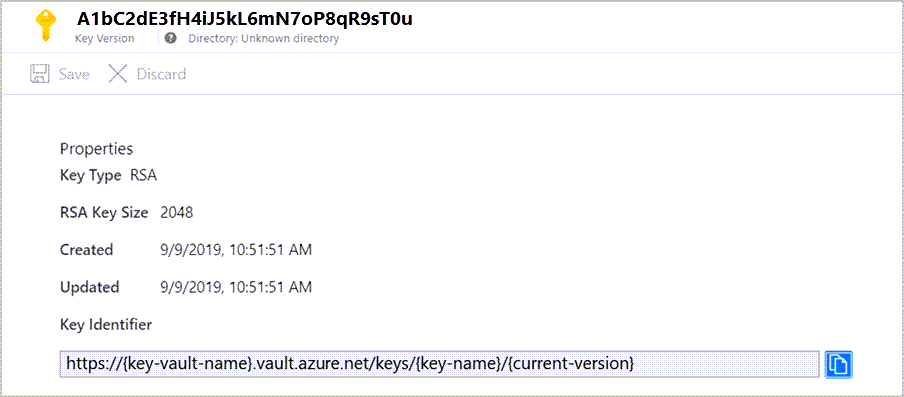
使用 Azure 管理的密钥对 Azure Monitor 中的数据进行加密。 可以使用自己的加密密钥来保护工作区中的数据。 Azure Monitor 中的客户管理的密钥使你可以控制加密密钥生命周期和对日志的访问。 配置后,引入到链接工作区的新数据会使用 Azure Key Vault 中的密钥或 Azure Key Vault 托管 HSM (硬件安全模块)进行加密。
客户管理的密钥概述
静态数据加密是组织中常见的隐私和安全要求。 可以让 Azure 完全管理静态加密,也可以使用各种选项严格管理加密和加密密钥。
Azure Monitor 确保使用 Azure 管理的密钥 (MMK) 静态加密所有数据和保存的查询。 Azure Monitor 进行加密的操作与Azure 存储加密的操作相同。
若要控制密钥生命周期,并能够撤销访问数据、使用自己的密钥在 Azure Key Vault 或 Azure Key Vault 托管 HSM 中加密数据。 客户管理的密钥功能在 专用群集 上可用,并提供更高级别的保护和控制。
引入到专用群集的数据进行两次加密 - 一次在服务级别使用 Azure 管理的密钥或客户管理的密钥进行,一次在基础结构级别使用两种不同的加密算法和两个不同的密钥进行。 双重加密可以在其中一种加密算法或密钥被泄露的情况下提供保护。
过去 14 天内引入的数据或最近在查询中使用的数据保存在热缓存(受 SSD 支持)中,以提高查询效率。 SSD 数据使用 Azure 管理的密钥进行加密,而不管你是否配置客户管理的密钥,但你对 SSD 访问的控制遵循密钥吊销规定。
重要
专用群集使用承诺层级定价模型,该模型至少为 100 GB/天。
客户管理的密钥在 Azure Monitor 中的工作原理
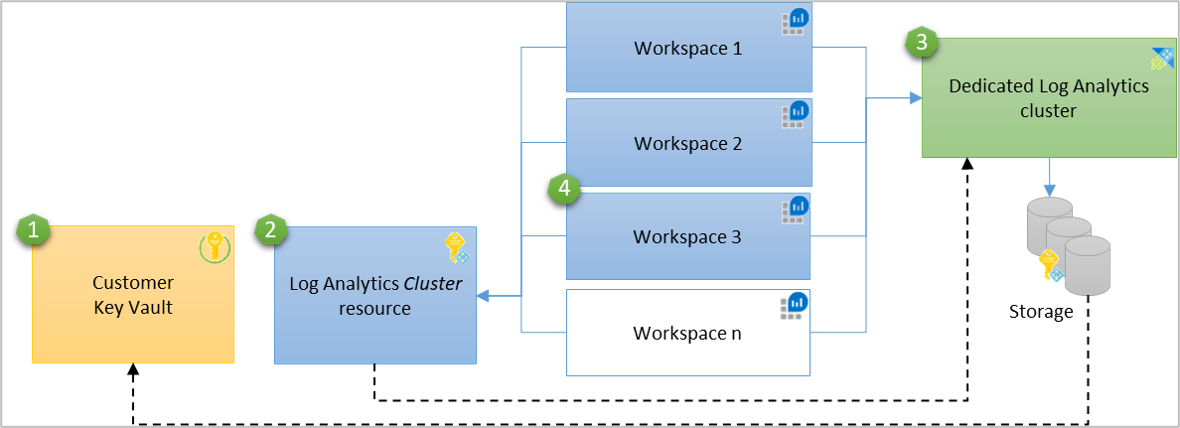
Azure Monitor 使用托管标识授予对 Azure Key Vault 中的密钥的访问权限。 系统将在群集级别支持 Log Analytics 群集的标识。 为了在多个工作区提供客户管理的密钥,Log Analytics 群集资源充当 Key Vault 和 Log Analytics 工作区之间的中间标识连接。 群集的存储使用与群集关联的托管标识,通过 Microsoft Entra ID 对 Azure Key Vault 进行身份验证。
群集支持两种托管标识类型:系统分配的标识和用户分配的标识,而单一标识可根据自己的场景在群集中进行自定义。
- 系统分配的托管标识更简单,会在
identitytype设置为SystemAssigned时随群集自动生成。 此标识稍后用于授予对 Key Vault 的存储访问权限,以便进行数据加密和解密。 - 用户分配的托管标识让你可以在创建群集时配置客户管理的密钥(如果
identitytype设置为UserAssigned,且在创建群集之前在 Key Vault 中向其授予权限)。
在新群集上或具有链接的数据引入工作区的现有专用群集上配置客户管理的密钥。 可以随时从群集取消链接工作区。 引入到链接工作区的新数据使用密钥进行加密,旧数据仍使用 Azure 管理的密钥进行加密。 配置不会中断引入或查询,查询可以无缝地跨新旧数据执行。 从群集取消链接工作区时,引入的新数据会使用 Azure 管理的密钥进行加密。
重要
客户管理的密钥功能是区域性的。 您的 Azure Key Vault、专用群集和链接工作区必须位于同一地区,但可以分别属于不同的订阅账户。
- Key Vault
- Log Analytics 群集资源具有拥有 Key Vault 权限的托管标识,此标识可传播到基础专用群集存储
- 专用群集
- 链接到专用群集的工作区
加密密钥类型
存储数据加密涉及 3 种类型的密钥:
- KEK - 密钥加密密钥(客户管理的密钥)
- AEK - 帐户加密密钥
- DEK - 数据加密密钥
下列规则适用:
- 群集存储为每个存储帐户都有唯一的加密密钥,称为 AEK。
- AEK 用于派生 DEKs,这是用于加密写入磁盘的每个数据块的密钥。
- 在群集中配置客户管理的 KEK 时,群集存储会针对
wrap加密和解密对 Key Vault 执行unwrap和请求。 - KEK 永远不会离开 Key Vault。 如果将密钥存储在 Azure Key Vault 托管 HSM 中,则它永远不会离开该硬件。
- Azure 存储使用与群集关联的托管标识进行身份验证。 它通过 Microsoft Entra ID 访问 Azure Key Vault。
客户管理的密钥的预配步骤
- 创建 Azure Key Vault 和存储密钥
- 创建专用群集
- 向 Key Vault 授予权限
- 为专用群集更新密钥 ID 详细信息
- 链接工作区
客户管理的密钥配置不支持设置标识详情和密钥识别码。 通过 PowerShell、 CLI 或 REST 请求执行这些作。
所需的权限
若要执行与群集相关的操作,需要以下权限:
| 行动 | 所需的权限或角色 |
|---|---|
| 创建专用群集 |
Microsoft.Resources/deployments/* 和 Microsoft.OperationalInsights/clusters/write 权限,例如 Log Analytics 参与者内置角色中所提供的权限 |
| 更改群集属性 |
Microsoft.OperationalInsights/clusters/write 权限,例如 Log Analytics 参与者内置角色中所提供的权限 |
| 将工作区链接到群集 |
Microsoft.OperationalInsights/clusters/write、Microsoft.OperationalInsights/workspaces/write 和 Microsoft.OperationalInsights/workspaces/linkedservices/write 权限,例如 Log Analytics 参与者内置角色中所提供的权限 |
| 检查工作区链接状态 | 工作区的 Microsoft.OperationalInsights/workspaces/read 权限,例如 Log Analytics 读取者内置角色中所提供的权限 |
| 获取群集或检查群集的预配状态 |
Microsoft.OperationalInsights/clusters/read 权限,例如 Log Analytics 读取者内置角色中所提供的权限 |
| 更新群集中的承诺层级或计费类型 |
Microsoft.OperationalInsights/clusters/write 权限,例如 Log Analytics 参与者内置角色中所提供的权限 |
| 授予所需权限 | 具有 */write 权限的所有者或参与者角色,或 具有 权限的 Microsoft.OperationalInsights/* |
| 从群集中取消与工作区的链接 |
Microsoft.OperationalInsights/workspaces/linkedServices/delete 权限,例如 Log Analytics 参与者内置角色中所提供的权限 |
| 删除专用群集 |
Microsoft.OperationalInsights/clusters/delete 权限,例如 Log Analytics 参与者内置角色中所提供的权限 |
存储加密密钥 (KEK)
Azure 密钥管理产品组合列出了可以使用的保管库和托管 HSM。
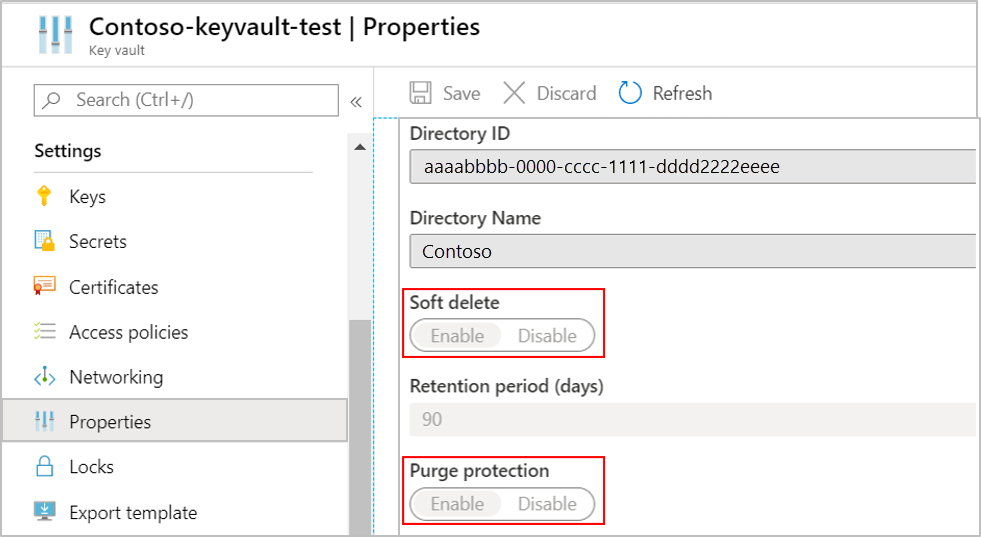
在计划群集的区域中创建或使用现有的 Azure Key Vault。 在 Key Vault 中,生成或导入用于日志加密的密钥。 必须将 Azure Key Vault 配置为可恢复,以保护密钥以及对 Azure Monitor 中的数据的访问权限。 可以验证是否应启用 Key Vault 中“软删除”和“清除保护”属性下的此配置 。
重要
建议通过 Azure 事件网格 设置通知,以有效响应 Azure Key Vault 事件,例如即将过期的密钥。 密钥过期时,引入和查询不会受到影响,但无法更新群集中的密钥。 按照以下步骤解决此问题
- 在 Azure 门户的群集概述页下的 JSON 视图中识别所用的密钥。
- 在 Azure Key Vault 中延长密钥到期日期
- 使用活动密钥更新群集,最好使用版本值“”,以始终自动使用最新版本
可以通过 CLI 和 PowerShell 在 Key Vault 中更新这些设置:
创建群集
