourceGroupName $RG1
在使用 VirtualNetworkGateway1 作为 $vnet1gw 创建 Vnet2Vnet VirtualNetworkGatewayConnection 时,需要先连接到 Tenant2、Subscription2,其他命令与前一节相同。
Connect-AzAccount -TenantID $Tenant2 -Environment AzureChinaCloud
Select-AzSubscription -SubscriptionId $subscription2
$vnet5gw = Get-AzVirtualNetworkGateway -Name $GWName1 -ResourceGroupName $RG1
New-AzVirtualNetworkGatewayConnection -Name $Connection51 -ResourceGroupName $RG5 -VirtualNetworkGateway1 $vnet5gw -VirtualNetworkGateway2 $vnet1gw -Location $Location5 -ConnectionType Vnet2Vnet -SharedKey 'AzureA1b2C3'
如何验证连接
重要
网关子网上的 NSG 不受支持。 将网络安全组关联到此子网可能会导致虚拟网络网关(VPN 和 ExpressRoute 网关)停止按预期方式工作。 有关网络安全组的详细信息,请参阅 什么是网络安全组?
可以验证连接是否成功,方法是使用“Get-AzVirtualNetworkGatewayConnection”cmdlet,带或不带“-Debug”。
使用以下 cmdlet 示例,配置符合自己需要的值。 如果出现提示,请选择“A”运行“所有”。 在此示例中,“ -Name”是指要测试的连接的名称。
Get-AzVirtualNetworkGatewayConnection -Name VNet1toSite1 -ResourceGroupName TestRG1cmdlet 运行完毕后,查看该值。 在以下示例中,连接状态显示为“已连接”,且可以看到入口和出口字节数。
"connectionStatus": "Connected", "ingressBytesTransferred": 33509044, "egressBytesTransferred": 4142431
VNet 到 VNet 常见问题
有关 VNet 到 VNet 连接的详细信息,请参阅 VPN 网关常见问题解答链接。
后续步骤
- 连接完成后,即可将虚拟机添加到虚拟网络。 有关详细信息,请参阅虚拟机文档。
- 有关 BGP 的信息,请参阅《BGP 概述》和《如何配置 BGP》。
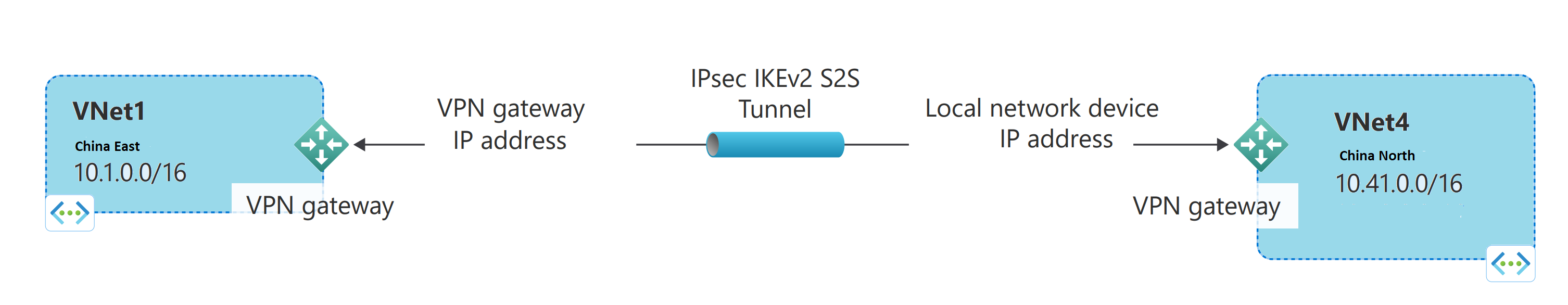 VNet 到 VNet 示意图。
VNet 到 VNet 示意图。