传输层安全性 (TLS)(前称为安全套接字层 (SSL))是用于在 Web 服务器与浏览器之间建立加密链接的标准安全技术。 该链接可确保在 Web 服务器和浏览器之间传递的所有数据都会得到保密和加密。 应用程序网关支持网关上的 TLS 终止以及端到端 TLS 加密。
Important
从 2025 年 8 月 31 日开始,与 Azure 应用程序网关交互的所有客户端和后端服务器必须使用传输层安全性 (TLS) 1.2 或更高版本,如对 TLS 1.0 和 1.1 的支持将会终止中所述。
TLS 终止
应用程序网关支持在网关上终止 TLS,之后,流量通常会以未加密状态流到后端服务器。 在应用程序网关上执行 TLS 终止可以带来诸多优势:
- 提高性能 - 执行 TLS 解密时,最大的性能损失发生在初次握手阶段。 为了提高性能,执行解密的服务器会缓存 TLS 会话 ID 并管理 TLS 会话票证。 如果在应用程序网关上完成此操作,则来自同一客户端的所有请求都可以使用缓存值。 如果此操作是在后端服务器上执行的,则每当客户端的请求转到另一台服务器时,客户端都必须重新进行身份验证。 使用 TLS 票证有助于缓解此问题,但并非所有客户端都支持 TLS 票证,并且配置和管理这些票证可能有难度。
- 更好地利用后端服务器 - SSL/TLS 处理会消耗大量的 CPU 资源,随着密钥大小不断地增大,其消耗的资源会越来越多。 从后端服务器中消除此任务可使它们专注于以最有效的方式提供内容。
- 智能路由 - 解密流量后,应用程序网关便可以访问标头、URI 等请求内容,并可以使用此数据来路由请求。
- 证书管理 - 只需在应用程序网关上购买并安装证书,所有后端服务器不需要证书。 这可以节省时间和开支。
若要配置 TLS 终止,必须向侦听器中添加 TLS/SSL 证书。 这样,应用程序网关便可以解密传入的流量并加密发到客户端的响应流量。 提供给应用程序网关的证书必须采用个人信息交换 (PFX) 格式,其中包含私钥和公钥。 支持的 PFX 算法在 PFXImportCertStore 函数处列出。
Important
侦听器上的证书要求上传整个证书链(来自 CA 的根证书、中间证书和叶证书)以建立信任链。
Note
应用程序网关不提供任何用于创建新证书,或者将证书请求发送到证书颁发机构的功能。
若要建立 TLS 连接,需要确保 TLS/SSL 证书符合以下条件:
- 当前日期和时间处于证书上的“生效日期”和“失效日期”日期范围内。
- 证书的“公用名”(CN) 与请求中的主机标头相匹配。 例如,如果客户端向
https://www.contoso.com/发出请求,则 CN 必须为www.contoso.com。
如果后端证书公用名称 (CN) 有误,请参阅故障排除指南。
支持用于 TLS 终止的证书
应用程序网关支持以下类型的证书:
- CA(证书颁发机构)证书:CA 证书是证书颁发机构 (CA) 颁发的数字证书
- EV(扩展验证)证书:EV 证书是符合行业标准证书准则的证书。 使用此类证书会让浏览器地址栏显示为绿色,并显示公司名称。
- 通配符证书:这种证书支持任意数量的以 *.site.com 为基础的子域,其中的 * 可以替换为你的子域。 但是,它不支持 site.com,因此,如果用户在不键入前导“www”的情况下访问你的网站,通配符证书不会反映这一点。
- 自签名证书:客户端浏览器不信任这些证书,并且会警告用户,指出虚拟服务的证书不是信任链的一部分。 自签名证书适合用于测试,或者管理员会在其中控制客户端并且可以安全绕过浏览器安全警报的环境。 切勿将自签名证书用于生产工作负荷。
有关详细信息,请参阅配置应用程序网关的 TLS 终止。
证书大小
查看应用程序网关限制部分,了解支持的最大 TLS/SSL 证书大小。
端到端 TLS 加密
你可能不希望与后端服务器进行未加密的通信。 你可能有安全要求、符合性要求,或者应用程序可能仅接受安全连接。 Azure 应用程序网关通过端到端 TLS 加密来支持这些要求。
当你使用应用程序网关的第 7 层负载均衡功能时,端到端 TLS 允许你加密敏感数据并将其安全地传输到后端。 这些功能包括:基于 Cookie 的会话相关性、基于 URL 的路由、基于站点的路由支持、能够重写或注入 X-Forwarded-* 标头,等等。
如果配置为端到端 TLS 通信模式,应用程序网关会在网关上终止 TLS 会话,并解密用户流量。 然后,它会应用配置的规则,以选择要将流量路由到的适当后端池实例。 应用程序网关接下来会初始化到后端服务器的新 TLS 连接,并先使用后端服务器的公钥证书重新加密数据,然后再将请求传输到后端。 来自 Web 服务器的任何响应都会经历相同的过程返回最终用户。 若要启用端到端 TLS,请将后端 HTTP 设置中的协议设置设为 HTTPS,然后再将其应用到后端池。
在应用程序网关 v1 SKU 网关中,TLS 策略仅将 TLS 版本应用于前端流量,而将定义的密码应用于前端和后端目标。 在应用程序网关 v2 SKU 网关中,TLS 策略仅适用于前端流量,而后端 TLS 连接将始终通过 TLS 1.0 到 TLS 1.2 版本进行协商。
应用程序网关仅与符合以下条件的后端服务器通信:已将其证书加入应用程序网关的允许列表,或者其证书已由已知的 CA 颁发机构签名,并且证书的 CN 与 HTTP 后端设置中的主机名匹配。 这些服务器包括受信任的 Azure 服务,例如 Azure 应用服务/Web 应用和 Azure API 管理。
如果后端池成员的证书未由已知 CA 颁发机构签名,则必须为后端池中已启用端到端 TLS 的每个实例配置一个证书,这样才能进行安全通信。 添加证书后,可确保应用程序网关仅与已知后端实例通信。 从而进一步保护端到端通信。
Note
添加到“后端 HTTP 设置”中用于对后端服务器进行身份验证的证书可以与添加到侦听器中用于在应用程序网关上实现 TLS 终止的证书相同,也可以不同以增强安全性。
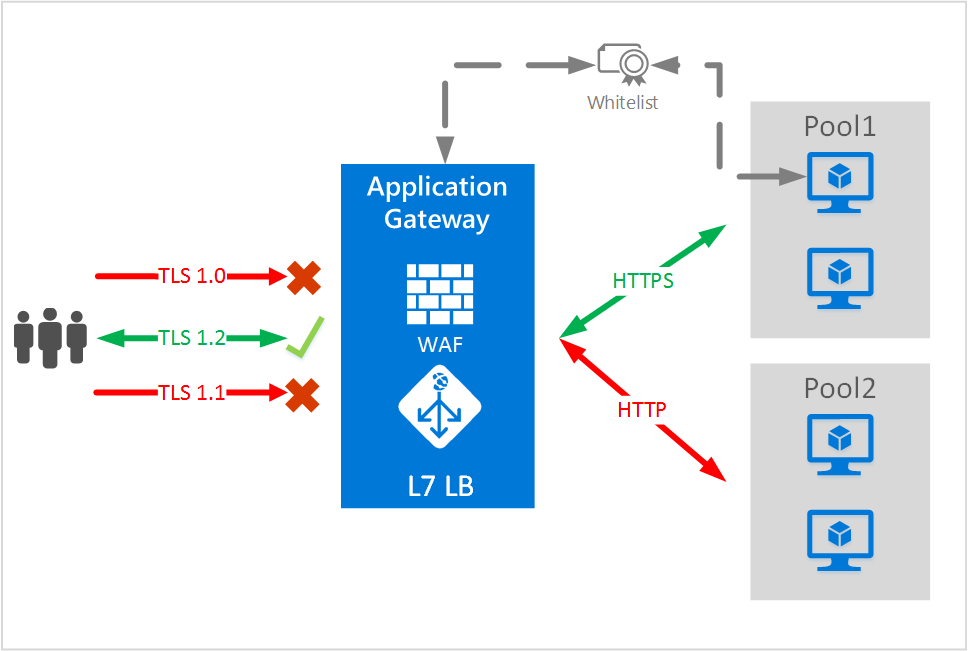
此示例通过端到端 TLS 将使用 TLS1.2 的请求路由到 Pool1 中的后端服务器。
端到端 TLS 和证书白名单
应用程序网关仅与符合以下条件的后端服务器通信:已将其证书加入应用程序网关的允许列表,或者其证书已由已知的 CA 颁发机构签名,并且证书的 CN 与 HTTP 后端设置中的主机名匹配。 根据所用应用程序网关版本的不同,端到端 TLS 的设置过程也存在一些差异。 以下部分将分别介绍这些版本。
v1 SKU 的端到端 TLS
若要为后端服务器启用端到端 TLS,并让应用程序网关将请求路由到后端服务器,运行状况探测必须成功并返回运行正常响应。
对于 HTTPS 运行状况探测,应用程序网关 v1 SKU 使用与要上传到 HTTP 设置的身份验证证书(后端服务器证书的公钥,而不是根证书)完全匹配的证书。
只允许连接到已知的和已允许的后端。 健康探测工具将其余后端服务器视为不健康。 自签名证书仅用于测试目的,不建议用于生产工作负荷。 如前面的步骤中所述,此类证书必须加入应用程序网关的允许列表才可以使用。
