机密范围
管理机密时首先需要创建机密范围。 机密范围是由名称标识的机密的集合。
一个工作区最多只能有 1000 个机密范围。 如果需要更多,请联系 Azure Databricks 支持团队。
注意
Databricks 建议将机密范围与角色或应用程序而非个人对齐。
概述
有两种类型的机密范围:Azure Key Vault 支持和 Databricks 支持。
Azure Key Vault 支持的范围
若要引用 Azure Key Vault 中存储的机密,可以创建 Azure Key Vault 支持的机密范围。 然后,你可以利用该机密范围中相应 Key Vault 实例中的所有机密。 由于 Azure Key Vault 支持的机密范围是 Key Vault 的只读接口,因此不允许进行 PutSecret 和 DeleteSecret机密 API 操作。 若要在 Azure 密钥保管库中管理机密,必须使用 Azure 设置机密 REST API 或 Azure 门户 UI。
Databricks 支持的范围
Databricks 支持的机密范围存储在 Azure Databricks 拥有并管理的加密数据库中并由该数据库支持。 机密范围名称:
- 在工作区中必须唯一。
- 必须包含字母数字字符、短划线、下划线、
@和句点,并且不得超过 128 个字符。
这些名称被视为是非敏感信息,工作区中的所有用户都可读取它们。
使用 Databricks CLI(版本 0.205 及更高版本)创建 Databricks 支持的机密范围。 也可以使用机密 API。
范围权限
使用 机密 ACL 控制的权限创建范围。 在默认情况下,使用创建范围的用户(“创建者”)的 MANAGE 权限创建范围,这使创建者可以读取范围中的机密、将机密写入范围以及更改范围的 ACL。 如果你的帐户具有高级计划,则可以在创建范围后随时分配细粒度权限。 有关详细信息,请参阅机密 ACL。
你还可以替代默认值,并在创建范围时向所有用户显式授予“管理”权限。 事实上,如果你的帐户不具有高级计划,则必须执行此操作。
注意
机密 ACL 位于作用域级别。 如果使用 Azure 密钥保管库支持的范围,则被授予该作用域访问权限的用户有权访问 Azure 密钥保管库中的所有机密。 若要限制访问,请使用单独的 Azure 密钥保管库实例。
创建 Azure Key Vault 支持的机密范围
本部分介绍如何使用 Azure 门户和 Azure Databricks 工作区 UI 创建 Azure Key Vault 支持的机密范围。 也可以使用 Databricks CLI 创建 Azure Key Vault 支持的机密范围。
要求
必须在要用于支持机密范围的 Azure 密钥保管库实例上具有“密钥保管库参与者”、“参与者”或“所有者”角色。
如果没有密钥保管库实例,请按照使用 Azure 门户创建 Key Vault 中的说明进行操作。
注意
创建 Azure Key Vault 支持的机密范围需要 Azure 密钥保管库实例上的“参与者”或“所有者”角色,即使 Azure Databricks 服务之前已被授予对密钥保管库的访问权限。
如果密钥保管库与 Azure Databricks 工作区位于不同的租户中,则创建机密范围的 Azure AD 用户必须具有在密钥保管库租户中创建服务主体的权限。 否则将发生以下错误:
Unable to grant read/list permission to Databricks service principal to KeyVault 'https://xxxxx.vault.azure.cn/': Status code 403, {"odata.error":{"code":"Authorization_RequestDenied","message":{"lang":"en","value":"Insufficient privileges to complete the operation."},"requestId":"XXXXX","date":"YYYY-MM-DDTHH:MM:SS"}}
