可以使用 Azure 门户为使用虚拟机作为后端服务器的应用程序网关配置 TLS 终止证书。
在本教程中,你将了解如何执行以下操作:
- 创建自签名证书
- 使用证书创建应用程序网关
- 创建用作后端服务器的虚拟机
- 测试应用程序网关
如果没有 Azure 订阅,可在开始前创建一个试用帐户。
注意
建议使用 Azure Az PowerShell 模块与 Azure 交互。 若要开始,请参阅安装 Azure PowerShell。 若要了解如何迁移到 Az PowerShell 模块,请参阅 将 Azure PowerShell 从 AzureRM 迁移到 Az。
先决条件
- Azure 订阅
创建自签名证书
在本部分中,你将使用 New-SelfSignedCertificate 创建自签名证书。 为应用程序网关创建侦听器时,需要将该证书上传到 Azure 门户。
在本地计算机上,以管理员身份打开 Windows PowerShell 窗口。 运行以下命令以创建证书:
New-SelfSignedCertificate `
-certstorelocation cert:\localmachine\my `
-dnsname www.contoso.com
应看到与此响应类似的内容:
PSParentPath: Microsoft.PowerShell.Security\Certificate::LocalMachine\my
Thumbprint Subject
---------- -------
E1E81C23B3AD33F9B4D1717B20AB65DBB91AC630 CN=www.contoso.com
