Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article helps you create IPsec tunnels in transport mode over ExpressRoute private peering. The tunnel is created between Azure VMs running Windows and on-premises Windows hosts. The steps in this article for this configuration use group policy objects. While it's possible to create this configuration without using organizational units (OUs) and group policy objects (GPOs). The combination of OUs and GPOs help simplify the control of your security policies and allows you to quickly scale up. The steps in this article assume you already have an Active Directory configuration and you're familiar with using OUs and GPOs.
About this configuration
The configuration in the following steps uses a single Azure virtual network (VNet) with ExpressRoute private peering. However, this configuration can span over other Azure VNets and on-premises networks. This article helps you define an IPsec encryption policy that you can apply to a group of Azure VMs or on-premises hosts. These Azure VMs or on-premises hosts are part of the same OU. You configure encryption between the Azure VMs (vm1 and vm2), and the on-premises host1 only for HTTP traffic with destination port 8080. Different types of IPsec policy can be created based on your requirements.
Working with OUs
The security policy associated with an OU is pushed to the computers via GPO. A few advantages to using OUs, rather than applying policies to a single host, are:
- Associating a policy with an OU guarantees that computers that belong to the same OU get the same policies.
- Changing the security policy associated with OU applies the changes to all hosts in the OU.
Diagrams
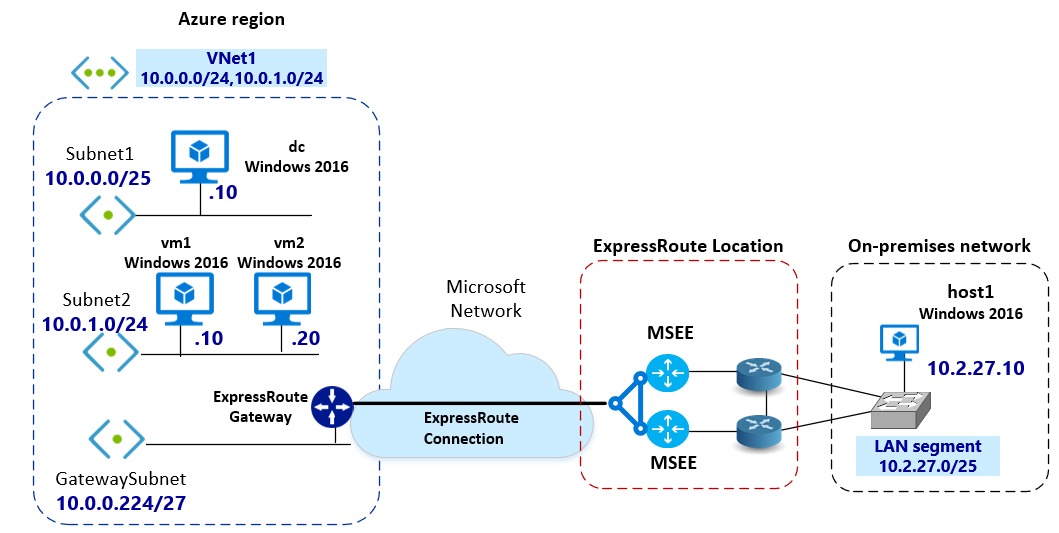
The following diagram shows the interconnection and assigned IP address space. The Azure VMs and the on-premises host are running Windows 2016. The Azure VMs and the on-premises host1 are part of the same domain. The Azure VMs and the on-premises hosts can resolve names properly using DNS.
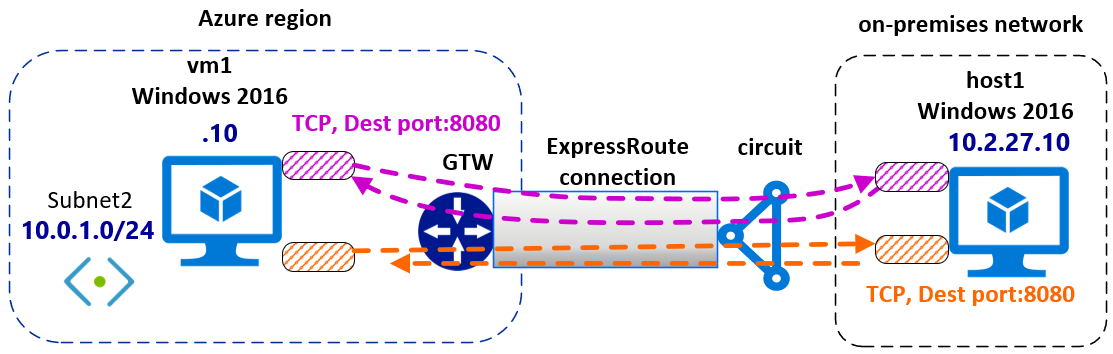
This diagram shows the IPsec tunnels in transit in ExpressRoute private peering.
Working with IPsec policy
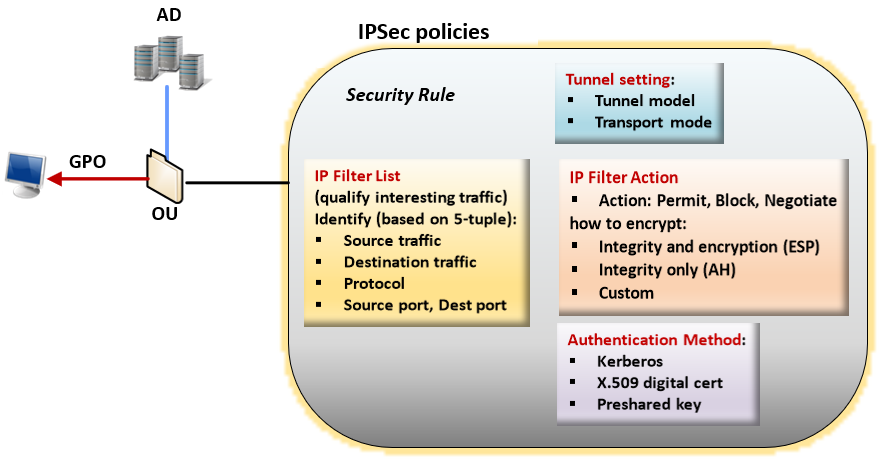
In Windows, encryption is associated with IPsec policy. IPsec policy determines which IP traffic is secured and the security mechanism applied to the IP packets. IPsec policies are composed of the following items: Filter Lists, Filter Actions, and Security Rules.
