本文内容
适用于:![]() IoT Edge 1.5
IoT Edge 1.5
重要
IoT Edge 1.5 LTS 是受支持的版本。 IoT Edge 1.4 LTS 的生命周期结束日期为 2024 年 11 月 12 日。 如果你使用的是较低的版本,请参阅更新 IoT Edge。
本文提供了将 IoT Edge 设备配置为透明网关的详细说明,以便其他设备可以连接到 IoT 中心。 在本文中, IoT Edge 网关 表示配置为透明网关的 IoT Edge 设备。 有关详细信息,请参阅如何将 IoT Edge 设备用作网关。
备注
下游设备不能使用文件上传。
设置透明网关连接有三个主要步骤。 本文介绍其中的第一个步骤:
- 将网关设备配置为服务器,以便下游设备可以安全地连接。 设置网关以接收来自下游设备的消息,并将其路由到正确的目标。
- 为下游设备创建设备标识,以便它可以通过 IoT 中心进行身份验证。 配置下游设备,使其通过网关设备发送消息。 有关这些步骤,请参阅向 Azure IoT 中心验证下游设备。
- 将下游设备连接到网关设备并开始发送消息。 有关这些步骤,请参阅将下游设备连接到 Azure IoT Edge 网关。
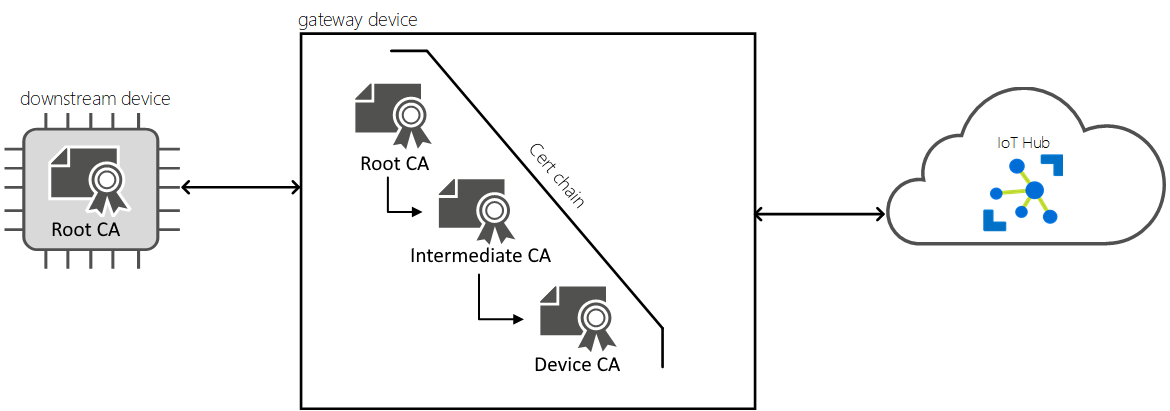
若要充当网关,设备需要安全地连接到其下游设备。 Azure IoT Edge 允许使用公钥基础结构(PKI)在设备之间设置安全连接。 在这种情况下,下游设备连接到充当透明网关的 IoT Edge 设备。 为了确保安全,下游设备会检查网关设备的标识。 此检查有助于防止设备连接到恶意网关。
下游设备可以是任何在 Azure IoT Hub 中创建标识的应用程序或平台。 这些应用程序通常使用 Azure IoT 设备 SDK。 下游设备甚至可以是 IoT Edge 网关设备本身上运行的应用程序。
可以创建任何启用设备网关拓扑所需的信任的证书基础结构。 本文使用与 IoT 中心 中的 X.509 CA 安全性 相同的证书设置。 此设置使用与特定 IoT 中心(即 IoT 中心根 CA)相关联的 X.509 CA 证书、一系列用此 CA 签名的证书以及用于 IoT Edge 设备的 CA。
备注
在这些文章中使用的术语“根 CA 证书”是指 PKI 证书链最顶层的颁发机构公共证书,而不一定是联合证书颁发机构的证书根。 在许多情况下,它实际上是中间 CA 公共证书。
按照以下步骤创建证书,并将其安装在网关上的正确位置。 使用任何计算机生成证书,然后将其复制到 IoT Edge 设备。
需要安装了 IoT Edge 的 Linux 或 Windows 设备。
如果尚未准备好设备,请在 Azure 虚拟机中创建一个设备。 按照将第一个 IoT Edge 模块部署到虚拟 Linux 设备中的步骤,创建一个 IoT 中心、创建一个虚拟机并配置 IoT Edge 运行时。
所有 IoT Edge 网关上都需要安装 Edge CA 证书。 IoT Edge 安全守护程序使用 Edge CA 证书为工作负载 CA 证书签名,而工作负载 CA 证书又为 IoT Edge 中心的服务器证书签名。 在连接启动期间,网关将其服务器证书提供给下游设备。 下游设备将进行检查,确保服务器证书是汇总到根 CA 证书的证书链的一部分。 此过程允许下游设备确认网关是否来自受信任的源。 有关详细信息,请参阅了解 Azure IoT Edge 如何使用证书。
根 CA 证书和 Edge CA 证书(其私钥)必须位于 IoT Edge 网关设备上,并在 IoT Edge 配置文件中设置。 在这种情况下, 根 CA 证书 表示此 IoT Edge 方案的顶级证书颁发机构。 网关 Edge CA 证书和下游设备证书必须汇总到相同的根 CA 证书。
提示
在 IoT Edge 设备上安装根 CA 证书和 Edge CA 证书的过程也在管理 IoT Edge 设备上的证书中进行了更详细的介绍。
准备好以下文件:
- 根 CA 证书
- Edge CA 证书
- 设备 CA 私钥
对于生产方案,请使用自己的证书颁发机构生成这些文件。 对于开发和测试方案,可以使用演示证书。
如果没有自己的证书颁发机构,并且想要使用演示证书,请按照创建演示证书来测试 IoT Edge 设备功能中的说明来创建文件。 在该页上,按照以下步骤进行操作:
- 设置用于在设备上生成证书的脚本。
- 创建根 CA 证书。 最后,你有一个根 CA 证书文件
<path>/certs/azure-iot-test-only.root.ca.cert.pem。 - 创建 Edge CA 证书。 最后,你有一个 Edge CA 证书
<path>/certs/iot-edge-device-ca-<cert name>-full-chain.cert.pem及其私钥<path>/private/iot-edge-device-ca-<cert name>.key.pem。
检查该证书是否符合格式要求。
如果在其他计算机上创建了证书,请将其复制到 IoT Edge 设备。 使用 USB 驱动器、 Azure Key Vault 等服务或 安全文件复制等命令。
将文件移动到证书和密钥的首选目录:
/var/aziot/certs证书和/var/aziot/secrets密钥。创建证书和密钥目录并设置权限。 将证书和密钥存储在首选
/var/aziot目录中:/var/aziot/certs用于证书和/var/aziot/secrets密钥。# If the certificate and keys directories don't exist, create, set ownership, and set permissions sudo mkdir -p /var/aziot/certs sudo chown aziotcs:aziotcs /var/aziot/certs sudo chmod 755 /var/aziot/certs sudo mkdir -p /var/aziot/secrets sudo chown aziotks:aziotks /var/aziot/secrets sudo chmod 700 /var/aziot/secrets更改证书和密钥的所有权和权限。
# Give aziotcs ownership to certificates # Read and write for aziotcs, read-only for others sudo chown -R aziotcs:aziotcs /var/aziot/certs sudo find /var/aziot/certs -type f -name "*.*" -exec chmod 644 {} \; # Give aziotks ownership to private keys # Read and write for aziotks, no permission for others sudo chown -R aziotks:aziotks /var/aziot/secrets sudo find /var/aziot/secrets -type f -name "*.*" -exec chmod 600 {} \;
在 IoT Edge 设备上,打开配置文件:
/etc/aziot/config.toml。 如果在 Windows 上使用 IoT Edge for Linux,请使用Connect-EflowVmPowerShell cmdlet 连接到 EFLOW 虚拟机。提示
如果设备上尚不存在配置文件,则使用
/etc/aziot/config.toml.edge.template作为模板来创建一个。查找
trust_bundle_cert参数。 取消注释此行,并为设备上的根 CA 证书文件提供文件 URI。找到文件的
[edge_ca]节。 取消注释此部分中的三行,并将证书和密钥文件的文件 URI 作为以下属性的值提供:- 证书:Edge CA 证书
- pk:设备 CA 私钥
保存并关闭该文件。
单击“应用”以应用更改。
sudo iotedge config apply
下游设备将遥测和消息发送到网关设备,其中 IoT Edge 中心模块将信息路由到其他模块或 IoT 中心。 若要为此功能准备网关设备,请确保:
IoT Edge 中心模块已部署到设备。
在设备上安装 IoT Edge 时,仅自动启动一个系统模块:IoT Edge 代理。 为设备创建第一个部署时,第二个系统模块和 IoT Edge 中心也会启动。 如果 edgeHub 模块未在设备上运行,请为设备创建一个部署。
IoT Edge 中心模块设置了路由,用于处理来自下游设备的传入消息。
网关设备需要路由来处理来自下游设备的消息,否则这些消息将无法被处理。 可以将消息发送到网关设备上的模块,也可以直接发送到 IoT 中心。
若要部署 IoT Edge 中心模块并配置路由以处理来自下游设备的传入消息,请执行以下步骤:
在 Azure 门户中,转到 IoT 中心。
转到“设备管理”菜单下的“设备”,然后选择要用作网关的 IoT Edge 设备。
选择“设置模块” 。
在“ 模块 ”页上,添加要部署到网关设备的任何模块。 本文重点介绍如何配置和部署 edgeHub 模块,无需在此页上显式设置该模块。
在完成时选择“下一步:路由”。
在“ 路由 ”页上,确保有一个路由来处理来自下游设备的消息。 例如:
将所有消息(无论是来自模块还是来自下游设备)发送到 IoT 中心的路由:
-
名称:
allMessagesToHub -
值:
FROM /messages/* INTO $upstream
-
名称:
将来自所有下游设备的全部消息发送到 IoT 中心的路由:
-
名称:
allDownstreamToHub -
值:
FROM /messages/* WHERE NOT IS_DEFINED ($connectionModuleId) INTO $upstream
该路由之所以有效,是因为与来自 IoT Edge 模块的消息不同,来自下游设备的消息没有与之关联的模块 ID。 使用路由的 WHERE 子句可以筛选出具有该系统属性的任何消息。
有关消息路由的详细信息,请参阅部署模块和建立路由。
-
名称:
创建您的路由或路由后,选择“查看+创建”。
在“查看 + 创建”页面上,选择“创建”。
标准 IoT Edge 设备不需要任何入站连接便可工作,因为与 IoT 中心之间的所有通信都是通过出站连接执行的。 网关设备则不同,因为它们需要从其下游设备接收消息。 如果下游设备与网关设备之间有防火墙,则也需要能够通过防火墙进行通信。
为了使网关方案能够正常工作,必须在 IoT Edge 中心至少为来自下游设备的入站流量打开一个受支持的协议。 受支持的协议包括 MQTT、AMQP、HTTPS、基于 WebSocket 的 MQTT 和基于 Websocket 的 AMQP。
| 端口 | 协议 |
|---|---|
| 8883 | MQTT |
| 5671 | AMQP(高级消息队列协议) |
| 443 | HTTPS MQTT+WS AMQP+WS |
将 IoT Edge 设备设置为透明网关后,请设置下游设备以信任网关并向其发送消息。 继续阅读在 Azure IoT 中心对下游设备进行身份验证,以了解设置透明网关方案的后续步骤。