将 Export-PfxCertificate 与返回的指纹配合使用,从证书导出 pfx 文件。 支持的 PFX 算法在 PFXImportCertStore 函数处列出。 请确保密码长度为 4 到 12 个字符:
$pwd = ConvertTo-SecureString -String <your password> -Force -AsPlainText
Export-PfxCertificate `
-cert cert:\localMachine\my\E1E81C23B3AD33F9B4D1717B20AB65DBB91AC630 `
-FilePath c:\appgwcert.pfx `
-Password $pwd
登录 Azure
登录 Azure 门户。
创建应用程序网关
在 Azure 门户菜单中,选择“+ 创建资源”“网络”>“应用程序网关”,或者在门户搜索框中搜索“应用程序网关”。
选择“创建” 。
“基本信息”选项卡
在“基本信息”选项卡上,输入或选择以下值:
资源组:选择 myResourceGroupAG 作为资源组。 如果该资源组不存在,请选择“新建”,创建一个新的。
应用程序网关名称:输入 myAppGateway 作为应用程序网关的名称。
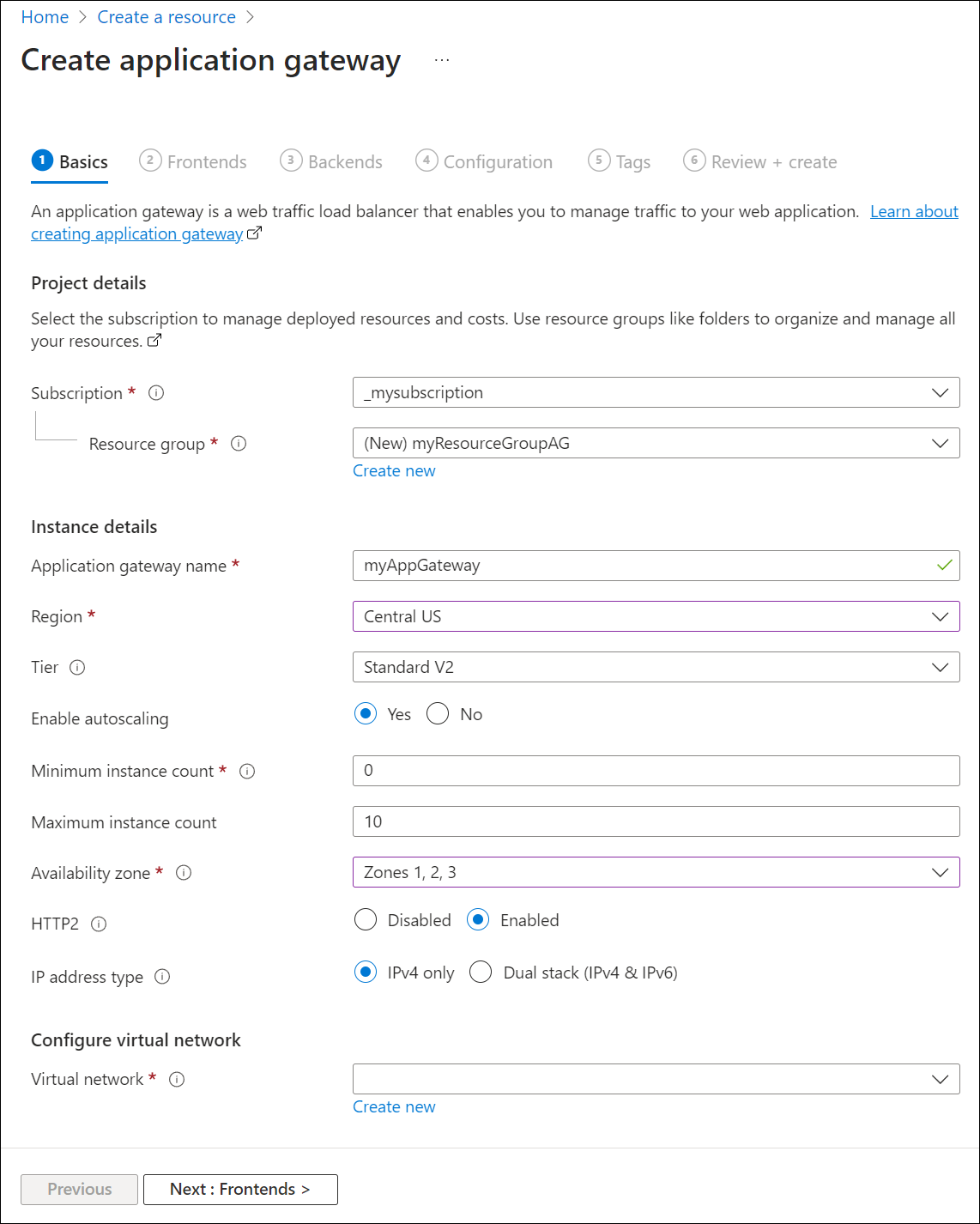
Azure 需要一个虚拟网络才能在创建的资源之间通信。 可以创建新的虚拟网络,或者使用现有的虚拟网络。 在此示例中,将在创建应用程序网关的同时创建新的虚拟网络。 在独立的子网中创建应用程序网关实例。 在本示例中创建两个子网:一个用于应用程序网关,另一个用于后端服务器。
