适用于:开发人员 | 高级
自承载网关是每个 API 管理实例中包含的默认托管网关的可选容器化版本。 它适用于在托管 API 的相同环境中放置网关等情景。 使用自承载网关可改善 API 流量流,并满足 API 安全性与合规性要求。
本文介绍 Azure API 管理的自承载网关功能如何实现混合和多云 API 管理。 它还提供该功能的高级体系结构并描述其功能。
有关托管网关与自承载网关之间的差异的概述,请参阅 API 管理中的 API 网关。
混合和多云 API 管理
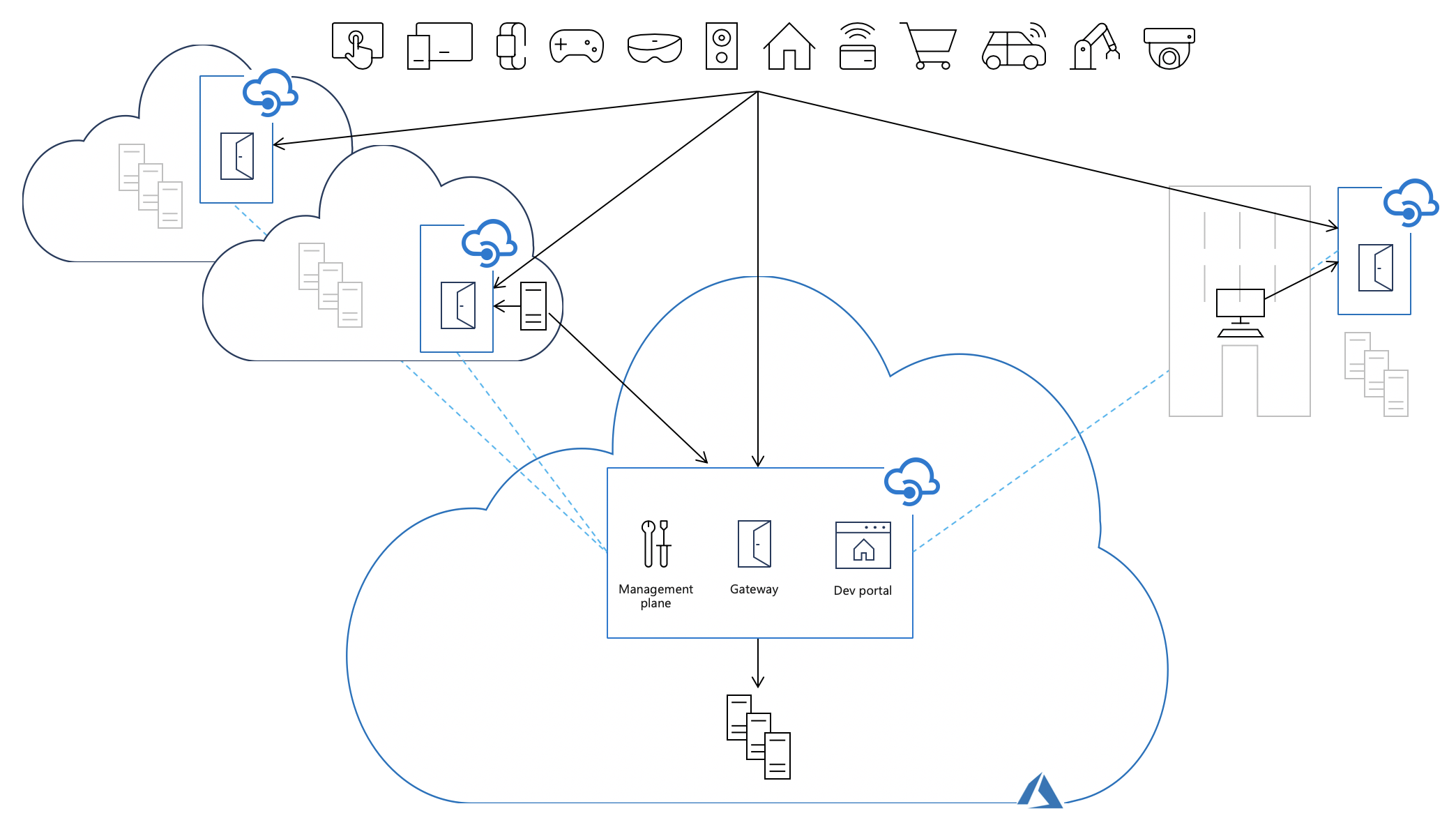
自承载网关功能扩展了对混合和多云环境的 API 管理支持,使你能够从 Azure 上的单个 API 管理实例高效安全地管理本地和跨云托管的 API。
使用自承载网关,可以灵活地将 API 管理网关组件的容器化版本部署到托管 API 的相同环境。 所有自托管网关都由与之联合的 API 管理实例进行管理,从而提供所有内部和外部 API 的可见性和统一管理体验。
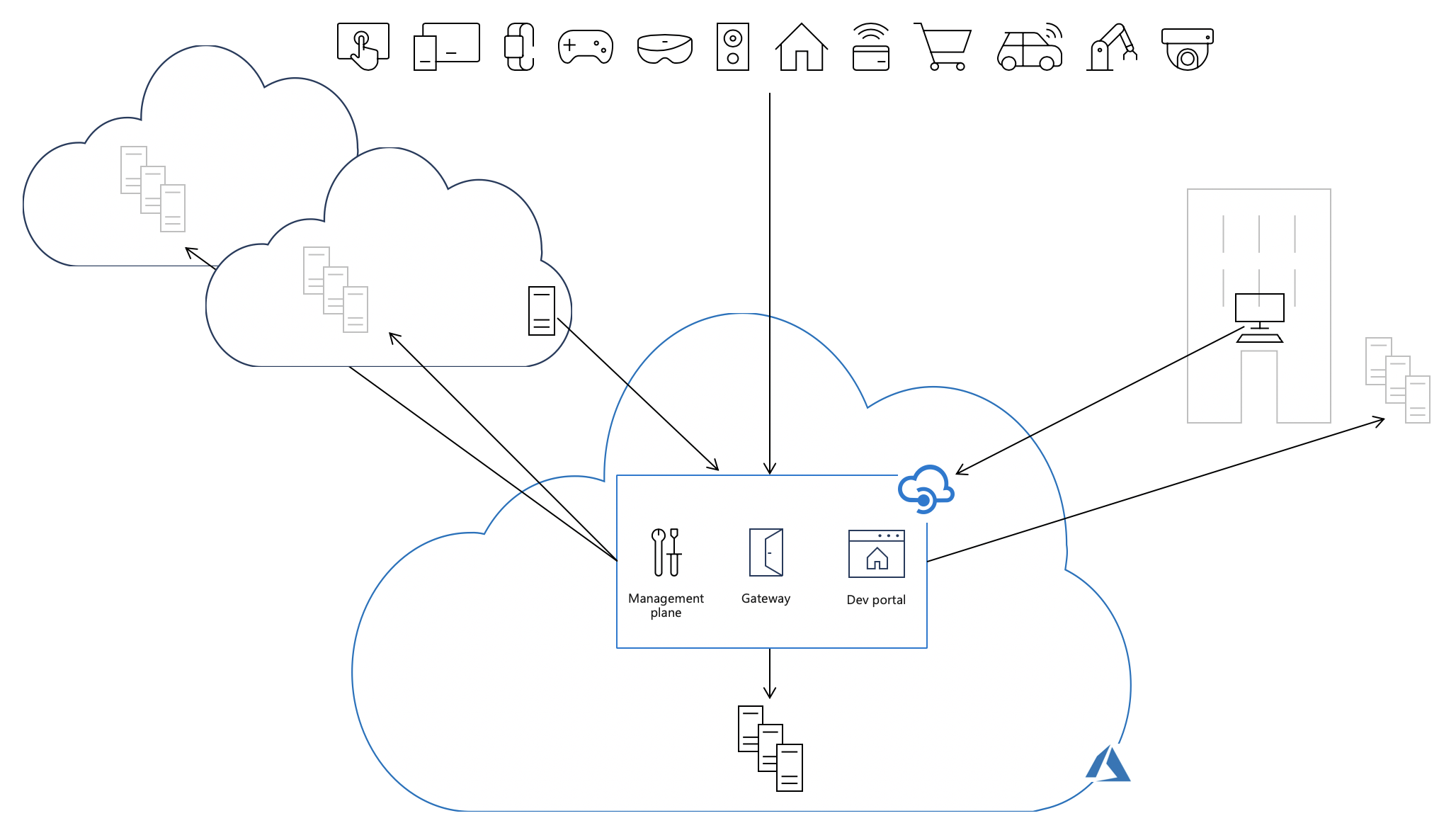
每个 API 管理实例由以下关键组件组成:
- 作为 API 公开的管理平面,用于通过 Azure 门户、PowerShell 和其他受支持的技术配置服务
- 负责代理 API 请求、应用策略和收集遥测数据的网关(或数据平面)
- 开发人员通过开发人员门户来发现、学习和注册使用 API
默认情况下,所有这些组件部署在 Azure 上,从而使得所有的 API 流量(如本文所示的实心黑箭头)流经 Azure,无论用于实现 API 的后端托管在哪里。 此模型虽然在操作上比较简单,但代价是增大延迟,造成合规性问题,而且在某些情况下还会产生额外的数据传输费。
将自承载网关部署到托管后端 API 实现的相同环境中,允许 API 流量直接流向后端 API,从而降低延迟、优化数据传输成本,并实现合规性,同时保留组织中所有 API 具有单一管理点、可观测性和发现的优势,而不管其实现托管在哪里。
打包
自托管网关在 Microsoft Artifact Registry 中以基于 Linux 的 Docker 容器映像的形式提供。 它可以部署到 Docker、Kubernetes,或任何其他在本地服务器节点上、云基础结构上或出于评估和开发目的在个人计算机上运行的容器业务流程解决方案。
容器映像
可以使用各种用于自行托管网关的容器映像:
| 标记约定 | 建议 | 示例 | 滚动标记 | 推荐用于生产 |
|---|---|---|---|---|
{major}.{minor}.{patch} |
