已验证的 X.509 证书颁发机构(CA)证书是一种 CA 证书,该证书已上传并注册到您的预配服务,然后通过该服务自动或通过所有权证明进行验证。
使用注册组时,验证的证书起着重要作用。 通过确保证书上传者拥有证书的私钥,验证证书所有权可提供额外的安全层。 验证可防止恶意参与者嗅探流量,提取中间证书并使用该证书在自己的预配服务中创建注册组,从而有效劫持设备。 通过证明证书链中根证书或中间证书的所有权,可以证明你有权为注册为该注册组的一部分的设备生成叶证书。 因此,注册组中配置的根证书或中间证书必须是已验证的证书,或者必须汇总到设备在向服务进行身份验证时提供的证书链中已验证的证书。 若要了解有关 X.509 证书证明的详细信息,请参阅 X.509 证书证明。
先决条件
在开始本文中的步骤之前,请准备好以下先决条件:
- 在 Azure 订阅中创建的 DPS 实例。
- .cer或 .pem 证书文件。
通过自签名自动验证中间 CA 或根 CA
如果您使用的是信任的中级或根CA,并且了解您对该证书拥有全部所有权,则可以自行声明确认您已验证该证书。
若要添加自动验证的证书,请执行以下步骤:
在 Azure 门户中,导航到预配服务,然后从左侧菜单中选择 “证书 ”。
选择 “添加” 以添加新证书。
输入证书的友好显示名称。
浏览到表示 X.509 证书的公共部分的 .cer 或 .pem 文件。 选择“上传”。
选中“在上传时将证书状态设置为已验证”旁边的复选框。
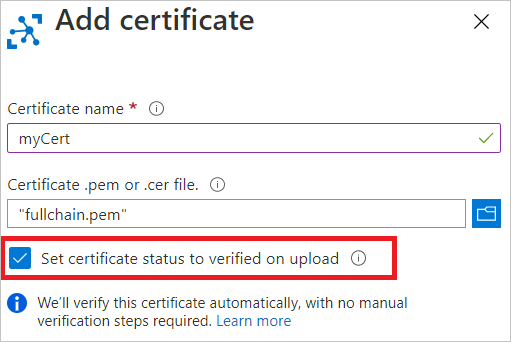
选择“保存”。
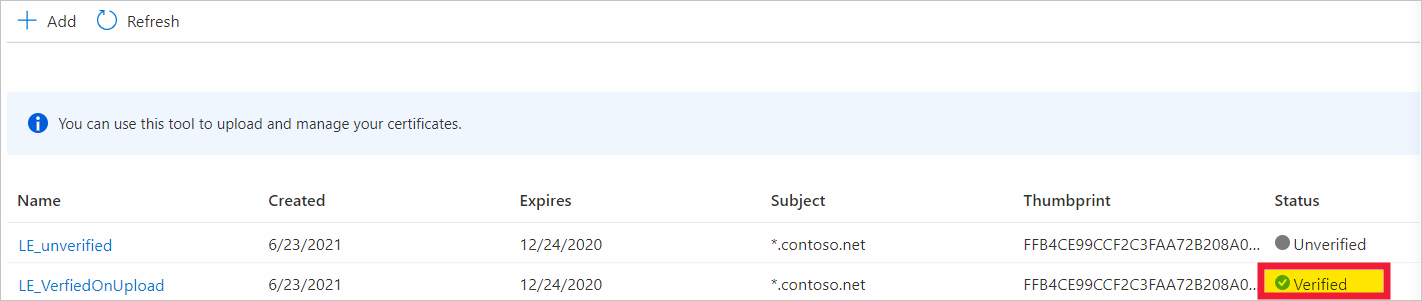
证书显示在“证书”选项卡中,状态 为“已验证”。
手动验证中间证书颁发机构或根证书颁发机构
将新的中间证书或根 CA 证书上传到 DPS 时,建议自动验证。 但是,如果在您的 IoT 场景中适用,仍可以执行占有证明。
所有权证明涉及以下步骤:
- 获取预配服务为 X.509 CA 证书生成的唯一验证码。 可以从 Azure 门户执行此步骤。
- 使用验证码作为使用者创建 X.509 验证证书,并使用与 X.509 CA 证书关联的私钥对证书进行签名。
- 将签名的验证证书上传到服务。 该服务使用要验证的 CA 证书的公共部分来验证验证证书,从而证明你拥有 CA 证书的私钥。
注册 X.509 证书的公共部分并获取验证码
若要将 CA 证书注册到预配服务,并获取可在所有权证明期间使用的验证码,请执行以下步骤。
