Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
External collaboration settings let you specify what roles in your organization can invite external users for B2B collaboration. These settings also include options for allowing or blocking specific domains, and options for restricting what external guest users can see in your Microsoft Entra directory. The following options are available:
Determine guest user access: Microsoft Entra External ID allows you to restrict what external guest users can see in your Microsoft Entra directory. For example, you can limit guest users' view of group memberships, or allow guests to view only their own profile information.
Specify who can invite guests: By default, all users in your organization, including B2B collaboration guest users, can invite external users to B2B collaboration. If you want to limit the ability to send invitations, you can turn invitations on or off for everyone, or limit invitations to certain roles.
Allow or block domains: You can use collaboration restrictions to allow or deny invitations to the domains you specify. For details, see Allow or block domains.
For B2B collaboration with other Microsoft Entra organizations, you should also review your cross-tenant access settings to ensure your inbound and outbound B2B collaboration and scope access to specific users, groups, and applications.
Note
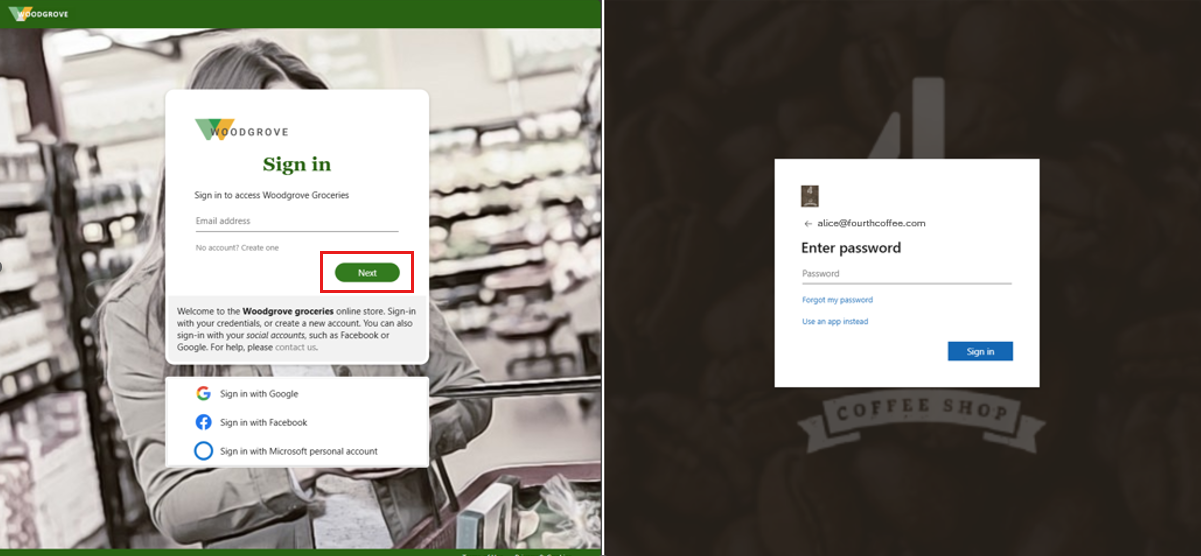
Effective July 2025, Microsoft begins rolling out an update to the guest user sign-in experience for B2B collaboration. The rollout continues through the end of 2025. With this update, guest users will be redirected to their own organization's sign-in page to provide their credentials. Guest users see the branding and URL endpoint of their home tenant. This step ensures greater clarity regarding which sign-in information to use. Following successful authentication in their own organization, guest users are returned to your organization to complete the sign-in process. In the following example, the company branding for Woodgrove Groceries appears on the left. The example on the right displays the custom branding for the user's home tenant.
Configure settings in the portal
In the Microsoft Entra admin center, you must be assigned the Global Administrator role to activate the External Collaboration Settings page and update the settings. When using Microsoft Graph, lesser privileged roles might be available for individual settings; see Configure settings with Microsoft Graph later in this article.
To configure guest user access
Sign in to the Microsoft Entra admin center.
Browse to Entra ID > External Identities > External collaboration settings.
Under Guest user access, choose the level of access you want guest users to have:
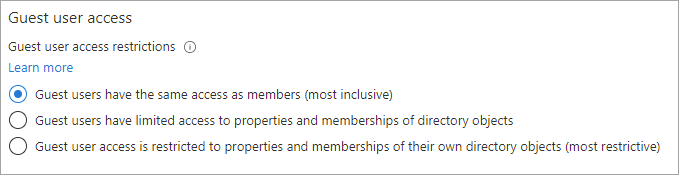
Guest users have the same access as members (most inclusive): This option gives guests the same access to Microsoft Entra resources and directory data as member users.
Guest users have limited access to properties and memberships of directory objects: (Default) This setting blocks guests from certain directory tasks, like enumerating users, groups, or other directory resources. Guests can see membership of all non-hidden groups. Learn more about default guest permissions.