使用此标签确保始终运行相同版本的网关。 | 2.0.0 |
❌ | ✔️ |
v{major} |
使用此标记就可以始终使用每个新功能和补丁运行一个主版本的网关。 | v2 |
✔️ | ❌ |
v{major}-preview |
如果始终想要运行最新的预览容器映像,请使用此标记。 | v2-preview |
✔️ | ❌ |
latest |
如果要评估自承载网关,请使用此标记。 | latest |
✔️ | ❌ |
beta
1 |
如果要评估自托管网关的预览版本,请使用此标记。 | beta |
✔️ | ❌ |
1预览版不受官方支持,仅用于实验目的。 请参阅自承载网关支持策略。
在官方部署选项中使用标记
Azure 门户中的部署选项使用 v2 标记,该标记允许使用包含所有功能更新和修补程序的自承载网关 v2 容器映像的最新版本。
注意
命令和 YAML 代码片段作为引用提供。 如果需要,可以使用更具体的标记。
使用 Helm 图表安装网关时,将优化图像标记。 Helm 图表的应用程序版本会将网关固定到给定版本,而不依赖于 latest。
有关详细信息,请参阅 使用 Helm 在 Kubernetes 上安装 API 管理自承载网关。
使用滚动标记的风险
滚动标记是发布新版容器映像时可能会更新的标记。 使用此类型的标记,容器用户无需更新其部署即可接收对容器映像的更新。
使用这种类型的标记时,可能会并行运行不同的版本,而没有注意到,例如,在更新标记后执行缩放操作。
示例:v2 标签与 2.0.0 容器映像一起发布。 当 2.1.0 被释放后,v2 标记将链接到 2.1.0 映像。
重要
请考虑在生产环境中使用特定的版本标记,以避免意外升级到较新版本。
连接到 Azure
自托管网关需要通过端口 443 来与 Azure 建立出站 TCP/IP 连接。 每个自承载网关必须与单个 API 管理实例相关联,并通过其管理平面进行配置。 自托管网关使用与 Azure 的连接来执行以下操作:
- 每分钟发送心跳消息来报告其状态。
- 定期(每 10 秒)检查和应用配置更新(只要可用)。
- 如果配置为这样做,则向 Azure Monitor 发送指标。
- 将事件发送到 Application Insights(如果配置为这样做)。
FQDN 依赖项
若要正常运行,每个自托管网关需要在端口 443 上与以下终结点建立出站连接,这些终结点与其基于云的 API 管理示例关联:
| 端点 | 必需? | 注释 |
|---|---|---|
| 的配置终结点的主机名 |
<api-management-service-name>.configuration.azure-api.cn
1 |
还支持自定义主机名,可以使用自定义主机名,而不是默认主机名。 |
| API 管理实例的公网 IP 地址 | ✔️ | 主位置的 IP 地址已足够。 |
| Azure 存储服务标签的公共 IP 地址 | 可选2 | IP 地址必须与 API 管理实例的主要位置相对应。 |
| Azure Blob 存储帐户的主机名 | 可选2 | 与实例关联的帐户(<blob-storage-account-name>.blob.core.chinacloudapi.cn)。 |
| Azure 表存储帐户的主机名 | 可选2 | 与实例关联的帐户(<table-storage-account-name>.table.core.chinacloudapi.cn)。 |
| 适用于 Azure 资源管理器的终结点 | 可选3 | 所需的终结点为 management.chinacloudapi.cn. |
| 用于 Microsoft Entra 集成的终结点 | 可选4 | 所需的终结点包括 <region>.login.microsoft.com 和 login.partner.microsoftonline.cn。 |
| Azure Application Insights 集成的终结点 | 可选5 | 所需的最小终结点是 rt.services.visualstudio.com:443, dc.services.visualstudio.com:443以及 {region}.livediagnostics.monitor.azure.com:443。 有关详细信息,请参阅 Azure Monitor 文档。 |
| 事件中心集成的终结点 | 可选5 | 有关详细信息,请参阅 Azure 事件中心文档。 |
| 外部缓存集成的终结点 | 可选5 | 此要求取决于正在使用的外部缓存。 |
1有关内部虚拟网络中的 API 管理实例的信息,请参阅 内部虚拟网络中的连接。
2仅当在策略中使用 API 检查器或配额时才需要在 v2 中。
3只有使用 Microsoft Entra 身份验证对 RBAC 权限进行验证时才需要。
4仅当使用与 Microsoft Entra 相关的Microsoft Entra 身份验证或策略时才是必需的。
5仅当使用该功能并且需要公共 IP 地址、端口和主机名信息时才是必需的。
重要
- DNS 主机名必须可解析为 IP 地址,并且必须可访问相应的 IP 地址。
- 关联的存储帐户名称在 Azure 门户的服务 网络连接状态 页上列出。
- 关联存储帐户下的公共 IP 地址是动态的,可能在不另行通知的情况下更改。
内部虚拟网络中的连接
