Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Microsoft Entra External ID combines powerful solutions for working with people outside of your organization. With External ID capabilities, you can allow external identities to securely access your apps and resources. Whether you’re working with external partners, consumers, or business customers, users can bring their own identities. These identities can range from corporate or government-issued accounts to social identity providers.
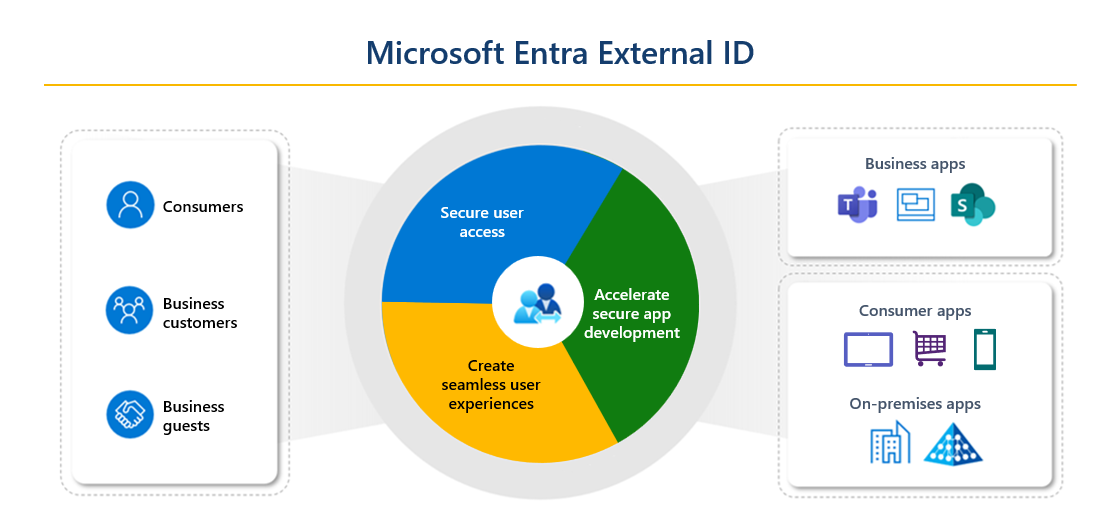
These scenarios fall within the scope of Microsoft Entra External ID:
If you’re an organization or a developer creating consumer apps, use External ID to quickly add authentication and customer identity and access management (CIAM) to your application. Register your app, create customized sign-in experiences, and manage your app users in a Microsoft Entra tenant in an external configuration. This tenant is separate from your employees and organizational resources.
If you want to enable your employees to collaborate with business partners and guests, use External ID for B2B collaboration. Allow secure access to your enterprise apps through invitation. Determine the level of access guests have to the Microsoft Entra tenant that contains your employees and organizational resources, which is a tenant in a workforce configuration.
Microsoft Entra External ID is a flexible solution for both consumer-oriented app developers needing authentication and CIAM, and businesses seeking secure B2B collaboration.
Collaborate with business guests
External ID B2B collaboration allows your workforce to collaborate with external business partners. You can invite anyone to sign in to your Microsoft Entra organization using their own credentials so they can access the apps and resources you want to share with them. Use B2B collaboration when you need to let business guests access your Office 365 apps, software-as-a-service (SaaS) apps, and line-of-business applications. There are no credentials associated with business guests. Instead, they authenticate with their home organization or identity provider, and then your organization checks the user’s eligibility for guest collaboration.
There are various ways to add business guests to your organization for collaboration:
Invite users to collaborate using their Microsoft Entra accounts, Microsoft accounts, or social identities that you enable. An admin can use the Microsoft Entra admin center or PowerShell to invite users to collaborate. The user signs into the shared resources using a simple redemption process with their work, school, or other email account.
Use Microsoft Entra entitlement management, an identity governance feature that lets you manage identity and access for external users at scale by automating access request workflows, access assignments, reviews, and expiration.
A user object is created for the business guest in the same directory as your employees. This user object can be managed like other user objects in your directory, added to groups, and so on. You can assign permissions to the user object (for authorization) while letting them use their existing credentials (for authentication).
