Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
A hub and spoke network is one of the building blocks of a highly available multiple location network infrastructure. The most common deployment of a hub and spoke network is done with the intention of routing all inter-spoke and outbound internet traffic through the central hub. The purpose is to inspect all of the traffic traversing the network with a Network Virtual Appliance (NVA) for security scanning and packet inspection.
For outbound traffic to the internet, the network virtual appliance would typically have one network interface with an assigned public IP address. The NVA after inspecting the outbound traffic forwards the traffic out the public interface and to the internet. Azure NAT Gateway eliminates the need for the public IP address assigned to the NVA. Associating a NAT gateway with the public subnet of the NVA changes the routing for the public interface to route all outbound internet traffic through the NAT gateway. The elimination of the public IP address increases security and allows for the scaling of outbound source network address translation (SNAT) with multiple public IP addresses and or public IP prefixes.
Important
The NVA used in this article is for demonstration purposes only and is simulated with an Ubuntu virtual machine. The solution doesn't include a load balancer for high availability of the NVA deployment. Replace the Ubuntu virtual machine in this article with an NVA of your choice. Consult the vendor of the chosen NVA for routing and configuration instructions. A load balancer and availability zones are recommended for a highly available NVA infrastructure.
In this tutorial, you learn how to:
- Create a NAT gateway.
- Create a hub and spoke virtual network.
- Create a simulated Network Virtual Appliance (NVA).
- Force all traffic from the spokes through the hub.
- Force all internet traffic in the hub and the spokes out the NAT gateway.
- Test the NAT gateway and inter-spoke routing.
Prerequisites
- An Azure account with an active subscription. Create an account for trial.
Create a resource group
Create a resource group to contain all resources for this quickstart.
Sign in to the Azure portal.
In the search box at the top of the portal enter Resource group. Select Resource groups in the search results.
Select + Create.
In the Basics tab of Create a resource group, enter or select the following information.
Setting Value Subscription Select your subscription Resource group test-rg Region China North 3 Select Review + create.
Select Create.
Create a NAT gateway
All outbound internet traffic traverses the NAT gateway to the internet. Use the following example to create a NAT gateway for the hub and spoke network.
Sign in to the Azure portal.
In the search box at the top of the Azure portal, enter Public IP address. Select Public IP addresses in the search results.
Select Create.
Enter the following information in Create public IP address.
Setting Value Subscription Select your subscription. Resource group Select your resource group. The example uses test-rg. Region Select a region. This example uses China North 3. Name Enter public-ip-nat. IP version Select IPv4. SKU Select Standard. Availability zone Select Zone-redundant. Tier Select Regional. Select Review + create and then select Create.
In the search box at the top of the Azure portal, enter NAT gateway. Select NAT gateways in the search results.
Select Create.
Enter or select the following information in the Basics tab of Create network address translation (NAT) gateway.
Setting Value Project details Subscription Select your subscription. Resource group Select test-rg or your resource group. Instance details NAT gateway name Enter nat-gateway. Region Select your region. This example uses China North 3. Availability zone Select a Zone or No zone. TCP idle timeout (minutes) Leave the default of 4. Select Next.
In the Outbound IP tab, select public IP addresses or prefixes.
Select Next.
In the Subnet tab, in Virtual network, select vnet-1.
Select specific subnets, select subnet-1.
Select Review + create, then select Create.
Create hub virtual network
The hub virtual network is the central network of the solution. The hub network contains the NVA appliance and a public and private subnet. The NAT gateway is assigned to the public subnet during the creation of the virtual network. An Azure Bastion host is configured as part of the following example. The bastion host is used to securely connect to the NVA virtual machine and the test virtual machines deployed in the spokes later in the article.
Sign in to the Azure portal.
In the search box at the top of the Azure portal, enter Virtual network. Select Virtual networks in the search results.
Select Create.
Enter or select the following information in the Basics tab of Create virtual network.
Setting Value Project details Subscription Select your subscription. Resource group Select test-rg or your resource group. Instance details Name Enter vnet-1. Region Select your region. This example uses China North 3. Select the IP Addresses tab, or select Next: Security, then Next: IP Addresses.
In Subnets select the default subnet.
Enter or select the following information in Edit subnet.
Setting Value Subnet purpose Leave the default. Name Enter subnet-1. Leave the rest of the settings as default, then select Save.
Select + Add a subnet.
In Add a subnet enter or select the following information.
Setting Value Subnet purpose Select Azure Bastion. Leave the rest of the settings as default, then select Add.
Select Review + create, then select Create.
Create Azure Bastion host
Azure Bastion provides secure RDP and SSH connectivity to virtual machines over TLS without requiring public IP addresses on the VMs.
In the search box at the top of the Azure portal, enter Bastion. Select Bastions in the search results.
Select Create.
Enter or select the following information in the Basics tab of Create a Bastion.
Setting Value Project details Subscription Select your subscription. Resource group Select test-rg or your resource group. Instance details Name Enter bastion. Region Select your region. This example uses China North 3. Tier Select Basic. Virtual network Select vnet-1. Subnet Select AzureBastionSubnet. Select Review + create, then select Create.
Create simulated NVA virtual machine
The simulated NVA acts as a virtual appliance to route all traffic between the spokes and hub and traffic outbound to the internet. An Ubuntu virtual machine is used for the simulated NVA. Use the following example to create the simulated NVA and configure the network interfaces.
In the search box at the top of the portal, enter Virtual machine. Select Virtual machines in the search results.
Select + Create then Azure virtual machine.
In Create a virtual machine enter or select the following information in the Basics tab:
Setting Value Project details Subscription Select your subscription. Resource group Select test-rg. Instance details Virtual machine name Enter vm-nva. Region Select China North 3. Availability options Select No infrastructure redundancy required. Security type Select Standard. Image Select Ubuntu Server 24.04 LTS - Gen2. Size Select a size. Administrator account Authentication type Select SSH public key. Username Enter a username. SSH public key source Select Generate new key pair. SSH Key Type Leave the default of RSA SSH Format. Key pair name Enter ssh-key. Inbound port rules Public inbound ports Select None. Select Next: Disks then Next: Networking.
In the Networking tab, enter or select the following information:
Setting Value Network interface Virtual network Select vnet-hub. Subnet Select subnet-public (10.0.253.0/28). Public IP Select None. NIC network security group Select Advanced. Configure network security group Select Create new.
In Name enter nsg-nva.
Select OK.Leave the rest of the options at the defaults and select Review + create.
Select Create.
The Generate new key pair dialog box appears. Select Download private key and create resource.
The private key will download to your local machine. The private key is needed in later steps for connecting to the virtual machine with Azure Bastion. The name of the private key file is the name you entered in the Key pair name field. In this example, the private key file is named ssh-key.
Configure virtual machine network interfaces
The IP configuration of the primary network interface of the virtual machine is set to dynamic by default. Use the following example to change the primary network interface IP configuration to static and add a secondary network interface for the private interface of the NVA.
In the search box at the top of the portal, enter Virtual machine. Select Virtual machines in the search results.
Select vm-nva.
In the Overview select Stop if the virtual machine is running.
Expand Networking then select Network settings.
In Network settings select the network interface name next to Network Interface:. The interface name is the virtual machine name and random numbers and letters. In this example, the interface name is vm-nva271.
In the network interface properties, select IP configurations in Settings.
Select the box next to Enable IP forwarding.
Select Apply.
When the apply action completes, select ipconfig1.
In Private IP address settings in ipconfig1 select Static.
In Private IP address enter 10.0.253.10.
Select Save.
When the save action completes, return to the networking configuration for vm-nva.
In Network settings of vm-nva select Attach network interface.
Select Create and attach network interface.