Guest user access is restricted to properties and memberships of their own directory objects (most restrictive): With this setting, guests can access only their own profiles. Guests aren't allowed to see other users' profiles, groups, or group memberships.
To configure guest invite settings
Sign in to the Microsoft Entra admin center.
Browse to Entra ID > External Identities > External collaboration settings.
Under Guest invite settings, choose the appropriate settings:
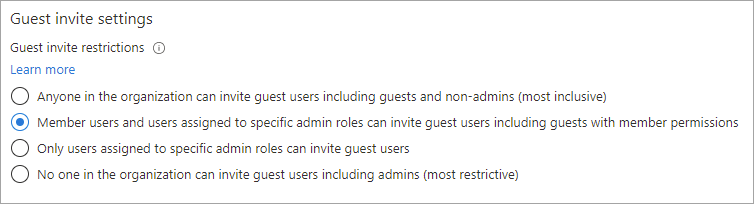
- Anyone in the organization can invite guest users including guests and non-admins (most inclusive): To allow guests in the organization to invite other guests including users who aren't members of an organization, select this radio button.
- Member users and users assigned to specific admin roles can invite guest users including guests with member permissions: To allow member users and users who have specific administrator roles to invite guests, select this radio button.
- Only users assigned to specific admin roles can invite guest users: To allow only those users with User Administrator or Guest Inviter roles to invite guests, select this radio button.
- No one in the organization can invite guest users including admins (most restrictive): To deny everyone in the organization from inviting guests, select this radio button.
To configure external user leave settings
Sign in to the Microsoft Entra admin center.
Browse to Entra ID > External Identities > External collaboration settings.
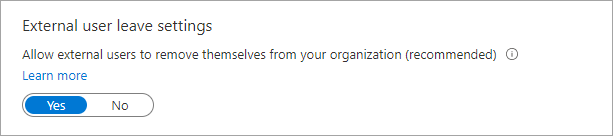
Under External user leave settings, you can control whether external users can remove themselves from your organization.
- Yes: Users can leave the organization themselves without approval from your admin or privacy contact.
- No: Users can't leave your organization themselves. They see a message guiding them to contact your admin or privacy contact to request removal from your organization.
Important
You can configure External user leave settings only if you have added your privacy information to your Microsoft Entra tenant. Otherwise, this setting will be unavailable.
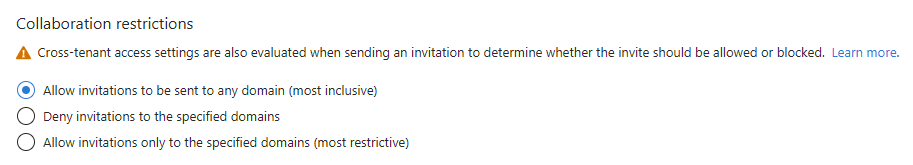
To configure collaboration restrictions (allow or block domains)
Important
Microsoft recommends that you use roles with the fewest permissions. This practice helps improve security for your organization. Global Administrator is a highly privileged role that should be limited to emergency scenarios or when you can't use an existing role.
Sign in to the Microsoft Entra admin center.
Browse to Entra ID > External Identities > External collaboration settings.
Under Collaboration restrictions, you can choose whether to allow or deny invitations to the domains you specify and enter specific domain names in the text boxes. For multiple domains, enter each domain on a new line. For more information, see Allow or block invitations to B2B users from specific organizations.
Configure settings with Microsoft Graph
External collaboration settings can be configured by using the Microsoft Graph API:
- For Guest user access restrictions and Guest invite restrictions, use the authorizationPolicy resource type.
- For External user leave settings, use the externalidentitiespolicy resource type.
Assign the Guest Inviter role to a user
With the Guest Inviter role, you can give individual users the ability to invite guests without assigning them a higher privilege administrator role. Users with the Guest Inviter role are able to invite guests even when the option Only users assigned to specific admin roles can invite guest users is selected (under Guest invite settings).
Here's an example that shows how to use Microsoft Graph PowerShell to add a user to the Guest Inviter role:
Import-Module Microsoft.Graph.Identity.DirectoryManagement
$roleName = "Guest Inviter"
$role = Get-MgDirectoryRole | where {$_.DisplayName -eq $roleName}
$userId = <User Id/User Principal Name>
$DirObject = @{
"@odata.id" = "https://microsoftgraph.chinacloudapi.cn/v1.0/directoryObjects/$userId"
}
New-MgDirectoryRoleMemberByRef -DirectoryRoleId $role.Id -BodyParameter $DirObject
Sign-in logs for B2B users
When a B2B user signs into a resource tenant to collaborate, a sign-in log is generated in both the home tenant and the resource tenant. These logs include information such as the application being used, email addresses, tenant name, and tenant ID for both the home tenant and the resource tenant.
Next steps
See the following articles on Microsoft Entra B2B collaboration: