要管理 Microsoft Entra 域服务中的用户安全,可以定义细化的密码策略来控制帐户锁定设置或最短密码长度和复杂性。 将创建一个默认的细化密码策略,并将其应用于域服务托管域中的所有用户。 为了提供细化控制并满足特定的业务需求或合规性需求,可以创建更多的策略并将其应用于特定的用户或组。
本文说明了如何使用 Active Directory 管理中心在域服务中创建和配置细化的密码策略。
注意
密码策略仅适用于使用资源管理器部署模型创建的托管域。
准备阶段
需有以下资源和特权才能完成本文:
- 一个有效的 Azure 订阅。
- 如果你没有 Azure 订阅,请创建一个帐户。
- 与订阅关联的 Microsoft Entra 租户,可以与本地目录或仅限云的目录同步。
- 在 Microsoft Entra 租户中启用和配置的 Microsoft Entra 域服务托管域。
- 请根据需要完成创建并配置 Microsoft Entra 域服务托管域的教程。
- 必须已使用资源管理器部署模型创建托管域。
- 已加入托管域的 Windows Server 管理 VM。
- 如果需要,请完成创建管理 VM 的教程。
- 属于 Microsoft Entra 租户中“Microsoft Entra DC 管理员”组的用户帐户。
默认密码策略设置
通过细化的密码策略 (FGPP),可以对域中的不同用户应用特定的密码和帐户锁定策略限制。 例如,若要保护特权帐户,你可以应用比常规的非特权帐户更严格的帐户锁定设置。 可以在托管域中创建多个 FGPP,并指定将其应用于用户时的优先级顺序。
若要详细了解密码策略以及如何使用 Active Directory 管理中心,请参阅以下文章:
策略通过托管域中的组关联进行分发,并在用户下次登录时应用你所做的任何更改。 更改策略不会解锁已锁定的用户帐户。
根据应用密码策略的用户帐户的创建方式,密码策略的行为方式稍有不同。 可以通过两种方式在域服务中创建用户帐户:
- 可以从 Microsoft Entra ID 同步用户帐户。 这包括直接在 Azure 中创建的纯云用户帐户,以及使用 Microsoft Entra Connect 从本地 AD DS 环境同步的混合用户帐户。