In Create network interface enter or select the following information:
Setting Value Project details Resource group Select test-rg. Network interface Name Enter nic-private. Subnet Select subnet-private (10.0.0.0/24). NIC network security group Select Advanced. Configure network security group Select nsg-nva. Private IP address assignment Select Static. Private IP address Enter 10.0.0.10. Select Create.
Start the virtual machine.
Configure virtual machine software
The routing for the simulated NVA uses IP tables and internal NAT in the Ubuntu virtual machine. Connect to the NVA virtual machine with Azure Bastion to configure IP tables and the routing configuration.
In the Azure portal, search for and select virtual machines.
On the Virtual machines page, select vm-nva.
On the VM's Overview page, select Connect then Connect via Bastion.
In the Bastion connection screen, change Authentication Type to SSH Private Key from Local File.
Enter the Username that you used when creating the virtual machine. In this example, the user is named azureuser, replace with the username you created.
In Local File, select the folder icon and browse to the private key file that was generated when you created the VM. The private key file is typically named
id_rsaorid_rsa.pemorssh-key.pem.Select Connect.
Enter the following information at the prompt of the virtual machine to enable IP forwarding:
sudo nano /etc/sysctl.confIn the Nano editor, remove the
#from the linenet.ipv4.ip_forward=1:# Uncomment the next line to enable packet forwarding for IPv4 net.ipv4.ip_forward=1Press Ctrl + O to save the file.
Press Ctrl + X to exit the editor.
Enter the following information to enable internal NAT in the virtual machine:
sudo iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE sudo apt-get update sudo apt install iptables-persistentSelect Yes twice.
sudo su iptables-save > /etc/iptables/rules.v4 exitUse Nano to edit the configuration with the following information:
sudo nano /etc/rc.localAdd the following line to the configuration file:
/sbin/iptables-restore < /etc/iptables/rules.v4Press Ctrl + O to save the file.
Press Ctrl + X to exit the editor.
Reboot the virtual machine:
sudo reboot
Create hub network route table
Route tables are used to overwrite Azure's default routing. Create a route table to force all traffic within the hub private subnet through the simulated NVA.
In the search box at the top of the portal, enter Route table. Select Route tables in the search results.
Select + Create.
In Create Route table enter or select the following information:
Setting Value Project details Subscription Select your subscription. Resource group Select test-rg. Instance details Region Select China North 3. Name Enter route-table-nat-hub. Propagate gateway routes Leave the default of Yes. Select Review + create.
Select Create.
In the search box at the top of the portal, enter Route table. Select Route tables in the search results.
Select route-table-nat-hub.
Expand Settings then select Routes.
Select + Add in Routes.
Enter or select the following information in Add route:
Setting Value Route name Enter default-via-nat-hub. Destination type Select IP Addresses. Destination IP addresses/CIDR ranges Enter 0.0.0.0/0. Next hop type Select Virtual appliance. Next hop address Enter 10.0.0.10.
This is the IP address you added to the private interface of the NVA in the previous steps..Select Add.
Select Subnets in Settings.
Select + Associate.
Enter or select the following information in Associate subnet:
Setting Value Virtual network Select vnet-hub (test-rg). Subnet Select subnet-private. Select OK.
Create spoke one virtual network
Create another virtual network in a different region for the first spoke of the hub and spoke network.
In the search box at the top of the portal, enter Virtual network. Select Virtual networks in the search results.
Select + Create.
In the Basics tab of Create virtual network, enter or select the following information:
Setting Value Project details Subscription Select your subscription. Resource group Select test-rg. Instance details Name Enter vnet-spoke-1. Region Select China North 2. Select Next to proceed to the Security tab.
Select Next to proceed to the IP addresses tab.
In the IP Addresses tab in IPv4 address space, select Delete address space to delete the address space that is auto populated.
Select Add IPv4 address space.
In IPv4 address space enter 10.1.0.0. Leave the default of /16 (65,536 addresses) in the mask selection.
Select + Add a subnet.
In Add a subnet enter or select the following information:
Setting Value Subnet purpose Leave the default Default. Name Enter subnet-private. IPv4 IPv4 address range Leave the default of 10.1.0.0/16. Starting address Leave the default of 10.1.0.0. Size Leave the default of /24(256 addresses). Select Add.
