从现有的运行方式帐户迁移到托管标识
重要
Azure 自动化运行方式帐户(包括经典运行方式帐户)已于 2023 年 9 月 30 日停用,被托管标识取代。 再也无法通过 Azure 门户创建或续订运行方式帐户。
有关迁移节奏以及运行方式帐户创建和证书续订支持时间表的详细信息,请参阅常见问题解答。
Azure 自动化中的运行方式帐户提供身份验证,以管理通过 Azure 资源管理器或经典部署模型部署的资源。�每当创建运行方式帐户时,都会注册一个 Microsoft Entra 应用程序,并生成一个自签名证书。 该证书的有效期为一个月。�每月在证书过期之前续订证书可使自动化帐户保持正常,但会增加开销。
现在,可将自动化帐户配置为使用托管标识,这是创建自动化帐户时的默认选项。 借助此功能,自动化帐户可对 Azure 资源进行身份验证,而无需交换任何凭据。 托管标识消除了续订证书或管理服务主体的开销。
托管标识可以是系统分配或用户分配的标识。 创建新的自动化帐户时,将启用系统分配的托管标识。
先决条件
在从运行方式帐户或经典运行方式帐户迁移到托管标识之前:
创建系统分配或用户分配的托管标识,或创建这两种类型的标识。 若要详细了解这两种类型之间的差别,请参阅托管标识类型。
注意
- 仅云作业支持用户分配的标识。 无法在混合 Runbook 辅助角色上使用自动化帐户的用户托管标识。 若要使用混合作业,必须创建系统分配的标识。
- 可通过两种方式在混合 Runbook 辅助角色脚本中使用托管标识:使用自动化帐户的系统分配的托管标识,或者作为混合 Runbook 辅助角色运行的 Azure 虚拟机 (VM) 的 VM 托管标识。
- 在配置了自动化帐户托管标识的自动化帐户中,VM 的用户分配的托管标识以及 VM 的系统分配的托管标识不起作用。 启用自动化帐户的托管标识时,只能使用自动化帐户的系统分配的托管标识,而不能使用 VM 托管标识。 有关详细信息,请参阅结合托管标识使用 Runbook 身份验证。
将同一角色分配到托管标识,以访问与运行方式帐户匹配的 Azure 资源。 使用此脚本在自动化帐户中启用系统分配的标识,并将 Azure 自动化运行方式帐户中存在的相同权限集分配给自动化帐户的系统分配的标识。
例如,如果自动化帐户只需用于启动或停止 Azure VM,则分配给运行方式帐户的权限只需是用于启动或停止 VM 的权限。 同样,如果 Runbook 从 Azure Blob 存储读取数据,则分配只读权限。 有关详细信息,请参阅 Azure 自动化安全准则。
如果使用的是经典运行方式帐户,请确保已将通过经典部署模型部署的资源迁移到 Azure 资源管理器。
使用此脚本可找出哪些自动化帐户正在使用运行方式帐户。 如果 Azure 自动化帐户包含运行方式帐户,则默认会为其分配内置参与者角色。 可以使用脚本检查 Azure 自动化运行方式帐户,并确定其角色分配是否为默认角色或是否已更改为其他角色定义。
使用此脚本来确定自动化帐户中的所有 runbook 是否都使用运行方式帐户。
从自动化运行方式帐户迁移到托管标识
若要从自动化运行方式帐户或经典运行方式帐户迁移到托管标识来进行 Runbook 身份验证,请执行以下步骤:
更改 Runbook 代码以使用托管标识。
我们建议测试托管标识,以通过创建生产 Runbook 的副本来验证 Runbook 是否按预期工作。 更新测试 Runbook 代码以使用托管标识进行身份验证。 此方法确保不会替代生产 Runbook 中的
AzureRunAsConnection和破坏现有的自动化实例。 在确认 Runbook 代码可以通过托管标识按预期运行后,更新生产 Runbook 以使用托管标识。若要获取托管标识支持,请使用
Connect-AzAccountcmdlet。 若要详细了解此 cmdlet,请参阅 PowerShell 参考中的 Connect-AzAccount。- 如果使用
Az模块,请遵循更新 Azure PowerShell 模块一文中的步骤更新到最新版本。 - 如果使用 AzureRM 模块,请将
AzureRM.Profile更新到最新版本,并结合Connect-AzureRMAccount �Identity使用Add-AzureRMAccountcmdlet 来替换它。
若要了解在使用托管标识之前需要对 Runbook 代码做出哪些更改,请使用示例脚本。
- 如果使用
在确认 Runbook 可以使用托管标识成功运行后,如果没有其他 Runbook 使用运行方式帐户,可以放心删除运行方式帐户。
示例脚本
以下 Runbook 脚本示例使用运行标识帐户(服务主体)和托管标识提取资源管理器资源。 你会在 Runbook 开头的 Runbook 代码中看到差异,此代码对资源进行身份验证。
注意
为此自动化帐户的系统标识启用适当的 RBAC 权限。 否则,Runbook 可能失败。
try
{
"Logging in to Azure..."
Connect-AzAccount -Identity -Environment AzureChinaCloud
}
catch {
Write-Error -Message $_.Exception
throw $_.Exception
}
#Get all Resource Manager resources from all resource groups
$ResourceGroups = Get-AzResourceGroup
foreach ($ResourceGroup in $ResourceGroups)
{
Write-Output ("Showing resources in resource group " + $ResourceGroup.ResourceGroupName)
$Resources = Get-AzResource -ResourceGroupName $ResourceGroup.ResourceGroupName
foreach ($Resource in $Resources)
{
Write-Output ($Resource.Name + " of type " + $Resource.ResourceType)
}
Write-Output ("")
}
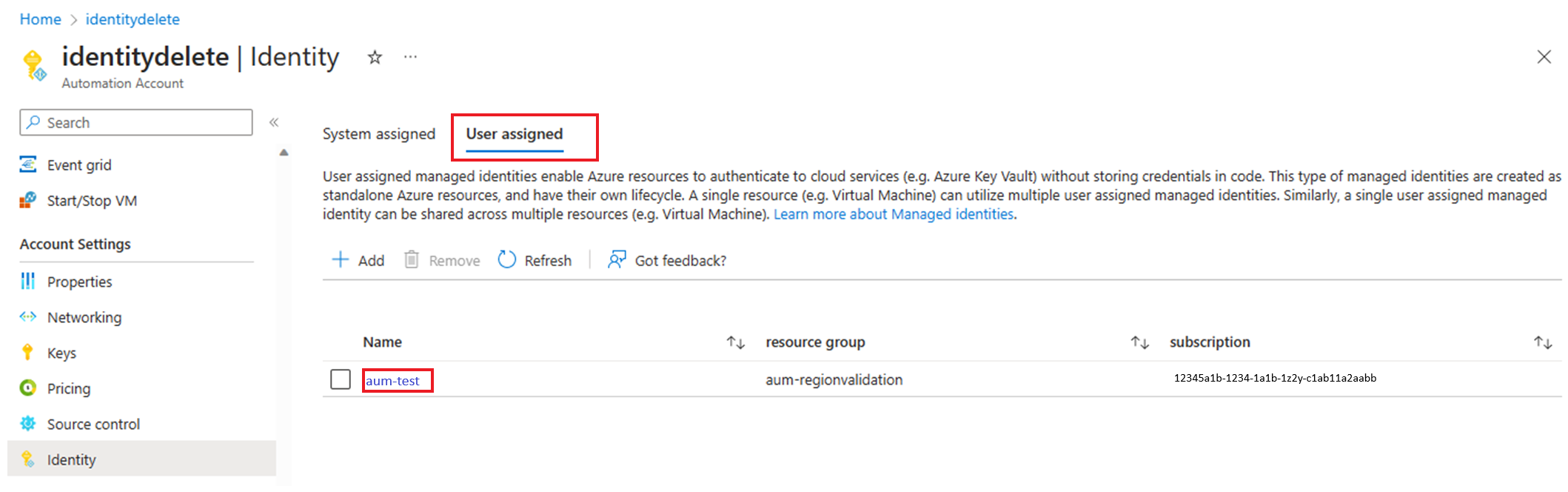
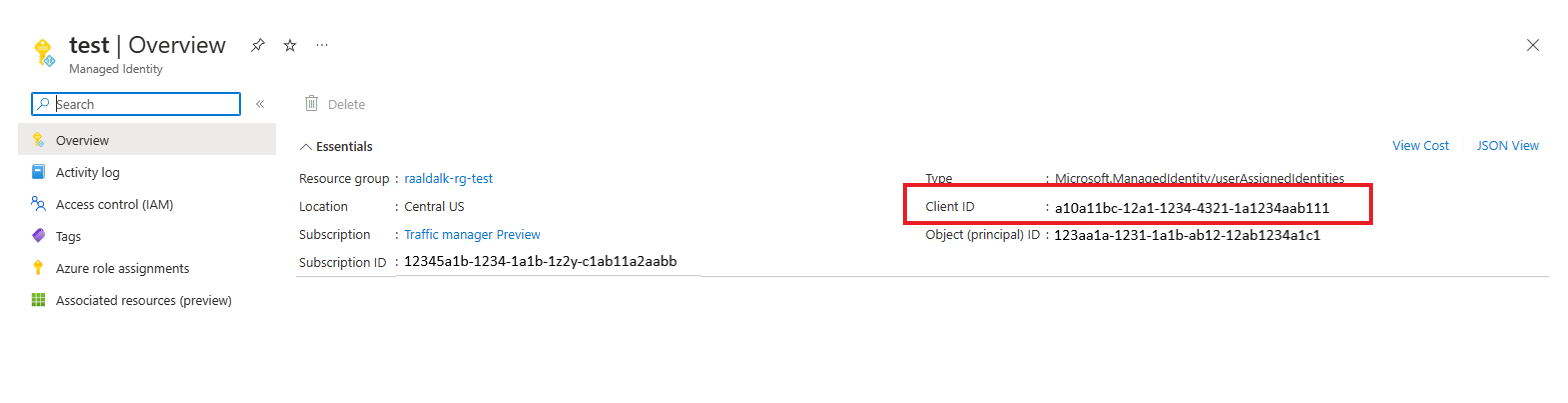
查看用户分配的标识的客户端 ID
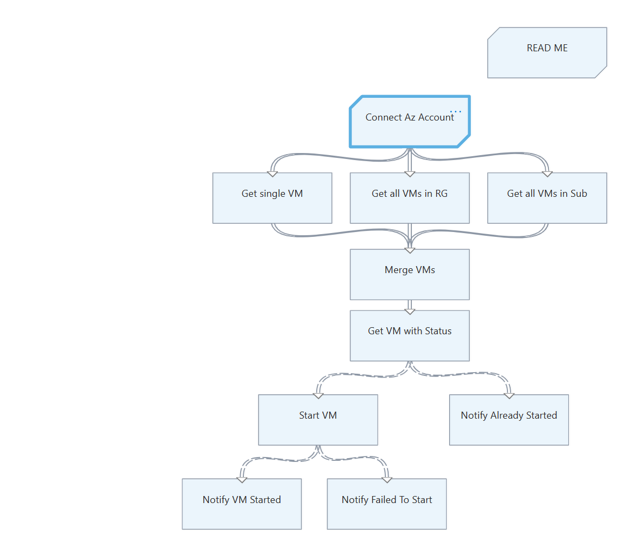
图形 Runbook
检查图形 Runbook 中是否使用了运行方式帐户
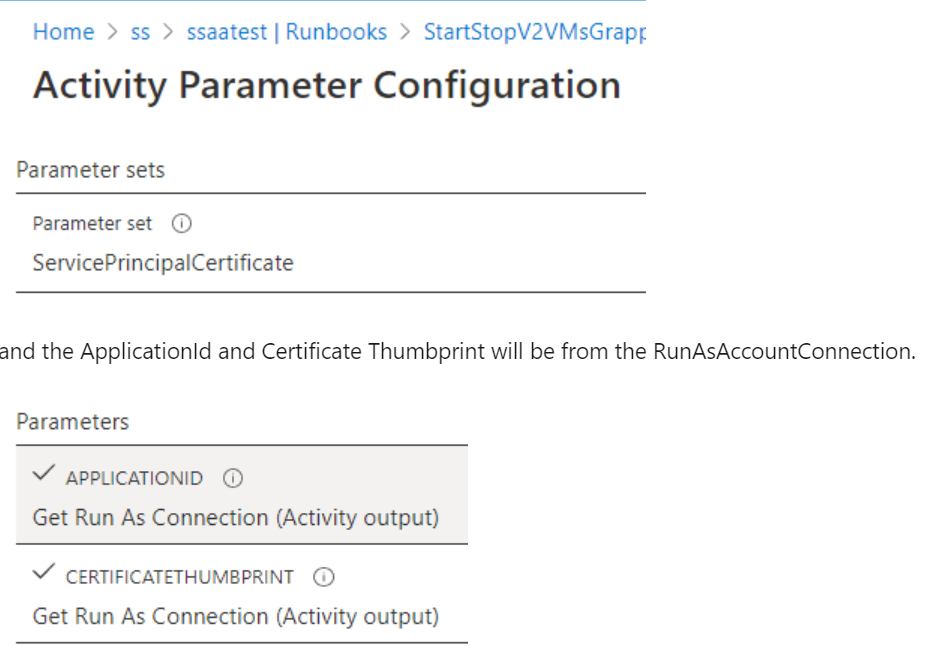
检查 Runbook 中的每个活动,确定该 Runbook 在调用任何登录 cmdlet 或别名(例如
Add-AzRmAccount/Connect-AzRmAccount/Add-AzAccount/Connect-AzAccount)时是否使用运行方式帐户。检查 cmdlet 使用的参数。
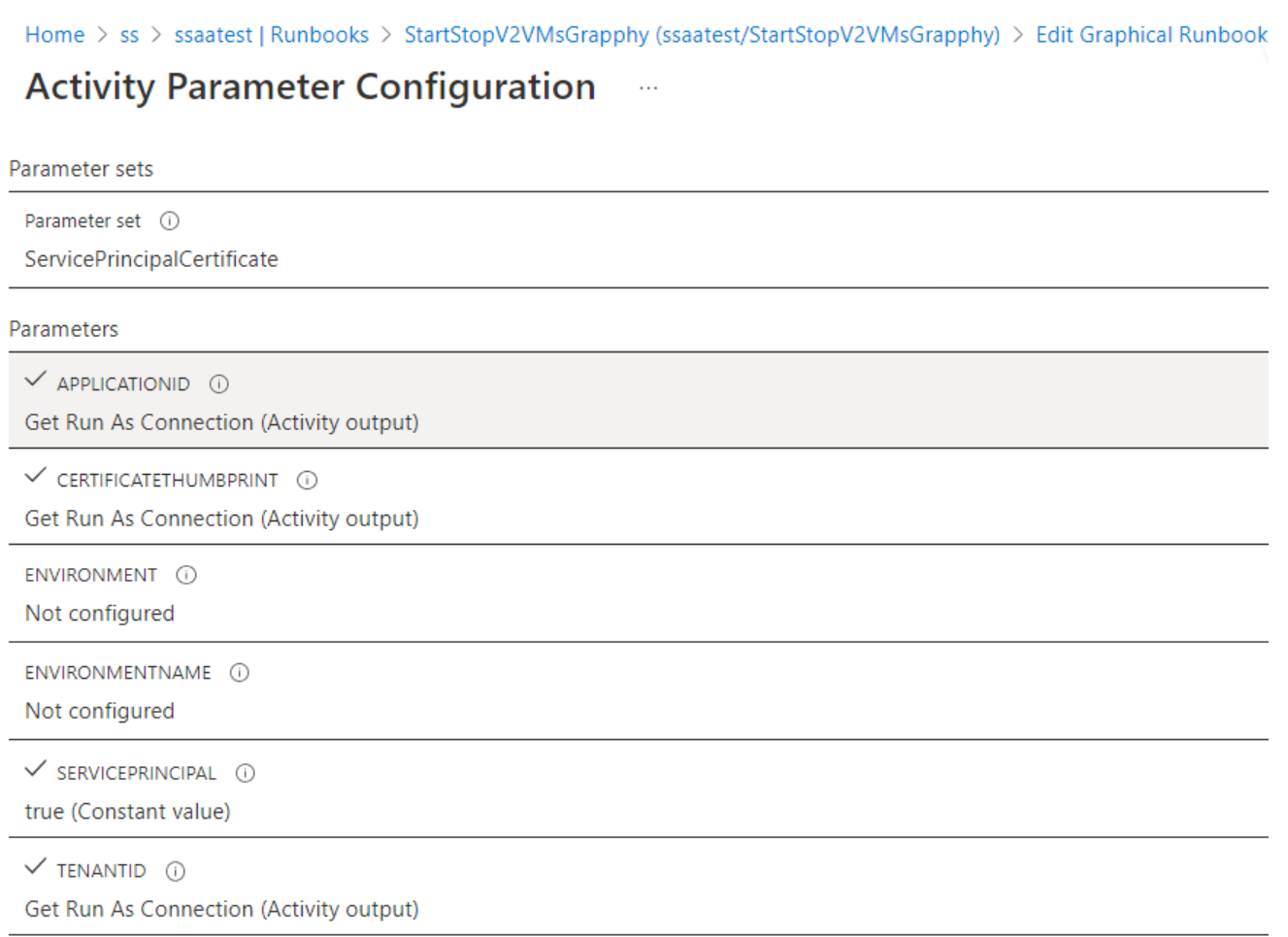
为了与运行方式帐户配合使用,cmdlet 将使用设置为
ApplicationId的ServicePrinicipalCertificate参数。CertificateThumbprint来自RunAsAccountConnection。
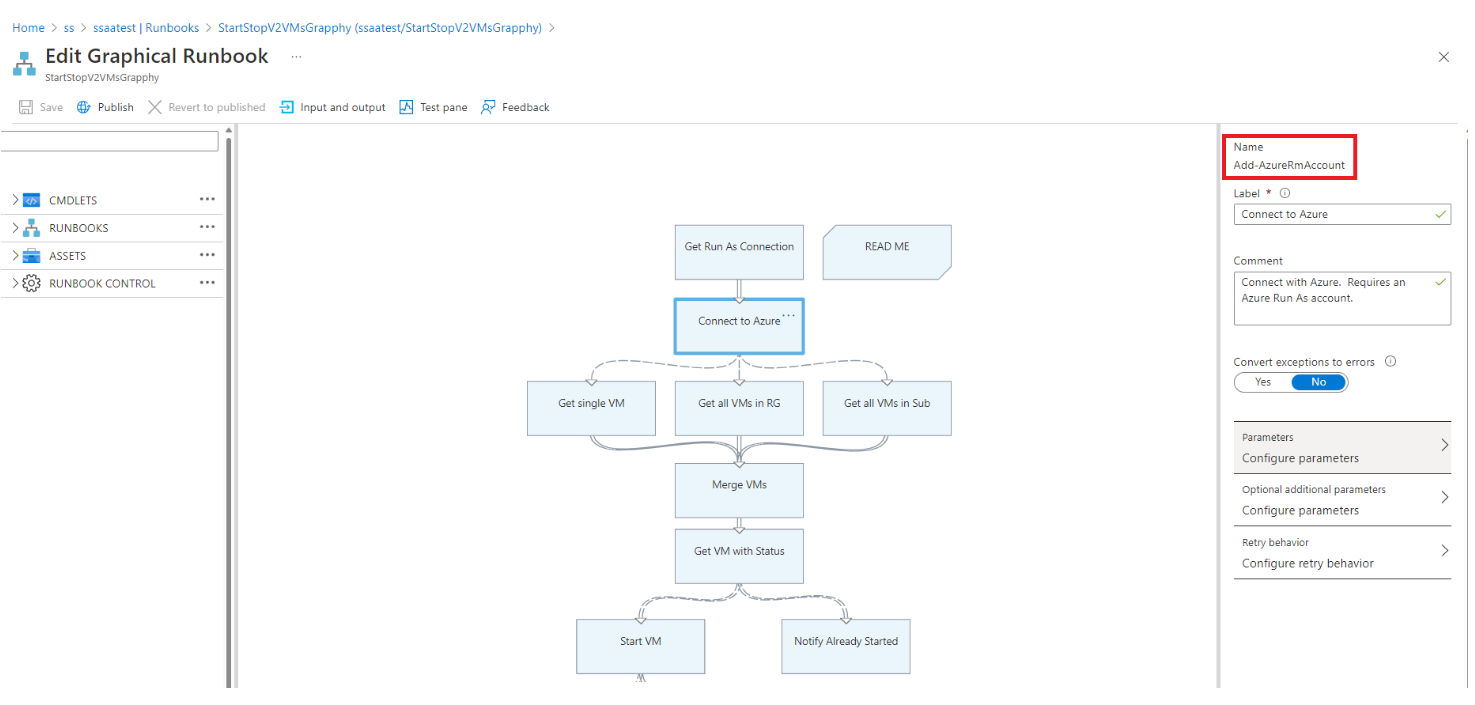
编辑图形 Runbook 以使用托管标识
必须测试托管标识以验证图形 Runbook 是否按预期工作。 创建生产 Runbook 的副本以使用托管标识,然后更新测试图形 Runbook 代码以使用托管标识进行身份验证。 可以通过添加 Connect-AzAccount cmdlet 将此功能添加到图形 Runbook。
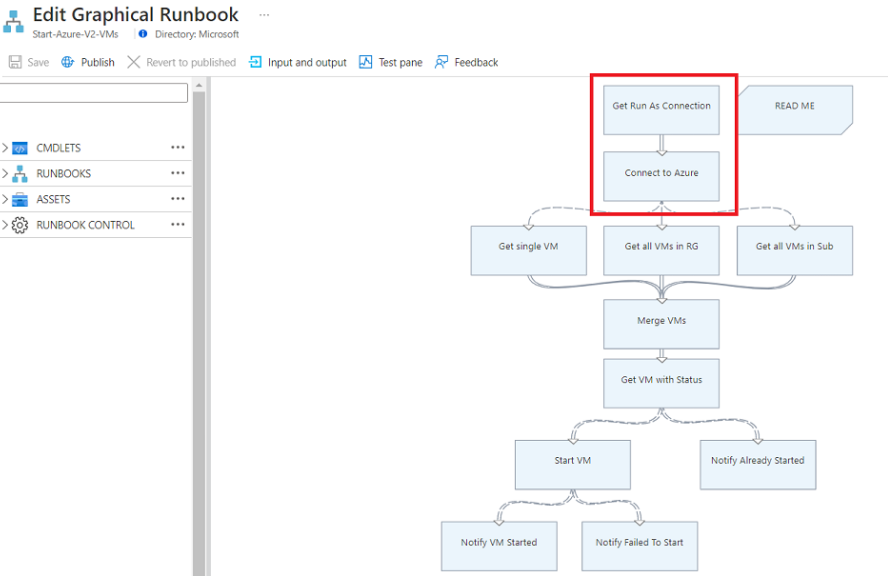