When configuring IPsec policy, it's important to understand the following IPsec policy terminology:
IPsec policy: A collection of rules. Only one policy can be active ("assigned") at any particular time. Each policy can have one or more rules, all of which can be active simultaneously. A computer can be assigned only one active IPsec policy at given time. However, within the IPsec policy, you can define multiple actions that may be taken in different situations. Each set of IPsec rules is associated with a filter list that affects the type of network traffic to which the rule applies.
Filter lists: Filter lists are bundle of one or more filters. One list can contain multiple filters. A filter defines if the communication gets blocked, allowed, or secured based on the following criteria: IP address ranges, protocols, or even specific ports. Each filter matches a particular set of conditions; for example, packets sent from a particular subnet to a particular computer on a specific destination port. When network conditions match one or more of those filters, the filter list is activated. Each filter is defined inside a specific filter list. Filters can't be shared between filter lists. However, a given filter list can be incorporated into several IPsec policies.
Filter actions: A security method defines a set of security algorithms, protocols, and key a computer offers during IKE negotiations. Filter actions are lists of security methods, ranked in order of preference. When a computer negotiates an IPsec session, it accepts or sends proposals based on the security setting stored in filter actions list.
Security rules: Rules govern how and when an IPsec policy protects communication. It uses filter list and filter actions to create an IPsec rule to build the IPsec connection. Each policy can have one or more rules, all of which can be active simultaneously. Each rule contains a list of IP filters and a collection of security actions that take place upon a match with that filter list:
- IP Filter Actions
- Authentication methods
- IP tunnel settings
- Connection types
Before you begin
Ensure that you meet the following prerequisites:
You must have a functioning Active Directory configuration that you can use to implement Group Policy settings. For more information about GPOs, see Group Policy Objects.
You must have an active ExpressRoute circuit.
- For information about creating an ExpressRoute circuit, see Create an ExpressRoute circuit.
- Verify that the circuit get enabled by your connectivity provider.
- Verify that you have Azure private peering configured for your circuit. See the configure routing article for routing instructions.
- Verify that you have a VNet and a virtual network gateway created and fully provisioned. Follow the instructions to create a virtual network gateway for ExpressRoute. A virtual network gateway for ExpressRoute uses the GatewayType ExpressRoute, not VPN.
The ExpressRoute virtual network gateway must be connected to the ExpressRoute circuit. For more information, see Connect a VNet to an ExpressRoute circuit.
Verify that the Azure Windows VMs are deployed to the VNet.
Verify that there's connectivity between the on-premises hosts and the Azure VMs.
Verify that the Azure Windows VMs and the on-premises hosts can use DNS to properly resolve names.
Workflow
- Create a GPO and associate it to the OU.
- Define an IPsec Filter Action.
- Define an IPsec Filter List.
- Create an IPsec Policy with Security Rules.
- Assign the IPsec GPO to the OU.
Example values
Domain Name: ipsectest.com
OU: IPSecOU
On-premises Windows computer: host1
Azure Windows VMs: vm1, vm2
1. Create a GPO
Create a new GPO linked to an OU by opening the Group Policy Management snap-in. Then locate the OU to which the GPO gets linked. In the example, the OU is named IPSecOU.
In the Group Policy Management snap-in, select the OU, and right-click. In the dropdown, select "Create a GPO in this domain, and Link it here…".
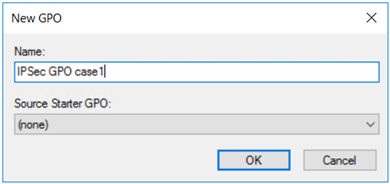
Name the GPO an intuitive name so that you can easily locate it later. Select OK to create and link the GPO.
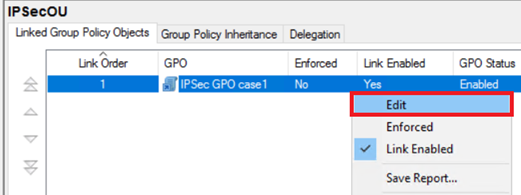
2. Enable the GPO link
To apply the GPO to the OU, the GPO must not only be linked to the OU, but the link must be also enabled.
Locate the GPO that you created, right-click, and select Edit from the dropdown.
To apply the GPO to the OU, select Link Enabled.
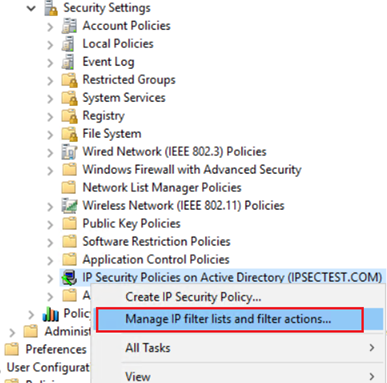
3. Define the IP filter action
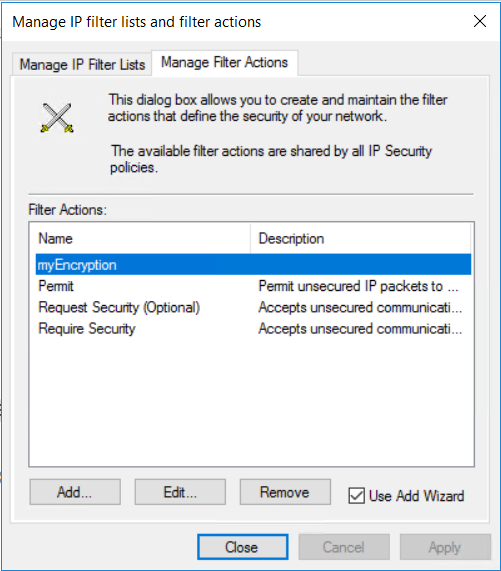
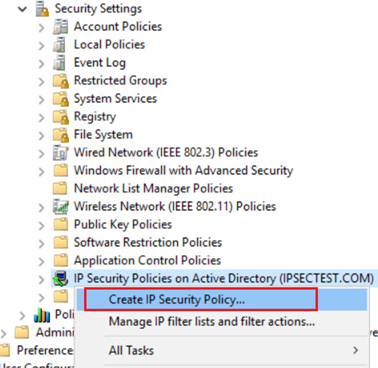
From the drop-down, right-click IP Security Policy on Active Directory, and then select Manage IP filter lists and filter actions....
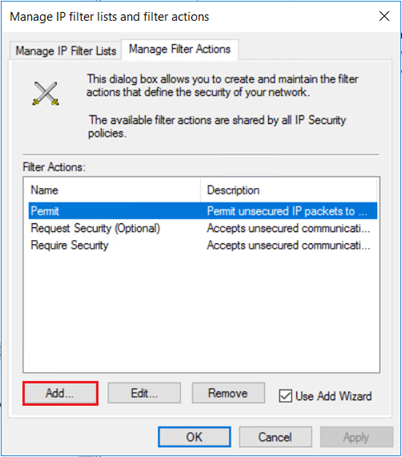
On the "Manage filter Actions" tab, select Add.
On the IP Security Filter Action wizard, select Next.
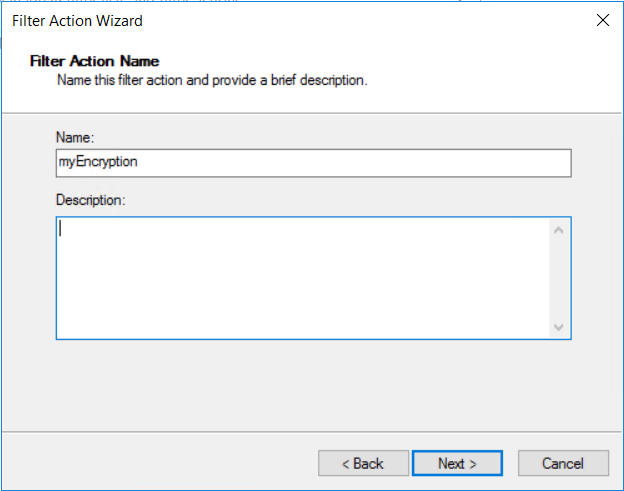
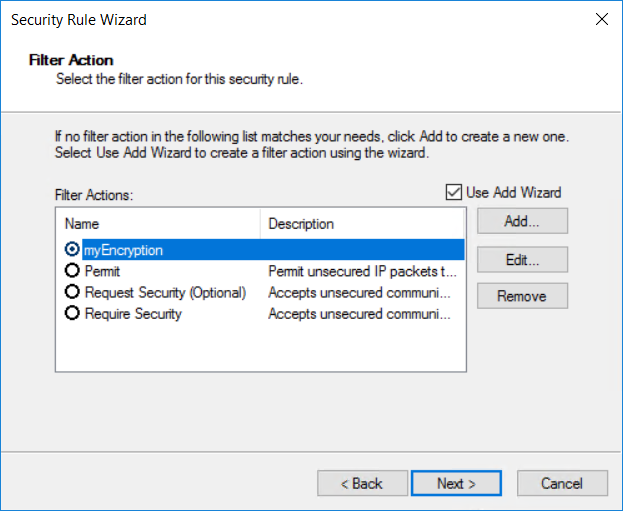
Name the filter action an intuitive name so that you can find it later. In this example, the filter action is named myEncryption. You can also add a description. Then, select Next.
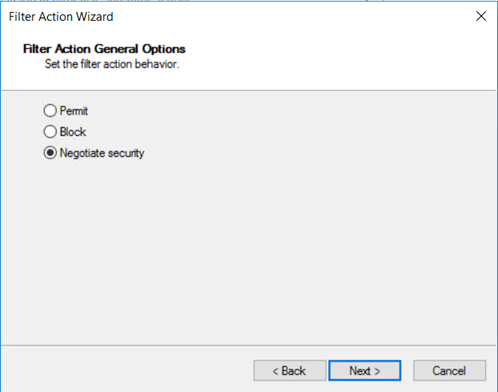
Negotiate security lets you define the behavior if IPsec can't be established with another computer. Select Negotiate security, then select Next.
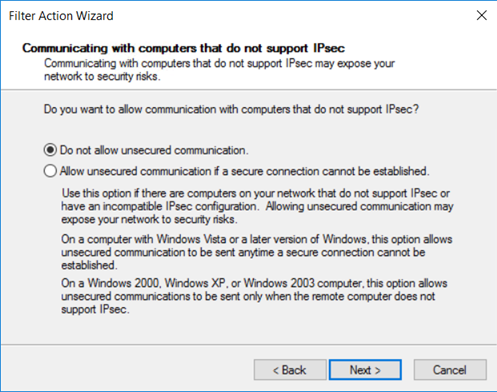
On the Communicating with computers that do not support IPsec page, select Do not allow unsecured communication, then select Next.
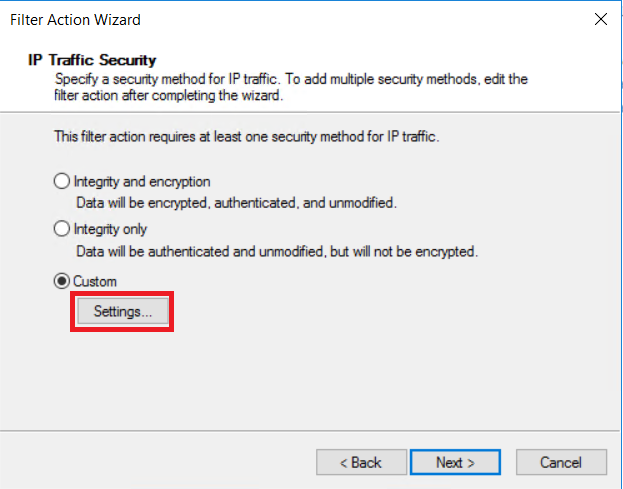
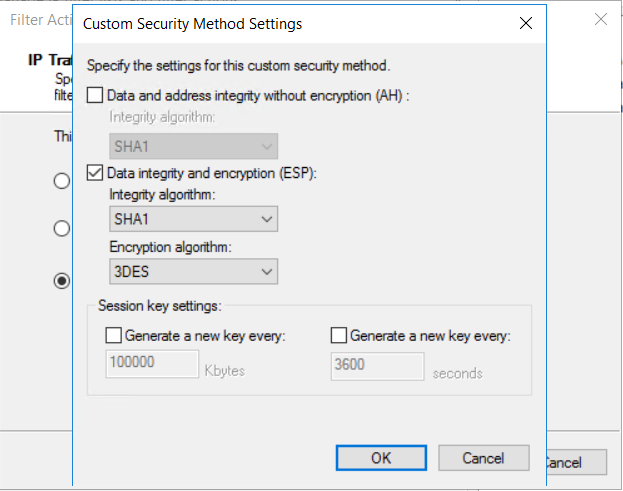
On the IP Traffic and Security page, select Custom, then select Settings....
On the Custom Security Method Settings page, select Data integrity and encryption (ESP): SHA1, 3DES. Then, select OK.
On the Manage Filter Actions page, you can see that the myEncryption filter was successfully added. Select Close.
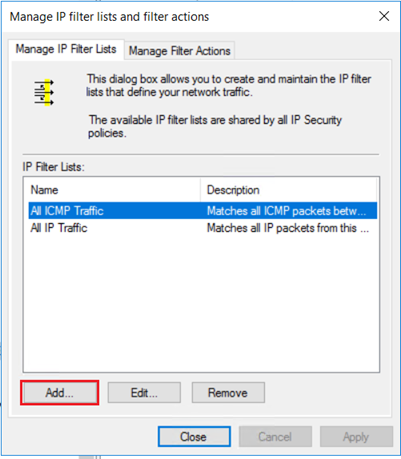
4. Define an IP filter list
Create a filter list that specifies encrypted HTTP traffic with destination port 8080.
To qualify which types of traffic must be encrypted, use an IP filter list. In the Manage IP Filter Lists tab, select Add to add a new IP filter list.
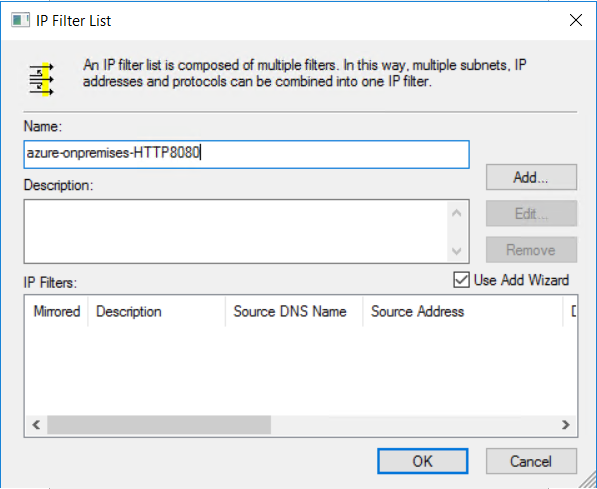
In the Name: field, type a name for your IP filter list. For example, azure-onpremises-HTTP8080. Then, select Add.
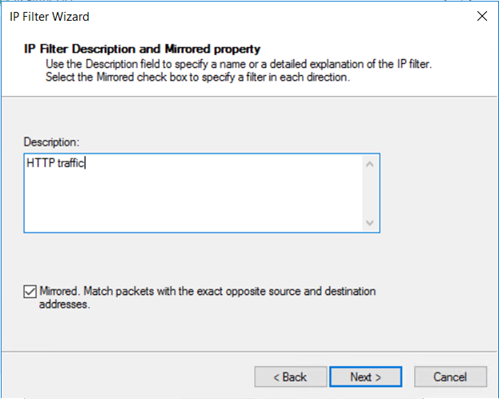
On the IP Filter Description and Mirrored property page, select Mirrored. The mirrored setting matches packets going in both directions, which allows for two-way communication. Then select Next.
