适用于:Azure SQL 数据库
Azure SQL 托管实例
Azure Synapse Analytics
本文概述了如何结合使用 Microsoft Entra 身份验证与 Azure SQL 数据库、Azure SQL 托管实例、Azure VM 上的 SQL Server、Azure Synapse Analytics 中的 Synapse SQL和适用于 Windows 和 Linux 的 SQL Server。
如果要配置 Microsoft Entra 身份验证,请查看:
注意
Microsoft Entra ID 以前称为 Azure Active Directory (Azure AD)。
概述
使用 Microsoft Entra ID,你可以集中管理数据资产中人和服务的标识。 通过将 Microsoft Entra 与 Azure SQL 集成进行身份验证,可以简化标识和权限管理,同时针对与数据的所有连接启用详细的条件访问和管理。
使用 Microsoft Entra 身份验证具有以下优势:
- 替换安全性较低的身份验证方法,如用户名和密码。
- 消除或帮助阻止用户身份在服务器之间的扩散。
- Microsoft Entra 组使数据库权限管理能够从单个帐户和操作组中抽象出来。
- 允许在单一位置中轮换密码。
- Microsoft Entra 的身份验证完全可以替代 SQL 身份验证。
- Azure 资源的托管标识无需存储连接到数据库的服务的密码,也无需存储从数据库到其他 Azure 资源的连接的密码。
- 启用现代安全控制功能,包括强大的多重身份验证,并提供一系列简单的验证选项,例如来电、短信、带有密码的智能卡或移动应用通知。
- Microsoft Entra ID 可实现与许多新式身份验证协议的集成,包括 OpenID Connect、OAuth2.0、Kerberos 约束委派等。
- 支持集中监视与数据源的连接。
- 启用条件访问控制,例如需要合规的设备或身份验证方法才能成功连接。
- 使用 Azure 策略集中管理和监视身份验证。
注意
Microsoft Entra 身份验证仅支持源自 Microsoft Entra ID 的访问令牌,不支持第三方访问令牌。 Microsoft Entra ID 也不支持将 Microsoft Entra ID 查询重定向到第三方端点。 这适用于所有支持 Microsoft Entra 身份验证的 SQL 平台和所有操作系统。
配置步骤
配置 Microsoft Entra 身份验证的一般步骤包括:
- 创建并填充 Microsoft Entra 租户。
- 在 Azure 中创建逻辑服务器或实例。
- 将 Microsoft Entra 管理员分配到服务器或实例。
- 在数据库中创建映射到 Microsoft Entra 标识的 SQL 主体。
- 将客户端应用程序配置为使用 Azure 标识库和身份验证方法进行连接。
- 使用 Microsoft Entra 标识连接数据库。
支持的标识和身份验证方法
Azure SQL 支持将以下 Microsoft Entra 标识用作服务器和数据库中的登录名和用户(主体):
- Microsoft Entra 用户:Microsoft Entra 租户中任何类型的用户,包括内部用户、外部用户、来宾和成员。 还支持与 Microsoft Entra ID 联合的 Active Directory 域的成员。
- 应用程序:Azure 中存在的应用程序可以使用服务主体或托管标识直接向 Azure SQL 进行身份验证。 首选使用托管标识,因为身份验证是无密码的,并且不需要开发人员管理的凭证。
- Microsoft Entra 组可基于组织的组成员身份管理用户和应用程序访问权限,从而简化整个组织的访问管理。
对于用户标识,支持以下身份验证方法:
- Microsoft Entra 集成(Windows 身份验证)由 Microsoft Entra 混合标识与 Active Directory [联合身份验证] 提供支持。