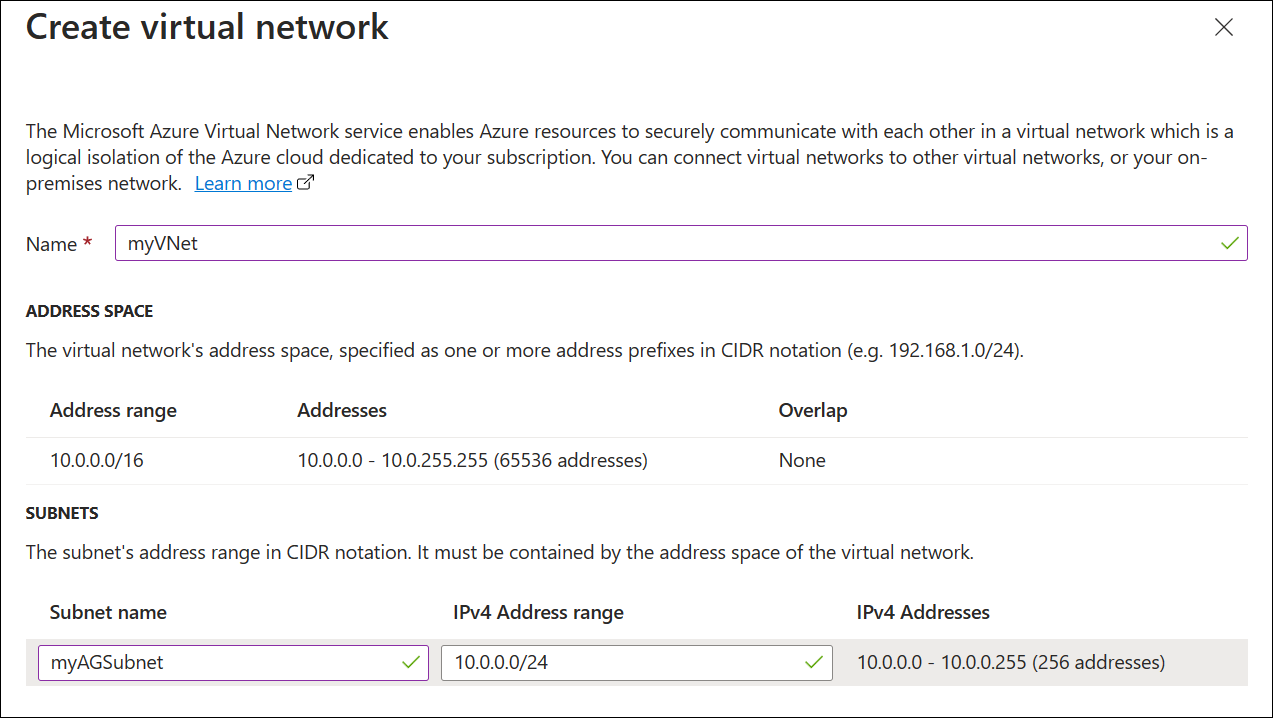
在“配置虚拟网络”下,通过选择“新建”创建新的虚拟网络 。 在打开的“创建虚拟网络”窗口中,输入以下值以创建虚拟网络和两个子网 :
名称:输入 myVNet 作为虚拟网络的名称。
子网名称(应用程序网关子网):子网网关将显示名为“默认值”的子网。 将此子网的名称更改为 myAGSubnet。
应用程序网关子网只能包含应用程序网关。 不允许其他资源。子网名称(后端服务器子网):在子网网关的第二行中,在“子网名称”列输入“myBackendSubnet”。
地址范围(后端服务器子网):在子网网格的第二行中,输入不会与 myAGSubnet 的地址范围重叠的地址范围。 例如,如果 myAGSubnet 的地址范围为 10.0.0.0/24,则为 myBackendSubnet 的地址范围输入 10.0.1.0/24 。
选择“确定”以关闭“创建虚拟网络”窗口,并保存虚拟网络设置 。
在“基本信息” 选项卡上,接受其他设置的默认值,然后选择“下一步: 前端”。
“前端”选项卡
在“前端”选项卡上,验证“IP 地址类型”是否设置为“公共” 。
可根据用例将前端 IP 配置为公共或专用 IP。 本示例将选择公共前端 IP。注意
对于应用程序网关 v2 SKU,只能选择公共前端 IP 配置。 目前尚未为此 v2 SKU 启用专用前端 IP 配置。
为“公共 IP 地址”选择“新增”,输入“myAGPublicIPAddress”作为公共 IP 地址名称,然后选择“确定” 。