- 域服务中的大部分用户帐户是通过同步过程从 Microsoft Entra ID 创建的。
- 对于 Microsoft Entra ID 中不存在的用户帐户,可以在托管域中手动创建该帐户。
无论创建方式如何,所有用户都会通过域服务中的默认密码策略应用以下帐户锁定策略:
- 帐户锁定持续时间: 30
- 允许的登录尝试失败次数: 5
- 多长时间后重置失败登录尝试计数:2 分钟
- 最长密码期限(生存期): 90 天
使用这些默认设置时,如果在 2 分钟内使用了 5 个无效密码,则会将用户帐户锁定 30 分钟。 帐户将在 30 分钟后自动解锁。
帐户锁定仅发生在托管域中。 用户帐户仅在域服务中锁定,并且仅在对托管域进行登录尝试失败的情况下锁定。 已从域服务或本地同步的用户帐户不会在其源目录中锁定,只会在 Microsoft Entra DS 中锁定。
如果 Microsoft Entra 密码策略指定的最长密码期限超过 90 天,则该密码期限会应用于域服务中的默认策略。 你可以配置自定义密码策略,以在域服务中定义不同的最长密码期限。 如果你在域服务密码策略中配置的密码最长期限比在 Microsoft Entra ID 或本地 AD DS 环境中配置的时间更短,则需要小心。 在这种情况下,系统在 Microsoft Entra ID 或本地 AD DS 环境中提示用户更改密码之前,该密码可能已在域服务中过期。
对于在托管域中手动创建的用户帐户,还会通过默认策略应用下述的其他密码设置。 这些设置不适用于从 Microsoft Entra ID 同步的用户帐户,因为用户无法直接在域服务中更新其密码。
- 最短密码长度(字符数): 7
- 密码必须符合复杂性要求
你无法修改默认密码策略中的帐户锁定或密码设置, 只能让“AAD DC 管理员”组的成员创建自定义密码策略,并将其配置为替代(优先于)默认的内置策略,如下一部分所示。
创建自定义密码策略
在 Azure 中生成并运行应用程序时,需要配置自定义密码策略。 例如,你可以创建一个策略来设置不同的帐户锁定策略设置。
自定义密码策略应用于托管域中的组。 此配置可有效地替代默认策略。
