Microsoft Azure 提供了许多工具,可以使用它们根据你公司的安全性和合规性需求来保护数据。 本文重点介绍:
- 在 Microsoft Azure 中如何保护静态数据。
- 参与数据保护实现的各种组件。
- 不同密钥管理保护方法的利弊。
静态加密是常见的安全要求。 在 Azure 中,默认情况下,使用平台管理的密钥对静态数据进行加密。 此方法为组织提供自动加密,无需自定义密钥管理解决方案的风险或成本。 企业可以依靠 Azure 使用平台管理的密钥来完全管理存储加密,或者在需要对加密密钥和密钥管理策略进行额外控制时,使用客户管理的密钥。
什么是静态加密?
加密是用于保护数据的机密性的数据的安全编码。 Azure 中的静态加密设计使用对称加密来根据简单的概念模型快速加密和解密大量数据:
- 对称加密密钥在将数据写入存储时对数据进行加密。
- 同一加密密钥用于解密准备在内存中使用的数据。
- 可以对数据进行分区,并为每个分区使用不同的键。
- 必须将密钥存储在实施了基于标识的访问控制和审核策略的安全位置。 如果数据加密密钥存储在安全位置之外,则使用保存在安全位置的密钥加密密钥对其进行加密。
在实践中,密钥管理和控制方案以及规模和可用性保证都需要其他构造。 以下部分介绍了Microsoft Azure 静态加密的概念和组件。
静态加密的目的
静态加密可保护存储的数据(静态)。 针对静态数据的攻击包括尝试获取对存储数据的硬件的物理访问,然后泄露包含的数据。 在此类攻击中,服务器硬盘可能在维护期间被错误处理,这允许攻击者删除硬盘驱动器。 攻击者随后将硬盘驱动器置于其控制之下的计算机,以尝试访问数据。
静态加密旨在防止攻击者访问未加密的数据,其方法是确保这些数据在磁盘上时是加密的。 如果攻击者获取了包含加密数据的硬盘驱动器但未获取加密密钥,则攻击者必须破解加密才能读取数据。 这种攻击比访问硬盘驱动器上的未加密数据要复杂得多,且消耗的资源也多得多。 因此,强烈建议使用静态加密。对于许多组织来说,这是需要完成的高优先级事项。
组织对数据管理和合规性工作的需求可能还需要静态加密。 行业和政府法规(如 HIPAA、PCI 和 FedRAMP)针对数据保护和加密要求制定具体的保护措施。 要符合这其中的许多法规,静态加密是一种必需的强制措施。 有关 Microsoft 的 FIPS 140-2 验证方法的详细信息,请参阅美国联邦信息处理标准 (FIPS) 出版物 140-2。
除了满足合规要求以外,静态加密还能提供深层防御保护。 Microsoft Azure 为服务、应用程序和数据提供合规的平台。 此外,它还提供综合性的设施和物理安全性、数据访问控制和审核。 但是,如果其他一项安全措施失败,请务必提供额外的“重叠”安全措施。 静态加密提供此类安全措施。
Microsoft 致力于提供跨云服务的静态加密选项,可让客户控制加密密钥和密钥使用日志。 另外,Microsoft 正在努力实现默认加密所有客户静态数据。
密钥管理选项
Azure 提供了两种管理加密密钥的主要方法:
平台管理的密钥(默认)( 有时也称为服务管理的密钥):Azure 会自动处理加密密钥管理的各个方面,包括密钥生成、存储、轮换和备份。 此方法为静态加密提供客户所需的零配置,并且默认在 Azure 服务中启用。 平台管理的密钥提供最高级别的便利性,无需额外的成本或管理开销。
客户管理的密钥(可选):需要更好地控制其加密密钥的客户可以选择使用 Azure Key Vault 或 Azure 托管 HSM 管理自己的密钥。 此方法允许客户控制密钥生命周期、访问策略和加密作。 客户管理的密钥以增加管理责任和复杂性为代价提供额外的控制。
这些方法之间的选择取决于组织的安全要求、合规性需求和作首选项。 大多数组织都可以依赖平台管理的密钥进行可靠的加密保护,而具有特定法规或安全要求的组织可能会选择客户管理的密钥。
Azure 静态加密组件
如前所述,静态加密的目标是使用机密加密密钥对磁盘上保存的数据进行加密。 要实现该目标,必须为加密密钥提供安全的密钥创建、存储、访问控制和管理措施。 尽管详细信息可能有所不同,但 Azure 服务静态加密实现可按下图中的说明进行说明。
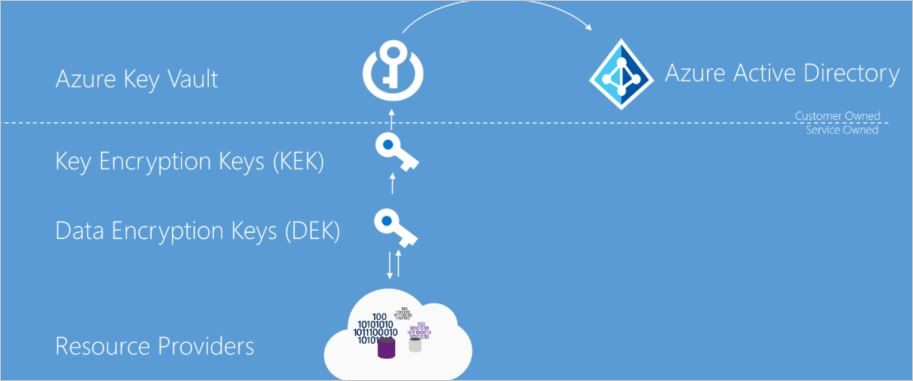
Azure Key Vault
对于静态加密模型来说,最重要的是加密密钥的存储位置以及对这些密钥的访问控制。 你需要高度保护密钥,但使它们可由指定用户管理,并可供特定服务使用。 对于 Azure 服务,建议使用 Azure Key Vault 作为密钥存储解决方案,它可以跨服务提供通常的管理体验。 可以在密钥保管库中存储和管理密钥,并为用户提供或服务对密钥保管库的访问权限。 Azure Key Vault 支持客户创建密钥,也支持将导入的客户密钥用于客户管理的加密密钥方案。
Microsoft Entra ID
可以授予 Microsoft Entra 帐户权限,以使用 Azure Key Vault 中存储的密钥来管理或访问它们进行静态加密和解密。
使用密钥层次结构进行信封加密
在静态加密实现中使用多个加密密钥。 将加密密钥存储在 Azure Key Vault 中可确保安全的密钥访问并可集中管理密钥。 但是,就批量加密和解密来说,通过服务在本地访问加密密钥比每项数据操作都要与 Key Vault 交互更为高效,可以提高加密强度和性能。 限制使用单个加密密钥可降低密钥泄露的风险,以及必须替换密钥时重新加密的成本。 Azure 静态加密模型使用信封加密,其中密钥加密密钥加密数据加密密钥。 此模型构成一个密钥层次结构,该层次结构可以更好地满足性能和安全要求:
- 数据加密密钥 (DEK) – 用于加密数据分区或数据块的对称 AES256 密钥,有时也简称为“数据密钥”。 单个资源可以有多个分区和多个数据加密密钥。 使用不同的密钥加密每个数据块可以增加加密分析攻击的难度。 将 DEK 保持在加密和解密数据的服务本地,可最大程度提高性能。
- 密钥加密密钥 (KEK) - 用于使用信封加密来加密数据加密密钥的加密密钥,也称为包装。 通过使用永不离开 Key Vault 的密钥加密密钥,可以加密和控制数据加密密钥。 有权访问 KEK 的实体可以不同于需要 DEK 的实体。 实体可以代理对 DEK 的访问,以限制每个 DEK 对特定分区的访问。 由于需要 KEK 来解密 DEK,因此客户可以通过禁用 KEK 来加密擦除 DEK 和数据。
资源提供程序和应用程序实例将加密的数据加密密钥存储为元数据。 只有有权访问密钥加密密钥的实体才能解密这些数据加密密钥。 支持各种不同的密钥存储模型。 有关详细信息,请参阅数据加密模型。
Azure 云服务中的静态加密
在所有三个云模型中都使用Microsoft云服务:IaaS、PaaS 和 SaaS。 以下示例演示了它们如何适应每个模型:
- 软件服务,也称软件即服务(简称 SaaS),它包含云提供的应用程序,例如 Microsoft 365。
- 平台服务,方便客户在其应用程序中将云用于存储、分析和服务总线功能等。
- 基础结构服务,也称基础结构即服务 (IaaS),方便客户部署托管在云中的操作系统和应用程序,并尽可能利用其他云服务。
适合 SaaS 客户的静态加密
软件即服务 (SaaS) 客户通常会在每个服务中启用或提供静态加密。 Microsoft 365 为客户提供多个选项来验证或启用静态加密。 若要了解 Microsoft 365 服务,请参阅 Microsoft 365 中的加密。
适合 PaaS 客户的静态加密
平台即服务(PaaS)客户通常将其数据存储在 Blob 存储等存储服务中。 但是,数据也可能缓存或存储在应用程序执行环境中,例如虚拟机。 若要查看适用的静态加密选项,请检查数据加密模型,确认是否存在所用的存储和应用程序平台。
适合 IaaS 客户的静态加密
基础结构即服务(IaaS)客户可以使用各种服务和应用程序。 IaaS 服务可以使用主机加密在其 Azure 托管的虚拟机中启用静态加密。
加密的存储
与 PaaS 一样,IaaS 解决方案可以利用其他存储静态加密数据的 Azure 服务。 在这些情况下,可以启用由每个已使用的 Azure 服务提供的静态数据加密支持。 数据加密模型枚举支持的主要存储、服务和应用程序平台以及静态加密模型。
加密的计算
默认情况下,所有托管磁盘、快照和映像都使用存储服务加密和平台管理的密钥进行加密。 此默认加密不需要客户配置或额外费用。 更全面的加密解决方案可确保所有数据永远不会以未加密的形式持久保存。 处理虚拟机上的数据时,系统可以将数据保存到 Windows 页面文件或 Linux 交换文件、故障转储或应用程序日志。 为了确保静态加密此数据,IaaS 应用程序可以在 Azure IaaS 虚拟机的主机上使用加密,该虚拟机默认使用平台管理的密钥,但可以选择使用客户管理的密钥进行配置,以便进行其他控制。
自定义静态加密
尽可能,IaaS 应用程序应利用所用 Azure 服务提供的主机加密和静态数据加密选项。 在某些情况下,例如不规则的加密要求或非 Azure 基于的存储,IaaS(基础设施即服务)应用程序的开发人员可能需要自行实现静态数据加密。 IaaS 解决方案开发人员可以利用某些 Azure 组件,改进与 Azure 管理的集成并更好地满足客户期望。 具体而言,开发人员应使用 Azure Key Vault 服务提供安全密钥存储,并为客户提供与 Azure 平台服务一致的密钥管理选项。 另外,自定义解决方案应通过 Azure 托管服务标识来允许服务帐户访问加密密钥。 有关 Azure Key Vault 和托管服务标识的开发人员信息,请参阅各自的 SDK。
Azure 资源提供程序加密模型支持
每个 Microsoft Azure 服务都支持一个或多个静态加密模型。 但是,对于某些服务,一个或多个加密模型可能不适用。 对于支持客户管理的密钥方案的服务,他们可能仅支持 Azure Key Vault 支持密钥加密密钥的一部分密钥类型。 此外,服务可能会按不同的计划发布对这些方案和关键类型的支持。 此部分介绍的静态加密支持在撰写本文时仍适用于每个主要的 Azure 数据存储服务。
Azure VM 磁盘加密
任何使用 Azure 基础结构即服务(IaaS)功能的客户都可以通过主机上的加密来加密其 IaaS VM 磁盘。 有关详细信息,请参阅 主机加密 - VM 的端到端加密。
Azure 存储
所有 Azure 存储服务(Blob 存储、队列存储、表存储和 Azure 文件存储)都支持服务器端静态加密,某些服务还支持客户端加密。
- 服务器端(默认):默认情况下,所有 Azure 存储服务都使用平台管理的密钥自动启用服务器端加密。 此加密对应用程序是透明的,无需配置。 有关详细信息,请参阅静态数据的 Azure 存储服务加密。 客户可以选择使用 Azure Key Vault 中的客户管理的密钥进行其他控制。 有关详细信息,请参阅 Azure Key Vault 中使用客户托管密钥的存储服务加密。
- 客户端(可选):Azure Blob、表和队列支持客户端加密,以便需要先加密数据才能到达 Azure 的客户。 使用客户端加密时,客户会加密数据并将数据作为加密的 blob 上传。 密钥管理由客户执行。 有关详细信息,请参阅 Client-Side Microsoft Azure 存储的加密和 Azure 密钥保管库。
Azure SQL 数据库
Azure SQL 数据库目前支持平台托管服务端和客户端加密方案的静态加密。
对服务器加密的支持目前通过名为“透明数据加密”的 SQL 功能来提供。 在 Azure SQL 数据库客户启用 TDE 后,系统会自动为其创建和管理密钥。 可以在数据库和服务器级别启用静态加密。 从 2017 年 6 月开始,会在新创建的数据库上默认启用透明数据加密 (TDE)。 Azure SQL 数据库支持 Azure Key Vault 中客户管理的 RSA 2048 位密钥。 有关详细信息,请参阅使用 Azure SQL 数据库和数据仓库的“创建自己的密钥”支持进行透明数据加密。
可以通过 Always Encrypted 功能启用对 Azure SQL 数据库数据的客户端加密。 Always Encrypted 使用客户端创建和存储的密钥。 客户可以将主密钥存储在 Windows 证书存储、Azure Key Vault 或本地硬件安全模块中。 使用 SQL Server Management Studio 时,SQL 用户可以选择想要使用什么密钥来加密哪个列。
结论
保护存储在 Azure 服务中的客户数据对于 Microsoft 来说至关重要。 所有 Azure 托管服务都致力于提供静态加密选项。 Azure 服务支持平台管理的密钥、客户管理的密钥或客户端加密。 Azure 服务正在广泛增强静态加密可用性,并计划未来几个月推出预览版和正式版的新选项。