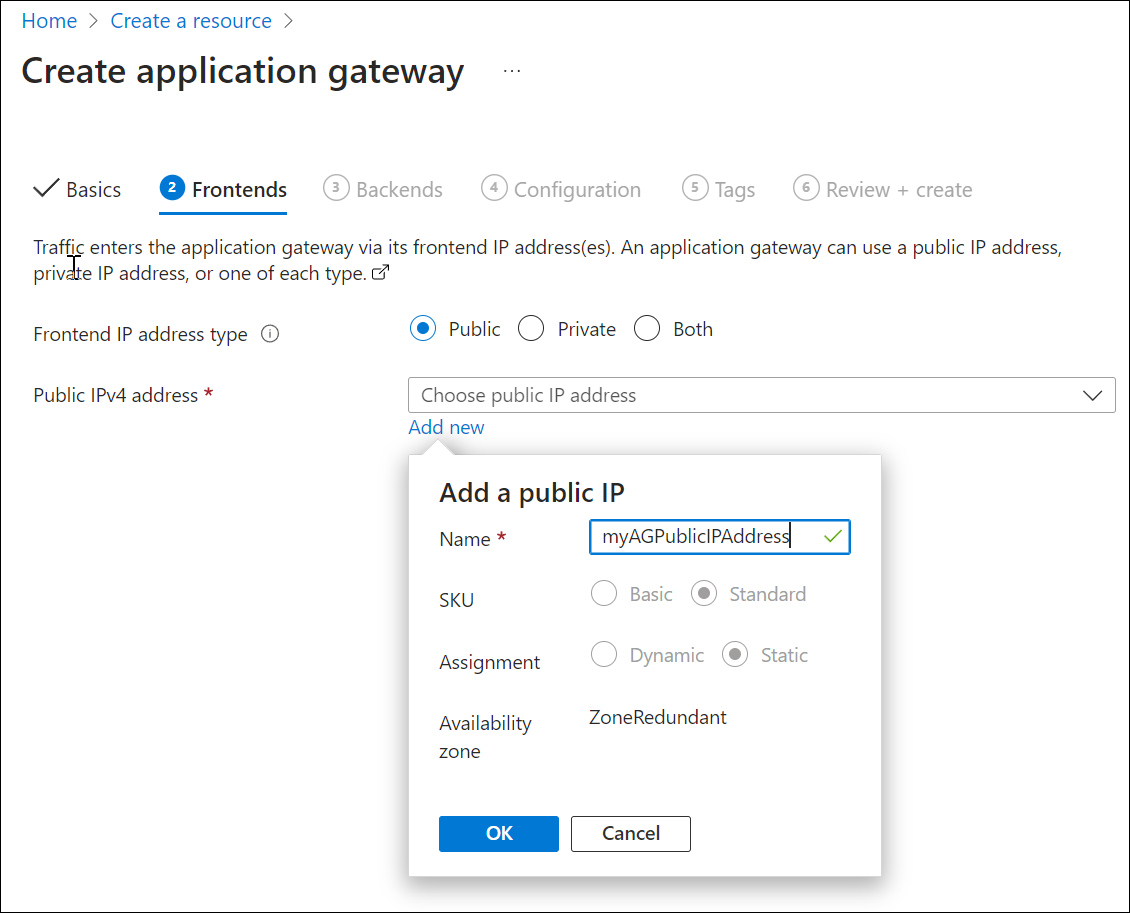
在完成时选择“下一步:后端。
“后端”选项卡
后端池用于将请求路由到为请求提供服务的后端服务器。 后端池可以包含 NIC、虚拟机规模集、公共 IP、内部 IP、完全限定的域名 (FQDN) 和多租户后端(例如 Azure 应用服务)。 在此示例中,将使用应用程序网关创建空的后端池,然后将后端目标添加到后端池。
在“后端”选项卡上,选择“添加后端池” 。
在打开的“添加后端池”窗口中,输入以下值以创建空的后端池 :
- 名称:输入“myBackendPool”作为后端池的名称。
- 添加不包含目标的后端池:选择“是”以创建不包含目标的后端池 。 你将在创建应用程序网关之后添加后端目标。
在“添加后端池”窗口中,选择“添加”以保存后端池配置并返回到“后端”选项卡 。
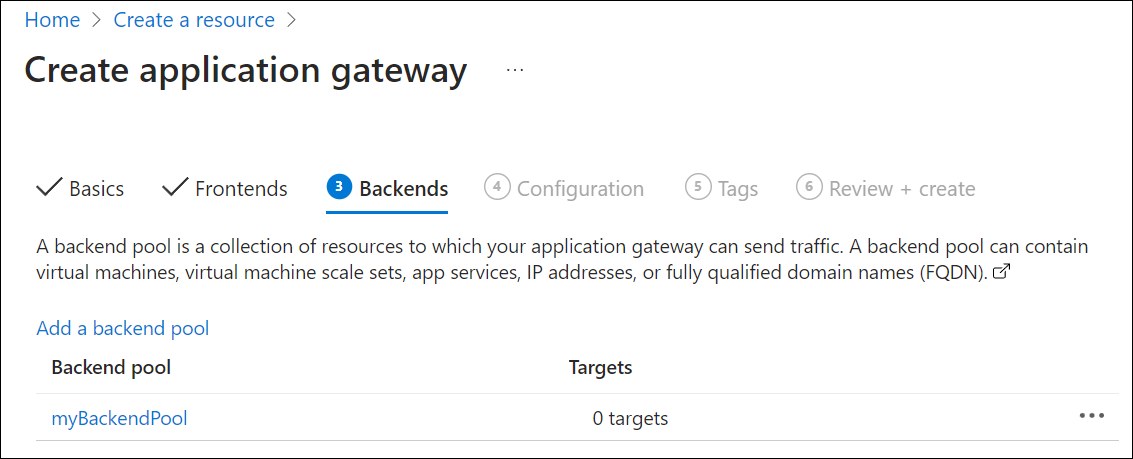
在“后端” 选项卡上,选择“下一步: 配置”。
配置选项卡
在“配置”选项卡上,将连接使用传递规则创建的前端和后端池。
选择“传递规则”列中的“添加传递规则” 。
在打开的“添加传递规则”窗口中,输入“myRoutingRule”作为规则名称。
传递规则需要侦听器。 在“添加传递规则”窗口中的“侦听器”选项卡上,输入侦听器的以下值 :
- 侦听器名称:输入“myListener”作为侦听器名称。
- 前端 IP:选择“公共”,以选择为前端创建的公共 IP。
- 协议:选择 HTTPS。
- 端口:验证是否为端口输入了 443。
