Azure 应用程序网关是一个 Web 流量负载均衡器,可帮助你管理发到 Web 应用程序的流量。 与基于 IP 地址和端口路由流量的传统负载均衡器不同,应用程序网关基于 HTTP 请求属性(如 URL 路径和主机标头)做出智能路由决策。
例如,可以将 URL 中的请求 /images 路由到针对图像优化的服务器,同时将请求路由 /video 到针对视频内容优化的服务器。 通过此应用程序层路由,可以更好地控制流量流向应用程序的方式。
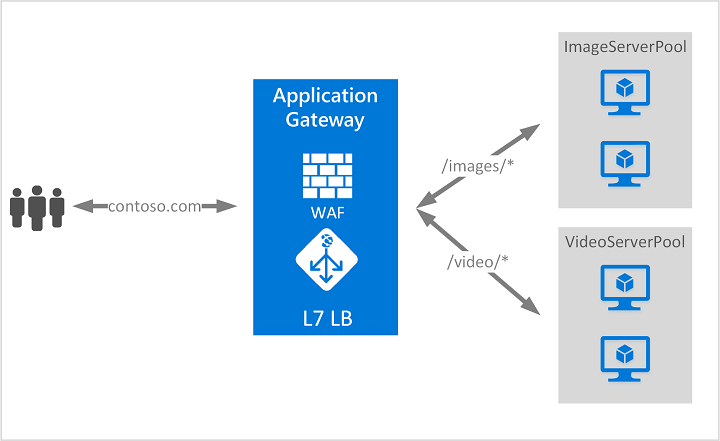
应用程序网关在应用程序层(OSI 第 7 层)运行,并提供 SSL/TLS 终止、自动缩放、区域冗余以及与 Web 应用程序防火墙集成等功能,以确保安全性。
注意
Azure 为方案提供了一套完全托管的负载均衡解决方案。
- 如果要执行基于 DNS 的全局路由,并且不需要传输层安全性(TLS)协议终止(“SSL 卸载”),每个 HTTP/HTTPS 请求或应用程序层处理,请查看 流量管理器。
- 如果需要优化 Web 流量的全局路由,并且需要通过快速全局故障转移来优化顶层最终用户的性能和可靠性,请参阅 Front Door。
- 若要执行传输层负载均衡,请查看负载均衡器。
端到端方案可以从根据需要组合这些解决方案中获益。
功能
若要了解应用程序网关功能,请参阅 Azure 应用程序网关功能。
基础结构
要了解应用程序网关基础结构,请参阅 Azure 应用程序网关基础结构配置。
安全性
使用 WAF 保护应用程序免受 L7 层 DDoS 保护。 有关详细信息,请参阅应用程序 DDoS 防护。
使用基于 Microsoft 自己的威胁情报的机器人管理器规则,保护你的应用免受恶意行动者的攻击。
使用 Azure DDoS 防护计划保护应用程序免受 L3 和 L4 DDoS 攻击。
使用专用链接以私密方式连接到位于应用程序网关后面的后端,并采用零信任访问模型。
通过完全仅限专用的应用程序网关部署,消除数据外泄的风险,并控制虚拟网络中的通信隐私。
通过 Azure Policy、Azure 顾问和 Microsoft Sentinel 集成确保跨应用实现一致的安全功能,从而为你的应用程序提供集中式安全体验。
定价和 SLA
有关应用程序网关定价信息,请参阅应用程序网关定价。
有关应用程序网关 SLA 信息,请参阅应用程序网关 SLA。
新增功能
若要了解 Azure 应用程序网关的新增功能,请参阅 Azure 更新。
后续步骤
根据要求和环境,可以使用 Azure 门户、Azure PowerShell 或 Azure CLI 创建测试应用程序网关。