专用连接。 如果自承载网关部署在虚拟网络中,请从自承载网关的位置启用与 v2 配置终结点的专用连接,例如,在对等网络中使用专用 DNS。
Internet 连接。 如果自承载网关需要通过 Internet 连接到 v2 配置终结点,请为配置终结点配置自定义主机名,并使用 Azure 应用程序网关公开终结点。
身份验证选项
网关容器 的配置设置 提供以下选项,用于验证自承载网关与基于云的 API 管理实例的配置终结点之间的连接。
| 选项 | 注意事项 |
|---|---|
| Microsoft Entra 身份验证 | 配置一个或多个Microsoft Entra 应用以访问网关。 按应用单独管理访问权限。 根据组织的策略为机密配置更长的过期时间。 使用标准Microsoft Entra 过程向应用分配或撤销用户或组权限,以及轮换机密。 |
| 网关访问令牌。 (也称为身份验证密钥。 | 令牌至少每 30 天到期,必须在容器中更新。 由可以独立轮换的网关密钥提供支持(例如,撤销访问权限)。 重新生成网关密钥会使使用网关密钥创建的所有访问令牌失效。 |
连接失败
与 Azure 断开连接时,自托管网关无法接收配置更新、报告自身的状态或上传遥测数据。
自托管网关采用“静态失败”设计,在暂时与 Azure 断开连接时可以留存。 可以在启用或不启用本地配置备份的情况下部署自托管网关。 通过配置备份,自托管网关会定期将下载配置的备份副本保存在已附加到其容器或 pod 的持久性卷上。
已禁用配置备份且与 Azure 中断连接时:
- 使用配置的内存中副本继续运行自承载网关。
- 停止的自承载网关将无法启动。
已启用配置备份且与 Azure 中断连接时:
- 使用配置的内存中副本继续运行自承载网关。
- 停止的自承载网关可以使用配置的备份副本启动。
还原连接后,受中断影响的每个自承载网关会自动与其关联的 API 管理实例重新连接,并下载网关脱机时发生的所有配置更新。
安全性
限制
托管网关中提供的以下功能在自承载网关中 不可用 :
- TLS 会话恢复。
- 客户端证书重新协商。 若要使用客户端证书身份验证,API 使用者必须出示其证书作为初始 TLS 握手的一部分。 为确保此行为,请在配置自承载网关自定义主机名(域名)时启用协商客户端证书设置。
传输层安全 (TLS) (Transport Layer Security) (TLS)
支持的协议
默认情况下,自承载网关支持 TLS v1.2。
如果使用自定义域,可以在 控制平面中启用 TLS v1.0 和/或 v1.1。
可用密码套件
自承载网关对客户端和服务器连接使用以下密码套件:
TLS_AES_256_GCM_SHA384TLS_CHACHA20_POLY1305_SHA256TLS_AES_128_GCM_SHA256TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384TLS_DHE_RSA_WITH_AES_256_GCM_SHA384TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256TLS_DHE_RSA_WITH_CHACHA20_POLY1305_SHA256TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256TLS_DHE_RSA_WITH_AES_128_GCM_SHA256TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384TLS_DHE_RSA_WITH_AES_256_CBC_SHA256TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256TLS_DHE_RSA_WITH_AES_128_CBC_SHA256TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHATLS_ECDHE_RSA_WITH_AES_256_CBC_SHATLS_DHE_RSA_WITH_AES_256_CBC_SHATLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHATLS_ECDHE_RSA_WITH_AES_128_CBC_SHATLS_DHE_RSA_WITH_AES_128_CBC_SHATLS_RSA_WITH_AES_256_GCM_SHA384TLS_RSA_WITH_AES_128_GCM_SHA256TLS_RSA_WITH_AES_256_CBC_SHA256TLS_RSA_WITH_AES_128_CBC_SHA256TLS_RSA_WITH_AES_256_CBC_SHATLS_RSA_WITH_AES_128_CBC_SHA
管理密码套件
使用 v2.1.1 及更高版本,可以管理通过配置使用的密码:
-
net.server.tls.ciphers.allowed-suites使你能够定义逗号分隔的密码列表,用于 API 客户端和自承载网关之间的 TLS 连接。 -
net.client.tls.ciphers.allowed-suites使你能够定义一个逗号分隔的密码列表,用于自承载网关和后端之间的 TLS 连接。