Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
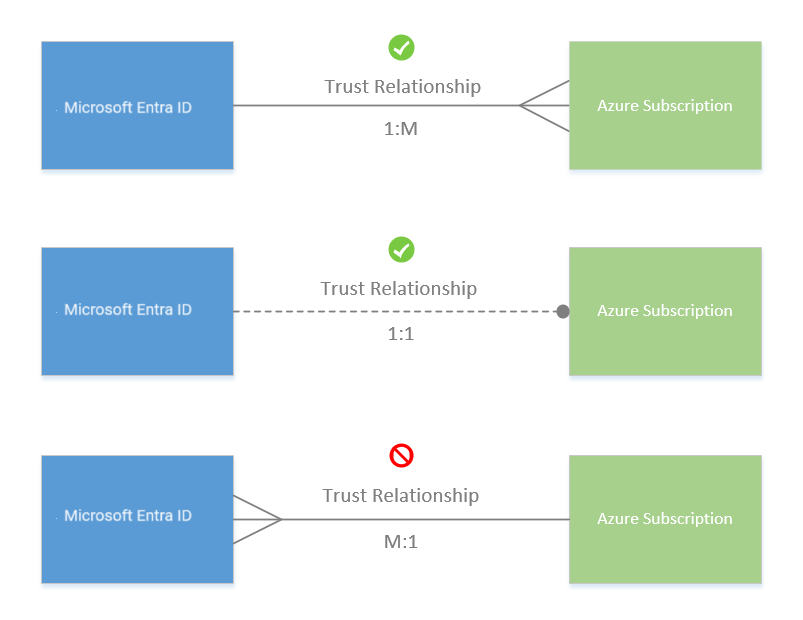
All Azure subscriptions have a trust relationship with a Microsoft Entra tenant. Subscriptions rely on this tenant (directory) to authenticate and authorize security principals and devices. When a subscription expires, the trusted instance remains, but the security principals lose access to Azure resources. Subscriptions can only trust a single directory while one Microsoft Entra tenant may be trusted by multiple subscriptions.
By default, the user who creates a Microsoft Entra tenant is automatically assigned the Global Administrator role. However, when an owner of a subscription joins their subscription to an existing tenant, the owner isn't assigned to the Global Administrator role.
While users may only have a single authentication home directory, users may participate as guests in multiple directories. You can see both the home and guest directories for each user in Microsoft Entra ID.
Important
When a subscription is associated with a different directory, users who have roles assigned using Azure role-based access control lose their access. Classic subscription administrators, including Service Administrator and Co-Administrators, also lose access.
Moving your Azure Kubernetes Service (AKS) cluster to a different subscription, or moving the cluster-owning subscription to a new tenant, causes the cluster to lose functionality due to lost role assignments and service principal's rights. For more information about AKS, see Azure Kubernetes Service (AKS).
Prerequisites
Before you can associate or add your subscription, do the following steps:
Review the following list of changes that will occur after you associate or add your subscription, and how you might be affected:
- Users assigned roles using Azure RBAC lose their access.
- Service Administrator and Co-Administrators will lose access.
- If you have any key vaults, they'll be inaccessible, and you'll have to fix them after association.
- If you have any managed identities for resources such as Virtual Machines or Logic Apps, you must re-enable or recreate them after the association.
- If you have a registered Azure Stack, you'll have to re-register it after association.
For more information, see Transfer an Azure subscription to a different Microsoft Entra directory.
Sign in using an account that:
- Has an Owner role assignment for the subscription. For information about how to assign the Owner role, see Assign Azure roles using the Azure portal.
- Exists in both the current directory and in the new directory. The current directory is associated with the subscription. You associate the new directory with the subscription. For more information about getting access to another directory, see Add Microsoft Entra B2B collaboration users in the Azure portal.
- Make sure that you're not using an Azure Cloud Service Providers (CSP) subscription (MS-AZR-0145P, MS-AZR-0146P, MS-AZR-159P), a Microsoft Internal subscription (MS-AZR-0015P), or a Azure for Students Starter subscription (MS-AZR-0144P).
Post-association steps
After you associate a subscription with a different directory, you might need to do the following tasks to resume operations:
If you have any key vaults, you must change the key vault tenant ID. For more information, see Change a key vault tenant ID after a subscription move.
If you used system-assigned Managed Identities for resources, you must re-enable these identities. If you used user-assigned Managed Identities, you must re-create these identities. After re-enabling or recreating the Managed Identities, you must re-establish the permissions assigned to those identities. For more information, see What are managed identities for Azure resources?.
If you've registered an Azure Stack using this subscription, you must re-register. For more information, see Register Azure Stack Hub with Azure.
For more information, see Transfer an Azure subscription to a different Microsoft Entra directory.