You can use cross-tenant access settings to manage collaboration with other Microsoft Entra organizations and across Azure clouds. For collaboration with non-Azure AD external users and organizations, use external collaboration settings.
Related technologies
There are several Microsoft Entra technologies that are related to collaboration with external users and organizations. As you design your External ID collaboration model, consider these other features.
Azure Active Directory B2C
Important
Effective May 1, 2025, Azure AD B2C will no longer be available to purchase for new customers. To learn more, please see Is Azure AD B2C still available to purchase? in our FAQ.
Azure Active Directory B2C (Azure AD B2C) is Microsoft's legacy solution for customer identity and access management. Azure AD B2C includes a separate consumer-based directory that you manage in the Azure portal through the Azure AD B2C service. Each Azure AD B2C tenant is separate and distinct from other Microsoft Entra ID and Azure AD B2C tenants. The Azure AD B2C portal experience is similar to Microsoft Entra ID, but there are key differences, such as the ability to customize your user journeys using the Identity Experience Framework.
For more information about how an Azure AD B2C tenant differs from a Microsoft Entra tenant, see Supported Microsoft Entra features in Azure AD B2C. For details about configuring and managing Azure AD B2C, see the Azure AD B2C documentation.
Microsoft Entra entitlement management for business guest sign-up
As an inviting organization, you might not know ahead of time who the individual external collaborators are who need access to your resources. You need a way for users from partner companies to sign themselves up with policies that you control. To enable users from other organizations to request access, you can use Microsoft Entra entitlement management to configure policies that manage access for external users. Upon approval, these users will be provisioned with guest accounts and assigned to groups, apps, and SharePoint Online sites.
Conditional Access
Organizations can use Conditional Access policies to enhance their security by applying the appropriate access controls, such as MFA, to external users.
Organizations can enforce Conditional Access policies for external B2B collaboration users in the same way that they're enabled for full-time employees and members of the organization. For Microsoft Entra cross-tenant scenarios, if your Conditional Access policies require MFA or device compliance, you can now trust MFA and device compliance claims from an external user's home organization. When trust settings are enabled, during authentication, Microsoft Entra ID checks a user's credentials for an MFA claim or a device ID to determine if the policies were already met. If so, the external user is granted seamless sign-on to your shared resource. Otherwise, an MFA or device challenge is initiated in the user's home tenant. Learn more about the authentication flow and Conditional Access for external users.
Multitenant applications
If you offer a Software as a Service (SaaS) application to many organizations, you can configure your application to accept sign-ins from any Microsoft Entra tenant. This configuration is called making your application multitenant. Users in any Microsoft Entra tenant will be able to sign in to your application after consenting to use their account with your application. See how to enable multitenant sign-ins.
Microsoft Graph APIs
All External ID features are also supported for automation through Microsoft Graph APIs except those listed in the next section. For more information, see Manage Microsoft Entra identity and network access by using Microsoft Graph.
Capabilities not supported in Microsoft Graph
| External ID feature | Supported in | Automation workarounds |
|---|---|---|
| Identify organizations that you belong to | Workforce tenants | Tenants - List Azure Resource Manager API. For Teams shared channels, use Get tenantReferences Microsoft Graph API. |
Microsoft Entra Microsoft Graph API for B2B collaboration
Cross-tenant access settings APIs: The cross-tenant access APIs in Microsoft Graph let you programmatically create the same B2B collaboration policies that are configurable in the Azure portal. Using these APIs, you can set up policies for inbound and outbound collaboration. For example, you can allow or block features for everyone by default and limit access to specific organizations, groups, users, and applications. The APIs also allow you to accept multifactor authentication (MFA) and device claims (compliant claims and Microsoft Entra hybrid joined claims) from other Microsoft Entra organizations.
B2B collaboration invitation manager: The invitation manager API in Microsoft Graph is available for building your own onboarding experiences for business guests. You can use the create invitation API to automatically send a customized invitation email directly to the B2B user, for example. Or your app can use the inviteRedeemUrl returned in the creation response to craft your own invitation (through your communication mechanism of choice) to the invited user.