在“HTTPS 设置”下:
对于“选择证书”,请选择“上传证书” 。
PFX 证书文件 - 浏览到并选择前面创建的 c:\appgwcert.pfx 文件。
证书名称 - 键入“mycert1”作为证书的名称。
对于“密码”,请键入创建证书所用的密码。
接受“侦听器”选项卡上其他设置的默认值,然后选择“后端目标”选项卡以配置剩余的传递规则 。
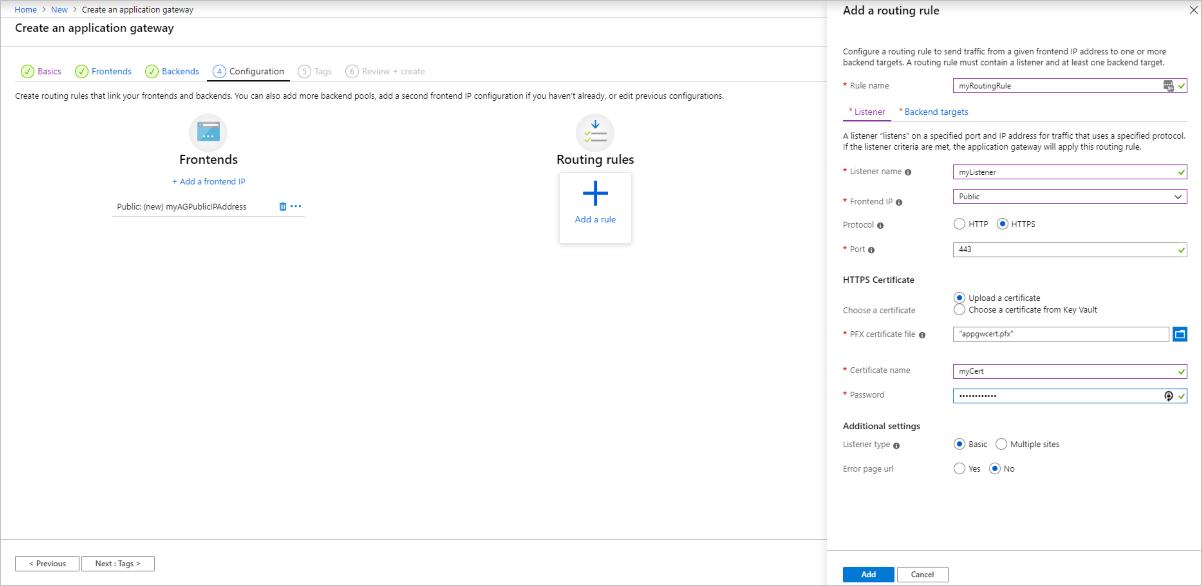
在“后端目标”选项卡上,为“后端目标”选择“myBackendPool” 。
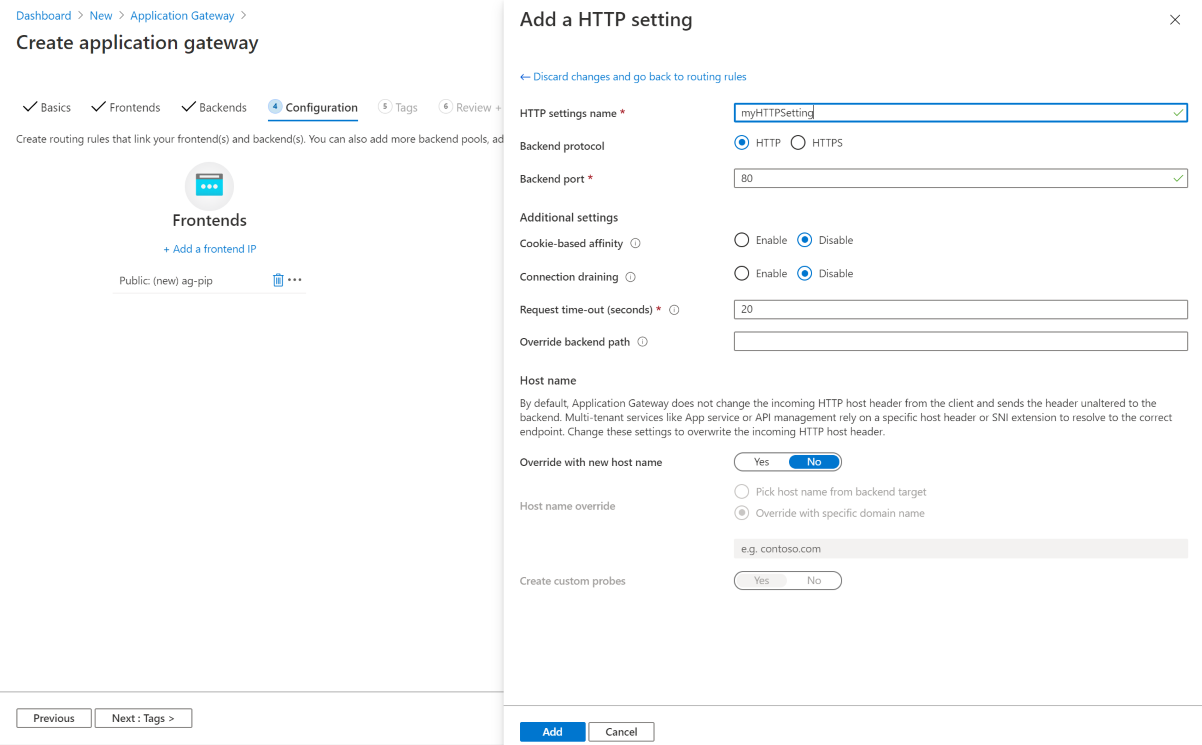
对于“HTTP 设置”,请选择“新建”以添加新的 HTTP 设置 。 HTTP 设置将决定传递规则的行为。 在打开的“添加 HTTP 设置”窗口中,为“HTTP 设置名称”输入“myHTTPSetting”。 接受“添加 HTTP 设置”窗口中其他设置的默认值,然后选择“添加”以返回到“添加传递规则”窗口 。
在“添加传递规则”窗口上,选择“添加”以保存传递规则并返回到“配置”选项卡 。
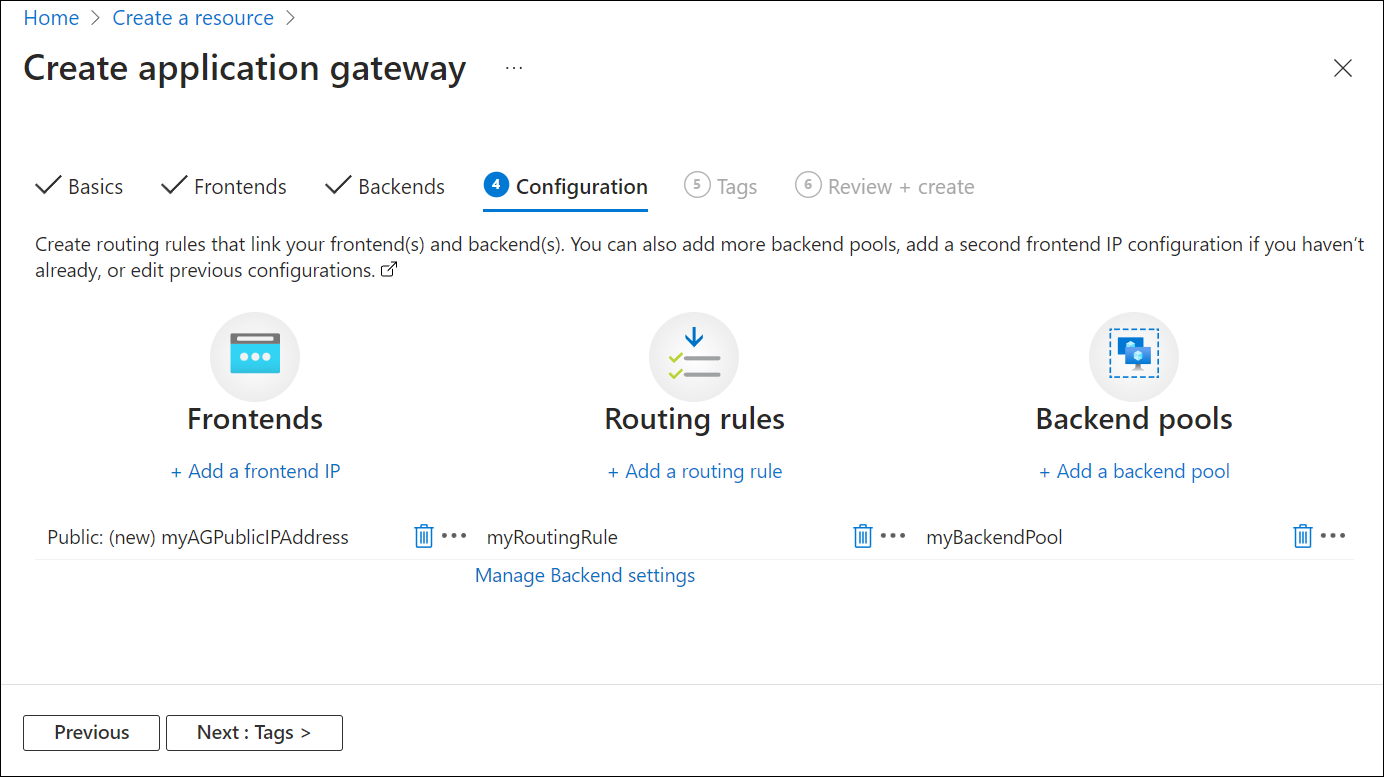
在完成时选择“下一步: 标记”,然后选择“下一步: 查看 + 创建”。
“查看 + 创建”选项卡
复查“查看 + 创建”选项卡上的设置,然后选择“创建”以创建虚拟网络、公共 IP 地址和应用程序网关 。 Azure 可能需要数分钟时间来创建应用程序网关。 请等待部署成功完成,然后再前进到下一部分。
添加后端目标
