Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Azure Route Server seamlessly integrates with Azure ExpressRoute and Azure VPN gateways, enabling dynamic route exchange between these gateways and network virtual appliances (NVAs). This integration allows you to create sophisticated hybrid network topologies where on-premises networks connected through different connectivity methods can communicate with each other and with NVAs in Azure.
This article explains how Azure Route Server works with ExpressRoute and VPN gateways, the configuration requirements, and key considerations for implementing these integrated scenarios.
Integration overview
Azure Route Server provides automated Border Gateway Protocol (BGP) peering with virtual network gateways, eliminating the need for manual BGP configuration. When you enable route exchange (also known as "branch-to-branch" connectivity), Azure Route Server facilitates route sharing between:
- Network virtual appliances and ExpressRoute gateways
- Network virtual appliances and VPN gateways
- ExpressRoute gateways and VPN gateways (when both are present)
You can enable route exchange using the Azure portal, Azure PowerShell, or Azure CLI.
Warning
When you create or delete a route server in a virtual network that contains a virtual network gateway (ExpressRoute or VPN), expect downtime until the operation is complete. If you have an ExpressRoute circuit connected to the virtual network where you're creating or deleting the route server, the downtime doesn't affect the ExpressRoute circuit or its connections to other virtual networks.
How route exchange works
When you deploy Azure Route Server in a virtual network alongside virtual network gateways and NVAs, route exchange enables these components to share routing information dynamically.
Default behavior
By default, Azure Route Server doesn't propagate routes between different types of network components. Each component (NVA, ExpressRoute gateway, VPN gateway) only exchanges routes directly with the route server.
With route exchange enabled
When you enable route exchange ("branch-to-branch" connectivity), Azure Route Server acts as a route reflector, allowing:
- Network virtual appliances to learn routes from virtual network gateways
- Virtual network gateways to learn routes from network virtual appliances
- Different gateway types to exchange routes with each other
Route exchange scenarios
ExpressRoute and network virtual appliance integration
The following diagram shows how an SD-WAN appliance and ExpressRoute gateway exchange routes through Azure Route Server:
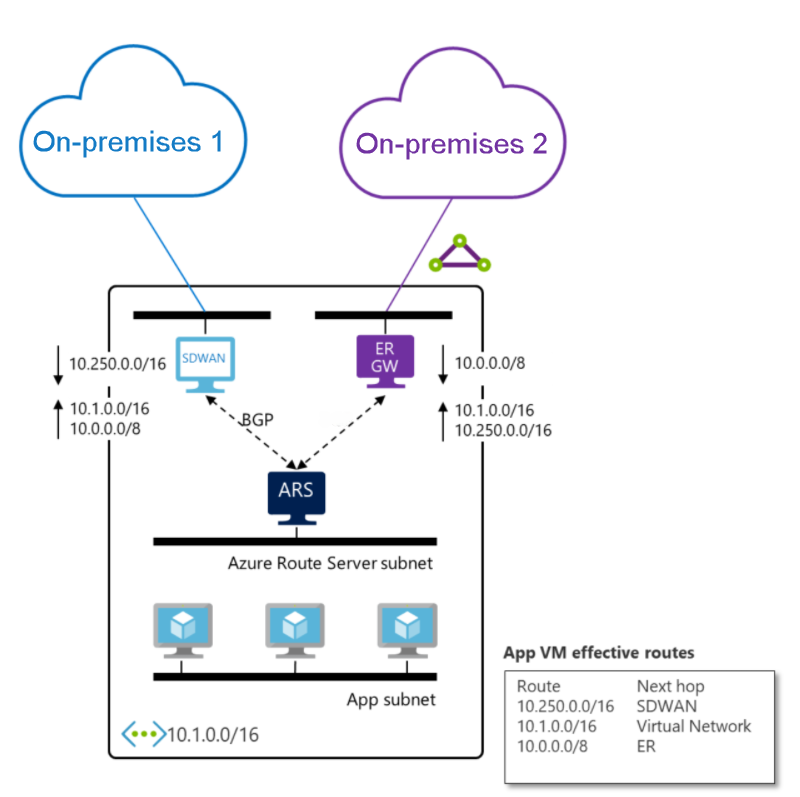
In this scenario:
- The SD-WAN appliance receives routes to On-premises 2 (connected through ExpressRoute) and virtual network routes from Azure Route Server
- The ExpressRoute gateway receives routes to On-premises 1 (connected through SD-WAN) and virtual network routes from Azure Route Server
- This enables connectivity between the two on-premises locations through Azure
ExpressRoute and VPN gateway integration
You can replace the SD-WAN appliance with an Azure VPN gateway to create a fully managed solution. Both Azure VPN and ExpressRoute gateways are fully managed services, so you only need to enable route exchange to establish connectivity between the on-premises networks.