以下步骤包含一个示例,用于演示使用运行方式帐户的图形 Runbook 如何使用托管标识:
登录 Azure 门户。
打开自动化帐户,然后选择“流程自动化”>“Runbook”。
选择一个 Runbook。 例如,从列表中选择“启动 Azure V2 VM Runbook”,然后选择“编辑”或转到“浏览库”,然后选择“启动 Azure V2 VM”。
将使用
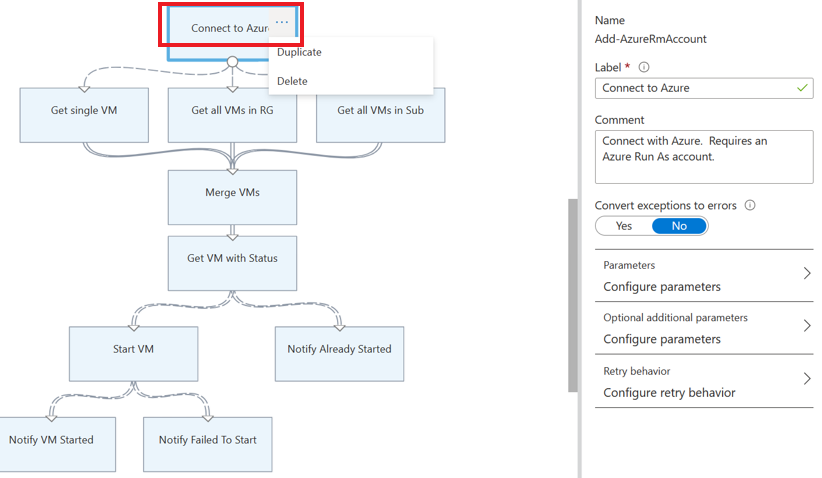
AzureRunAsConnection的运行方式连接以及在内部使用 PowerShellGet-AutomationConnectioncmdlet 的连接资产替换为Connect-AzAccountcmdlet。选择“删除”以删除
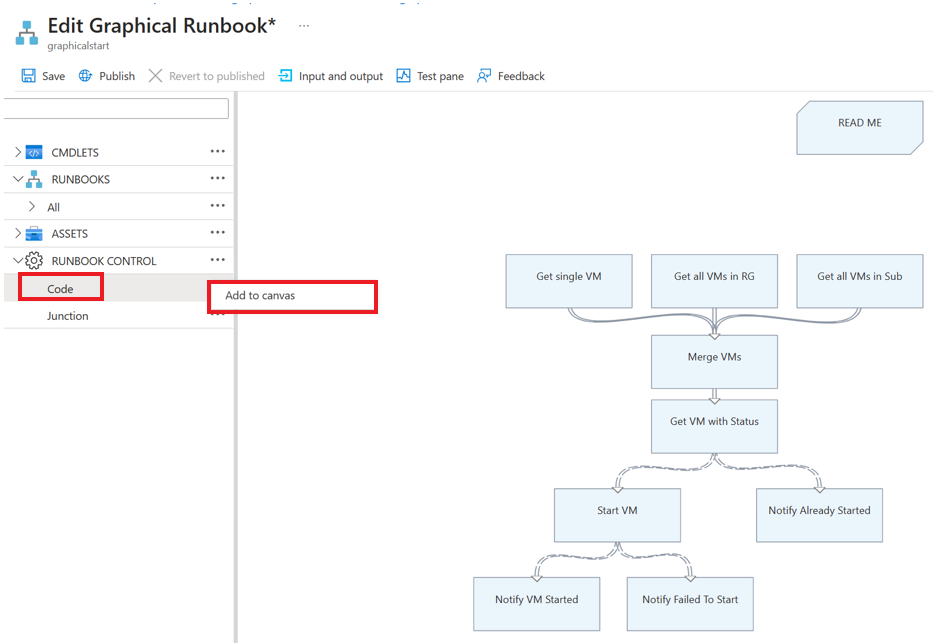
Get Run As Connection和Connect to Azure活动。在左侧面板中的“RUNBOOK CONTROL”下,选择“代码”,然后选择“添加到画布”。
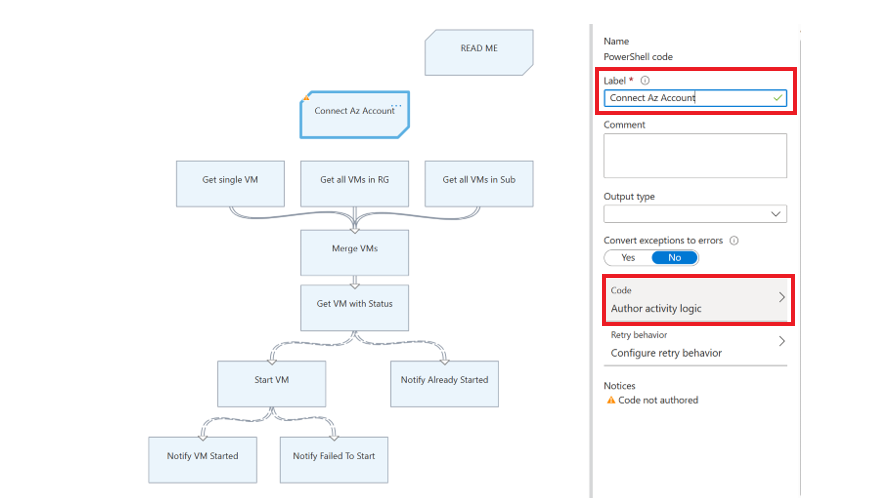
编辑代码活动,分配任何适当的标签名称,然后选择“创作活动逻辑”。
在“代码编辑器”页中,输入以下 PowerShell 代码,然后选择“确定”。
try { Write-Output ("Logging in to Azure...") Connect-AzAccount -Identity -Environment AzureChinaCloud } catch { Write-Error -Message $_.Exception throw $_.Exception }将新活动连接到之前通过连接到 Azure 所连接的活动,并保存 Runbook。
例如,在 Runbook 库中的“启动 Azure V2 VM”Runbook 中,必须如上所述,将 Get Run As Connection 和 Connect to Azure 活动替换为使用 Connect-AzAccount -Environment AzureChinaCloud cmdlet 的代码活动。
有关详细信息,请参阅使用自动化帐户创建的示例 Runbook 名称“AzureAutomationTutorialWithIdentityGraphical”。
注意
AzureRM PowerShell 模块将于 2024 年 2 月 29 日停用。 如果你在图形 Runbook 中使用 AzureRM PowerShell 模块,必须升级这些模块以使用 Az PowerShell 模块。 了解详细信息。
后续步骤
如果 Runbook 不能成功完成,请查看排查 Azure 自动化托管标识问题。
若要详细了解系统分配的托管标识,请参阅为 Azure 自动化帐户使用系统分配的托管标识。
若要详细了解用户分配的托管标识,请参阅为 Azure 自动化帐户使用用户分配的托管标识。
有关 Azure 自动化帐户安全性的信息,请参阅 Azure 自动化帐户身份验证概述。