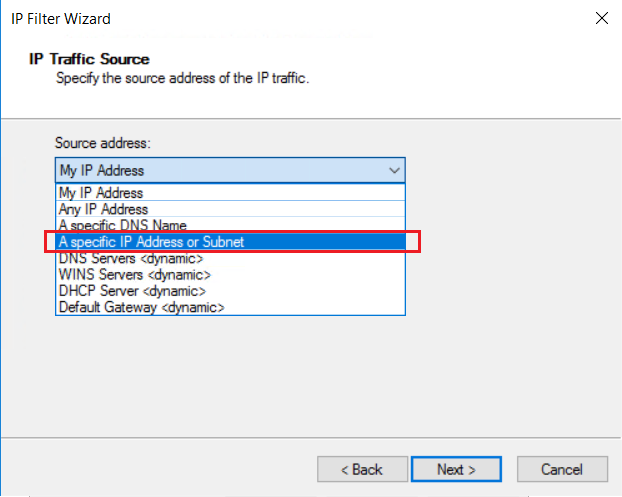
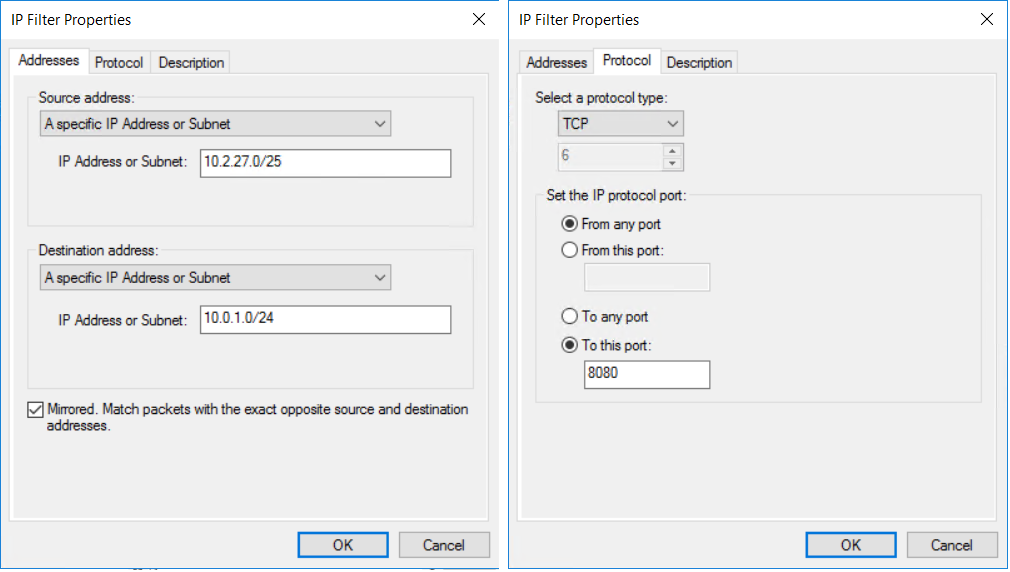
On the IP Traffic Source page, from the Source address: dropdown, choose A specific IP Address or Subnet.
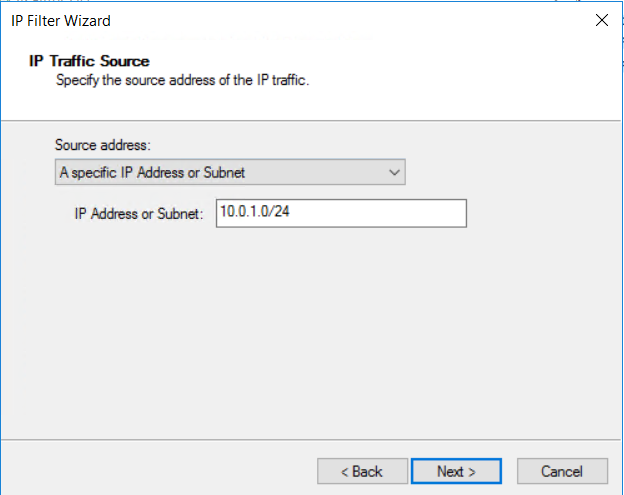
Specify the source address IP Address or Subnet: of the IP traffic, then select Next.
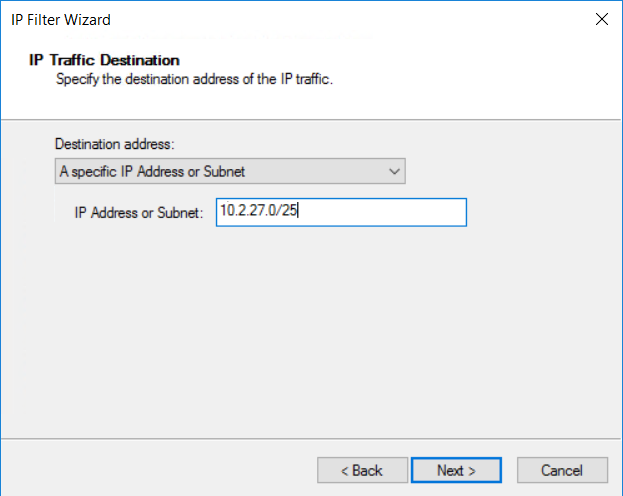
Specify the Destination address: IP Address or Subnet. Then, select Next.
On the IP Protocol Type page, select TCP. Then, select Next.
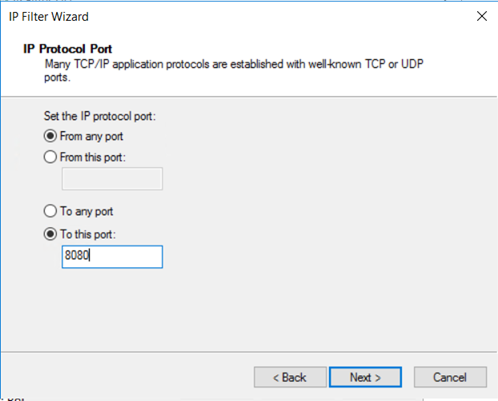
On the IP Protocol Port page, select From any port and To this port:. Type 8080 in the text box. These settings specify only the HTTP traffic on destination port 8080 gets encrypted. Then, select Next.
