Azure Key Vault 支持存储任何证书颁发机构 (CA) 颁发的数字证书。 它支持使用私钥/公钥对创建证书签名请求 (CSR)。 CSR 可以由任何 CA(内部企业 CA 或外部公共 CA)签名。 证书签名请求 (CSR) 是你发送给 CA 以请求数字证书的消息。
若要详细了解证书的常规信息,请参阅 Azure Key Vault 证书。
如果没有 Azure 订阅,请在开始前创建一个试用版订阅。
在 Key Vault 中添加合作 CA 颁发的证书
Key Vault 与以下证书颁发机构合作,以简化证书的创建。
| 提供程序 | 证书类型 | 配置设置 |
|---|---|---|
| DigiCert | Key Vault 提供 DigiCert 的 OV 或 EV SSL 证书 | 集成指南 |
| GlobalSign | Key Vault 提供 GlobalSign 的 OV 或 EV SSL 证书 | 集成指南 |
在 Key Vault 中添加非合作 CA 颁发的证书
请按照以下步骤添加来自未与 Key Vault 合作的 CA 的证书。 (例如,GoDaddy 不是受信任的 Key Vault CA。)
转到要向其添加证书的密钥保管库。
在“属性”页上,选择“证书”。
选择“生成/导入”选项卡。
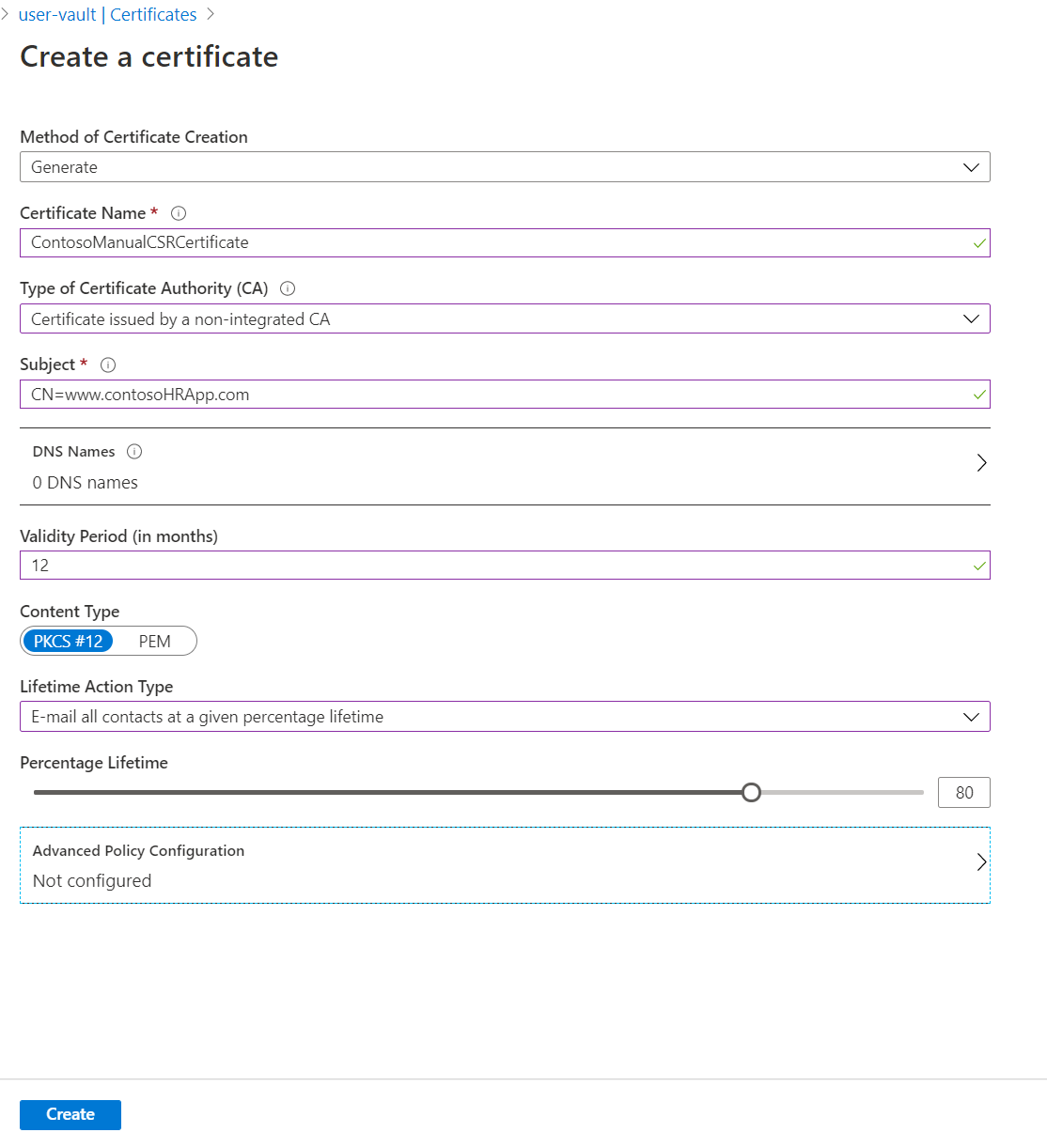
在“创建证书”屏幕上,选择以下值:
- 证书创建方法:生成。
- 证书名称:ContosoManualCSRCertificate。
- 证书颁发机构 (CA) 类型:非集成 CA 颁发的证书。
- 使用者:。
注意
如果使用在值中具有逗号 (,) 的相对可分辨名称 (RDN),请将包含特殊字符的值括在双引号中。
“使用者”的示例条目:
在本示例中,RDN
OU包含在名称中有逗号的值。OU生成的输出是“Docs, Contoso”。根据需要选择“其他值”,然后选择“创建”,将证书添加到“证书”列表 。
在“证书”列表中,选择该新证书。 证书的当前状态为“已禁用”,因为它尚未由 CA 颁发。
在“证书操作”选项卡上,选择“下载 CSR” 。
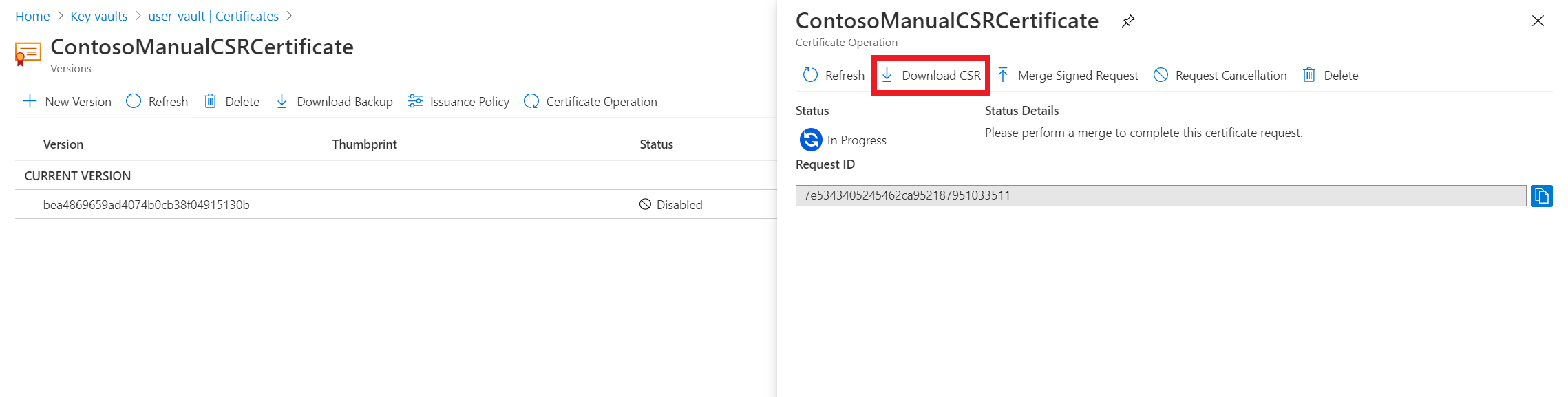
让 CA 为 CSR (.csr) 签名。
对请求签名后,在“证书操作”选项卡上选择“合并已签名的请求”,以将已签名的证书添加到 Key Vault 。
现已成功合并证书请求。
向 CSR 添加更多信息
若要在创建 CSR 时添加更多信息,请在“SubjectName”中定义它。 你可能希望添加以下信息:
- 区域
- 城市/区域
- 省/自治区/直辖市
- 组织
- 组织单位
示例
SubjectName="CN = learn.microsoft.com, OU = Microsoft Corporation, O = Microsoft Corporation, L = Redmond, S = WA, C = US"
注意
如果你请求的是带有其他信息的域验证 (DV) 证书,则 CA 如果无法验证请求中的所有信息,则可能会拒绝该请求。 如果你请求组织验证 (OV) 证书,则这些附加信息可能更合适。
常见问题解答
如何监视或管理我的 CSR?
请参阅监视和管理证书创建。
如果出现此情况该怎么办 - 错误类型“指定的 X.509 证书内容中最终实体证书的公钥与指定私钥的公共部分不一致。请检查证书是否有效”?
如果未将已签名的 CSR 与启动的同一 CSR 请求合并,则会发生此错误。 创建的每个新 CSR 都有一个私钥,当你合并已签名的请求时,该私钥必须匹配。
当 CSR 合并时,它会合并整个链吗?
是的,它会合并整个链,前提是用户返回 p7b 文件进行合并。
如果颁发的证书在 Azure 门户中处于禁用状态怎么办?
查看“证书操作”选项卡以查看该证书的错误消息。
如果出现此情况该怎么办 - 错误类型“提供的使用者名称不是有效的 X500 名称”?
如果“SubjectName”包含任何特殊字符,则可能发生此错误。 请参阅 Azure 门户和 PowerShell 说明中的注释。
错误类型“已使用用于获取证书的 CSR。请尝试使用新的 CSR 生成新证书”。转到证书的“高级策略”部分,检查是否关闭了“续订时重用密钥”选项。