控制出站网络访问是整个网络安全计划的重要组成部分。 例如,你可能想要限制对网站的访问, 您可能希望限制可以访问的出站 IP 地址和端口。
可以控制 Azure 子网的出站网络访问的一种方法是使用 Azure 防火墙。 使用 Azure 防火墙,可以配置:
- 应用程序规则,用于定义可从子网访问的完全限定域名 (FQDN)。
- 网络规则,用于定义源地址、协议、目标端口和目标地址。
将网络流量路由到用作子网默认网关的防火墙时,网络流量受到配置的防火墙规则的控制。
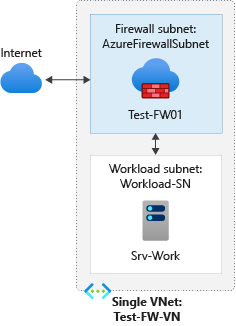
在本文中,你将创建一个包含两个子网的简化虚拟网络便于轻松部署。
对于生产部署,建议使用中心辐射模型,其中的防火墙位于其自身的虚拟网络中。 工作负载服务器位于同一区域的对等虚拟网络中,并包含一个或多个子网。
- AzureFirewallSubnet - 防火墙在此子网中。
- Workload-SN - 工作负荷服务器在此子网中。 此子网的网络流量通过防火墙。
在本文中,您将学习如何:
- 设置测试网络环境
- 部署防火墙
- 创建默认路由
- 配置一个应用程序规则以允许访问 www.qq.com
- 配置网络规则,以允许访问外部 DNS 服务器
- 部署 Azure Bastion 以保护 VM 访问
- 测试防火墙
注意事项
本文使用经典防火墙规则来管理防火墙。 首选方法是使用防火墙策略。 若要使用防火墙策略完成此过程,请查看教程:使用 Azure 门户部署和配置 Azure 防火墙和策略
如果需要,可以使用 Azure PowerShell 完成此过程。
先决条件
如果没有 Azure 订阅,请在开始前创建一个试用版订阅。
设置网络
首先,创建一个资源组用于包含部署防火墙所需的资源。 然后创建虚拟网络、子网和测试服务器。
创建资源组
资源组包含此过程中使用的所有资源。
- 登录到 Azure 门户。
- 在 Azure 门户菜单上,选择“资源组”或从任意页面搜索并选择“资源组”。 然后选择“创建”。
- 请选择您的订阅。
- 对于资源组名称,请键入Test-FW-RG。
- 对于“区域”,选择一个区域。 你创建的所有其他资源必须位于同一区域中。
- 选择“查看 + 创建”。
- 选择“创建”。
创建虚拟网络
此虚拟网络有两个子网。
注意事项
AzureFirewallSubnet 子网的大小为 /26。 有关子网大小的详细信息,请参阅 Azure 防火墙常见问题解答。
在 Azure 门户菜单或 主页 上,搜索并选择 “虚拟网络”。
选择“创建”。
在“ 基本信息 ”选项卡上,配置以下设置:
设置 值 Subscription 选择订阅 资源组 Test-FW-RG 虚拟网络名称 Test-FW-VN 区域 中国北部 选择下一步。
在“ 安全 ”选项卡上,配置以下设置:
设置 值 启用 Azure 防火墙 Selected Azure 防火墙名称 Test-FW01 层 标准 Policy 无(使用经典防火墙规则) Azure 防火墙公共 IP 地址 选择 “创建公共 IP 地址”,键入 fw-pip 作为名称,然后选择“ 确定” 选择下一步。
在 “IP 地址 ”选项卡上,配置以下设置:
设置 值 地址空间 接受默认 10.0.0.0/16 子网 选择 默认值,将 名称 更改为 Workload-SN,并将 起始地址 设置为 10.0.2.0/24。 选择“保存”。 选择“查看 + 创建”。
选择“创建”。
注意事项
Azure 防火墙会根据可用端口视需要使用公共 IP。 随机选择一个公共 IP 进行出站连接后,只有在再也无法从当前公共 IP 进行连接后,它才会使用下一个可用的公共 IP。 在流量和吞吐量较高的方案中,建议使用 NAT 网关提供出站连接。 SNAT 端口在与 NAT 网关关联的所有公共 IP 之间动态分配。 若要了解详细信息,请参阅 使用 Azure NAT 网关缩放 SNAT 端口。