Select Review + create.
Select Create.
Create peering between hub and spoke one
A virtual network peering is used to connect the hub to spoke one and spoke one to the hub. Use the following example to create a two-way network peering between the hub and spoke one.
In the search box at the top of the portal, enter Virtual network. Select Virtual networks in the search results.
Select vnet-hub.
Expand Settings, then select Peerings.
Select + Add.
Enter or select the following information in Add peering:
Setting Value Remote virtual network summary Peering link name Enter vnet-spoke-1-to-vnet-hub. Virtual network deployment model Leave the default of Resource manager. Subscription Select your subscription. Virtual network Select vnet-spoke-1 (test-rg). Remote virtual network peering settings Allow 'vnet-spoke-1' to access 'vnet-hub' Leave the default of Selected. Allow 'vnet-spoke-1' to receive forwarded traffic from 'vnet-hub' Select the checkbox. Allow gateway or route server in 'vnet-spoke-1' to forward traffic to 'vnet-hub' Leave the default of Unselected. Enable 'vnet-spoke-1' to use 'vnet-hub's' remote gateway or route server Leave the default of Unselected. Local virtual network summary Peering link name Enter vnet-hub-to-vnet-spoke-1. Local virtual network peering settings Allow 'vnet-hub' to access 'vnet-spoke-1' Leave the default of Selected. Allow 'vnet-hub' to receive forwarded traffic from 'vnet-spoke-1' Select the checkbox. Allow gateway or route server in 'vnet-hub' to forward traffic to 'vnet-spoke-1' Leave the default of Unselected. Enable 'vnet-hub' to use 'vnet-spoke-1's' remote gateway or route server Leave the default of Unselected. Select Add.
Select Refresh and verify Peering status is Connected.
Create spoke one network route table
Create a route table to force all inter-spoke and internet egress traffic through the simulated NVA in the hub virtual network.
In the search box at the top of the portal, enter Route table. Select Route tables in the search results.
Select + Create.
In Create Route table enter or select the following information:
Setting Value Project details Subscription Select your subscription. Resource group Select test-rg. Instance details Region Select China North 2. Name Enter route-table-nat-spoke-1. Propagate gateway routes Leave the default of Yes. Select Review + create.
Select Create.
In the search box at the top of the portal, enter Route table. Select Route tables in the search results.
Select route-table-nat-spoke-1.
Expand Settings, then select Routes.
Select + Add in Routes.
Enter or select the following information in Add route:
Setting Value Route name Enter default-via-nat-spoke-1. Destination type Select IP Addresses. Destination IP addresses/CIDR ranges Enter 0.0.0.0/0. Next hop type Select Virtual appliance. Next hop address Enter 10.0.0.10.
This is the IP address you added to the private interface of the NVA in the previous steps..Select Add.
Select Subnets in Settings.
Select + Associate.
Enter or select the following information in Associate subnet:
Setting Value Virtual network Select vnet-spoke-1 (test-rg). Subnet Select subnet-private. Select OK.
Create spoke one test virtual machine
A Windows Server 2022 virtual machine is used to test the outbound internet traffic through the NAT gateway and inter-spoke traffic in the hub and spoke network. Use the following example to create a Windows Server 2022 virtual machine.
In the search box at the top of the portal, enter Virtual machine. Select Virtual machines in the search results.
Select + Create then Azure virtual machine.
In Create a virtual machine enter or select the following information in the Basics tab:
Setting Value Project details Subscription Select your subscription. Resource group Select test-rg. Instance details Virtual machine name Enter vm-spoke-1. Region Select China North 2. Availability options Select No infrastructure redundancy required. Security type Select Standard. Image Select Windows Server 2022 Datacenter - Gen2. Size Select a size. Administrator account Authentication type Select Password. Username Enter a username. Password Enter a password. Confirm password Reenter password. Inbound port rules Public inbound ports Select None. Select Next: Disks then Next: Networking.