- Microsoft Entra MFA 或多重身份验证,它需要除用户已知信息之外的额外安全检查。
- Microsoft Entra 密码身份验证,该身份验证使用在 Microsoft Entra ID 中存储和管理的用户凭证。
- Microsoft Entra 默认身份验证,该身份验证扫描应用程序计算机上的各种凭证缓存,并且可以使用用户令牌向 SQL 进行身份验证。
对于服务或工作负载标识,支持以下身份验证方法:
- Azure 资源的托管标识,包括用户分配和系统分配的托管标识。 托管标识身份验证是基于令牌的机制,在这种身份验证中,标识分配给需要使用该标识进行验证的资源。 Azure 标识平台会验证该关系,从而实现无密码身份验证。
- Microsoft Entra 服务主机名称和应用程序(客户端)密码。 不建议使用此身份验证方法,因为存在密码被猜测和泄露的风险。
- Microsoft Entra 默认身份验证,该身份验证扫描应用程序计算机上的各种凭证缓存,并且可以使用应用程序令牌向 SQL 进行身份验证。
Microsoft Entra 管理员
若要启用 Microsoft Entra 身份验证,必须为逻辑服务器或托管实例设置一位 Microsoft Entra 管理员。 此管理员与 SQL Server 管理员 (SA) 一起存在。 Microsoft Entra 管理员可以是 Azure 租户中的任何一个安全对象,包括 Microsoft Entra 用户、组、服务主体和托管标识。 Microsoft Entra 管理员是一个单一属性,而不是一个列表,这意味着在任何时候只能配置一个标识。 从服务器中删除 Microsoft Entra 管理员会禁用所有基于 Microsoft Entra 身份验证的连接,即使对于数据库中具有权限的现有 Microsoft Entra 用户也是如此。
提示
Microsoft Entra 群组使多个身份能够在服务器上充当 Microsoft Entra 管理员。 当管理员设置为组时,所有组成员都会继承 Microsoft Entra 管理员角色。 通过将管理员管理从服务器数据平面作转移到 Microsoft Entra ID 和组所有者手中,Microsoft Entra 组管理员提高了可管理性。 组可用于连接到 SQL 的所有 Microsoft Entra 标识,支持在服务器和数据库中进行一次性用户和权限配置,从而将所有用户管理工作交给组。
Microsoft Entra 管理员扮演着特殊角色:它是第一个帐户,可以创建其他 Microsoft Entra 登录名(在 SQL 数据库中处于预览状态)和用户,这些统称为主题。 管理员是服务器的 master 数据库中包含的数据库用户。 管理员帐户是每个用户数据库中 db_owner 角色的成员,并且以 dbo 用户身份输入每个用户数据库。 有关管理员帐户的详细信息,请参阅管理数据库和登录名。
Microsoft Entra 主体
注意
Microsoft Entra 服务器主体(登录名)目前在 Azure SQL 数据库和 Azure Synapse Analytics 中处于公共预览状态。 Microsoft Entra 登录名通常可用于 Azure SQL 托管实例和 SQL Server 2022。
Microsoft Entra 标识可以通过三种方式在 Azure SQL 中创建为主体:
- 作为服务器主体或登录名(在 Azure SQL 数据库中处于预览状态)
- 作为基于登录的用户(数据库主体类型)
- 作为包含的数据库用户
重要
Azure SQL 的 Microsoft Entra 身份验证不与 Azure RBAC 集成。 使用 Microsoft Entra 标识连接到 Azure SQL 并执行查询需要将这些标识创建为他们需要访问的数据库中的 Microsoft Entra 主体。 这些 SQL Server Contributor 和 SQL DB Contributor 角色用于保护与管理相关的部署操作,而不是数据库连接访问。
登录名(服务器主体)
Microsoft Entra 标识的服务器主体(登录名)通常用于 Azure VM 上的 Azure SQL 托管实例、SQL Server 2022 和 SQL Server。 Microsoft Entra 登录功能正在 Azure SQL 数据库中处于预览阶段。
以下 T-SQL 演示如何创建 Microsoft Entra 登录名:
CREATE LOGIN [MSEntraUser] FROM EXTERNAL PROVIDER
Microsoft Entra 登录名在 sys.server_principals 中具有以下属性值:
| 财产 | 价值 |
|---|---|
SID (安全标识符) |
Microsoft Entra 标识对象 ID 的二进制表示形式 |
| 类型 | E = Microsoft Entra ID 中的外部登录名或应用程序 X = 来自 Microsoft Entra ID 的外部组 |
| type_desc | Microsoft Entra 登录或应用的EXTERNAL_LOGIN Microsoft Entra 组的 EXTERNAL_GROUP |
基于登录的用户
基于登录的用户将继承分配给其 Microsoft Entra 登录名的服务器级角色和权限。 基于 Microsoft Entra 登录的用户在 Azure SQL 数据库中处于预览状态。
以下 T-SQL 演示如何为 Microsoft Entra 标识创建基于登录名的用户:
CREATE USER [MSEntraUser] FROM LOGIN [MSEntraUser]
下表详细介绍了 sys.database_principals 中基于 Microsoft Entra 登录名的用户属性值:
| 财产 | 价值 |
|---|---|
SID (安全标识符) |
Microsoft Entra 标识对象 ID 的二进制表示形式,以及“AADE” |
| 类型 | E = Microsoft Entra ID 中的外部登录名或应用程序 X = 来自 Microsoft Entra ID 的外部组 |
| type_desc | Microsoft Entra 登录或应用的EXTERNAL_LOGIN Microsoft Entra 组的 EXTERNAL_GROUP |
受限的数据库用户
包含的数据库用户可与数据库一起移植。 它们与服务器或实例中定义的标识没有连接,因此可以轻松地将它们与数据库一起从一个服务器或实例移动到另一个服务器或实例,而不会中断。
以下 T-SQL 演示如何为 Microsoft Entra 标识创建包含的数据库用户:
CREATE USER [MSEntraUser] FROM EXTERNAL PROVIDER
基于 Microsoft Entra 数据库的用户与 sys.database_principals 中基于登录名的用户具有相同的属性值,但 SID 的构造方式除外:
| 财产 | 价值 |
|---|---|
SID (安全标识符) |
Microsoft Entra 标识对象 ID 的二进制表示形式 |
| 类型 | E = Microsoft Entra ID 中的外部登录名或应用程序 X = 来自 Microsoft Entra ID 的外部组 |
| type_desc | Microsoft Entra 登录或应用的EXTERNAL_LOGIN Microsoft Entra 组的 EXTERNAL_GROUP |
若要获取 SID 所基于的原始 Microsoft Entra GUID,请使用以下 T-SQL 转换:
SELECT CAST(sid AS UNIQUEIDENTIFIER) AS EntraID FROM sys.database_principals
注意
在服务器或实例级别,可能会在无意中创建与 Microsoft Entra 登录名同名的包含型 Microsoft Entra 数据库用户。 由于主体没有相互连接,因此数据库用户不会从服务器登录名继承权限,并且标识可以在连接请求中合并,从而导致未定义的行为。
使用以下 T-SQL 查询来确定数据库用户是基于登录名的用户还是包含的数据库用户:
SELECT CASE
WHEN CONVERT(VARCHAR(100), sid, 2) LIKE '%AADE' AND len(sid) = 18 THEN 'login-based user'
ELSE 'contained database user'
END AS user_type,
*
FROM sys.database_principals WHERE TYPE = 'E' OR TYPE = 'X'
使用以下 T-SQL 查询查看数据库中的所有 Microsoft Entra 主体:
SELECT
name,
CAST(sid AS UNIQUEIDENTIFIER) AS EntraID,
CASE WHEN TYPE = 'E' THEN 'App/User' ELSE 'Group' AS user_type,
sid
FROM sys.database_principals WHERE TYPE = 'E' OR TYPE = 'X'
仅限 Microsoft Entra 的身份验证
启用仅限 Microsoft Entra 的身份验证后,所有其他身份验证方法将被禁用,并且不能用于连接到服务器、实例或数据库,包括 SA 和 Azure SQL 的所有其他基于 SQL 身份验证的帐户,以及用于 Azure SQL 托管实例的 Windows 身份验证。
要开始使用,请查看 配置仅限 Microsoft Entra 的身份验证。
多重身份验证 (MFA)
Microsoft Entra 多重身份验证是 Microsoft 基于云的标识和访问管理服务提供的安全功能。 多重身份验证要求用户在密码之外提供额外的验证步骤,从而增强用户登录的安全性。
Microsoft Entra 多重身份验证可帮助保护对数据和应用程序的访问,同时可以满足用户对简单登录过程的需求。 MFA 通过要求用户提供两个或两个以上的身份验证因素,为用户登录添加了额外的安全层。 这些因素通常包括用户知道的东西(密码)、用户拥有的东西(智能手机或硬件令牌),以及/或用户自身的东西(生物识别数据)。 通过结合多种因素,MFA 可显著降低未经授权的访问的可能性。
Azure SQL 数据库、Azure SQL 托管实例、Azure Synapse Analytics 和 SQL Server 2022 (16.x) 及更高版本支持多重身份验证方法。
要开始使用,请查看配置 Microsoft Entra 多重身份验证。
Microsoft Entra B2B 支持
所有 SQL 产品中的 Microsoft Entra 身份验证还支持 Microsoft Entra B2B 协作,从而使企业能够邀请来宾用户与其组织协作。 来宾用户可以作为单个用户或 Microsoft Entra 组的成员连接到数据库。 有关详细信息,请参阅创建来宾用户。
Microsoft Entra 与 Active Directory 联合身份验证的信任体系结构
对于联合身份验证,Microsoft Entra ID 支持密码哈希身份验证。
有关 Microsoft Entra 混合标识的设置和同步的详细信息,请参阅以下文章:
- 使用 Microsoft Entra Connect Sync 实现密码哈希同步
- 在 Azure 中部署 Active Directory 联合身份验证服务和 Microsoft Entra Connect 和联合身份验证
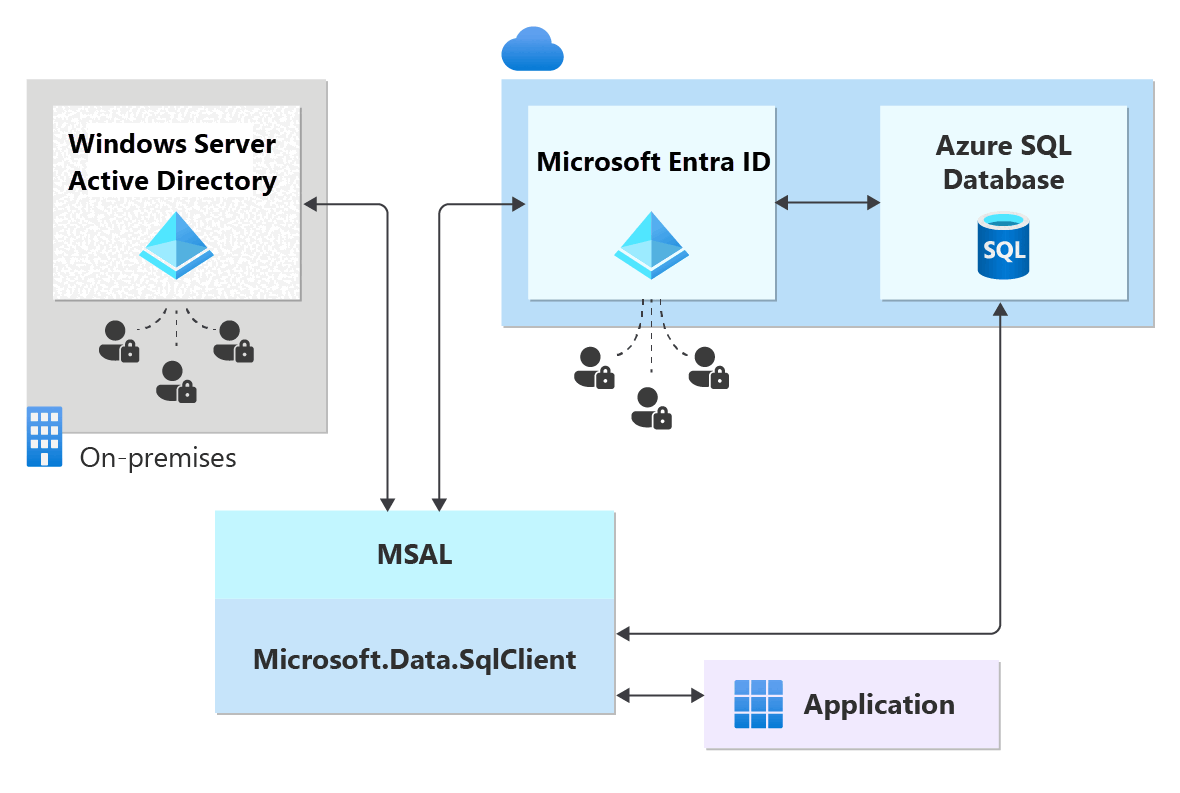
此关系图显示有关使用 ADFS 基础结构(或 Windows 凭证的用户/密码)进行联合身份验证的示例。 箭头表示通信路径。
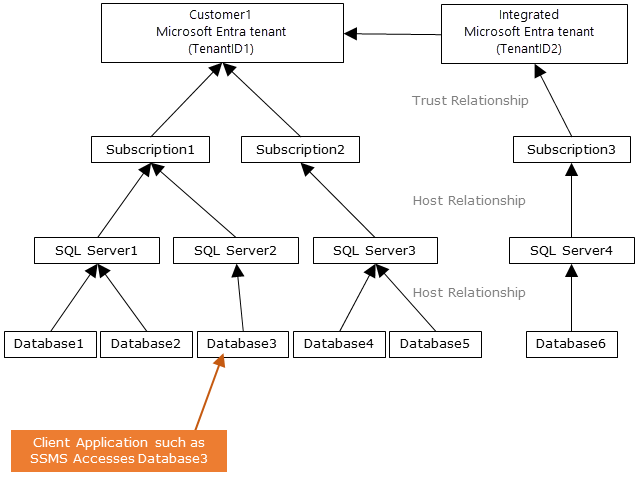
下图表明允许客户端通过提交令牌连接到数据库的联合、信任和托管关系。 Microsoft Entra ID 对令牌进行身份验证,数据库信任令牌并验证颁发者和其他详细信息。 客户 1 可以代表本机用户的 Microsoft Entra ID,也可以代表联合用户的 Microsoft Entra ID。 客户 2 代表一种包括已导入用户的可行解决方案,在此示例中,这些用户来自基于 ADFS 的联合 Microsoft Entra ID,且 ADFS 与 Microsoft Entra ID 同步。 请务必了解,使用 Microsoft Entra 身份验证访问数据库需要托管订阅与 Microsoft Entra ID 相关联。 必须使用相同的订阅创建 Azure SQL 或 Azure Synapse 资源。
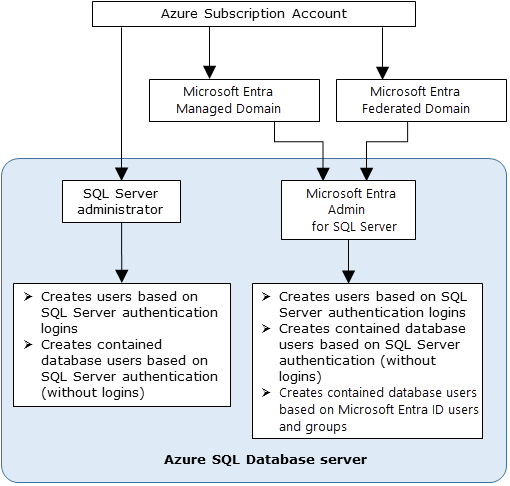
权限
分配给 Microsoft Entra 管理员的权限与 Azure SQL 中的权限分配主体不同。 在少数情况下,Azure SQL 还需要 Microsoft Graph 权限才能使用 Microsoft Entra 身份验证。
管理员权限
Microsoft Entra 管理员在创建时被分配以下权限和角色:
- 服务器或实例上每个数据库的 db_owner
Azure SQL 权限
主体需要在数据库中拥有 ALTER ANY USER 权限以便创建用户。
默认情况下,ALTER ANY USER 授予服务器管理员帐户、具有 CONTROL ON DATABASE 的数据库用户和 db_owner 数据库角色的成员。
若要在 Azure SQL 中创建 Microsoft Entra 主体,请求标识必须查询 Microsoft Graph 以获取有关主体的详细信息。 初始部署时,唯一能够查询 MS Graph 的标识是 Microsoft Entra 管理员;因此,管理员必须是创建其他 Microsoft Entra 主体的第一个标识。 之后,它可以分配 ALTER ANY USER 给其他主体,以允许它们也创建其他 Microsoft Entra 主体。
使用 Microsoft Entra 身份验证进行零接触部署
由于 Microsoft Entra 管理员必须是连接到数据库并创建其他 Microsoft Entra 用户的第一个标识,因此将部署基础结构的标识添加为管理员会非常有用。 然后,部署可以执行初始设置,例如创建其他 Microsoft Entra 主体并为其分配权限。 部署可以使用 PowerShell ARM 模板等工具来编写自动主体创建脚本。 Azure SQL 目前不支持本机 API 来配置用户创建和权限管理;仅允许通过与 SQL 实例直接连接来完成这些操作。
Microsoft Graph 权限
若要创建 Microsoft Entra 主体和其他几种应用场景,Azure SQL 需要进行 Microsoft Graph 调用,以检索有关 Microsoft Entra ID 中的标识的信息,并验证其是否存在。 为此,SQL 进程必须具有或获取对客户租户中的 MS Graph 读取权限的访问,这可以通过多种方式实现:
- 如果执行命令的 SQL 主体是用户标识,则查询 MS Graph 不需要 SQL 实例上的额外权限。
- 如果执行命令的 SQL 主体是服务标识,例如服务主体或托管标识,则 Azure SQL 实例需要其自己的权限来查询 MS Graph。
- 可将应用程序权限分配给逻辑服务器或托管实例的主服务器标识(托管标识)。 SQL 进程可以使用主服务器标识向租户中的其他 Azure 服务(如 MS Graph)进行身份验证。 下表说明了命令成功执行所需的各种应用场景和 MS Graph 权限。
| 应用场景 | 最低权限 |
|---|---|
CREATE 用户 或 CREATE LOGIN Microsoft Entra 服务主体或托管身份 |
Application.Read.All |
CREATE USER 或适用于CREATE LOGIN Microsoft Entra 用户 |
User.Read.All |
CREATE Microsoft Entra 组中的用户或 CREATE LOGIN |
GroupMember.Read.All |
| 使用 Azure SQL 托管实例的 Microsoft Entra 身份验证 | 分配给托管实例标识的目录读取者角色 |
提示
目录读取者角色是最小范围的角色,可以分配给涵盖 Azure SQL 所需的所有权限的标识。 使用角色的优点是能够分配给 Microsoft Entra 安全组,将管理从单个实体中抽象出来,并转换为概念组。
工具支持
SQL Server Management Studio (SSMS) 支持许多 Microsoft Entra 身份验证连接选项,包括多重身份验证。
从 2015 版开始,适用于 Visual Studio 的 SQL Server Data Tools (SSDT) 支持使用 Microsoft Entra ID 进行密码、集成和交互式身份验证。 有关详细信息,请参阅 SQL Server Data Tools (SSDT) 中的 Microsoft Entra ID 支持。
- 目前,Microsoft Entra 用户不会显示在 SSDT 对象资源管理器中。 解决方法是在 sys.database_principals 中查看这些用户。
最低版本
若要将 Microsoft Entra 身份验证与 Azure SQL 配合使用,在使用这些工具时需要以下最低版本:
- SQL Server Management Studio (SSMS) 18.6 或更高版本
- 适用于 Visual Studio 2015 的 SQL Server Data Tools,版本 14.0.60311.1(2016 年 4 月)或更高版本
- 用于 SQL Server 的 .NET Framework 数据提供程序,最低版本 .NET Framework 4.6
- 从版本 15.0.1 开始,sqlcmd 实用工具和 bcp 实用工具支持使用多重身份验证的 Active Directory 交互式身份验证。
- Microsoft JDBC Driver 6.0 for SQL Server 支持 Microsoft Entra 身份验证。 另外,请参阅设置连接属性。
使用 Microsoft Entra 连接到 Azure SQL 资源
为 Azure SQL 资源配置 Microsoft Entra 身份验证后,可以使用 SQL Server Management Studio、SQL Server Data Tools 和客户端应用程序连接到该资源。
限制
将 Microsoft Entra 身份验证与 Azure SQL 配合使用时,请考虑以下限制:
属于超过 2048 个 Microsoft Entra 安全组的成员的 Microsoft Entra 用户和服务主体(Microsoft Entra 应用程序)不受支持,且无法登录数据库。
不支持以下系统功能,并在由 Microsoft Entra 主体执行时返回
NULL值:SUSER_ID()SUSER_NAME(<ID>)SUSER_SNAME(<SID>)SUSER_ID(<name>)SUSER_SID(<name>)
我们建议将连接超时值设置为 30 秒。
Azure SQL 数据库和 Azure Synapse Analytics
将 Microsoft Entra 身份验证与 Azure SQL 数据库 和 Azure Synapse Analytics 配合使用时,请考虑以下限制:
属于作为
db_owner数据库角色成员的组的 Microsoft Entra 用户在尝试针对 Azure SQL 数据库和 Azure Synapse 使用 CREATE DATABASE SCOPED CREDENTIAL 语法时可能会看到以下错误:SQL Error [2760] [S0001]: The specified schema name 'user@mydomain.com' either doesn't exist or you do not have permission to use it.若要缓解
CREATE DATABASE SCOPED CREDENTIAL问题,请将 Microsoft Entra 用户的标识直接添加到db_owner角色。Azure SQL 数据库和 Azure Synapse Analytics 不会为以 Microsoft Entra 组成员身份登录的用户创建隐式用户。 因此,需要分配所有权的多种操作都会失败,即使将 Microsoft Entra 组作为成员添加到具有这些权限的角色也是如此。
例如,通过具有 db_ddladmin 角色的 Microsoft Entra 组登录到数据库的用户,如果没有显式定义的架构,如表、视图或类型,则无法执行
CREATE SCHEMA、ALTER SCHEMA以及其他对象创建语句。 若要解决此问题,必须为该用户创建 Microsoft Entra 用户,或者更改 Microsoft Entra 组的设置,以便分配一个如DEFAULT_SCHEMA的角色。如果使用异地复制和故障转移组,必须为主服务器和辅助服务器配置 Microsoft Entra 管理员。 如果服务器没有 Microsoft Entra 管理员,则 Microsoft Entra 登录名和用户会收到
Cannot connect错误。移除服务器的 Microsoft Entra 管理员会阻止建立与服务器的任何 Microsoft Entra 身份验证连接。 必要时,SQL 数据库管理员可以手动删除无法使用的 Microsoft Entra 用户。
Azure SQL 托管实例
将 Microsoft Entra 身份验证与 Azure SQL 托管实例配合使用时,请考虑以下限制:
SQL 托管实例支持 Microsoft Entra 服务器主体(登录名)和用户。
SQL 托管实例 不支持将 Microsoft Entra 组登录名设置为数据库所有者。
- 此情况的扩展是当将组添加为
dbcreator服务器角色的一部分时,此组中的用户可以连接到 SQL 托管实例并创建新数据库,但不能访问数据库。 这是因为新的数据库所有者是 SA,而不是 Microsoft Entra 用户。 如果将个体用户添加到dbcreator服务器角色,则不会出现此问题。
- 此情况的扩展是当将组添加为
SQL 托管实例的 Microsoft Entra 服务器主体(登录名)允许创建多个可添加到
sysadmin角色的登录名。Microsoft Entra 登录名支持 SQL 代理管理和作业执行。
Microsoft Entra 服务器主体(登录名)可以执行数据库备份和还原操作。
支持审核与 Microsoft Entra 服务器主体(登录名)和身份验证事件相关的所有语句。
支持为属于 sysadmin 服务器角色成员的 Microsoft Entra 服务器主体(登录名)建立专用管理员连接。
- 可以通过 SQLCMD 实用工具和 SQL Server Management Studio 提供此支持。
来自 Microsoft Entra 服务器主体(登录名)的登录事件支持登录触发器。
可以使用 Microsoft Entra 服务器主体(登录名)设置 Service Broker 和数据库邮件。
使用故障转移组时,必须为主实例和辅助实例配置 Microsoft Entra 管理员。 如果实例没有 Microsoft Entra 管理员,则 Microsoft Entra 登录名和用户会收到
Cannot connect错误。PolyBase 无法使用 Microsoft Entra 身份验证进行身份验证。
移除实例的 Microsoft Entra 管理员会阻止与实例建立任何 Microsoft Entra 身份验证连接。 必要时,SQL 托管实例管理员可以手动删除无法使用的 Microsoft Entra 用户。