本示例将使用虚拟机作为目标后端。 可以使用现有的虚拟机,或创建新的虚拟机。 将创建两个虚拟机,供 Azure 用作应用程序网关的后端服务器。
为此,将要:
- 创建两个新的 VM(myVM 和 myVM2),用作后端服务器 。
- 在虚拟机上安装 IIS,以验证是否成功创建了应用程序网关。
- 将后端服务器添加到后端池。
创建虚拟机
在 Azure 门户菜单中,请选择“+ 创建资源”“计算”>“Windows Server 2016 Datacenter”,或在门户搜索框中搜索“Windows Server”,然后选择“Windows Server 2016 Datacenter”。
选择“创建” 。
应用程序网关可将流量路由到其后端池中使用的任何类型的虚拟机。 本示例使用 Windows Server 2016 Datacenter。
对于以下虚拟机设置,请在“基本信息”选项卡中输入相应值:
- 资源组:选择 myResourceGroupAG 作为资源组名称。
- 虚拟机名称:输入 myVM 作为虚拟机的名称。
- 用户名:为管理员用户名输入一个名称。
- 密码:输入管理员帐户的密码。
接受其他默认值,然后选择“下一步:磁盘” 。
接受“磁盘”选项卡的默认值,然后选择“下一步:网络” 。
在“网络”选项卡上,验证是否已选择 myVNet 作为虚拟网络,以及是否已将“子网”设置为 myBackendSubnet。 接受其他默认值,然后选择“下一步:管理” 。
应用程序网关可与其所在的虚拟网络外部的实例进行通信,但需要确保已建立 IP 连接。
在“管理”选项卡上,将“启动诊断”设置为“禁用” 。 接受其他默认值,然后选择“复查 + 创建”。