群集使用托管标识对 Key Vault 进行数据加密。 在identity时将 typeSystemAssigned 属性配置为 UserAssigned 或 ,以允许访问 Key Vault 进行数据加密和解密操作。
例如,在系统分配的托管标识的请求正文中添加这些属性
{
"identity": {
"type": "SystemAssigned"
}
}
注意
创建群集后,可以更改标识类型,且不会中断引入或查询,但有以下注意事项:
- 无法同时为群集更新标识和密钥。 在两个连续操作中更新。
- 将
SystemAssigned更新为UserAssigned时,在 Key Vault 中 授予UserAssign标识,然后在群集中更新identity。 - 将
UserAssigned更新为SystemAssigned时,在 Key Vault 中 授予SystemAssigned标识,然后在群集中更新identity。
请按照“专用群集”一文中阐述的过程进行操作。
授予 Key Vault 权限
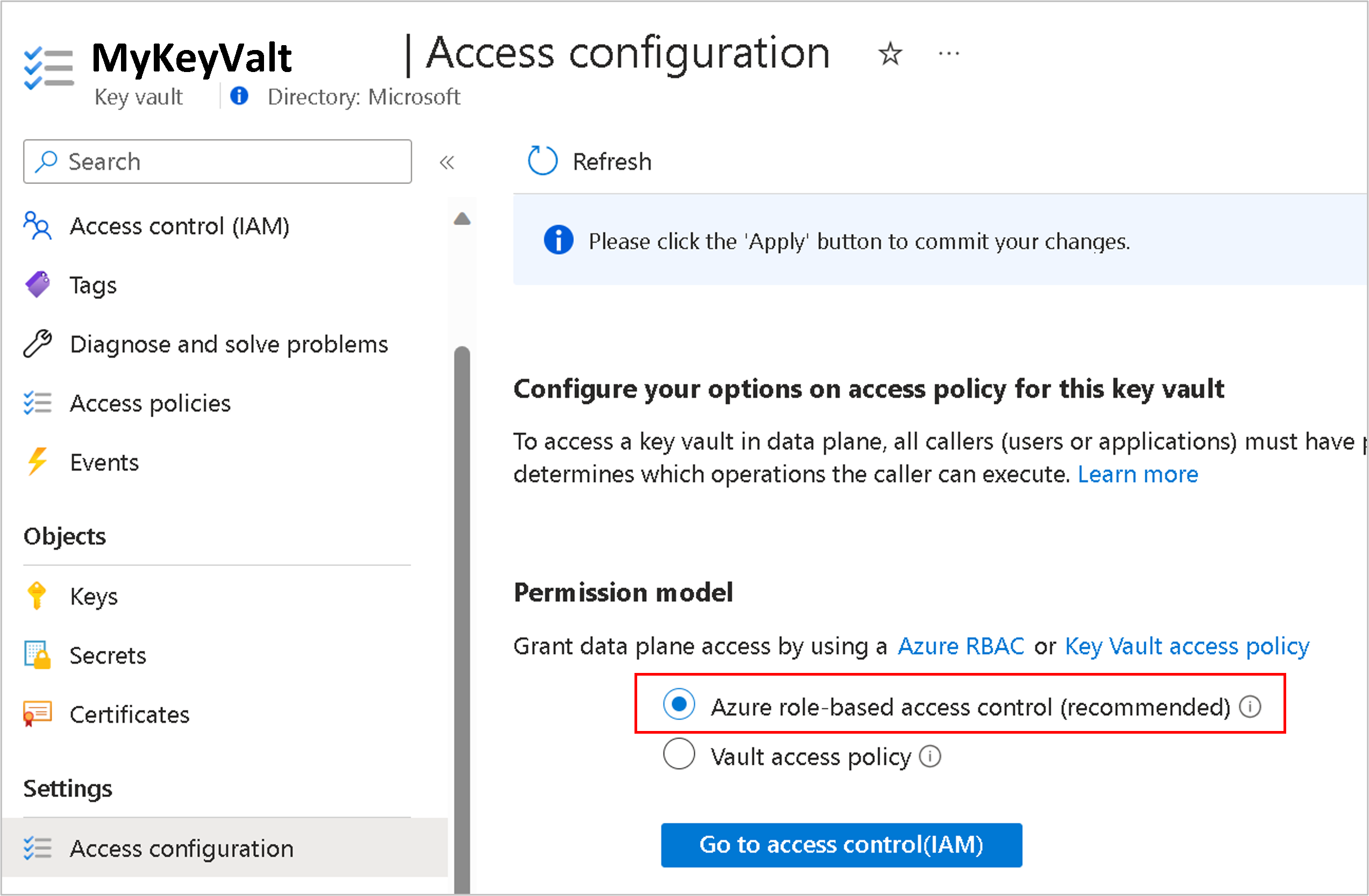
Azure 密钥保管库中有两种权限模型用于向群集和底层存储授予权限,分别是基于 Azure 角色的访问控制 (Azure RBAC) 和保管库访问策略(旧版)。
分配你控制的 Azure RBAC(建议做法)
若要添加角色分配,你必须具有一个拥有
Microsoft.Authorization/roleAssignments/write和Microsoft.Authorization/roleAssignments/delete权限的角色,例如用户访问管理员或所有者。- 在 Azure 门户中打开 Key Vault,然后选择 “设置>访问配置>Azure 基于角色的访问控制 并 应用”。
- 选择 “转到访问控制(IAM)”,并添加 Key Vault 加密服务加密用户 角色分配。
- 在“成员”选项卡中选择“托管标识”,然后选择相应标识对应的订阅,从而将该标识作为成员。
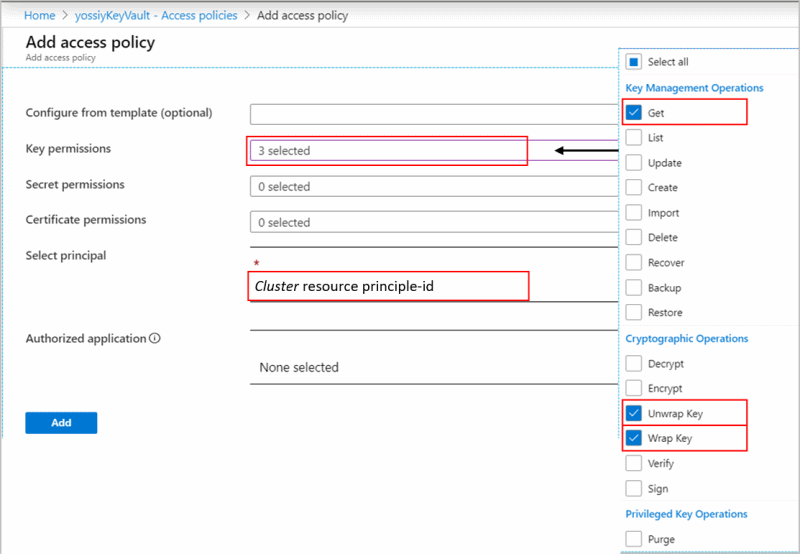
分配保管库访问策略(旧版)
在 Azure 门户中打开 Key Vault,然后选择“访问策略”“保管库访问策略”>“+ 添加访问策略”以使用以下设置创建策略>:
- 密钥权限 - 选择“ 获取>包装密钥 ”和 “解包密钥”。
- 根据群集中使用的标识类型(系统或用户分配的托管标识)选择主体
- 系统分配的托管标识 - 输入群集名称或群集主体 ID
- 用户分配的托管标识 - 输入标识名称
需要“获取”权限,才能验证是否已将 Key Vault 配置为可恢复以保护密钥以及对 Azure Monitor 数据的访问。
为群集更新密钥标识符详细信息
群集的所有操作都需要 Microsoft.OperationalInsights/clusters/write 操作权限。 可以通过包含 */write 操作的所有者或参与者或包含 Microsoft.OperationalInsights/* 操作的 Log Analytics 参与者角色授予此权限。
此步骤更新专用群集存储的密钥和版本,以便用于 AEKwrap 和 unwrap。
重要
- 密钥轮换可以是自动操作,也可以遵守显式的密钥版本。请参阅密钥轮换,确定合适的方法后再更新群集中的密钥 ID 详细信息。
- 群集更新不应在同一个操作中同时包含标识和密钥标识符详细信息。 如果需要对两者进行更新,则更新应为两个连续操作。
- 如果仅启用或更改 CMK,请使用 REST API 而不是 CLI。 即使命令中不使用该属性,群集更新 CLI 也会向容量发送更新,从而触发 30 天更改或最低 500GB 的阈值。
使用密钥标识符详细信息在群集中更新 KeyVaultProperties。
该操作是异步操作,可能需要一段时间才能完成。
将工作区链接到群集
重要
此步骤应仅在群集配置之后执行。 如果在预配之前链接工作区和引入数据,则会删除引入的数据,并且无法恢复。
请遵循“专用群集”一文中说明的过程。
取消工作区与群集的链接
请遵循“专用群集”一文中说明的过程。
密钥吊销
重要
- 撤销对数据的访问权限的建议方法是禁用密钥或删除 Key Vault 中的访问策略。
- 如果将群集的
identitytype设置为None,还可撤销数据访问权,但不建议使用此方法,因为如果不联系支持人员就无法将其还原。
群集的存储在一小时或更短时间内始终认可密钥权限的更改,存储会变得不可用。 引入到链接工作区的新数据将被删除且不可恢复。 这些工作空间上的数据无法访问,并且查询失败。 只要不删除群集和工作区,之前引入的数据就会保留在存储中。 数据保留策略控制无法访问的数据,并在达到保留期时将其清除。 过去 14 天内引入的数据和最近在查询中使用的数据也保存在热缓存(受 SSD 支持)中,以提高查询效率。 SSD 上的数据在密钥吊销作上被删除,并且无法访问。 群集存储尝试定期连接 Key Vault,以执行 wrap 和 unwrap 操作。 启用密钥并 unwrap 成功后,SSD 数据将从存储重新加载。 数据引入和查询功能将在 30 分钟内恢复。
密钥轮换
密钥轮换具有两种模式:
- 自动轮换 – 更新群集中的
"keyVaultProperties"属性并省略"keyVersion"属性,或将其设置为""。 存储会自动使用最新的密钥版本。 - 显式密钥版本更新 – 更新
"keyVaultProperties"属性并在"keyVersion"属性中更新密钥版本。 密钥轮换需要显式更新群集中的"keyVersion"属性。 有关详细信息,请参阅为群集更新密钥标识符详细信息。 如果在 Key Vault 中生成了新的密钥版本但未在群集中更新密钥,群集存储将继续使用之前的密钥。 如果在更新群集中的新密钥之前禁用或删除了旧密钥,则你将进入密钥吊销状态。
在密钥轮换操作期间和之后,你的所有数据仍然可以访问。 数据始终使用帐户加密密钥 (AEK) 加密,该密钥使用 Key Vault 中的新密钥加密密钥 (KEK) 版本进行加密。
适用于已保存查询和日志搜索警报的客户管理的密钥
Log Analytics 中使用的查询语言具有表达性,可以在查询语法或注释中包含敏感信息。 受严格法规和合规性要求约束的组织必须维护使用客户管理的密钥加密的此类信息。 使用 Azure Monitor,可以在链接到工作区时,在自己的存储帐户中存储已保存的查询、函数和日志搜索警报,这些警报使用密钥加密。
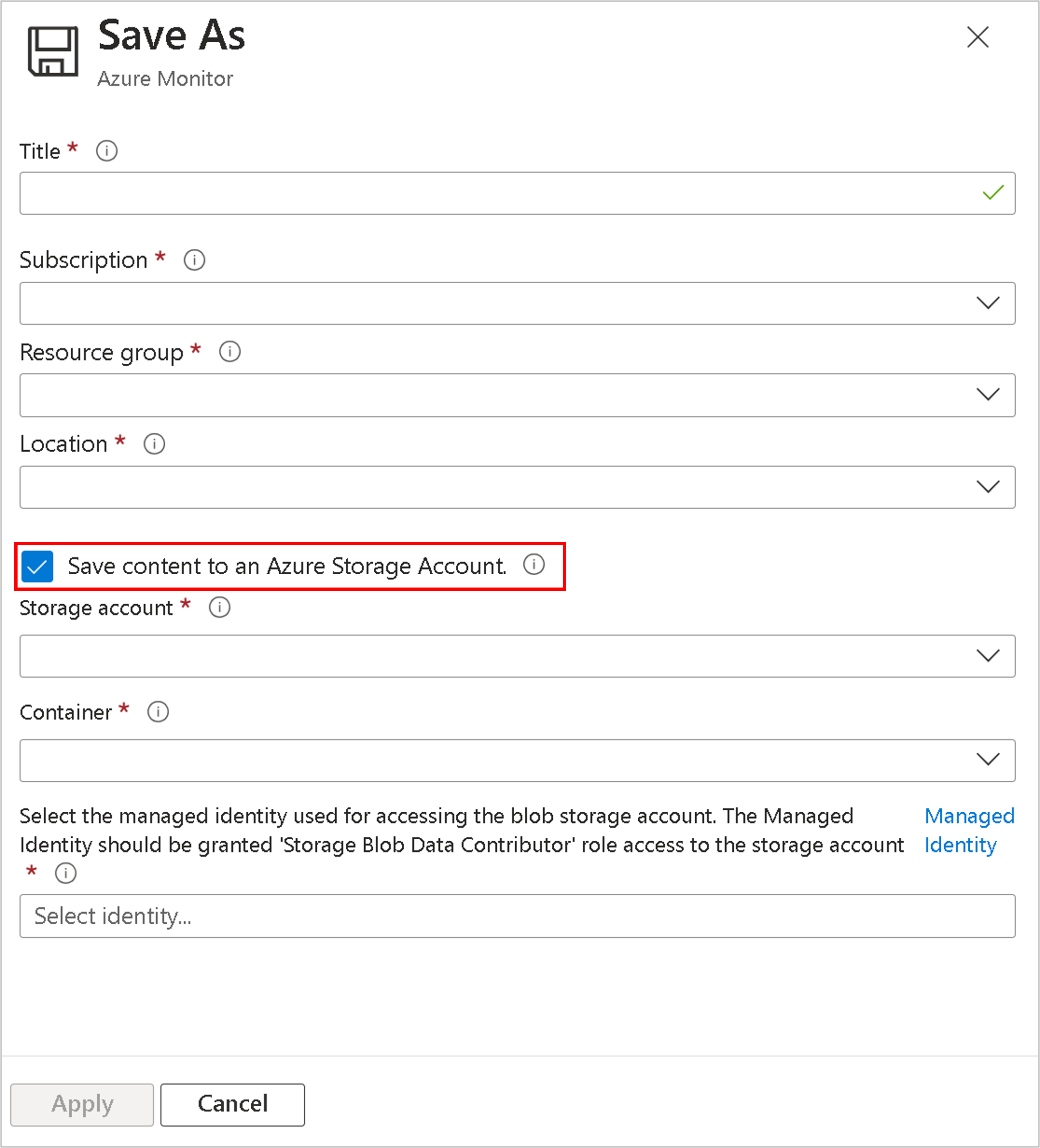
工作簿的客户管理的密钥
使用 Azure Monitor,可以在工作簿“保存”操作中选择“将内容保存到 Azure 存储帐户”时,将使用密钥加密的工作簿查询存储在自己的存储帐户中,但需留意所提及的有关用于已保存查询和日志搜索警报的客户管理的密钥的注意事项。
注意
无论客户管理的密钥配置如何,Azure 仪表板、Azure 逻辑应用、Azure Notebooks 和自动化运行手册中的查询仍使用 Microsoft 密钥(MMK)进行加密。
当链接到已保存查询的“存储帐户”后,服务会将已保存查询和日志搜索警报查询存储在存储帐户中。 掌握对存储帐户“encryption-at-rest 策略”的控制权后,可以使用客户管理的密钥来保护所保存的查询和日志搜索警报。 但需支付与该存储帐户相关的费用。
为保存的查询设置客户管理的密钥之前注意事项
- 需拥有对工作区和存储帐户的“写入”权限。
- 存储帐户必须是 StorageV2,并且与 Log Analytics 工作区位于同一区域中。
- 链接已保存查询的存储帐户时,将从工作区中删除现有已保存的查询和函数,以便隐私。 如果需要使用这些方便,请先复制现有保存的查询和函数,然后再进行配置。 可以使用 PowerShell 查看已保存的查询,也可以在工作区中的“自动化”下导出模板时查看。
- 保存在 查询包 中的查询不会存储在链接的存储帐户上,并且无法使用客户管理的密钥进行加密。 建议 保存为旧查询 ,以使用客户管理的密钥保护查询。
- 链接存储帐户中保存的查询和函数被视为服务项目,其格式可能会更改。
- 链接已保存查询的存储帐户时,不支持查询“历史记录”和“固定至仪表板”。
- 可以将保存的查询和日志搜索警报查询连接到单个或多个存储帐户。
- 若要使用密钥保持查询和功能加密,请使用客户管理的密钥配置链接的存储帐户。 此操作可以在创建存储帐户时完成,也可以稍后完成。
为保存的查询配置链接存储帐户
链接用于保存的查询和函数的存储帐户,以将保存的查询保留在存储帐户中。
注意
操作将保存的查询和函数从工作区转移到存储帐户中的一个表。 可以取消链接已保存查询的存储帐户,以便将保存的查询和函数移回工作区。 如果未保存的查询或函数在作后未显示在 Azure 门户中,请刷新浏览器。
完成配置后,所有新的已存搜索查询将保存在存储中。
为日志搜索警报查询配置链接存储帐户
为已保存日志警报查询设置客户管理的密钥之前注意事项
- 警报查询作为 Blob 保存在存储帐户中。
- 触发的日志搜索警报不包含搜索结果或警报查询。 使用 警报维度 获取触发警报的上下文。
- 若要使用密钥保持查询和功能加密,请使用客户管理的密钥配置链接的存储帐户。 此操作可以在创建存储帐户时完成,也可以稍后完成。
链接警报的存储帐户,以在你的存储帐户中保留日志搜索警报查询。
完成配置后,所有新的日志警报查询将保存在存储中。
客户管理的密钥的操作
客户管理的密钥在专用群集上提供,并且专用群集文章中引用了这些操作
- 获取资源组中的所有群集
- 获取订阅中的所有群集
- 更新群集中的容量预留
- 更新群集中的 billingType
- 从群集中取消与工作区的链接
- 删除群集
限制和约束
每个区域和订阅中最多可以创建两个活动群集。
每个区域和订阅中最多可以存在 7 个保留群集(活动或最近删除的群集)。
最多可以将 1,000 个 Log Analytics 工作区链接到一个群集。
在 30 天内最多允许对特定工作区进行两次工作区链接操作。
当前不支持将群集移到另一个资源组或订阅。
群集更新不应在同一操作中同时包含标识和密钥标识符详细信息。 如果两者都需要更新,则应在两次连续操作中进行更新。
当前不能在中国使用密码箱。
对于受支持区域中自 2020 年 10 月开始创建的群集,系统会自动为其配置双重加密。 可以通过在群集上发送
GET请求,并观察对于启用了双重加密的群集,isDoubleEncryptionEnabled的值是否为true,来验证群集是否配置了双重加密。- 如果创建群集并收到错误—“区域名称不支持群集双重加密”,则仍可以通过在 REST 请求正文中添加
"properties": {"isDoubleEncryptionEnabled": false}来创建没有双重加密的群集。 - 创建群集后,无法再更改双重加密设置。
- 如果创建群集并收到错误—“区域名称不支持群集双重加密”,则仍可以通过在 REST 请求正文中添加
客户管理的密钥的加密应用于在配置后新引入的数据。 在配置前引入的数据仍将使用 Microsoft 密钥进行加密。 你可以无缝查询在配置客户管理的密钥前后引入的数据。
Azure Key Vault 必须配置为可恢复。 默认情况下,这些属性不会启用,并且应使用 CLI 或 PowerShell 对其进行配置:
Azure Key Vault、群集和工作区必须位于同一区域和同一 Microsoft Entra 租户,但可以位于不同订阅。
如果将群集的
identitytype设置为None,还可撤销数据访问权,但不建议使用此方法,因为如果不联系支持人员就无法将其还原。 建议通过密钥吊销来撤销对你的数据的访问权限。如果 Key Vault 位于 Private-Link(虚拟网络),则不能将客户管理的密钥与用户分配的托管标识一起使用。 在此应用场景中,使用系统分配的托管标识。
故障排除
依据 Key Vault 可用性的行为:
在正常操作中,存储会缓存 AEK 一小段时间,并返回密钥保管库定期进行
unwrap。Key Vault 连接错误——存储能够应对暂时性错误(超时、连接失败、DNS 问题),允许密钥在可用性问题期间保留在缓存中,并克服间歇性故障和可用性问题。 查询和引入功能将继续运行而不会中断。
Key Vault 访问速率 - 群集存储访问 Key Vault 的频率对于
wrap和unwrap操作而言,间隔在 6 到 60 秒之间。如果在群集处于预配状态或更新状态时更新群集,则更新会失败。
如果在创建群集时遇到冲突错误,则可能是因为在过去14天内删除了具有相同名称的群集,并且该名称已被保留。 删除后的群集名称在删除后 14 天内可用。
如果工作区已链接到另一个群集,则将工作区链接到群集将失败。
如果您创建群集并立即指定
KeyVaultProperties,操作可能会失败,直到将标识分配给群集并授予给 Key Vault。如果在 Key Vault 中更新现有群集时,
KeyVaultProperties和Get密钥访问策略缺失,操作将失败。如果无法部署群集,请验证 Azure Key Vault、群集和链接的工作区是否位于同一区域。 可以位于不同的订阅。
如果在 Key Vault 中轮换密钥,并且不会更新群集中的新密钥标识符详细信息,则群集会继续使用以前的密钥,并且数据将不可访问。 更新群集中的新密钥标识符详细信息以恢复数据引入和查询功能。 使用
''表示法更新密钥版本,以确保存储始终自动使用最新的密钥版本。部分操作较为耗时,可能需要一段时间才能完成,包括群集创建、群集密钥更新和群集删除。 可以通过向群集或工作区发送
GET请求并观察响应来检查作状态。 例如,未链接的工作区在clusterResourceId下没有features。错误消息
群集更新
- 400 - 群集处于正在删除状态。 正在执行异步操作。 群集必须完成其操作,才能执行任意更新操作。
- 400 - KeyVaultProperties 不为空,但格式错误。 请参阅密钥标识符更新。
- 400 - 无法验证 Key Vault 中的密钥。 可能是由于权限不足或密钥不存在。 验证是否在 Key Vault 中设置密钥和访问策略。
- 400 - 密钥不可恢复。 Key Vault 必须设置为“软删除”和“清除保护”。 请参阅 Key Vault 文档
- 400 - 现在无法执行操作。 等待异步操作完成,然后重试。
- 400 - 群集处于正在删除状态。 等待异步操作完成,然后重试。
群集获取
- 404 - 找不到群集,群集可能已被删除。 如果尝试使用该名称创建群集但发生冲突,则该群集正处于删除过程中。