Note
Azure 应用服务之类的受信任的 Azure 服务不需要进行身份验证和受信任的根证书设置。 默认情况下,它们被认为是可信的。
使用 v2 SKU 的端到端 TLS
身份验证证书已弃用,并由应用程序网关 v2 SKU 中的受信任的根证书替换。 它们的功能与身份验证证书类似,但有一些主要区别:
由知名 CA 颁发机构签署且其 CN 与 HTTP 后端设置中的主机名匹配的证书,不需要任何额外的步骤即可支持端到端 TLS 功能。
例如,如果后端证书由知名 CA 颁发并具有 contoso.com 的 CN,并且后端 http 设置的主机字段也设置为 contoso.com,则不需要其他步骤。 可以将后端 HTTP 设置协议设置为 HTTPS,则运行状况探测和数据路径都会启用 TLS。 如果使用 Azure 应用服务或其他 Azure Web 服务作为后端,则这些服务也是受隐式信任的,不需要对端到端 TLS 执行其他步骤。
Note
为了使 TLS/SSL 证书受信任,后端服务器的证书必须由已知 CA 颁发。 如果证书不是由受信任的 CA 颁发的,应用程序网关会检查发证 CA 的证书是否由受信任的 CA 颁发,依此类推,直到找到受信任的 CA(此时会建立受信任的安全连接),或者直到找不到受信任的 CA(此时,应用程序网关会将后端标记为“运行不正常”)。 因此,建议后端服务器证书同时包含根 CA 和中间 CA。
如果后端服务器证书是自签名的,或者是由未知 CA/中介签名的,则要在应用程序网关 v2 中启用端到端 TLS,必须上传受信任的根证书。 应用程序网关仅与符合以下条件的后端进行通信:后端的服务器证书的根证书与后端 http 设置中与池关联的受信任根证书列表之一匹配。
除了根证书匹配之外,应用程序网关 v2 还会验证后端 http 设置中指定的主机设置是否与后端服务器的 TLS/SSL 证书提供的公用名 (CN) 的主机设置相匹配。 尝试与后端建立 TLS 连接时,应用程序网关 v2 会将服务器名称指示 (SNI) 扩展设置为后端 http 设置中指定的主机。
如果已选择“从后端目标选择主机名”,而不是选择后端 HTTP 设置中的主机字段,则 SNI 标头始终设置为后端池 FQDN,并且后端服务器 TLS/SSL 证书上的 CN 必须与其 FQDN 匹配。 此方案不支持具有 IP 的后端池成员。
根证书是来自后端服务器证书的 base64 编码的根证书。
v1 和 v2 SKU 中的 SNI 差异
如前所述,应用程序网关在应用程序网关侦听器处终止来自客户端的 TLS 流量(我们称其为前端连接),对流量进行解密,应用必要的规则来确定必须将请求转发到的后端服务器,并与后端服务器建立新的 TLS 会话(我们称其为后端连接)。
下表概述了 v1 和 v2 SKU 在前端和后端连接方面的 SNI 差异。
前端 TLS 连接(客户端到应用程序网关)
| Scenario | v1 | v2 |
|---|---|---|
| 如果客户端指定了 SNI 标头,且所有多站点侦听器都启用了“需要 SNI”选项 | 返回相应的证书;如果站点不存在(根据 server_name),则重置连接。 | 返回相应的证书(如可用);否则,根据与 HTTPS 侦听器关联的请求传递规则指定的顺序返回第一个 HTTPS 侦听器的证书 |
| 如果客户端未指定 SNI 标头,并且所有多站点标头都启用了“需要 SNI” | 重置连接 | 根据与 HTTPS 侦听器关联的请求传递规则指定的顺序返回第一个 HTTPS 侦听器的证书 |