若要创建自定义密码策略,请使用已加入域的 VM 中的 Active Directory 管理工具。 使用 Active Directory 管理中心,你可以在托管域中查看、编辑和创建资源,包括 OU。
注意
若要在托管域中创建自定义密码策略,必须登录到 AAD DC 管理员组成员的用户帐户。
在“开始”屏幕中选择“管理工具”。 其中显示了可用管理工具列表,这些工具是在教程创建管理 VM 中安装的。
若要创建和管理 OU,请从管理工具列表中选择“Active Directory 管理中心”。
在左窗格中选择你的托管域,例如 aaddscontoso.com。
打开“系统”容器,然后打开“密码设置”容器。
此时会显示托管域的内置密码策略。 你无法修改此内置策略, 只能创建一个自定义密码策略来替代默认策略。
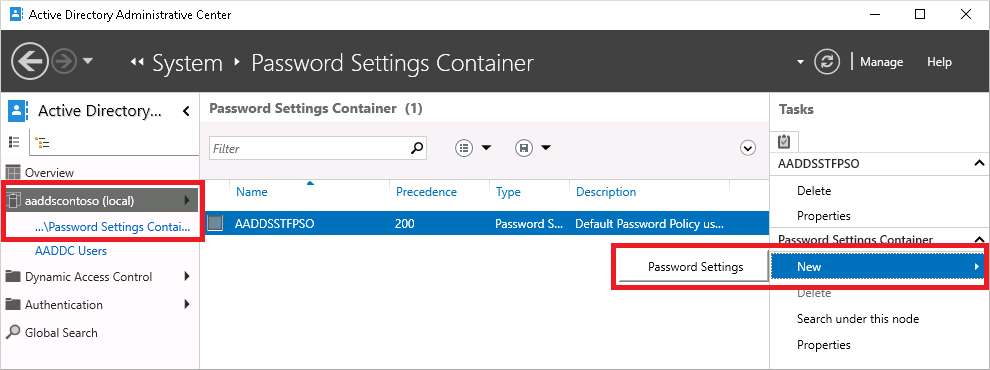
在右侧的“任务”面板中,选择“新建”>“密码设置”。
在“创建密码设置”对话框中,输入策略的名称,例如 MyCustomFGPP。
存在多个密码策略时,优先级最高的策略将应用于用户。 编号越低,优先级越高。 默认密码策略的优先级为 200。
设置自定义密码策略的优先级(例如 1)来替代默认值。
根据需要编辑其他密码策略设置。 帐户锁定设置适用于所有用户,但仅在托管域中生效,而不会在 Microsoft Entra 本身中生效。
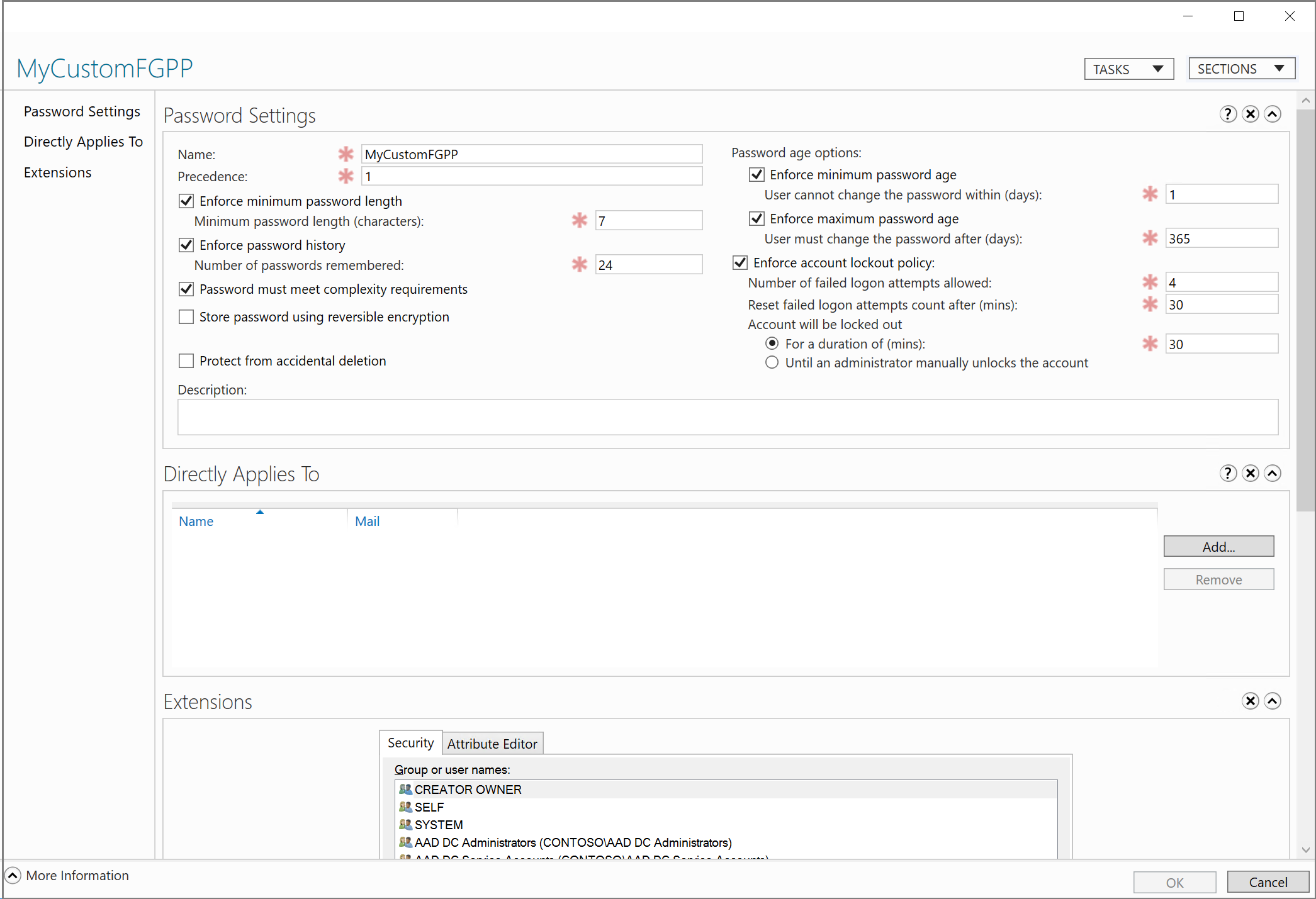
取消选中“防止意外删除”。 如果选中此选项,则不能保存 FGPP。
在“直接应用到”部分中,选择“添加”按钮。 在“选择用户或组”对话框中,选择“位置”按钮。
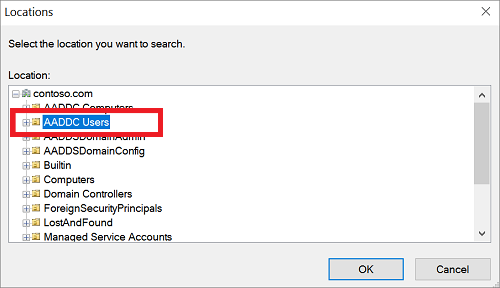
在“位置”对话框中展开域名(例如 aaddscontoso.com),然后选择一个 OU(例如“AADDC 用户”)。 如果你有一个自定义 OU,其中包含要应用的用户组,请选择该 OU。
键入要向其应用策略的用户或组的名称。 选择“检查名称”以验证账户。
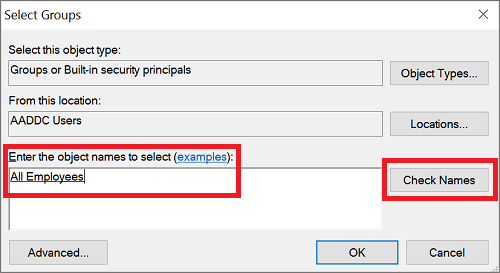
单击“确定”以保存自定义密码策略。
后续步骤
若要详细了解密码策略以及如何使用 Active Directory 管理中心,请参阅以下文章: