Azure 数据资源管理器会加密存储帐户中的所有静态数据。 默认情况下,数据使用 Microsoft 管理的密钥进行加密。 为了额外控制加密密钥,可以提供客户管理的密钥用于数据加密。
客户管理的密钥必须存储在 Azure Key Vault 中。 可以创建自己的密钥并将其存储在 Key Vault 中,或者使用 Azure Key Vault API 来生成密钥。 Azure 数据资源管理器群集和密钥保管库必须位于同一区域,但它们可以位于不同的订阅中。 有关客户管理的密钥的详细说明,请参阅 使用 Azure Key Vault 的客户管理的密钥。
本文介绍如何配置客户管理的密钥。
有关基于以前的 SDK 版本的代码示例,请参阅存档的文章。
若要使用 Azure 数据资源管理器配置客户管理的密钥,必须在 密钥保管库上设置两个属性: 软删除 和 不清除。 默认情况下不会启用这些属性。 若要启用这些属性,请在新的或现有的密钥保管库上在 PowerShell 或 Azure CLI 中执行“启用软删除”和“启用清除保护”。 支持 RSA 和大小为 2048、3072 和 4096 的 RSA-HSM 密钥。 若要利用 RSA-HSM 密钥,请使用以下 C#、Azure CLI、PowerShell 或 ARM 模板方法。 有关密钥的详细信息,请参阅 Key Vault 密钥。
注释
有关在领导者和关注者群集上使用客户托管密钥的限制的信息,请参阅“限制”。
将托管标识分配给群集
