Azure 密钥保管库证书支持适用于 X.509 证书管理,它提供以下行为:
允许证书所有者通过密钥保管库创建过程或通过导入现有证书来创建证书。 导入的证书包括自签名证书和证书颁发机构 (CA) 生成的证书。
允许密钥保管库证书所有者在不与私钥材料交互的情况下实现 X.509 证书的安全存储和管理。
允许证书所有者创建策略来指示密钥保管库如何管理证书的生命周期。
允许证书所有者提供联系信息用于接收有关证书过期和续订生命周期事件的通知。
支持在选定的颁发者处自动续订:密钥保管库合作伙伴 X.509 证书提供者和 CA。
注意
也允许在非合作的提供者和颁发机构处续订,但不支持自动续订。
有关证书创建的详细信息,请参阅证书创建方法。
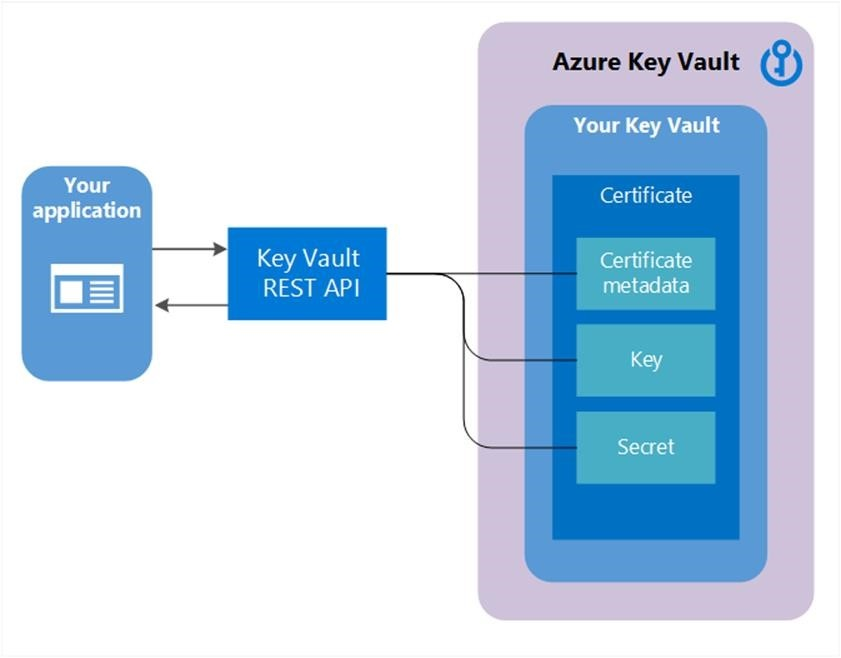
证书的组成部分
创建 Key Vault 证书后,还可以创建具有相同名称的可寻址密钥和机密。 密钥保管库密钥允许密钥操作,密钥保管库机密允许将证书值检索为机密。 密钥保管库证书还包含公共 X.509 证书元数据。
证书的标识符和版本与密钥和机密的类似。 使用 Key Vault 证书版本创建的特定版本的可寻址密钥和机密可用于 Key Vault 证书响应。
可导出或不可导出的密钥
创建 Key Vault 证书后,可以使用 PFX 或 PEM 格式的私钥从可寻址机密中检索该证书。 用于创建证书的策略必须指示密钥可导出。 如果策略指示密钥不可导出,则在作为机密检索私钥时,该私钥不包括在值中。
使用不可导出的 Key Vault 证书时,可寻址密钥变得更相关。 可寻址密钥保管库密钥的操作从用于创建密钥保管库证书的密钥保管库证书策略的 keyusage 字段进行映射。
有关支持的密钥类型的完整列表,请参阅 “关于密钥:密钥类型和保护方法”。 仅允许 RSA 和 EC 使用可导出密钥。 HSM 密钥不可导出。
证书属性和标记
除了证书元数据、可寻址密钥和可寻址机密外,密钥保管库证书还包含属性和标记。
属性
证书属性将镜像到创建密钥保管库证书时创建的可寻址密钥和机密的属性。
密钥保管库证书具有以下属性:
enabled:此布尔属性是可选的。 默认值为true。 可以指定此属性,以指示证书数据是否可以作为机密进行检索,或者可以作为密钥进行操作。当操作发生在
nbf和exp之间时,该属性还与nbf和exp结合使用,但前提是将enabled设置为true。nbf和exp时段外的操作会自动禁止。
响应包含以下附加只读属性:
-
created:IntDate指示创建此版本的证书的时间。 -
updated:IntDate指示更新此版本的证书的时间。 -
exp:IntDate包含 X.509 证书的过期日期值。 -
nbf:IntDate包含 X.509 证书的“不早于”日期值。
注意
如果密钥保管库证书过期,仍可以检索该证书,但在需要验证证书是否过期的 TLS 保护等情况下,证书可能无法使用。
Tags
证书的标记是客户端指定的键/值对字典,非常类似于密钥和机密中的标记。
注意
如果调用方具有该对象类型(密钥、机密或证书)的列出或获取权限,则该调用方可以读取标记。
证书策略
证书策略包含有关如何创建和管理密钥保管库证书生命周期的信息。 将具有私钥的证书导入密钥保管库时,密钥保管库服务将通过读取 X.509 证书创建一个默认策略。
从零开始创建 Key Vault 证书时,需要提供策略。 该策略指定如何创建此密钥保管库证书版本或下一个密钥保管库证书版本。 建立策略后,便不需要使用连续创建操作创建将来的版本。 所有版本的 Key Vault 证书只有一个策略实例。
在高级别,证书策略包含以下信息:
X.509 证书属性,包括使用者名称、使用者备用名称以及用于创建 X.509 证书请求的其他属性。
键属性,包括密钥类型、密钥长度、可导出字段和
ReuseKeyOnRenewal字段。 这些字段指示密钥保管库如何生成密钥。支持的密钥类型 包括 RSA、RSA-HSM、EC、EC-HSM 和 oct。
机密属性,例如可寻址机密的内容类型,用于生成机密值以将证书作为机密检索。
密钥保管库证书的生存期操作。 每个生存期操作包含:
- 触发器:指定为过期前的天数或剩余生存期百分比。
- 操作:
emailContacts或autoRenew。
有关用于颁发 X.509 证书的证书颁发者的参数。
与策略关联的属性。
有关详细信息,请参阅 Set-AzKeyVaultCertificatePolicy。
将 X.509 用法映射到密钥操作
下表表示 X.509 密钥用法策略映射到在创建密钥保管库证书过程中创建的密钥的有效密钥操作。
| X.509 密钥使用情况标记 | Key Vault 密钥操作 | 默认行为 |
|---|---|---|
DataEncipherment |
encrypt,decrypt |
不适用 |
DecipherOnly |
decrypt |
不适用 |
DigitalSignature |
sign,verify |
Key Vault 在创建证书时默认为无使用规范 |
EncipherOnly |
encrypt |
不适用 |
KeyCertSign |
sign,verify |
不适用 |
KeyEncipherment |
wrapKey,unwrapKey |
Key Vault 在创建证书时默认为无使用规范 |
NonRepudiation |
sign,verify |
不适用 |
crlsign |
sign,verify |
不适用 |
证书颁发者
密钥保管库证书对象包含与所选证书颁发者提供者进行通信的配置以订购 X.509 证书。
密钥保管库合作伙伴,具有 TLS/SSL 证书的以下证书颁发者提供者。
| 提供程序名称 | 位置 |
|---|---|
| DigiCert | 公有云中所有 Key Vault 服务位置均受支持 |
| GlobalSign | 公有云中所有 Key Vault 服务位置均受支持 |
在 Key Vault 中创建证书颁发者之前,管理员必须执行以下先决条件步骤:
加入至少具有一个 CA 提供者的组织。
为密钥保管库创建请求者凭据以注册(和续订)TLS/SSL 证书。 此步骤提供用于在密钥保管库中创建提供者颁发者对象的配置。
有关从证书门户创建颁发者对象的详细信息,请参阅密钥保管库团队博客。
密钥保管库允许使用其他颁发者提供者的配置创建多个颁发者对象。 创建颁发者对象后,可以在一个或多个证书的策略中引用其名称。 在创建和续订证书的过程中从 CA 提供者请求 X.509 证书时,引用颁发者对象可以指示密钥保管库按颁发者对象中的规定使用配置。
颁发者对象是在保管库中创建的。 它们只能与同一保管库中的密钥保管库证书一起使用。
注意
在注册期间,公开受信任的证书将发送到 Azure 边界之外的 CA 和证书透明度 (CT) 日志。 它们受这些实体的 GDPR 策略保护。
证书联系人
证书联系人包含用于发送证书生存期事件触发的通知的联系人信息。 密钥保管库中的所有证书共享这些联系人信息。
如果保管库中的任何证书发生事件,所有指定联系人都会收到通知。 有关如何设置证书联系人的信息,请参阅续订 Azure 密钥保管库证书。
证书访问控制
密钥保管库管理证书的访问控制。 包含这些证书的密钥保管库提供访问控制。 针对证书的访问控制策略不同于针对同一密钥保管库中密钥和机密的访问控制策略。
用户可以创建一个或多个保管库来保存证书,以维护适用于方案的证书分段和管理。 有关详细信息,请参阅证书访问控制。
证书用例
安全通信和身份验证
TLS 证书可以帮助加密通过 Internet 进行的通信并建立网站标识。 这种加密可以提高入口点和通信模式的安全性。 此外,由公共 CA 签名的链式证书可以帮助验证持有证书的实体是否合法。
例如,下面是使用证书来保护通信和实现身份验证的一些用例:
- Intranet/Internet 网站:保护对 Intranet 站点的访问,并确保使用 TLS 证书来加密通过 Internet 进行的数据传输。
- IoT 和网络设备:通过使用证书进行身份验证和通信来保护设备。
- 云/多云方案:保护本地、跨云或云提供商租户中的基于云的应用程序。