在 Azure 门户中,导航到预配服务,然后从左侧菜单中打开 证书 。
选择 “添加” 以添加新证书。
在 “证书名称 ”字段中输入证书的友好显示名称。
选择文件夹图标,然后浏览到表示 X.509 证书公共部分的 .cer 或 .pem 文件。 选择打开。
收到成功上传证书的通知后,选择“ 保存”。
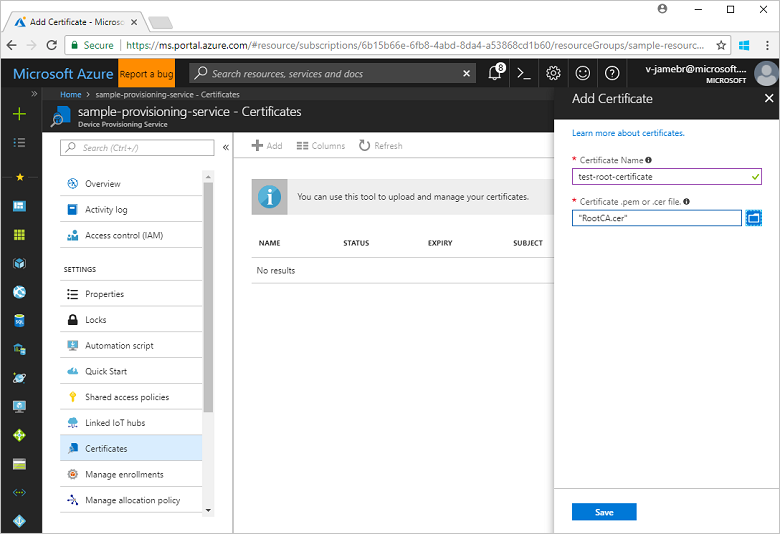
证书显示在 “证书资源管理器” 列表中。 此证书的状态为 “未验证”。
选择在上一步骤中添加的证书,打开其详细信息。
在证书详细信息中,请注意“验证码”字段为空。 选择“ 生成验证码 ”按钮。
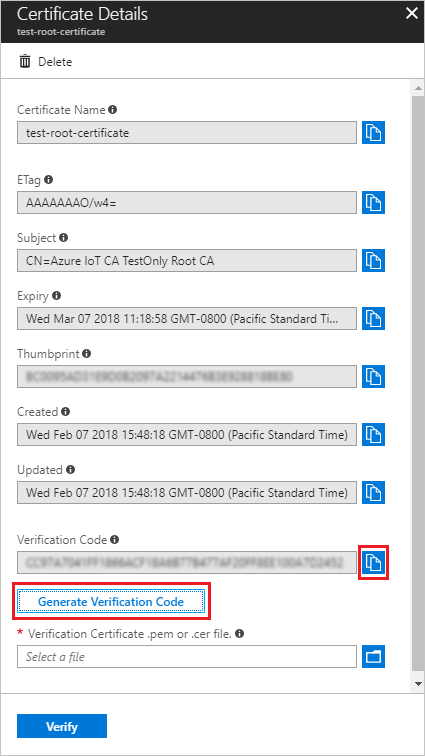
预配服务将创建一个 验证码 ,可用于验证证书所有权。 将代码复制到剪贴板。
对验证码进行数字签名以创建验证证书
现在,需要使用与 X.509 CA 证书关联的私钥(生成签名)对 DPS 中的验证码进行签名。 此步骤称为 所有权证明 ,并导致签名验证证书。
Azure 提供了有助于创建签名验证证书的工具和示例:
- Azure IoT 中心 C SDK 提供 PowerShell(Windows)和 Bash (Linux) 脚本,可帮助你创建 CA 和叶证书进行开发,并使用验证码执行所有权证明。 可以将与系统相关的 文件 下载到工作文件夹,并按照 “管理测试 CA 证书”中的说明,获取示例和教程自述文件 以对 CA 证书执行所有权证明。
- Azure IoT 中心 C# SDK 包含组证书验证示例,可用于执行所有权证明。
文档和 SDK 中提供的 PowerShell 和 Bash 脚本依赖于 OpenSSL。 还可以使用 OpenSSL 或其他第三方工具来帮助执行所有权证明。
上传签名的验证证书
将生成的签名作为验证证书上传到 Azure 门户中的预配服务。
在 Azure 门户上的证书详细信息中,从中复制验证码,选择“验证证书 .pem 或 .cer 文件”字段旁边的文件夹图标。 从系统浏览到已签名的验证证书,然后选择“ 打开”。
成功上传证书后,选择“ 验证”。 证书的状态将更改为“证书”列表中的“已验证”。 如果未自动更新,请选择“ 刷新 ”。
后续步骤
- 若要了解如何使用门户创建注册组,请参阅 在 Azure 门户中管理设备注册。
- 若要了解如何使用服务 SDK 创建注册组,请参阅 以编程方式创建用于 X.509 证书证明的设备预配服务注册组。