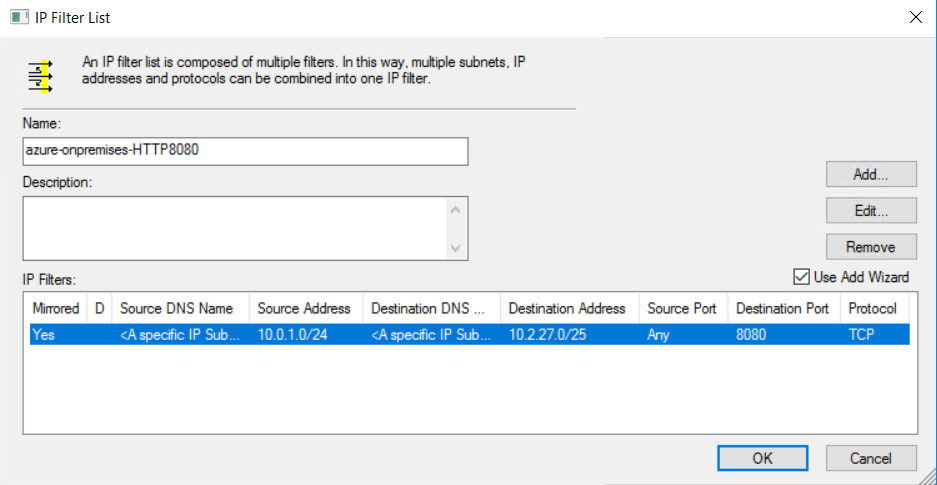
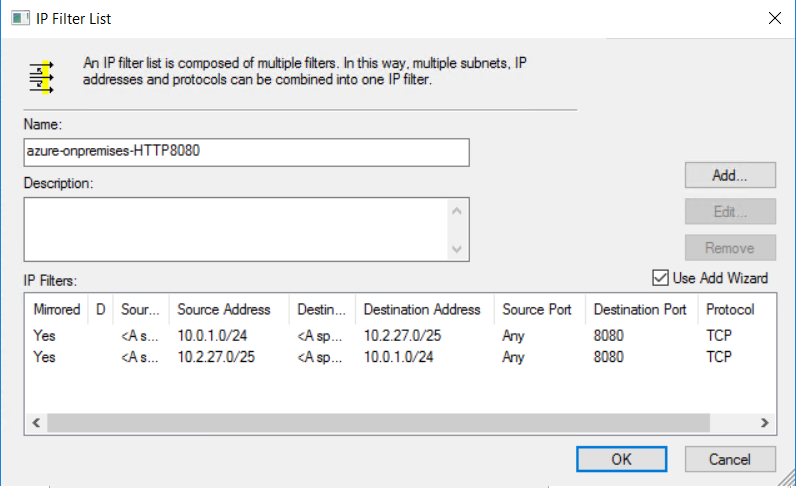
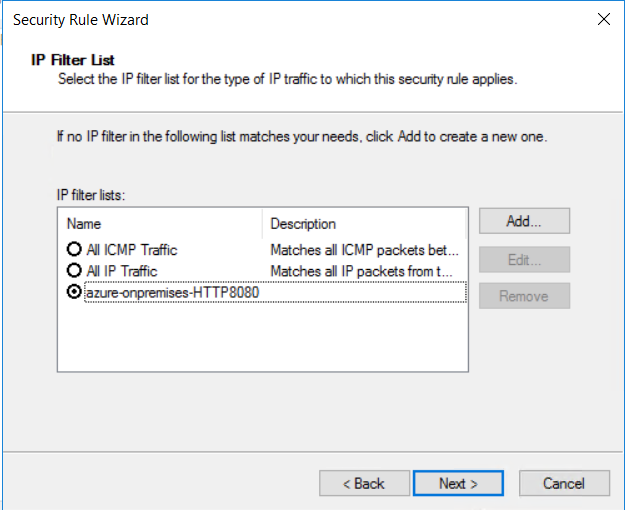
View the IP filter list. The configuration of the IP Filter List azure-onpremises-HTTP8080 triggers encryption for all traffic that matches the following criteria:
- Any source address in 10.0.1.0/24 (Azure Subnet2)
- Any destination address in 10.2.27.0/25 (on-premises subnet)
- TCP protocol
- Destination port 8080
5. Edit the IP filter list
To encrypt the same type of traffic from the on-premises host to the Azure VM, you need a second IP filter. Follow the same steps you used for setting up the first IP filter and create a new IP filter. The only differences are the source subnet and destination subnet.
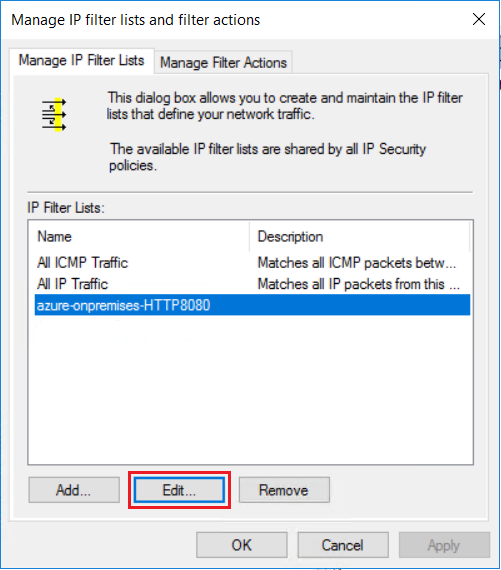
To add a new IP filter to the IP Filter List, select Edit.
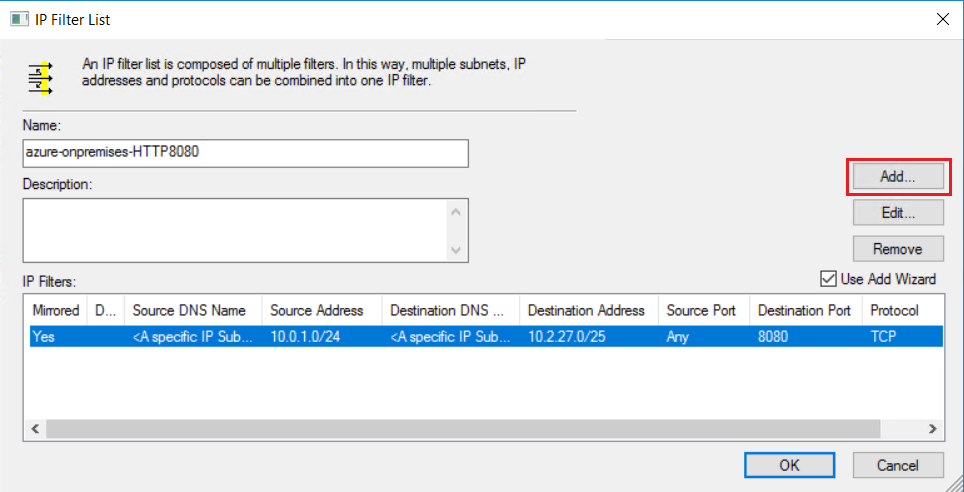
On the IP Filter List page, select Add.
Create a second IP filter using the settings in the following example:
After you create the second IP filter, the IP filter list will look like this:
If encryption is required between an on-premises location and an Azure subnet to protect an application. Instead of modifying the existing IP filter list, you can add a new IP filter list. Associating two or more IP filters lists to the same IPsec policy can provide you with more flexibility. You can modify or remove an IP filter list without affecting the other IP filter lists.
6. Create an IPsec security policy
Create an IPsec policy with security rules.
Select the IPSecurity Policies on Active directory that is associated with the OU. Right-click, and select Create IP Security Policy.
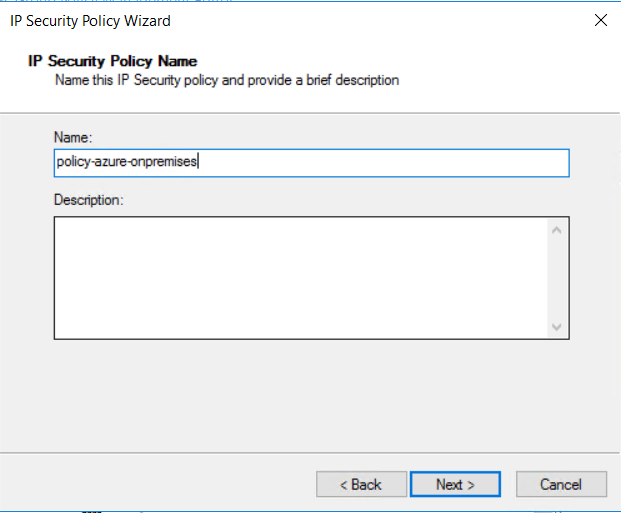
Name the security policy. For example, policy-azure-onpremises. Then, select Next.
Select Next without selecting the checkbox.
Verify that the Edit properties checkbox is selected, and then select Finish.
7. Edit the IPsec security policy
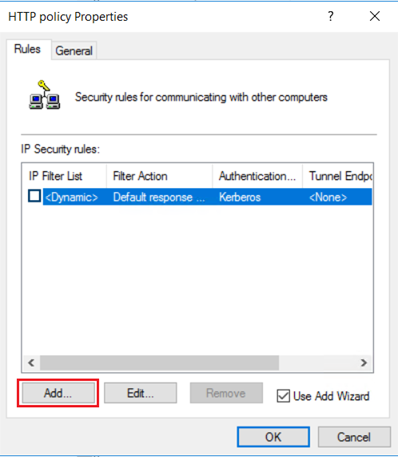
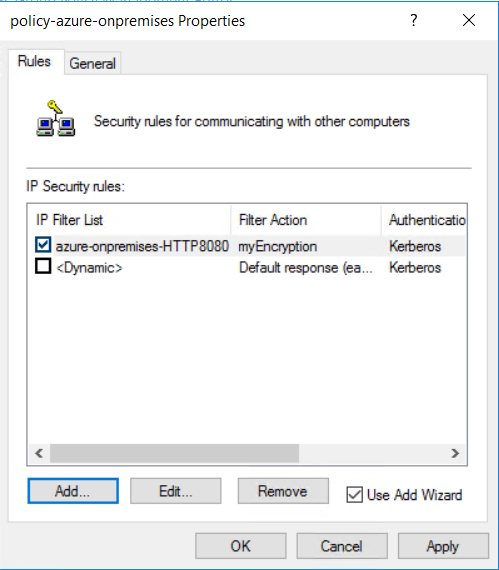
Add to the IPsec policy the IP Filter List and Filter Action that you previously configured.
On the HTTP policy Properties Rules tab, select Add.
On the Welcome page, select Next.
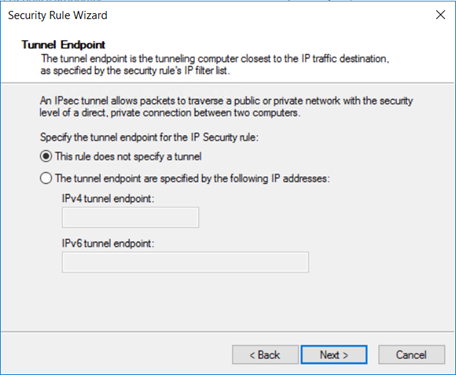
A rule provides the option to define the IPsec mode: tunnel mode or transport mode.
In tunnel mode, the original packet gets encapsulated with a set of IP headers. Tunnel mode protects the internal routing information by encrypting the IP header of the original packet. Tunnel mode is widely implemented between gateways in site-to-site VPN scenarios. Tunnel mode is in most of cases used for end-to-end encryption between hosts.
Transport mode encrypts only the payload and ESP trailer; the IP header of the original packet isn't encrypted. In transport mode, the IP source and IP destination of the packets are unchanged.
Select This rule does not specify a tunnel, and then select Next.
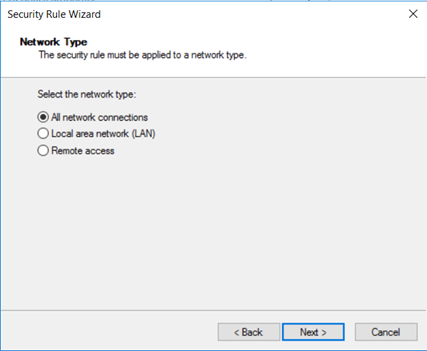
Network Type defines which network connection associates with the security policy. Select All network connections, and then select Next.
Select the IP filter list that you created previously, azure-onpremises-HTTP8080, and then select Next.
Select the existing Filter Action myEncryption that you created previously.
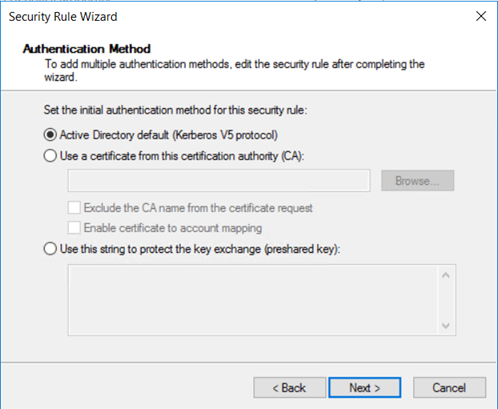
Windows supports four distinct types of authentications: Kerberos, certificates, NTLMv2, and preshared key. Since we're working with domain-joined hosts, select Active Directory default (Kerberos V5 protocol), and then select Next.
The new policy creates the security rule: azure-onpremises-HTTP8080. Select OK.
The IPsec policy requires all HTTP connections on the destination port 8080 to use IPsec transport mode. Since HTTP is a clear text protocol, having the security policy enabled, ensures data is encrypted when being transferred through the ExpressRoute private peering. IPsec policy for Active Directory is more complex to configure than Windows Firewall with Advanced Security. However, it allows for more customization of the IPsec connection.
8. Assign the IPsec GPO to the OU
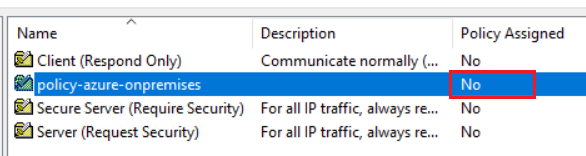
View the policy. The security group policy is defined, but not yet assigned.
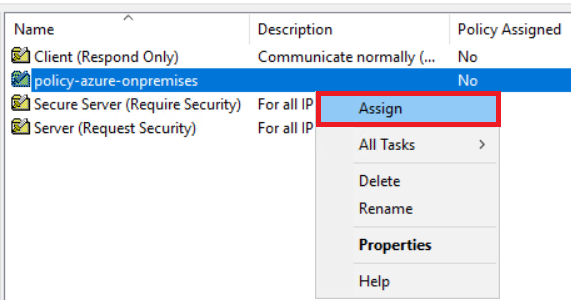
To assign the security group policy to the OU IPSecOU, right-click the security policy and chose Assign. Every computer that belongs to the OU has the security group policy assigned.
Check traffic encryption
To check out the encryption GPO applied on the OU, install IIS on all Azure VMs and in the host1. Every IIS is customized to answer to HTTP requests on port 8080. To verify encryption, you can install a network sniffer (like Wireshark) in all computers in the OU. A PowerShell script works as an HTTP client to generate HTTP requests on port 8080:
$url = "http://10.0.1.20:8080"
while ($true) {
try {
[net.httpWebRequest]
$req = [net.webRequest]::create($url)
$req.method = "GET"
$req.ContentType = "application/x-www-form-urlencoded"
$req.TimeOut = 60000
$start = get-date
[net.httpWebResponse] $res = $req.getResponse()
$timetaken = ((get-date) - $start).TotalMilliseconds
Write-Output $res.Content
Write-Output ("{0} {1} {2}" -f (get-date), $res.StatusCode.value__, $timetaken)
$req = $null
$res.Close()
$res = $null
} catch [Exception] {
Write-Output ("{0} {1}" -f (get-date), $_.ToString())
}
$req = $null
# uncomment the line below and change the wait time to add a pause between requests
#Start-Sleep -Seconds 1
}
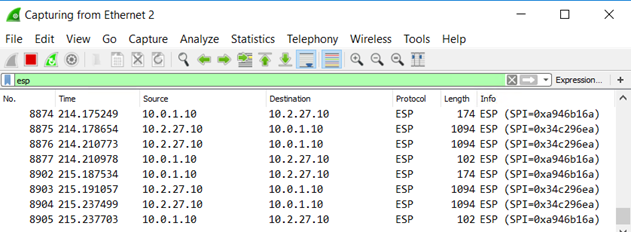
The following network capture shows the results for on-premises host1 with display filter ESP to match only the encrypted traffic:
If you run the PowerShell script on-premises (HTTP client), the network capture in the Azure VM shows a similar trace.
Next steps
For more information about ExpressRoute, see the ExpressRoute FAQ.