适用于:![]() IoT Edge 1.5
IoT Edge 1.5
重要
IoT Edge 1.5 LTS 是受支持的版本。 IoT Edge 1.4 LTS 的生命周期结束日期为 2024 年 11 月 12 日。 如果你使用的是较低的版本,请参阅更新 IoT Edge。
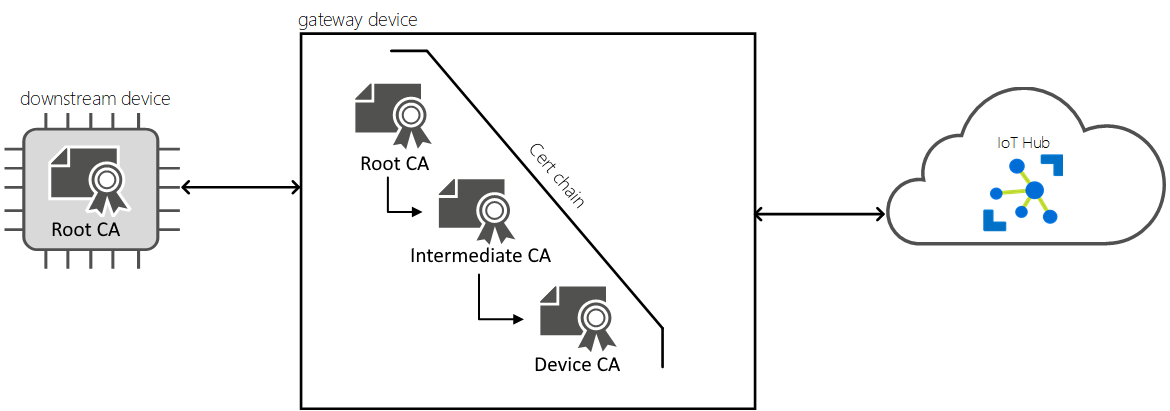
本文提供有关在下游设备和 IoT Edge 透明 网关之间设置受信任连接的说明。 在透明网关方案中,一个或多个设备通过维护与 IoT 中心连接的单个网关设备发送消息。 在本文中,术语 网关 和 IoT Edge 网关 是指配置为透明网关的 IoT Edge 设备。
备注
下游设备将数据直接发送到互联网或网关设备(支持 IoT Edge 或不支持)。 子设备可以是下游设备,也可以是嵌套拓扑中的网关设备。
可通过三个步骤设置透明网关连接。 本文介绍第三个步骤。
将网关设备配置为服务器,以便下游设备可以安全地连接到它。 设置网关以接收来自下游设备的消息,并将其路由到正确的目标。 有关这些步骤,请参阅配置 IoT Edge 设备以充当透明网关。
为下游设备创建设备标识,以便它可以通过 IoT 中心进行身份验证。 配置下游设备,使其通过网关设备发送消息。 有关这些步骤,请参阅向 Azure IoT 中心验证下游设备。
将下游设备连接到网关设备,然后开始发送消息。
本文介绍下游设备连接组件,例如:
- 传输层安全性(TLS)和证书基础知识
- 跨不同作系统工作的 TLS 库,以不同的方式处理证书
你使用首选语言浏览 Azure IoT 示例,使设备能够将消息发送到网关。
提供以下各项以准备好下游设备:
一个下游设备。
该设备可以是任何在 Azure IoT 中心创建了标识的应用程序或平台。 在许多情况下,应用程序使用 Azure IoT 设备 SDK。 下游设备也可以是 IoT Edge 网关设备上运行的应用程序。
稍后,本文介绍如何将 IoT 设备作为下游设备进行连接。 如果要将 IoT Edge 设备用作下游设备,请参阅将 Azure IoT Edge 设备连接在一起以创建层次结构(嵌套边缘)。
一个根 CA 证书。
此文件用于在 配置 IoT Edge 设备以充当透明网关时生成 Edge CA 证书,并在下游设备上可用。
下游设备使用此证书检查网关设备的标识。 此受信任证书将验证与网关设备的传输层安全性 (TLS) 连接。 有关使用情况详细信息,请参阅 提供根 CA 证书。
已修改的指向网关设备的连接字符串。
若要了解如何更改连接字符串,请参阅 向 Azure IoT 中心对下游设备进行身份验证。
备注
已向 IoT 中心注册的 IoT 设备可以使用模块孪生在单个设备上隔离不同的进程、硬件或函数。 IoT Edge 网关支持使用对称密钥身份验证的下游模块连接,但不支持 X.509 证书身份验证。
将下游设备安全连接到 IoT Edge 所存在的难题就如同通过 Internet 进行其他任何客户端/服务器安全通信。 客户端和服务器使用传输层安全性 (TLS) 通过 Internet 安全通信。 TLS 是使用称作“证书”的标准公钥基础结构 (PKI) 构造生成的。 TLS 是一种相当复杂的规范,阐述了与保护两个终结点相关的各种主题。 本部分汇总了将设备安全连接到 IoT Edge 网关的相关概念。
当客户端连接到服务器时,服务器会显示一个称为 服务器证书链的证书链。 证书链通常具有根证书颁发机构(CA)证书、一个或多个中间 CA 证书和服务器的证书。 客户端通过加密方式验证整个服务器证书链来信任服务器。 此过程称为 服务器链验证。 客户端还要求服务器证明其具有服务器证书的私钥,称为 所有权证明。 服务器链验证和所有权证明一起称为 服务器身份验证。 若要验证服务器证书链,客户端需要用于颁发服务器的证书的根 CA 证书的副本。 连接到网站时,浏览器预配置了常见的 CA 证书,因此客户端过程是无缝的。
当某个设备连接到 Azure IoT 中心时,该设备为客户端,IoT 中心云服务为服务器。 IoT 中心云服务使用名为 Baltimore CyberTrust Root 的根 CA 证书,该证书公开可用且广泛使用。 由于 IoT 中心 CA 证书已在大多数设备上安装,因此许多 TLS 实现(OpenSSL、Schannel、LibreSSL)会在服务器证书验证期间自动使用它。 但是,连接到 IoT 中心的设备在连接到 IoT Edge 网关时可能会出现问题。
当某个设备连接到 IoT Edge 网关时,下游设备为客户端,网关设备为服务器。 Azure IoT Edge 允许根据需要生成网关证书链。 可以使用公共 CA 证书(如 Baltimore)或自签名(或内部)根 CA 证书。 公共 CA 证书通常具有成本,因此它们通常用于生产方案。 最好是使用自签名的 CA 证书进行开发和测试。 演示证书是自签名的根 CA 证书。
为 IoT Edge 网关使用自签名根 CA 证书时,需要将其安装到该网关或将其提供给连接到网关的所有下游设备。
若要详细了解 IoT Edge 证书和生产影响,请参阅 IoT Edge 证书使用情况详细信息。
若要验证网关设备的证书,下游设备需要提供自身的根 CA 证书副本。 如果使用 IoT Edge git 存储库中的脚本创建测试证书,则根 CA 证书称为 azure-iot-test-only.root.ca.cert.pem。
将此证书文件移动到下游设备上的任何目录(如果尚未这样做)。 通过在操作系统的证书存储中安装 CA 证书,或在使用 Azure IoT SDK 的应用程序中引用证书来移动该文件。
使用 Azure Key Vault 等服务或 安全复制协议 等工具移动证书文件。
将根 CA 证书复制到下游设备后,请确保连接到网关的应用程序可以访问证书。
在作系统的证书存储中安装根 CA 证书,以便大多数应用程序都可以使用它。 某些应用程序(如 Node.js)不使用 OS 证书存储,而是使用 Node 运行时的内部证书存储。 如果无法在操作系统级别安装证书,请转到“ 在 Azure IoT SDK 中使用证书”部分。
在 Ubuntu 或 Windows 上安装根 CA 证书。
使用以下命令在 Ubuntu 主机上安装 CA 证书。 此示例使用先决条件文章中的 azure-iot-test-only.root.ca.cert.pem 证书,并假定已将证书复制到下游设备上的某个位置。
sudo cp <file path>/azure-iot-test-only.root.ca.cert.pem /usr/local/share/ca-certificates/azure-iot-test-only.root.ca.cert.pem.crt
sudo update-ca-certificates
完成后,你将 在 /etc/ssl/certs 中看到更新证书...已添加 1,删除 0;完成 消息。
Azure IoT SDK 使用简单的示例应用程序连接到 IoT Edge 设备。 示例的目标是连接设备客户端并将设备遥测消息发送到网关,然后关闭连接并退出。
在使用应用程序级别的示例之前,请获取以下项:
从下游设备获取的 IoT 中心连接字符串,已修改为指向网关设备。
在 IoT 中心对下游设备进行身份验证所需的任何证书。 有关详细信息,请参阅在 Azure IoT 中心对下游设备进行身份验证。
已复制并保存在下游设备上某个位置的根 CA 证书的完整路径。
例如:
<file path>/azure-iot-test-only.root.ca.cert.pem。
现已准备好在以所选语言编写的示例中使用证书:
本部分提供用于将 Azure IoT Node.js 设备客户端连接到 IoT Edge 网关的示例应用程序。 对于 Node.js 应用程序,必须按如下所示在应用程序级别安装根 CA 证书。 Node.js 应用程序不使用系统的证书存储。
- 从适用于 Node.js 的 Azure IoT 设备 SDK 示例存储库获取 edge_downstream_device.js 的示例。
- 查看 readme.md 文件,确保满足运行该示例的所有先决条件。
- 在 edge_downstream_device.js 文件中,更新 connectionString 和 edge_ca_cert_path 变量。
- 参阅 SDK 文档,获取有关如何在设备上运行该示例的说明。
若要了解所运行的示例,请参阅以下代码片段,其中演示了客户端 SDK 如何读取证书文件,并使用它来建立安全的 TLS 连接:
// Provide the Azure IoT device client via setOptions with the X509
// Edge root CA certificate that was used to setup the Edge runtime
var options = {
ca : fs.readFileSync(edge_ca_cert_path, 'utf-8'),
};
在下游设备上运行此示例命令,测试它是否可以连接到网关设备:
openssl s_client -connect mygateway.contoso.com:8883 -CAfile <CERTDIR>/certs/azure-iot-test-only.root.ca.cert.pem -showcerts
此命令通过 MQTTS(端口 8883)检查连接。 如果使用其他协议,请调整 AMQPS(5671)或 HTTPS(443)的命令。
此命令的输出可能很长,并且包含有关链中所有证书的信息。 如果连接成功,您会看到一行类似于 Verification: OK 或 Verify return code: 0 (ok) 的信息。
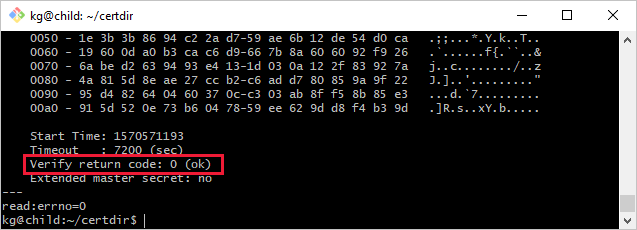
如果下游设备与其网关设备的连接不稳定,请考虑这些问题以帮助解决问题。
- 连接字符串中的网关主机名是否与网关设备上 IoT Edge 配置文件中的主机名值相同?
- 网关主机名能否解析为 IP 地址? 使用 DNS 或添加下游设备上的主机文件条目修复间歇性连接。
- 防火墙中是否打开了通信端口? 请确保在下游设备和透明 IoT Edge 设备之间打开所需的协议端口(MQTTS:8883、AMQPS:5671、HTTPS:433)。
了解 IoT Edge 如何将 脱机功能 扩展到下游设备。