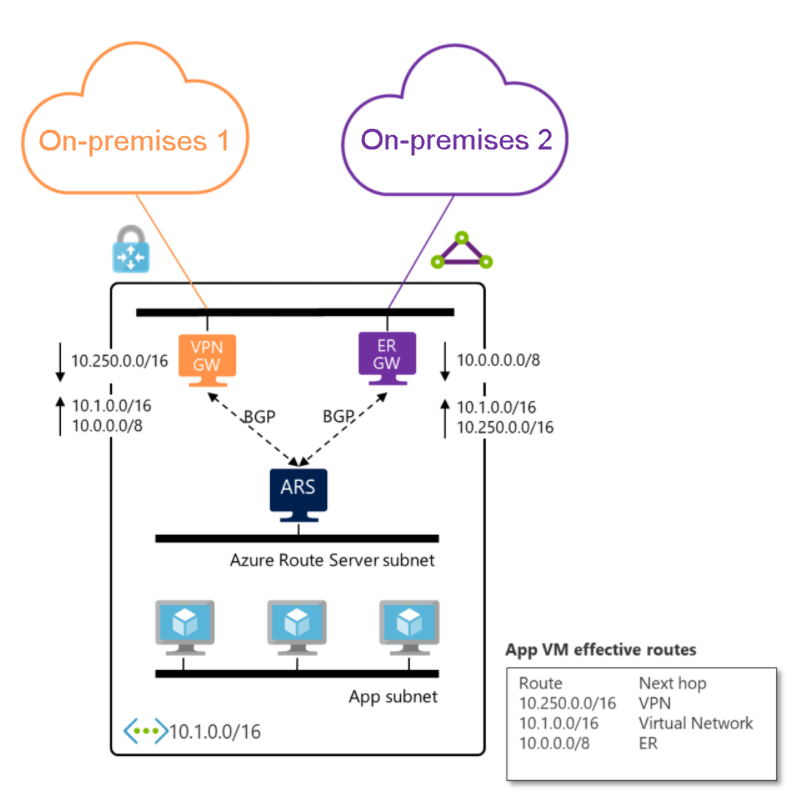
VPN gateway configuration considerations
For Azure VPN gateways, route learning behavior depends on your BGP configuration. BGP-enabled VPN gateways learn on-premises routes dynamically through BGP, provide automatic route updates when network topology changes, and offer enhanced failover and redundancy capabilities. For configuration guidance on BGP-enabled gateways, see Configure BGP for Azure VPN Gateway. In contrast, VPN gateways without BGP learn routes from local network gateway definitions, require static route configuration for on-premises networks, and need manual updates when topology changes occur. For configuration guidance on non-BGP gateways, see Create a local network gateway.
Regardless of BGP configuration, VPN gateways advertise learned routes to Azure Route Server when route exchange is enabled.
Important
The Azure VPN gateway must be configured in active-active mode and have the ASN set to 65515. It's not a requirement to have BGP enabled on the VPN gateway to communicate with the route server.
Configuration requirements
To configure route exchange, you must have Azure Route Server deployed in the target virtual network. The virtual network should also contain virtual network gateways such as ExpressRoute, VPN, or both types. If you plan to use network virtual appliances, ensure they're configured for BGP peering.
Key considerations
All gateways must be deployed in the same virtual network as Azure Route Server. The route exchange configuration applies to all gateways within the virtual network. ExpressRoute routes take precedence over VPN routes by default, but you can configure routing preference to influence route selection when multiple paths exist to the same destination. When advertising routes from on-premises networks, avoid using the Azure reserved BGP community 65517:65517.
Troubleshooting
When troubleshooting route exchange issues, first verify that route exchange is enabled and BGP sessions are properly established. Use Azure Route Server diagnostics to check routing tables and monitor BGP session states and route advertisements for any anomalies.