若要为群集启用客户管理的密钥,请先将系统分配的托管标识或用户分配的托管标识分配给群集。 你将使用此托管标识授予群集访问密钥保管库的权限。 若要配置托管标识,请参阅 托管标识。
使用客户管理的密钥启用加密
以下步骤说明如何使用 Azure 门户启用客户管理的密钥加密。 默认情况下,Azure 数据资源管理器加密使用Microsoft管理的密钥。 将 Azure 数据资源管理器群集配置为使用客户管理的密钥,并指定要与群集关联的密钥。
在 Azure 门户中,转到 Azure 数据资源管理器群集 资源。
在门户的左窗格中选择 “设置>加密 ”。
在“加密”窗格中,为“客户管理的密钥”设置选择“开”。
选择 “选择密钥”。
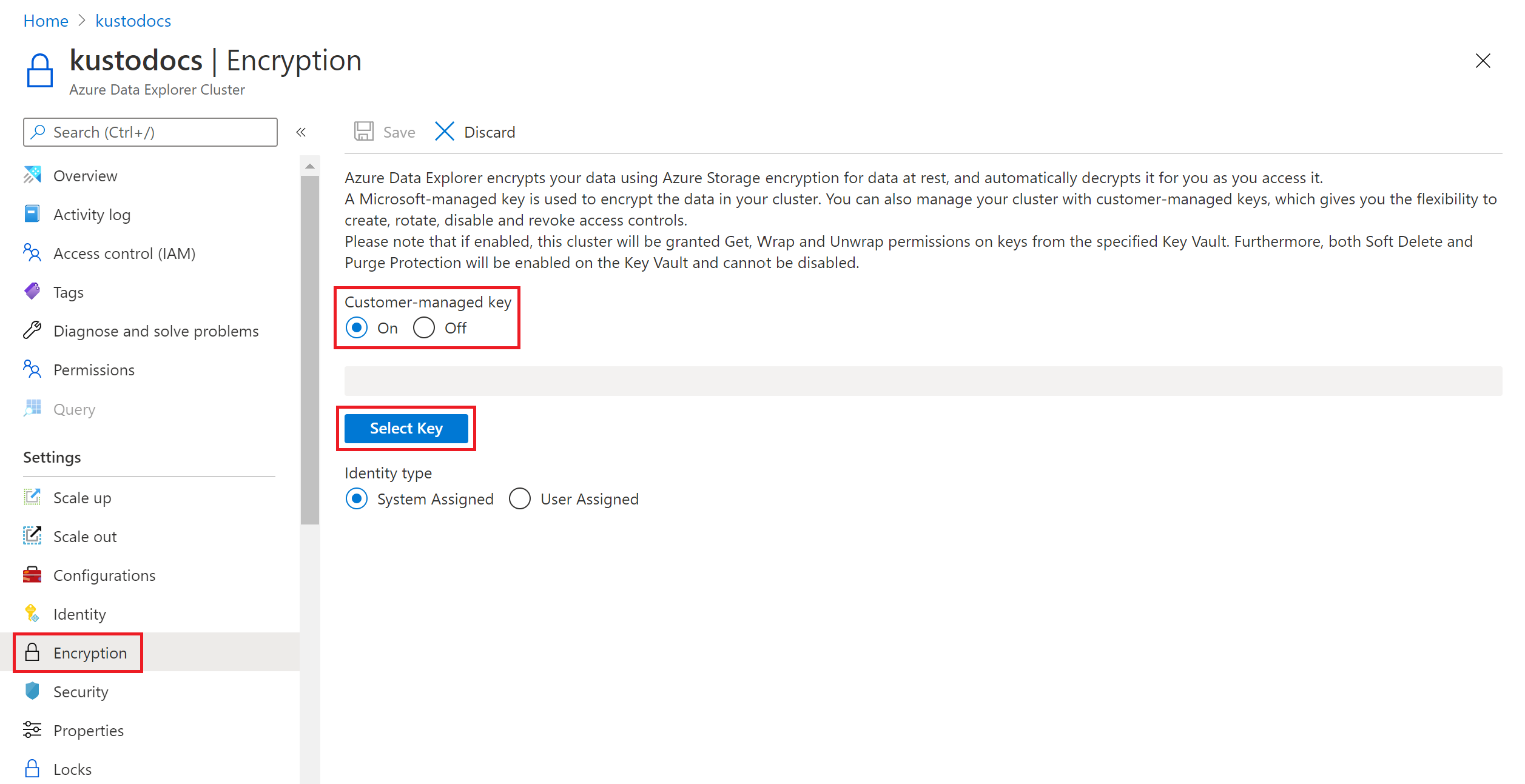
在 “从 Azure Key Vault 中选择密钥 ”窗口中,从下拉列表中选择现有的 Key Vault 。 如果选择“创建新密钥保管库”,则会路由到“创建 Key Vault”屏幕。
选择 密钥。
版本:
- 若要确保此密钥始终使用最新的密钥版本,请选中 “始终使用当前密钥版本 ”复选框。
- 否则,请选择 “版本”。
选择 选择。
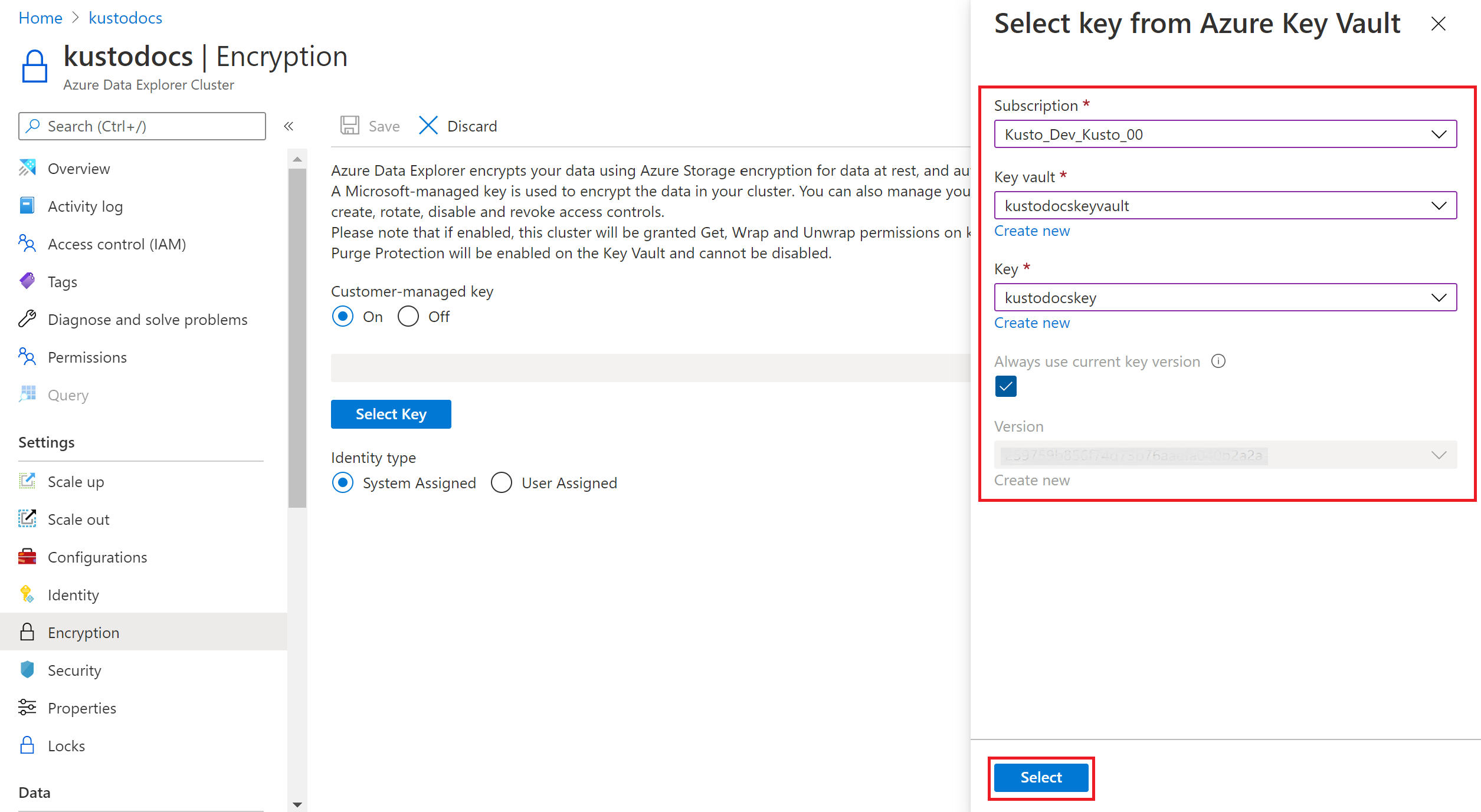
在 “标识类型”下,选择“ 系统分配 ”或“ 用户分配”。
如果选择用户分配,请从下拉列表中选择用户分配的身份。
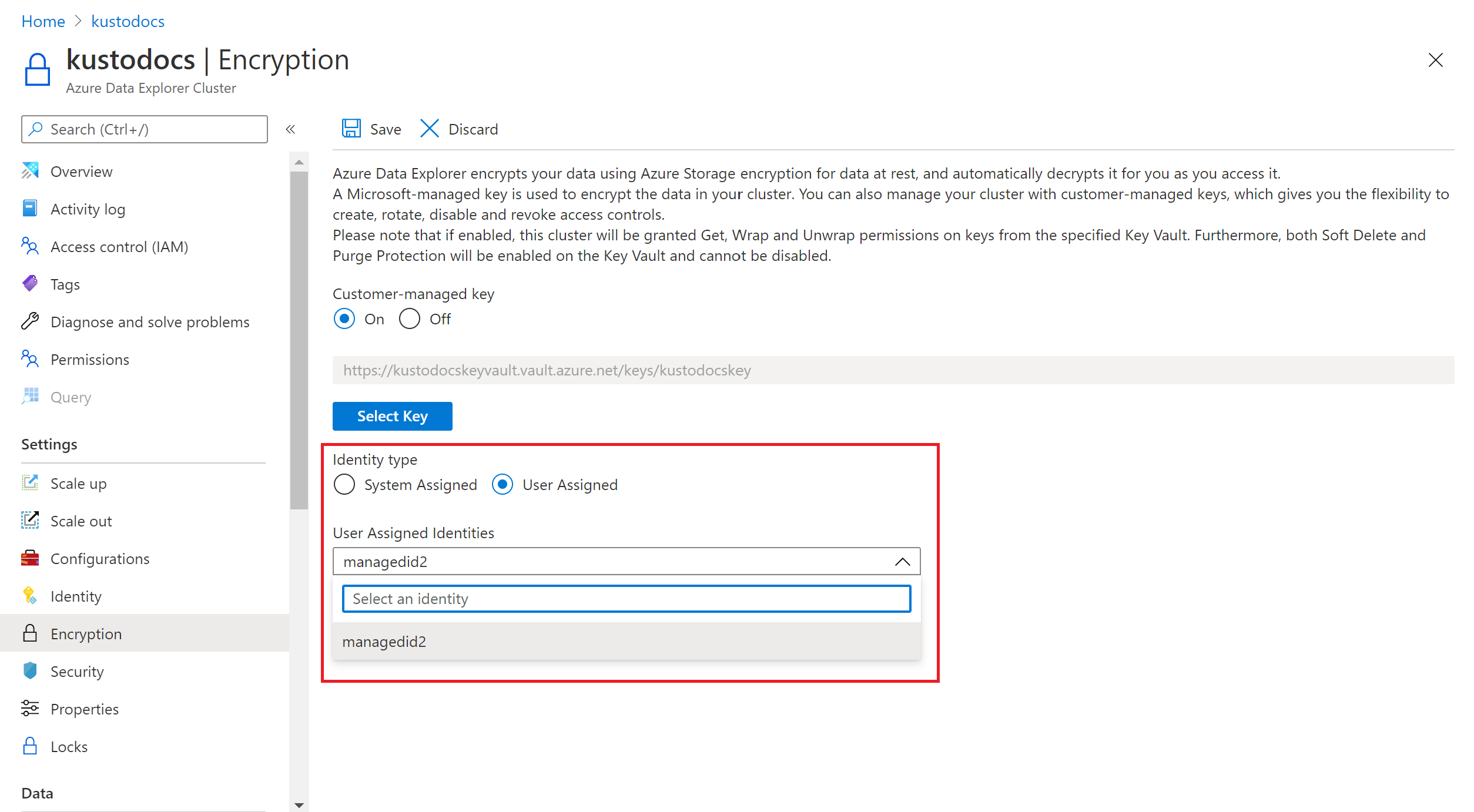
在现在包含密钥的 “加密 ”窗格中,选择“ 保存”。 CMK 创建成功后,“ 通知”中会显示一条成功消息。