In the Networking tab, enter or select the following information:
Setting Value Network interface Virtual network Select vnet-spoke-1. Subnet Select subnet-private (10.1.0.0/24). Public IP Select None. NIC network security group Select Advanced. Configure network security group Select Create new.
Enter nsg-spoke-1.Inbound rules Select + Add an inbound rule.
Select HTTP in Service.
Select Add.
Select OK.Select OK.
Leave the rest of the options at the defaults and select Review + create.
Select Create.
Wait for the virtual machine to finishing deploying before continuing to the next steps.
Install IIS on spoke one test virtual machine
IIS is installed on the Windows Server 2022 virtual machine to test outbound internet traffic through the NAT gateway and inter-spoke traffic in the hub and spoke network.
In the search box at the top of the portal, enter Virtual machine. Select Virtual machines in the search results.
Select vm-spoke-1.
Expand Operations then select Run command.
Select RunPowerShellScript.
Enter the following script in Run Command Script:
# Install IIS server role Install-WindowsFeature -name Web-Server -IncludeManagementTools # Remove default htm file Remove-Item C:\inetpub\wwwroot\iisstart.htm # Add a new htm file that displays server name Add-Content -Path "C:\inetpub\wwwroot\iisstart.htm" -Value $("Hello World from " + $env:computername)Select Run.
Wait for the script to complete before continuing to the next step. It can take a few minutes for the script to complete.
When the script completes, the Output displays the following:
Success Restart Needed Exit Code Feature Result ------- -------------- --------- -------------- True No Success {Common HTTP Features, Default Document, D...
Create the second spoke virtual network
Create the second virtual network for the second spoke of the hub and spoke network.
In the search box at the top of the portal, enter Virtual network. Select Virtual networks in the search results.
Select + Create.
In the Basics tab of Create virtual network, enter or select the following information:
Setting Value Project details Subscription Select your subscription. Resource group Select test-rg. Instance details Name Enter vnet-spoke-2. Region Select China North 2. Select Next to proceed to the Security tab.
Select Next to proceed to the IP addresses tab.
In the IP Addresses tab in IPv4 address space, select Delete address space to delete the address space that is auto populated.
Select Add IPv4 address space.
In IPv4 address space enter 10.2.0.0. Leave the default of /16 (65,536 addresses) in the mask selection.
Select + Add a subnet.
In Add a subnet enter or select the following information:
Setting Value Subnet purpose Leave the default Default. Name Enter subnet-private. IPv4 IPv4 address range Leave the default of 10.2.0.0/16. Starting address Leave the default of 10.2.0.0. Size Leave the default of /24(256 addresses). Select Add.
Select Review + create.
Select Create.
Create peering between hub and spoke two
Create a two-way virtual network peer between the hub and spoke two.
In the search box at the top of the portal, enter Virtual network. Select Virtual networks in the search results.
Select vnet-hub.
Select Peerings in Settings.
Select + Add.
In the search box at the top of the portal, enter Virtual network. Select Virtual networks in the search results.
Select vnet-hub.
Select Peerings in Settings.
Select + Add.
Enter or select the following information in Add peering:
Setting Value Remote virtual network summary Peering link name Enter vnet-spoke-2-to-vnet-hub. Virtual network deployment model Leave the default of Resource manager. Subscription Select your subscription. Virtual network Select vnet-spoke-2 (test-rg). Remote virtual network peering settings Allow 'vnet-spoke-2' to access 'vnet-hub' Leave the default of Selected. Allow 'vnet-spoke-2' to receive forwarded traffic from 'vnet-hub' Select the checkbox. Allow gateway or route server in 'vnet-spoke-2' to forward traffic to 'vnet-hub' Leave the default of Unselected. Enable 'vnet-spoke-2' to use 'vnet-hub's' remote gateway or route server Leave the default of Unselected. Local virtual network summary Peering link name Enter vnet-hub-to-vnet-spoke-2. Local virtual network peering settings Allow 'vnet-hub' to access 'vnet-spoke-2' Leave the default of Selected. Allow 'vnet-hub' to receive forwarded traffic from 'vnet-spoke-2' Select the checkbox. Allow gateway or route server in 'vnet-hub' to forward traffic to 'vnet-spoke-2' Leave the default of Unselected. Enable 'vnet-hub' to use 'vnet-spoke-2's' remote gateway or route server Leave the default of Unselected. Select Add.