为 Azure Databricks 配置 Azure 密钥保管库实例
登录到 Azure 门户,查找并选择 Azure 密钥保管库实例。
在“设置”下选择“访问配置”选项卡。
将 权限模型 设置为 保管库访问策略。
注意
创建 Azure Key Vault 支持的机密范围角色会使用密钥保管库访问策略授予对 Azure Databricks 服务的应用 ID 的“获取”和“列表”权限。 Azure Databricks 当前不支持 Azure 基于角色的访问控制权限模型。
在“设置”下选择“网络”选项卡。
在“防火墙和虚拟网络”中,将“允许的访问来源:”设置为“允许从特定虚拟网络和 IP 地址访问”。
在“例外”下,选中“允许受信任的 Microsoft 服务跳过此防火墙”。
注意
还可以将“允许的访问来源”设置为“允许来自所有网络的公共访问”。
创建 Azure Key Vault 支持的机密范围
转到
https://<databricks-instance>#secrets/createScope。 (将<databricks-instance>替换为 Azure Databricks 部署的工作区 URL)。 此 URL 区分大小写(createScope中的范围必须大写)。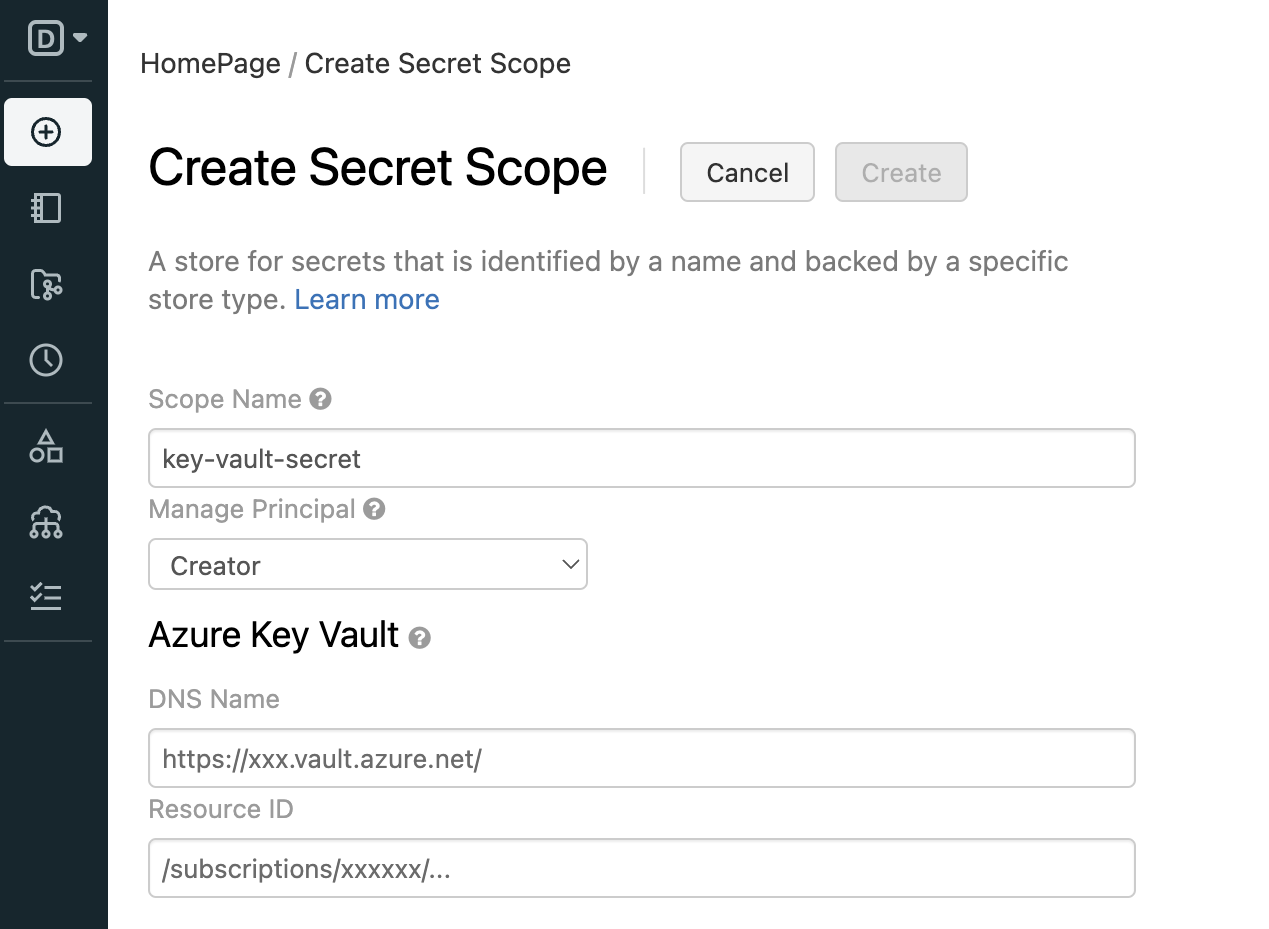
输入机密范围的名称。 机密范围名称不区分大小写。
使用“管理主体”下拉列表指定是所有用户都对此机密范围具有“管理”权限,还是仅机密范围的创建者具有该权限。
“管理”权限允许用户在此机密范围内进行读取和写入,如果是高级计划中的帐户,则还允许更改范围的权限。
你的帐户必须具有高级计划才能选择“创建者”。 建议的做法是:在创建机密范围时向创建者授予“管理”权限,然后在测试范围后分配更细粒度的访问权限。 有关示例工作流的信息,请参阅机密工作流示例。
如果你的帐户具有标准计划,则必须将 MANAGE 权限设置为“所有用户”组。 如果在此处选择“创建者”,则在尝试保存该范围时,将看到一条错误消息。
有关“管理”权限的详细信息,请参阅机密 ACL。
输入“DNS 名称”(例如 )和“资源 ID”,例如:
/subscriptions/xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx/resourcegroups/databricks-rg/providers/Microsoft.KeyVault/vaults/databricksKV可从 Azure 门户中 Azure Key Vault 的“设置 > 属性”选项卡中使用这些属性。
单击“创建” 按钮。
使用 Databricks CLI
databricks secrets list-scopes命令验证是否已成功创建范围。
创建 Databricks 支持的机密范围
机密范围名称不区分大小写。
使用 Databricks CLI 创建范围:
databricks secrets create-scope <scope-name>
默认情况下,使用创建范围的用户的“管理”权限创建范围。 如果你的帐户没有高级计划,则必须替代此默认值,并在创建范围时向用户(所有用户)显式授予 MANAGE 权限:
databricks secrets create-scope <scope-name> --initial-manage-principal users
还可使用机密 API 来创建 Databricks 支持的机密范围。
如果你的帐户具有高级计划,则可以在创建范围后随时更改权限。 有关详细信息,请参阅机密 ACL。
创建 Databricks 支持的机密范围后,可以添加机密。
列出机密范围
使用 CLI 列出工作区中的现有范围:
databricks secrets list-scopes
还可使用机密 API 来列出现有范围。
删除机密范围
删除机密范围时会删除应用于该范围的所有机密和 ACL。 要使用 CLI 删除范围,请运行以下命令:
databricks secrets delete-scope <scope-name>
还可使用机密 API 来删除机密范围。