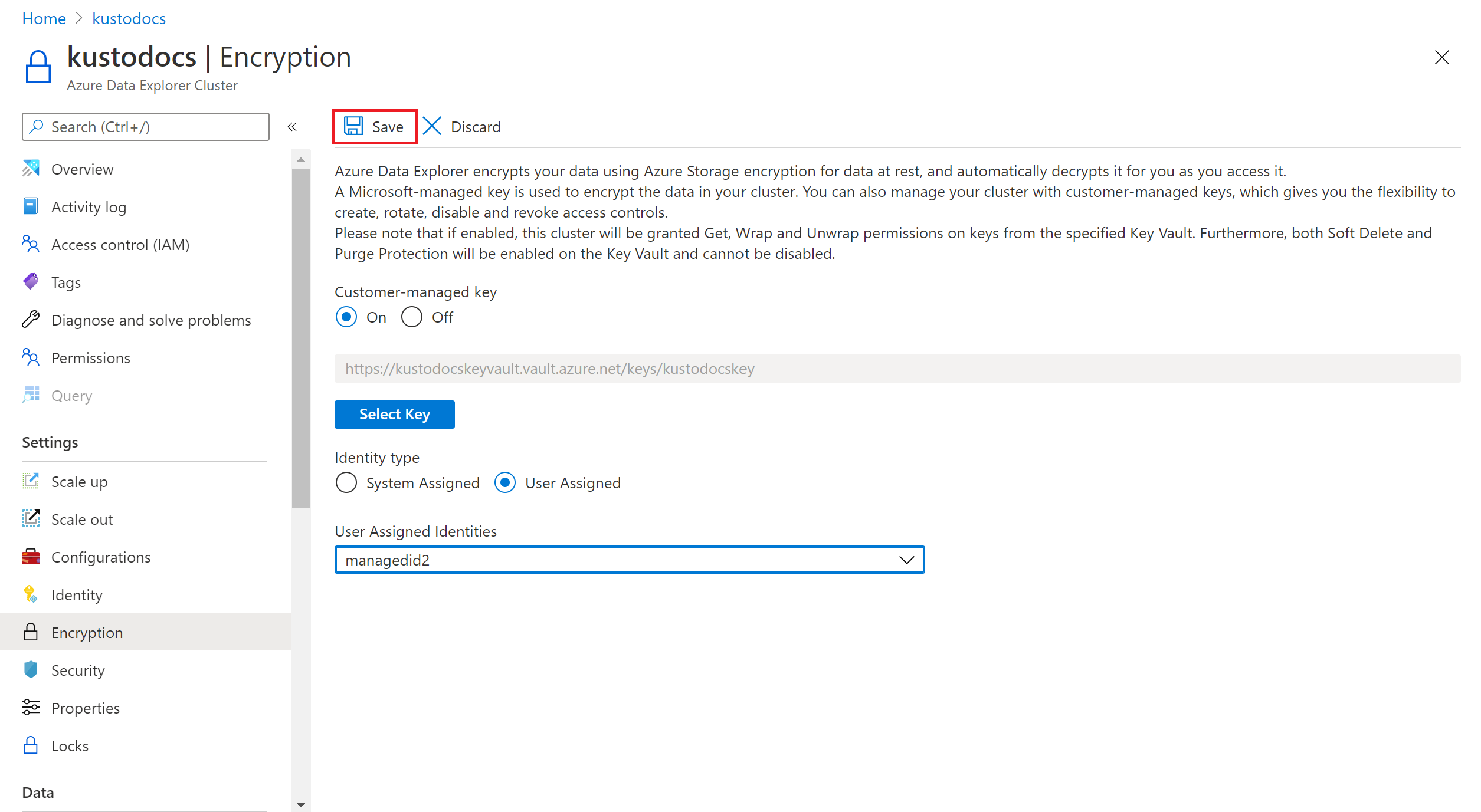
如果在为 Azure 数据资源管理器群集启用客户管理的密钥时选择系统分配的标识,则为群集创建系统分配的标识(如果不存在)。 此外,你将向所选 Key Vault 上的 Azure 数据资源管理器群集提供所需的 get、wrapKey 和 unwrapKey 权限,并获取 Key Vault 属性。
注释
选择 “关闭 ”以在创建客户管理的密钥后将其删除。
以下部分介绍如何使用 Azure 数据资源管理器 C# 客户端配置客户管理的密钥加密。
安装软件包
Authentication
若要运行本文中的示例, 请创建可访问资源的 Microsoft Entra 应用程序和 服务主体。 可以在订阅范围内添加角色分配,并获取所需的 Microsoft Entra Directory (tenant) ID、Application ID 和 Application Secret。
以下代码片段演示如何使用 Microsoft身份验证库(MSAL) 获取Microsoft Entra 应用程序令牌来访问群集。 若要使流成功,必须将应用程序注册到 Microsoft Entra ID,并且必须具有应用程序身份验证的凭据,例如Microsoft Entra ID 颁发的应用程序密钥或Microsoft Entra 注册的 X.509v2 证书。
默认情况下,Azure 数据资源管理器加密使用Microsoft管理的密钥。 将 Azure 数据资源管理器群集配置为使用客户管理的密钥,并指定要与群集关联的密钥。
使用以下代码更新群集:
var tenantId = "xxxxxxxx-xxxxx-xxxx-xxxx-xxxxxxxxx"; // Azure AD Directory (tenant) ID
var clientId = "xxxxxxxx-xxxxx-xxxx-xxxx-xxxxxxxxx"; // Application ID
var clientSecret = "PlaceholderClientSecret"; // Application secret
var subscriptionId = "xxxxxxxx-xxxxx-xxxx-xxxx-xxxxxxxxx";
var credentials = new ClientSecretCredential(tenantId, clientId, clientSecret);
var resourceManagementClient = new ArmClient(credentials, subscriptionId);
var resourceGroupName = "testrg";
var clusterName = "mykustocluster";
var subscription = await resourceManagementClient.GetDefaultSubscriptionAsync();
var resourceGroup = (await subscription.GetResourceGroupAsync(resourceGroupName)).Value;
var clusters = resourceGroup.GetKustoClusters();
var cluster = (await clusters.GetAsync(clusterName)).Value;
var clusterPatch = new KustoClusterPatch(cluster.Data.Location)
{
KeyVaultProperties = new KustoKeyVaultProperties
{
KeyName = "<keyName>",
KeyVersion = "<keyVersion>", // Optional, leave as NULL for the latest version of the key.
KeyVaultUri = new Uri("https://<keyVaultName>.vault.azure.cn/"),
UserIdentity = "/subscriptions/<identitySubscriptionId>/resourcegroups/<identityResourceGroupName>/providers/Microsoft.ManagedIdentity/userAssignedIdentities/<identityName>" // Use NULL if you want to use system assigned identity.
}
};
await cluster.UpdateAsync(WaitUntil.Completed, clusterPatch);
运行以下命令,检查群集是否已成功更新:
var clusterData = (await resourceGroup.GetKustoClusterAsync(clusterName)).Value.Data;
如果结果包含ProvisioningState并具有Succeeded值,则您的集群已成功更新。
以下步骤介绍如何使用 Azure CLI 客户端启用客户管理的密钥加密。 默认情况下,Azure 数据资源管理器加密使用Microsoft管理的密钥。 将 Azure 数据资源管理器群集配置为使用客户管理的密钥,并指定要与群集关联的密钥。
运行以下命令来登录到 Azure:
az login
设置群集注册所在的订阅。 将 MyAzureSub 替换为要使用的 Azure 订阅的名称。
az account set --subscription MyAzureSub
运行以下命令,使用群集的系统分配标识设置新密钥
az kusto cluster update --cluster-name "mytestcluster" --resource-group "mytestrg" --key-vault-properties key-name="<key-name>" key-version="<key-version>" key-vault-uri="<key-vault-uri>"
或者,使用用户分配的标识设置新密钥。
az kusto cluster update --cluster-name "mytestcluster" --resource-group "mytestrg" --key-vault-properties key-name="<key-name>" key-version="<key-version>" key-vault-uri="<key-vault-uri>" key-user-identity="<user-identity-resource-id>"
运行以下命令并检查“keyVaultProperties”属性以验证群集是否已成功更新。
az kusto cluster show --cluster-name "mytestcluster" --resource-group "mytestrg"
以下步骤说明如何使用 PowerShell 启用客户管理的密钥加密。 默认情况下,Azure 数据资源管理器加密使用Microsoft管理的密钥。 将 Azure 数据资源管理器群集配置为使用客户管理的密钥,并指定要与群集关联的密钥。
运行以下命令来登录到 Azure:
Connect-AzAccount -Environment AzureChinaCloud
设置群集注册所在的订阅。
Set-AzContext -SubscriptionId "xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx"
运行以下命令,使用系统分配的标识设置新密钥。
Update-AzKustoCluster -ResourceGroupName "mytestrg" -Name "mytestcluster" -KeyVaultPropertyKeyName "<key-name>" -KeyVaultPropertyKeyVaultUri "<key-vault-uri>" -KeyVaultPropertyKeyVersion "<key-version>"
或者,使用用户分配的标识设置新密钥。
Update-AzKustoCluster -ResourceGroupName "mytestrg" -Name "mytestcluster" -KeyVaultPropertyKeyName "<key-name>" -KeyVaultPropertyKeyVaultUri "<key-vault-uri>" -KeyVaultPropertyKeyVersion "<key-version>" -KeyVaultPropertyUserIdentity "user-assigned-identity-resource-id"
运行以下命令,并检查"KeyVaultProperty..."属性以验证群集是否成功更新。
Get-AzKustoCluster -Name "mytestcluster" -ResourceGroupName "mytestrg" | Format-List
以下步骤说明如何使用 Azure 资源管理器模板配置客户管理的密钥。 默认情况下,Azure 数据资源管理器加密使用Microsoft管理的密钥。 在此步骤中,将 Azure 数据资源管理器群集配置为使用客户管理的密钥并指定要与群集关联的密钥。
如果要使用系统分配的标识访问密钥保管库,请留 userIdentity 空。 否则,请设置身份识别的资源 ID。
可以使用 Azure 门户或使用 PowerShell 部署 Azure 资源管理器模板。
{
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"clusterName": {
"type": "string",
"defaultValue": "[concat('kusto', uniqueString(resourceGroup().id))]",
"metadata": {
"description": "Name of the cluster to create"
}
},
"location": {
"type": "string",
"defaultValue": "[resourceGroup().location]",
"metadata": {
"description": "Location for all resources."
}
}
},
"variables": {},
"resources": [
{
"name": "[parameters('clusterName')]",
"type": "Microsoft.Kusto/clusters",
"sku": {
"name": "Standard_D13_v2",
"tier": "Standard",
"capacity": 2
},
"apiVersion": "2019-09-07",
"location": "[parameters('location')]",
"properties": {
"keyVaultProperties": {
"keyVaultUri": "<keyVaultUri>",
"keyName": "<keyName>",
"keyVersion": "<keyVersion>",
"userIdentity": "<userIdentity>"
}
}
}
]
}
更新密钥版本
创建新版本的密钥时,需要更新群集以使用新版本。 首先,调用 Get-AzKeyVaultKey 以获取最新版本的密钥。 然后更新群集的密钥保管库属性以使用新版密钥,如 “使用客户管理的密钥启用加密”中所示。
相关内容