Select Refresh and verify Peering status is Connected.
Create spoke two network route table
Create a route table to force all outbound internet and inter-spoke traffic through the simulated NVA in the hub virtual network.
In the search box at the top of the portal, enter Route table. Select Route tables in the search results.
Select + Create.
In Create Route table enter or select the following information:
Setting Value Project details Subscription Select your subscription. Resource group Select test-rg. Instance details Region Select China East 2. Name Enter route-table-nat-spoke-2. Propagate gateway routes Leave the default of Yes. Select Review + create.
Select Create.
In the search box at the top of the portal, enter Route table. Select Route tables in the search results.
Select route-table-nat-spoke-2.
In Settings select Routes.
Select + Add in Routes.
Enter or select the following information in Add route:
Setting Value Route name Enter default-via-nat-spoke-2. Destination type Select IP Addresses. Destination IP addresses/CIDR ranges Enter 0.0.0.0/0. Next hop type Select Virtual appliance. Next hop address Enter 10.0.0.10.
This is the IP address you added to the private interface of the NVA in the previous steps..Select Add.
Select Subnets in Settings.
Select + Associate.
Enter or select the following information in Associate subnet:
Setting Value Virtual network Select vnet-spoke-2 (test-rg). Subnet Select subnet-private. Select OK.
Create spoke two test virtual machine
Create a Windows Server 2022 virtual machine for the test virtual machine in spoke two.
In the search box at the top of the portal, enter Virtual machine. Select Virtual machines in the search results.
Select + Create then Azure virtual machine.
In Create a virtual machine enter or select the following information in the Basics tab:
Setting Value Project details Subscription Select your subscription. Resource group Select test-rg. Instance details Virtual machine name Enter vm-spoke-2. Region Select China East 2. Availability options Select No infrastructure redundancy required. Security type Select Standard. Image Select Windows Server 2022 Datacenter - Gen2. Size Select a size. Administrator account Authentication type Select Password. Username Enter a username. Password Enter a password. Confirm password Reenter password. Inbound port rules Public inbound ports Select None. Select Next: Disks then Next: Networking.
In the Networking tab, enter or select the following information:
Setting Value Network interface Virtual network Select vnet-spoke-2. Subnet Select subnet-private (10.2.0.0/24). Public IP Select None. NIC network security group Select Advanced. Configure network security group Select Create new.
Enter nsg-spoke-2.Inbound rules Select + Add an inbound rule.
Select HTTP in Service.
Select Add.
Select OK.Leave the rest of the options at the defaults and select Review + create.
Select Create.
Wait for the virtual machine to finish deploying before continuing to the next steps.
Install IIS on spoke two test virtual machine
IIS is installed on the Windows Server 2022 virtual machine to test outbound internet traffic through the NAT gateway and inter-spoke traffic in the hub and spoke network.
In the search box at the top of the portal, enter Virtual machine. Select Virtual machines in the search results.
Select vm-spoke-2.
In Operations, select Run command.
Select RunPowerShellScript.
Enter the following script in Run Command Script:
# Install IIS server role Install-WindowsFeature -name Web-Server -IncludeManagementTools # Remove default htm file Remove-Item C:\inetpub\wwwroot\iisstart.htm # Add a new htm file that displays server name Add-Content -Path "C:\inetpub\wwwroot\iisstart.htm" -Value $("Hello World from " + $env:computername)Select Run.
Wait for the script to complete before continuing to the next step. It can take a few minutes for the script to complete.
