适用于:Azure SQL 数据库
Azure SQL 托管实例
Azure Synapse Analytics
本文介绍如何将 Microsoft Entra ID 身份验证与 Azure SQL 数据库、Azure SQL 托管实例和 Azure Synapse Analytics 结合使用。
注意
Microsoft Entra ID 以前称为 Azure Active Directory (Azure AD)。
或者,还可以为 Azure 虚拟机 上的 SQL Server 配置 Microsoft Entra 身份验证。
先决条件
要将 Microsoft Entra 身份验证与 Azure SQL 资源结合使用,需要满足以下先决条件:
- Microsoft Entra 租户已填充用户和组。
- 现有的 Azure SQL 资源,例如 Azure SQL 数据库或 Azure SQL 托管实例。
创建并填充 Microsoft Entra 租户
在为 Azure SQL 资源配置 Microsoft Entra 身份验证之前,需要创建 Microsoft Entra 租户,并将其填充用户和组。 Microsoft Entra 租户可以完全在 Azure 中托管,或者用于本地 Active Directory 域服务的联合。
有关详细信息,请参阅:
- 什么是 Microsoft Entra ID?
- 将本地标识与 Microsoft Entra ID 集成
- 在 Microsoft Entra ID 中添加自己的域名
- 什么是与 Microsoft Entra ID 的联合?
- 与 Microsoft Entra ID 目录同步
- 使用 Windows PowerShell 管理 Microsoft Entra ID
- 混合标识所需的端口和协议
设置 Microsoft Entra 管理员
要将 Microsoft Entra 身份验证与资源结合使用,需要设置 Microsoft Entra 管理员。 虽然从概念上讲,Azure SQL 数据库、Azure Synapse Analytics 和 Azure SQL 托管实例的步骤是相同,但本部分详细介绍了每个产品要执行的不同 API 和门户体验。
创建 Azure SQL 资源时也可以配置 Microsoft Entra 管理员。 如果已配置 Microsoft Entra 管理员,请跳过本部分。
Azure SQL 数据库和 Azure Synapse Analytics
设置 Microsoft Entra 管理员可为 Azure SQL 数据库和 Azure Synapse Analytics 的 逻辑服务器 启用 Microsoft Entra 身份验证。 可以使用 Azure 门户、PowerShell、Azure CLI 或 REST API 为服务器设置 Microsoft Entra 管理员。
在 Azure 门户中,可以找到该逻辑服务器名称
- 在 Azure SQL 数据库“概述”页面上的“服务器名称”字段中。
- 在 Azure Synapse Analytics 中独立专用 SQL 池“概述”页面上的“服务器名称”字段中。
- 在 Azure Synapse Analytics 工作区“概述”页面上的相关“SQL 终结点”中。
要在 Azure 门户中为逻辑服务器设置 Microsoft Entra 管理员,请执行以下步骤:
在 Azure 门户“目录 + 订阅”窗格中,选择包含 Azure SQL 资源的目录作为“当前目录”。
搜索“SQL 服务器”,然后选择数据库资源的逻辑服务器以打开“SQL Server”窗格。
在逻辑服务器的“SQL Server”窗格中,选择“设置”下的“Microsoft Entra ID”,以打开“Microsoft Entra ID”窗格。
在“Microsoft Entra ID”窗格中,选择“设置管理员”以打开“Microsoft Entra ID”窗格。
“Microsoft Entra ID”窗格显示当前目录中的所有用户、组和应用程序,并允许按名称、别名或 ID 进行搜索。 找到您所需的 Microsoft Entra 管理员身份,选择它,然后选择“选择”以关闭窗格。
在逻辑服务器的“Microsoft Entra ID”页面顶部,选择“保存”。
对于 Microsoft Entra 用户和组,“对象 ID”显示在管理员名称旁。 对于应用程序(服务主体),将显示应用程序 ID。
更改管理员的过程可能需要几分钟时间。 然后,新管理员出现在“Microsoft Entra 管理员”字段中。
要删除管理员,请在“Microsoft Entra ID”页面顶部,选择“移除管理员”,然后选择“保存”。 移除 Microsoft Entra 管理员会禁用逻辑服务器的 Microsoft Entra 身份验证。
注意
Microsoft Entra 管理员以用户(数据库主体)的形式存储在服务器的 master 数据库中。 由于数据库主体名称必须唯一,因此管理员的显示名称不能与服务器 master 数据库中任何用户的名称相同。 如果已有该名称的用户,则 Microsoft Entra 管理员设置将失败并回退,指示该名称已被占用。
Azure SQL 托管实例
设置 Microsoft Entra 管理员可为 Azure SQL 托管实例启用 Microsoft Entra 身份验证。 可以使用 Azure 门户、PowerShell、Azure CLI 或 REST API 为 SQL 托管实例设置 Microsoft Entra 管理员。
要使用 Azure 门户授予 SQL 托管实例 Microsoft Entra ID 的读取权限,请以特权角色管理员身份登录,然后执行以下步骤:
在 Azure 门户中的右上角选择帐户,然后选择“切换目录”以确认哪个目录是当前目录。 如有必要,请切换目录。
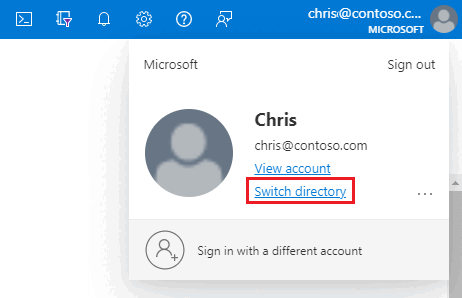
在 Azure 门户“目录 + 订阅”窗格中,选择包含托管实例的目录作为“当前目录”。
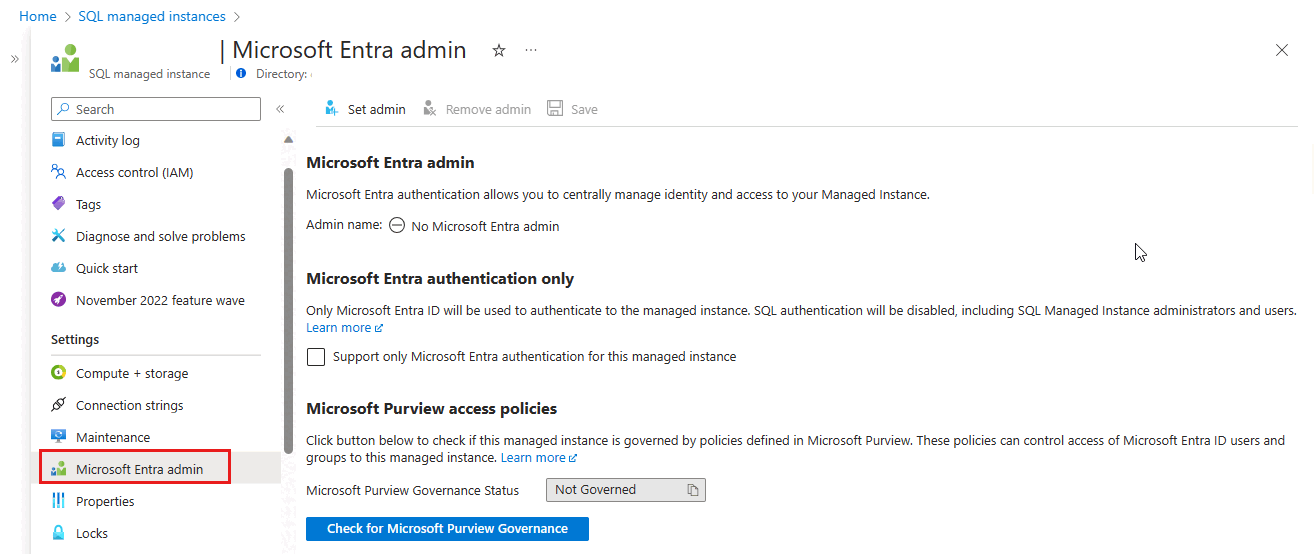
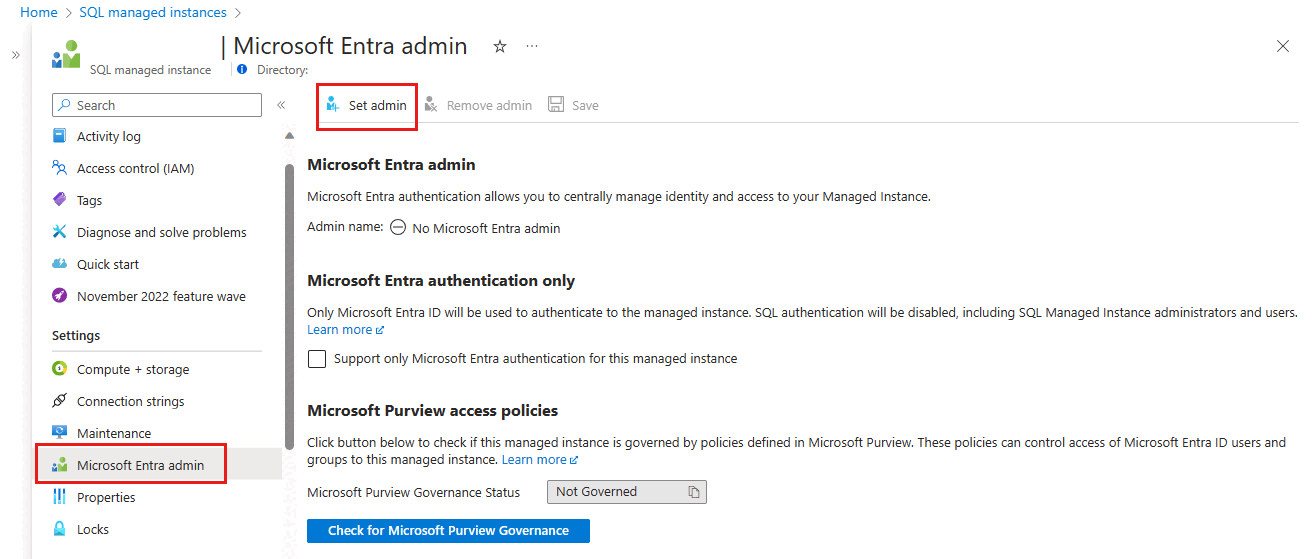
搜索“SQL 托管实例”,然后选择托管实例 以打开“SQL 托管实例”窗格。 然后,在“设置”下选择“Microsoft Entra ID”,打开实例的“Microsoft Entra ID”窗格。
在“Microsoft Entra 管理员”窗格中,从导航栏中选择“设置管理员”以打开“Microsoft Entra ID”窗格。
在“Microsoft Entra ID”窗格中,搜索用户,选中要成为管理员的用户或组旁边的框,按下“选择”以关闭窗格,然后返回到托管实例的“Microsoft Entra 管理员”页面。
“Microsoft Entra ID”窗格显示当前目录中的所有成员和组。 不能选择灰显的用户或组,因为其无法充当 Microsoft Entra 管理员。 选择要以管理员身份分配的标识。
在托管实例的“Microsoft Entra 管理员”页面的导航栏中,选择“保存”以确认 Microsoft Entra 管理员。
管理员更改操作完成后,新管理员将在 Microsoft Entra 管理员字段中显示。
对于 Microsoft Entra 用户和组,“对象 ID”显示在管理员名称旁。 对于应用程序(服务主体),将显示应用程序 ID。
提示
要删除管理员,请在“Microsoft Entra ID”页面顶部,选择“移除管理员”,然后选择“保存”。
分配 Microsoft Graph 权限
SQL 托管实例需要权限来读取 Microsoft Entra ID,用于授权通过安全组成员身份连接的用户和新用户创建等应用场景。 要使 Microsoft Entra 身份验证正常工作,需要将托管实例标识分配给“目录读取者”角色。 可以使用 Azure 门户或 PowerShell 执行此操作。
对于某些操作,Azure SQL 数据库和 Azure Synapse Analytics 还需要有权查询 Microsoft Graph,如 Microsoft Graph 权限中所述。 Azure SQL 数据库和 Azure Synapse Analytics 支持这些应用场景的精细 Graph 权限,而 SQL 托管实例需要“目录读取者”角色。 启用服务主体创建 Microsoft Entra 用户中详细描述了细化权限及其分配。
目录读取者角色
Azure 门户中 SQL 托管实例的“Microsoft Entra ID”页在实例未分配目录读取者权限时显示方便的横幅。
选择“Microsoft Entra ID”页顶部的横幅,并向代表实例的系统分配或用户分配的托管标识授予权限。 只有租户中的特权角色管理员或更高角色可以执行此操作。
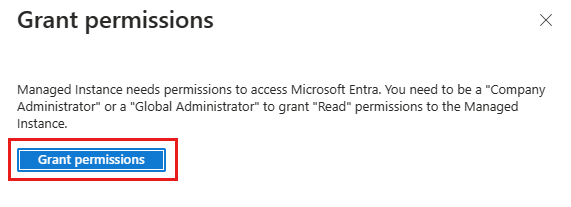
操作成功后,右上角会显示“成功”通知:
Microsoft Entra 管理员现在可用于创建 Microsoft Entra 服务器主体(登录名)和数据库主体(用户)。 有关更多信息,请参阅 Microsoft Entra 与 Azure SQL 托管实例 集成。
在 SQL 中创建 Microsoft Entra 主体
要使用 Microsoft Entra 身份验证连接到 SQL 数据库 或 Azure Synapse Analytics 中的数据库,必须在数据库中为具有至少 CONNECT 权限的标识配置主体。
数据库用户权限
创建数据库用户时,它默认会收到 CONNECT 对数据库的权限。 数据库用户还会在两种情况下继承权限:
- 如果用户是 Microsoft Entra 组的成员,则该组也被分配了服务器权限。
- 如果用户是从登录名创建的,它将继承适用于数据库登录的服务器分配权限。
无论主体类型如何(Microsoft Entra ID、SQL 身份验证等),服务器和数据库主体的管理权限都相同。 建议向数据库角色授予权限,而不是直接向用户授予权限。 然后,可以将用户添加到具有适当权限的角色。 这简化了长期权限管理,并减少了标识在适当情况下保留访问的可能性。
有关详细信息,请参阅:
包含的数据库用户
包含的数据库用户是一种未连接到 master 数据库中登录名的 SQL 用户。 若要创建 Microsoft Entra 受限数据库用户,请使用具有至少 ALTER ANY USER** 权限的 Microsoft Entra 标识连接到数据库。 以下 T-SQL 示例从 Microsoft Entra ID 创建数据库主体 Microsoft_Entra_principal_name。
CREATE USER [<Microsoft_Entra_principal_name>] FROM EXTERNAL PROVIDER;
要为 Microsoft Entra 组创建包含的数据库用户,请提供该组的显示名称:
CREATE USER [ICU Nurses] FROM EXTERNAL PROVIDER;
要为托管标识或服务主体创建包含的数据库用户,请输入该标识的显示名称:
CREATE USER [appName] FROM EXTERNAL PROVIDER;
要为 Microsoft Entra 用户创建包含的数据库用户,请输入该标识的用户主体名称:
CREATE USER [adrian@contoso.com] FROM EXTERNAL PROVIDER;
基于登录名的用户
注意
对于 Azure SQL 数据库和 Azure Synapse Analytics,Microsoft Entra 服务器主体(登录名)当前为公共预览版。 Microsoft Entra 登录名通常可用于 Azure SQL 托管实例和 SQL Server 2022。
Microsoft Entra 服务器主体(或登录名)受支持,这意味着不需要包含的数据库用户。 数据库主体(用户)可以基于服务器主体创建,这意味着 Microsoft Entra 用户可以继承登录名的服务器级分配权限。
CREATE USER [appName] FROM LOGIN [appName];
有关详细信息,请参阅 SQL 托管实例概述。 有关创建 Microsoft Entra 服务器主体(登录名)的语法,请参阅 CREATE LOGIN。
外部用户
无法直接为在与 Azure 订阅关联的不同 Microsoft Entra 租户中托管的标识创建数据库用户。 但是,可以将其他目录中的用户作为外部用户导入到关联的目录中。 然后,可以使用其创建可访问数据库的包含的数据库用户。 外部用户还可以通过 Microsoft Entra 组中的成员身份获得访问权限。
示例:创建代表 Microsoft Entra 联合或托管域用户的包含的数据库用户:
CREATE USER [alice@fabrikam.com] FROM EXTERNAL PROVIDER;
如果将联合域用户帐户作为外部用户导入到托管域,则此用户必须使用托管域标识。
名称考虑事项
不支持在 T-SQL 和语句中作为用户名包含特殊字符,例如冒号 : 或与号 &。
Microsoft Entra ID 和 Azure SQL 在用户管理设计上有一个关键区别:Microsoft Entra ID 允许在租户内有重复的显示名称,而 Azure SQL 要求服务器或实例上的所有服务器主体以及数据库中的所有数据库主体具有唯一名称。 由于 Azure SQL 在创建主体时直接使用标识的 Microsoft Entra 显示名称,因此在创建用户时可能会导致错误。 为了解决此问题,Azure SQL 已发布 WITH OBJECT_ID 当前预览版中的增强功能,允许用户指定要添加到服务器或实例的标识的 Microsoft Entra 对象 ID。
Microsoft Graph 权限
CREATE USER ... FROM EXTERNAL PROVIDER 命令要求 Azure SQL 代表已登录用户访问 Microsoft Entra ID(“外部提供程序”)。 有时候,会出现导致 Microsoft Entra ID 将异常返回给 Azure SQL 的情况。
- 你可能会遇到 SQL 错误 33134,其中包含 Microsoft Entra ID 特定的错误消息。 错误通常会指出访问被拒绝、用户必须注册 MFA 才能访问资源,或者在第一方应用程序之间进行的访问必须通过预授权进行处理。 如果是前面的两种情况,则问题通常是由在用户的 Microsoft Entra 租户中设置的条件访问策略引起的:这些策略阻止用户访问外部提供程序。 更新条件访问策略以允许访问应用程序“00000003-0000-0000-c000-000000000000”(Microsoft Graph API 的应用程序 ID)应该就能解决此问题。 如果错误指出在第一方应用程序之间进行的访问必须通过预授权进行处理,则出现问题是因为用户以服务主体的身份登录。 如果改由用户执行命令,则命名应该会成功。
- 如果收到 Connection Timeout Expired 消息,则可能需要将连接字符串的
TransparentNetworkIPResolution参数设置为 false。 有关详细信息,请参阅 .NET Framework 4.6.1 的连接超时问题 - TransparentNetworkIPResolution。
有关基于 Microsoft Entra 标识创建包含的数据库用户的详细信息,请参阅 CREATE USER。
配置多重身份验证
为了提高 Azure SQL 资源的安全性,请考虑配置多重身份验证 (MFA),这会提示用户使用第二种替代方法(例如电话呼叫或验证器应用)向数据库进行身份验证。
若要对 Azure SQL 资源使用多重身份验证,请先 启用多重身份验证,然后使用 条件访问策略 为 Azure SQL 资源强制实施 MFA。
使用 Microsoft Entra 进行连接
配置 Microsoft Entra 身份验证后,可以使用该功能通过 SQL Server Management Studio 和 SQL Server Data Tools 等 Microsoft 工具连接到 SQL 资源,并配置客户端应用程序以使用 Microsoft Entra 标识进行连接。
Microsoft Entra 身份验证故障排除
有关故障排除指导,请参阅博客:使用 Azure SQL 数据库和 Azure Synapse 解决与 Microsoft Entra 身份验证相关的问题。