在“复查 + 创建”选项卡上复查设置,更正任何验证错误,然后选择“创建”。
等待部署完成,然后再继续。
安装 IIS 用于测试
本示例在虚拟机上安装 IIS,只为验证 Azure 是否已成功创建应用程序网关。
在 powershell 中使用以下命令登录 Azure 门户:
Connect-AzAccount -Environment AzureChinaCloud更改你的环境的位置设置,然后运行以下命令在虚拟机上安装 IIS:
Set-AzVMExtension ` -ResourceGroupName myResourceGroupAG ` -ExtensionName IIS ` -VMName myVM ` -Publisher Microsoft.Compute ` -ExtensionType CustomScriptExtension ` -TypeHandlerVersion 1.4 ` -SettingString '{"commandToExecute":"powershell Add-WindowsFeature Web-Server; powershell Add-Content -Path \"C:\\inetpub\\wwwroot\\Default.htm\" -Value $($env:computername)"}' ` -Location <location>使用以前完成的步骤创建第二个虚拟机并安装 IIS。 使用 myVM2 作为虚拟机名称,以及作为 Set-AzVMExtension cmdlet 的 VMName 设置。
将后端服务器添加到后端池
选择“所有资源”,然后选择“myAppGateway”。
从左侧菜单中选择“后端池”。
选择“myBackendPool”。
在“目标”类型下,从下拉列表中选择“虚拟机” 。
在“目标”下,从下拉列表中选择“myVM”下的网络接口。
重复此步骤以添加“myVM2”的网络接口。
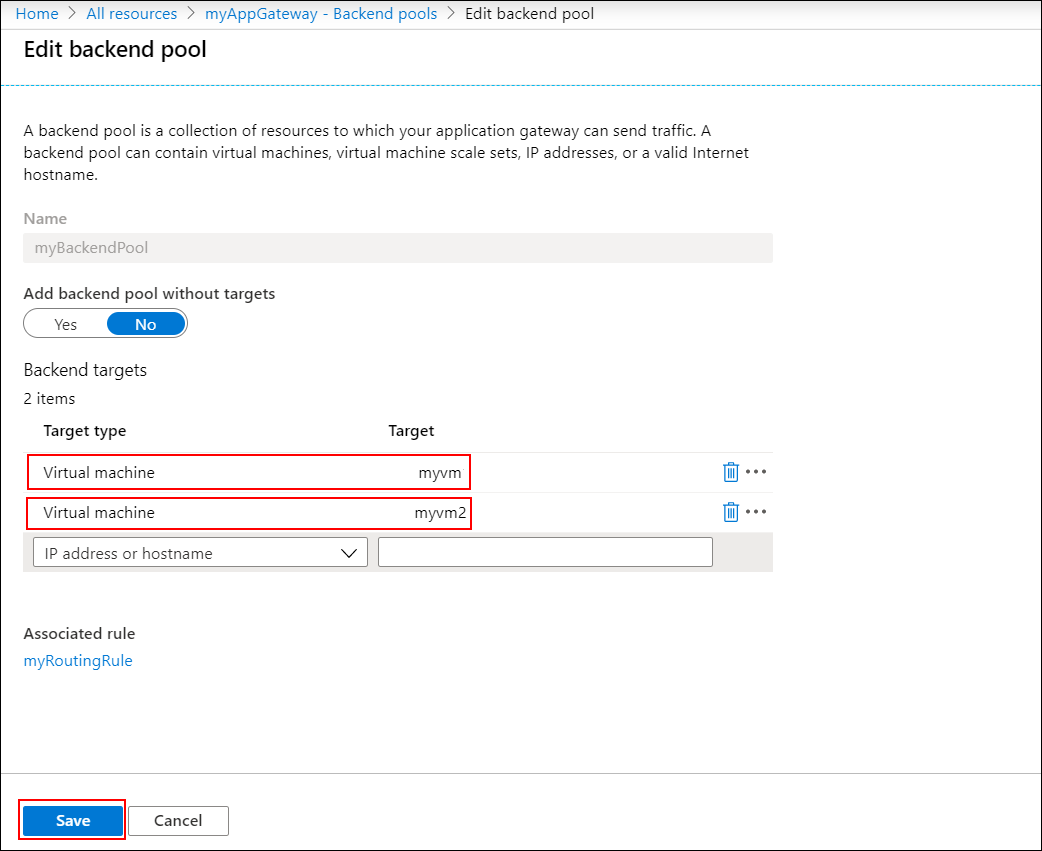
选择“保存”。
等待部署完成之后再继续下一步。
测试应用程序网关
依次选择“所有资源”、“myAGPublicIPAddress”。
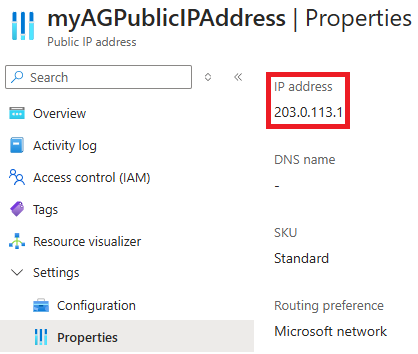
在浏览器的地址栏中,键入“https://<应用程序网关 IP 地址>”。
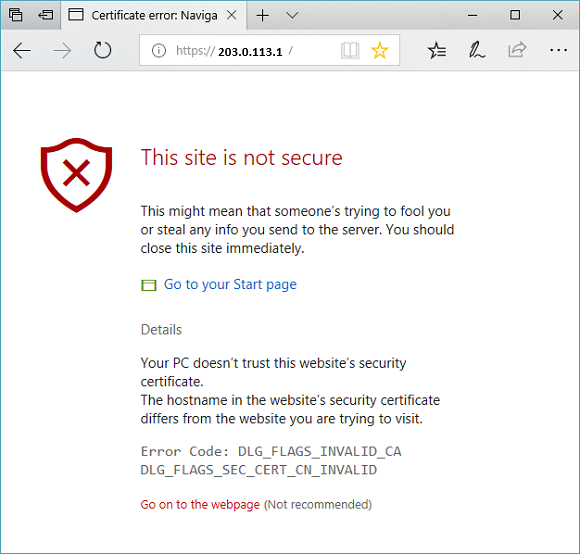
若要在使用自签名证书时接受安全警告,请选择“详细信息”(或 Chrome上的“高级”),然后转到相应网页:
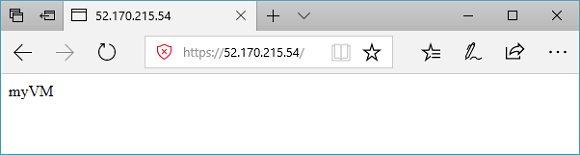
随即显示受保护的 IIS 网站,如下例所示:
清理资源
不再需要时,请删除资源组及所有相关资源。 为此,请选择资源组,然后选择“删除资源组”。
后续步骤
在本教程中,你将了解:
- 创建自签名证书
- 使用证书创建应用程序网关
若要详细了解应用程序网关 TLS 支持,请参阅使用应用程序网关的端到端 TLS 以及应用程序网关 TLS 策略。
若要了解如何使用 Azure 门户创建和配置应用程序网关以托管多个网站,请前往下一教程。