When the script completes, the Output* displays the following:
Success Restart Needed Exit Code Feature Result ------- -------------- --------- -------------- True No Success {Common HTTP Features, Default Document, D...
Test NAT gateway
To verify that the outbound internet traffic is leaving the NAT gateway, connect to the Windows Server 2022 virtual machines you created in the previous steps.
Obtain NAT gateway public IP address
Obtain the NAT gateway public IP address for verification of the steps later in the article.
Sign in to the Azure portal at https://portal.azure.cn.
In the search box at the top of the portal, enter Public IP. Select Public IP addresses in the search results.
Select public-ip-nat.
Make note of value in IP address. The example used in this article is 203.0.113.25.
Test NAT gateway from spoke one
Use Microsoft Edge on the Windows Server 2022 virtual machine to connect to https://whatsmyip.com to verify the functionality of the NAT gateway.
In the search box at the top of the portal, enter Virtual machine. Select Virtual machines in the search results.
Select vm-spoke-1.
In Overview, select Connect then Connect via Bastion.
Enter the username and password you entered when the virtual machine was created.
Select Connect.
Open Microsoft Edge when the desktop finishes loading.
In the address bar, enter https://whatsmyip.com.
Verify the outbound IP address displayed is the same as the IP of the NAT gateway you obtained previously.
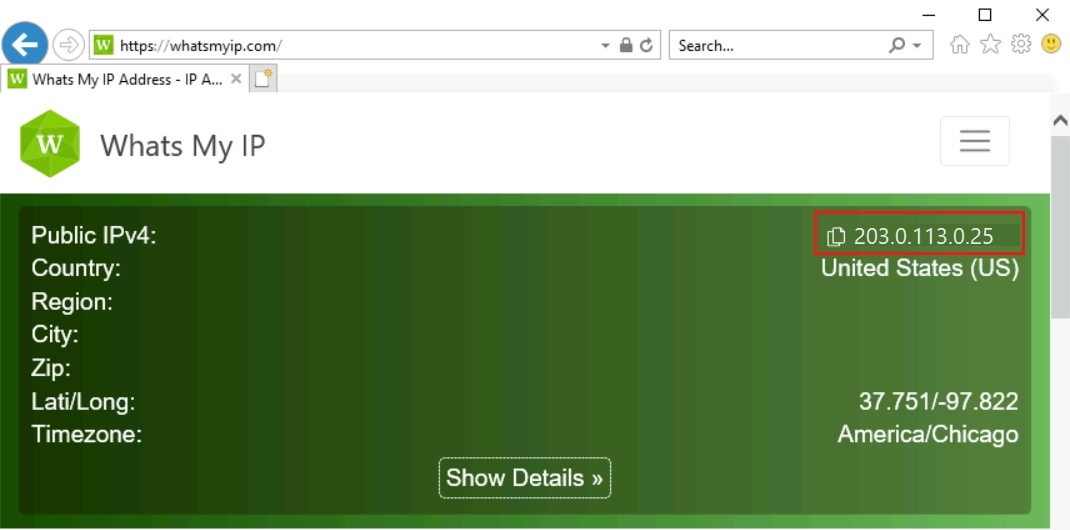
Leave the bastion connection open to vm-spoke-1.
Test NAT gateway from spoke two
Use Microsoft Edge on the Windows Server 2022 virtual machine to connect to https://whatsmyip.com to verify the functionality of the NAT gateway.
In the search box at the top of the portal, enter Virtual machine. Select Virtual machines in the search results.
Select vm-spoke-2.
In Overview, select Connect then Connect via Bastion.
Enter the username and password you entered when the virtual machine was created.
Select Connect.
Open Microsoft Edge when the desktop finishes loading.
In the address bar, enter https://whatsmyip.com.
Verify the outbound IP address displayed is the same as the IP of the NAT gateway you obtained previously.

Leave the bastion connection open to vm-spoke-2.