创建虚拟机
现在创建工作负荷虚拟机,将其置于“Workload-SN”子网中。
在 Azure 门户菜单或“主页”页上,选择“创建资源” 。
选择“Ubuntu Server 22.04 LTS”。
输入虚拟机的以下值:
设置 值 资源组 Test-FW-RG 虚拟机名称 Srv-Work 区域 中国北部 图像 Ubuntu Server 22.04 LTS - x64 Gen2 尺寸 Standard_B2s 身份验证类型 SSH 公钥 用户名 azureuser SSH 公钥源 生成新密钥对 密钥对名称 Srv-Work_key 在“ 网络 ”选项卡上,配置以下设置:
设置 值 虚拟网络 Test-FW-VN 子网 Workload-SN 公网 IP 没有 接受其他默认值,然后选择“下一步:管理” 。
接受默认值,然后选择“下一步: 监视”。
对于“启动诊断”,请选择“禁用”。 接受其他默认值,然后选择“查看 + 创建”。
检查摘要页上的设置,然后选择“创建”。
在“ 生成新密钥对 ”对话框中,选择“ 下载私钥”并创建资源。 将密钥文件另存为 Srv-Work_key.pem。
部署完成后,选择“转到资源”并记下稍后需要使用的“Srv-Work”专用 IP 地址。
注意事项
Azure 会为未分配公共 IP 地址的 VM 或位于内部基本 Azure 负载均衡器的后端池中的 VM 提供默认出站访问 IP。 默认出站访问 IP 机制会提供不可配置的出站 IP 地址。
发生以下事件之一时,将禁用默认出站访问 IP:
- 将公共 IP 地址分配给 VM。
- 虚拟机被放置在标准负载均衡器的后端池中,可以有出站规则,也可以没有。
- 向 VM 的子网分配了 Azure NAT 网关资源。
在灵活业务流程模式下通过使用虚拟机规模集创建的 VM 没有默认的出站访问权限。
有关 Azure 中的出站连接的详细信息,请参阅 Azure 中的默认出站访问权限和使用用于出站连接的源网络地址转换 (SNAT)。
检查防火墙
- 转到资源组并选择防火墙。
- 记下防火墙专用 IP 地址和公共 IP 地址。 您稍后将使用这些地址。
创建默认路由
为实现通过防火墙的出站和入站连接创建路由,使用虚拟设备专用 IP 作为下一个跃点的默认路由 0.0.0.0/0 即可满足要求。 这会通过防火墙定向任何传出和传入连接。 例如,如果防火墙正在完成 TCP 握手并响应传入请求,则系统会将响应定向到发送流量的 IP 地址。 这是设计的结果。
因此,无需创建另一个用户定义的路由来包括 AzureFirewallSubnet IP 范围。 这可能会导致连接断开。 原始默认路由就已足够。
对于“Workload-SN”子网,请配置出站默认路由,使其通过防火墙。
在 Azure 门户中,搜索并选择 “路由表”。
选择“创建”。
在“ 基本信息 ”选项卡上,配置以下设置:
设置 值 Subscription 选择订阅 资源组 Test-FW-RG 区域 中国北部 Name Firewall-route 传播网关路由 选择首选项 选择“查看 + 创建”。
选择“创建”。
部署完成后,选择“转到资源”。
在 “防火墙路由 ”页上,选择 “设置>子网 ”,然后选择“ 关联”。
对于虚拟网络,请选择“Test-FW-VN”。
对于“子网”,请选择“Workload-SN”。 请确保仅为此路由选择“Workload-SN” 子网,否则防火墙将无法正常工作
选择“确定”。
选择“路由”,然后选择“添加”。
使用以下设置配置路由:
设置 值 路由名称 fw-dg 目标类型 IP 地址 目标 IP 地址/CIDR 范围 0.0.0.0/0 下一个跃点类型 虚拟设备。 Azure 防火墙实际上是一个托管服务,但虚拟设备可在此场合下正常工作。 下一个跃点地址 前面记录的防火墙的专用 IP 地址 选择添加。
配置应用程序规则
这是允许出站访问 www.qq.com 的应用程序规则。
打开 Test-FW-RG 资源组,然后选择 Test-FW01 防火墙。
在 Test-FW01 页的“设置”下,选择“规则(经典)”。
选择“应用程序规则集合”选项卡。
选择“添加应用程序规则集合”。
使用以下设置配置规则集合:
设置 值 Name App-Coll01 Priority 200 Action 允许 在规则、目标 FQDN下,配置以下设置:
设置 值 Name Allow-qq 源类型 IP 地址 来源 10.0.2.0/24 Protocol:port http、https 目标 FQDN www.qq.com选择添加。
Azure 防火墙包含默认情况下允许的基础结构 FQDN 的内置规则集合。 这些 FQDN 特定于平台,不能用于其他目的。 有关详细信息,请参阅基础结构 FQDN。
配置网络规则
这是允许在端口 53 (DNS) 上对两个 IP 地址进行出站访问的网络规则。
选择“网络规则集合”选项卡。
选择“添加网络规则集合”。
使用以下设置配置规则集合:
设置 值 Name Net-Coll01 Priority 200 Action 允许 在 “规则”下, IP 地址配置以下设置:
设置 值 Name Allow-DNS 协议 UDP 源类型 IP 地址 来源 10.0.2.0/24 目标类型 IP 地址 目标地址 209.244.0.3,209.244.0.4 (由 Level3 运营的公共 DNS 服务器) 目标端口 53 选择添加。
部署 Azure Bastion
现在部署 Azure Bastion 以提供对虚拟机的安全访问。
在 Azure 门户菜单中,选择“创建资源”。
在搜索框中,键入 Bastion 并从结果中选择它。
选择“创建”。
在“ 基本信息 ”选项卡上,配置以下设置:
设置 值 Subscription 选择订阅 资源组 Test-FW-RG Name Test-Bastion 区域 中国北部 层 开发人员 虚拟网络 Test-FW-VN 子网 选择 编辑子网 在 “编辑子网 ”页中,配置以下设置:
设置 值 起始地址 10.0.4.0/26 尺寸 /26 选择“ 保存 ”并关闭“子网”页。
选择“查看 + 创建”。
验证通过后,选择“ 创建”。
注意事项
Bastion 部署需要大约 10 分钟才能完成。 开发人员层用于测试和评估目的。 有关生产部署,请查看 Azure Bastion SKU 比较中的 SKU 选项。
更改 Srv-Work 网络接口的主要和辅助 DNS 地址
为了进行测试,请配置服务器的主要和辅助 DNS 地址。 这并不是一项常规的 Azure 防火墙要求。
在 Azure 门户菜单上,选择“资源组”或从任意页面搜索并选择“资源组”。 选择“Test-FW-RG”资源组。
选择 Srv-Work 虚拟机的网络接口。
在“设置”下,选择“DNS 服务器”。
在“DNS 服务器”下,选择“自定义”。
配置以下 DNS 服务器:
DNS 服务器 值 主要 209.244.0.3 次级 209.244.0.4 选择“保存”。
重启 Srv-Work 虚拟机。
测试防火墙
现在测试防火墙,以确认它是否按预期方式工作。
将远程桌面连接到防火墙公共 IP 地址,并登录到“Srv-Work”虚拟机。
打开 Internet Explorer 并浏览到
https://www.qq.com。在 Internet Explorer 安全警报中,请选择确定关闭。
您应该看到 QQ 主页。
浏览到
https://www.microsoft.com。防火墙应该会阻止你。
现已验证防火墙规则可正常工作:
- 可以使用 Bastion 和 SSH 连接到虚拟机。
- 可以浏览到一个允许的 FQDN,但不能浏览到其他任何 FQDN。
- 可以使用配置的外部 DNS 服务器解析 DNS 名称。
清理资源
可保留防火墙资源来继续测试。如果不再需要,请删除 Test-FW-RG 资源组,以删除与防火墙相关的所有资源。