| 如果客户端未指定 SNI 标头,并且有配置了证书的基本侦听器 | 将基本侦听器中配置的证书返回给客户端(默认或备用证书) | 返回具有最高优先级路由规则的 HTTPS 侦听器的证书。 基本侦听器证书 不 作为回退机制。 |
Important
V2 SKU 默认证书行为: 当客户端在没有 SNI 标头(例如使用 IP 地址)的情况下进行连接时,应用程序网关 V2 不会 回退到基本侦听器的证书。 相反,它始终从 HTTPS 侦听器返回证书,其关联的请求路由规则具有 最高优先级 (最低优先级编号)。 此行为不同于 V1 SKU,后者将基本侦听器的证书作为回退返回。
Tip
使用 SNI 孔控制默认证书: 若要防止应用程序网关 V2 在客户端在没有 SNI 的情况下通过 IP 地址连接时公开生产站点证书,可以配置“SNI 孔”:
- 使用虚拟主机名创建多站点 HTTPS 侦听器,该主机名与任何真实站点不匹配(例如)。
sni-hole.invalid - 将 自签名证书 上传到此侦听器。
- 创建与此侦听器关联的 请求路由规则 ,并在所有规则中为其分配 最高优先级 (最低优先级编号)。
使用此配置,任何没有匹配 SNI 标头的连接都会收到自签名证书,而不是有效的站点证书。 这可以防止仅限于 IP 的连接获取有关您托管站点的具体信息。
后端 TLS 连接(应用程序网关到后端服务器)
对于探测流量
| Scenario | v1 | v2 |
|---|---|---|
| 配置 FQDN 或 SNI 时 | 设置为后端池中的 FQDN。 根据 RFC 6066,SNI 主机名中不允许使用原义 IPv4 和 IPv6 地址。 | SNI 值是根据后端设置中的 TLS 验证类型 设置的。 1. 完成验证 - 探测按以下优先级顺序使用 SNI: a) 自定义健康探测的主机名 b)后端设置的主机名(根据覆盖值或从后端服务器中选择) 2. 可配置 使用特定的 SNI:探测使用此固定主机名进行验证。 跳过 SNI:不验证主题名称。 |
| 未配置 FQDN 或 SNI 时(仅提供 IP 地址) | 将不会设置 SNI (server_name)。 注意:在这种情况下,后端服务器应该能够返回默认/备用证书,并且该证书应加入 HTTP 设置中身份验证证书下的允许列表。 如果后端服务器中未配置默认/备用证书,但需要提供 SNI,则服务器可能会重置连接并导致探测失败 |
如果自定义探测或后端设置在主机名字段中使用了 IP 地址,那么将不会设置 SNI,这符合 RFC 6066 的规定。 这包括默认探测使用 127.0.0.1 的情况。 |
对于实时流量
| Scenario | v1 | v2 |
|---|---|---|
| FQDN 或 SNI 可用时 | SNI 是使用后端服务器的 FQDN 设置的。 | SNI 值是根据后端设置中的 TLS 验证类型 设置的。 1. 完成验证 - 根据以下优先级顺序设置 SNI: a)后端设置中的主机名(根据重写的值或从后端服务器选取) b) 传入客户端请求的主机标头 2. 可配置 使用特定的 SNI:使用此固定主机名进行验证。 跳过 SNI:不验证主题名称。 |
| 当 FQDN 或 SNI 不可用时(只有 IP 地址可用) | 根据 RFC 6066,如果后端池条目不是 FQDN,则不设置 SNI | SNI 不会根据 RFC 6066 设置。 |
后续步骤
了解端到端 TLS 后,请转到使用应用程序网关和 PowerShell 配置端到端 TLS,以使用端到端 TLS 创建应用程序网关。