Test routing between the spokes
Traffic from spoke one to spoke two and spoke two to spoke one route through the simulated NVA in the hub virtual network. Use the following examples to verify the routing between spokes of the hub and spoke network.
Test routing from spoke one to spoke two
Use Microsoft Edge to connect to the web server on vm-spoke-2 you installed in the previous steps.
Return to the open bastion connection to vm-spoke-1.
Open Microsoft Edge if it's not open.
In the address bar, enter 10.2.0.4.
Verify the IIS page is displayed from vm-spoke-2.
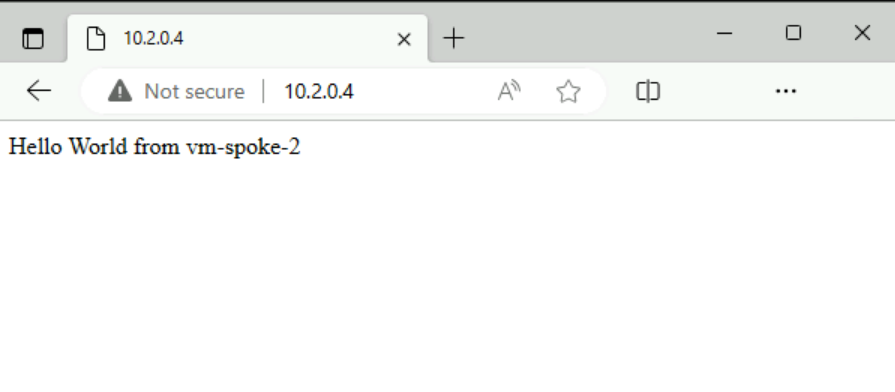
Close the bastion connection to vm-spoke-1.
Test routing from spoke two to spoke one
Use Microsoft Edge to connect to the web server on vm-spoke-1 you installed in the previous steps.
Return to the open bastion connection to vm-spoke-2.
Open Microsoft Edge if it's not open.
In the address bar, enter 10.1.0.4.
Verify the IIS page is displayed from vm-spoke-1.
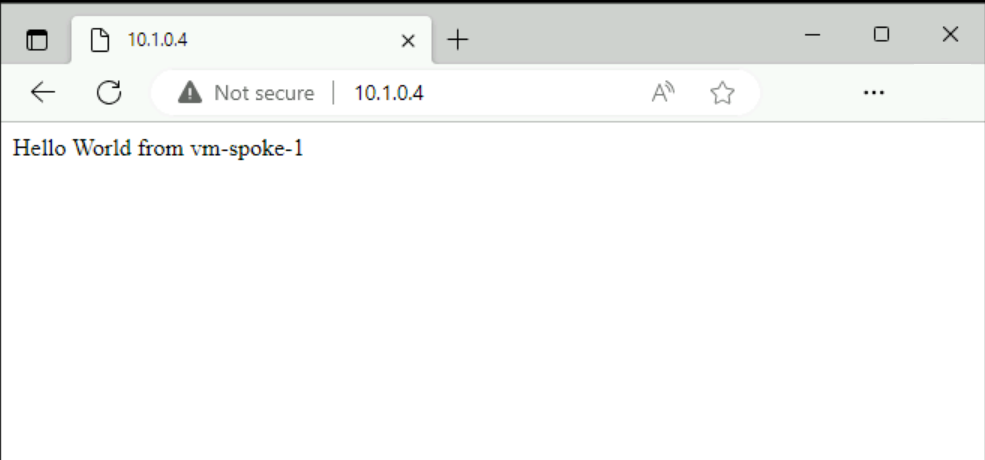
Close the bastion connection to vm-spoke-1.
Clean up resources
When you finish using the resources that you created, you can delete the resource group and all its resources:
In the Azure portal, search for and select Resource groups.
On the Resource groups page, select the test-rg resource group.
On the test-rg page, select Delete resource group.
Enter test-rg in Enter resource group name to confirm deletion, and then select Delete.
Next steps
Advance to the next article to learn how to use an Azure Gateway Load Balancer for highly available network virtual appliances: