虚拟网络安全组流日志记录是 Azure 网络观察程序的一项功能,可用于记录有关流经 Azure 虚拟网络的 IP 流量的信息。 有关虚拟网络流日志记录的详细信息,请参阅 虚拟网络流日志。
本教程可帮助你使用 VNet 流日志来记录流经虚拟网络的虚拟机网络流量。
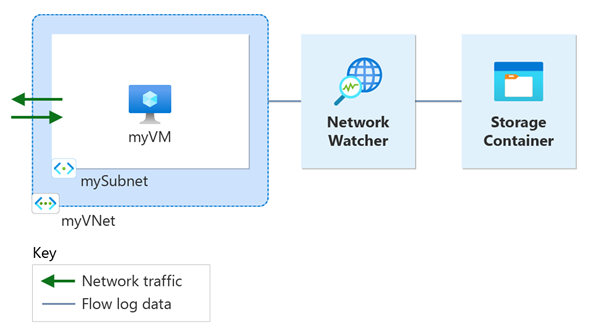
本教程中,您将学习如何:
- 创建虚拟网络
- 创建虚拟机
- 注册 Microsoft.insights 提供程序
- 使用网络观察程序流日志为虚拟网络启用流日志记录
- 下载记录的数据
- 查看记录的数据
先决条件
- 拥有有效订阅的 Azure 帐户。 如果没有 Azure 订阅,请在开始之前创建一个试用版订阅。
创建虚拟网络
在本部分中,将为虚拟机创建包含一个子网的 myVNet 虚拟网络。
登录到 Azure 门户。
在门户顶部的搜索框中,输入 虚拟网络。 从搜索结果中选择 虚拟网络 。
选择+ 新建。 在 “创建虚拟网络”中,在 “基本信息 ”选项卡中输入或选择以下值:
设置 价值 项目详细信息 Subscription 选择 Azure 订阅。 资源组 选择“新建”。
在名称中输入 myResourceGroup。
选择“确定”。实例详细信息 Name 输入 myVNet。 区域 选择 “(亚太)中国东部”。 选择“查看 + 创建”。
检查设置,然后选择创建。
创建虚拟机
在本部分中,将创建 myVM 虚拟机。
在门户顶部的搜索框中,输入 虚拟机。 从搜索结果中选择 虚拟机 。
选择 “+ 创建 ”,然后选择 “虚拟机”。
在 “创建虚拟机”中,在 “基本信息 ”选项卡中输入或选择以下值:
设置 价值 项目详细信息 Subscription 选择 Azure 订阅。 资源组 选择 myResourceGroup。 实例详细信息 虚拟机名称 输入 myVM。 区域 选择 “(亚太)中国东部”。 可用性选项 选择 “不需要基础结构冗余”。 安全类型 选择 “标准”。 图像 选择你喜欢的图像。 本教程使用 Windows Server 2022 Datacenter:Azure Edition - x64 Gen2。 尺寸 选择 VM 大小或保留默认设置。 管理员帐户 用户名 输入用户名。 密码 输入密码。 确认密码 重新输入密码。 选择“ 网络 ”选项卡,或依次选择“ 下一步:磁盘”、“ 下一步:网络”。
在“网络”选项卡中,选择以下值:
设置 价值 网络接口 虚拟网络 选择 myVNet。 子网 选择 mySubnet。 公共 IP 选择 (新建)myVM-ip。 NIC 网络安全组 选择 “基本”。 公共入站端口 选择 “允许选择的端口”。 选择入站端口 选择 RDP (3389)。 注意
建议仅将 RDP 端口打开到 Internet 进行测试。 对于生产环境,建议将 RDP 端口的访问限制为特定的 IP 地址或 IP 地址范围。 还可以阻止 Internet 访问 RDP 端口,并使用 Azure Bastion 从 Azure 门户安全地连接到虚拟机。
选择“查看 + 创建”。
检查设置,然后选择创建。
部署完成后,选择“转到资源”以转到 myVM 的“概述”页。
选择 “连接 ”,然后选择 “RDP”。
选择 “下载 RDP 文件 ”并打开下载的文件。
选择 “连接” ,然后输入在前面的步骤中创建的用户名和密码。 如果系统提示,请接受证书。
注册见解提供程序
流日志记录需要 Microsoft.Insights 提供程序。 若要检查其状态,请执行以下步骤:
在门户顶部的搜索框中,输入“订阅”。 从搜索结果中选择“订阅”。
在“订阅”中,选择要为其启用提供程序的 Azure 订阅。
在“设置”下,选择“资源提供程序”。
在筛选器框中输入见解。
确认显示的提供程序状态为“已注册”。 如果状态为“NotRegistered”,请选择“Microsoft.Insights”提供程序,然后选择“注册”。
创建存储帐户
在本部分中,你将创建一个存储帐户来使用它来存储流日志。
在门户顶部的搜索框中,输入“存储帐户”。 从搜索结果中选择“存储帐户”。
选择+ 新建。 在 “创建存储帐户”中,在 “基本信息 ”选项卡中输入或选择以下值:
设置 价值 项目详细信息 Subscription 选择 Azure 订阅。 资源组 选择 myResourceGroup。 实例详细信息 存储帐户名称 输入唯一名称。 本教程使用 nwteststorageaccount。 区域 选择 “(亚太)中国东部”。 存储帐户必须与虚拟机及其网络安全组位于同一区域。 主要服务 选择 Azure Blob 存储或 Azure Data Lake Storage Gen 2。 Performance 选择 “标准”。 流日志仅支持标准层存储帐户。 冗余 选择首选的冗余。 本教程使用本地冗余存储(LRS)。 选择“ 审阅 ”选项卡,或选择底部的 “审阅 ”按钮。
检查设置,然后选择创建。
创建流日志
在本部分中,将创建一个虚拟网络流日志,该日志保存到之前在本教程中创建的存储帐户中。
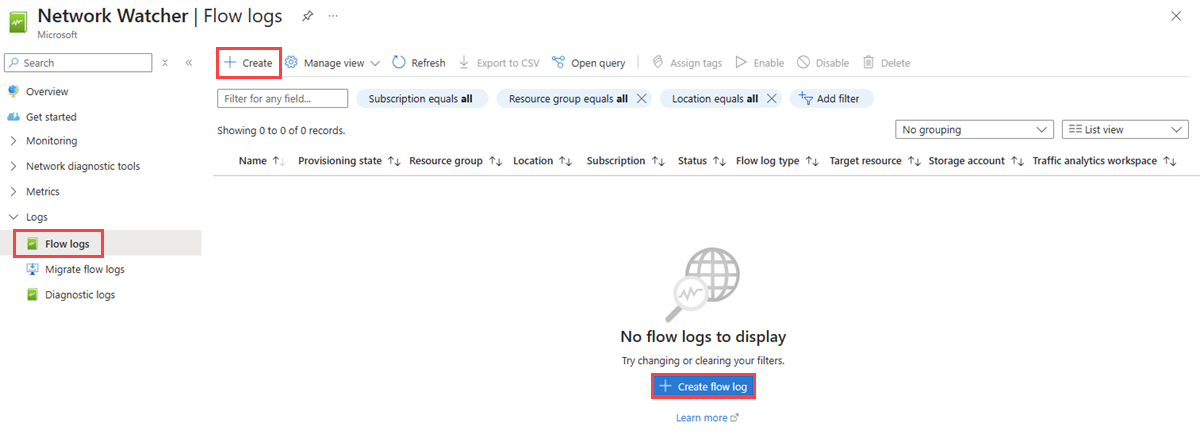
在门户顶部的搜索框中,输入网络监视工具。 在搜索结果中,选择“网络监视器”。
在“日志”下,选择“流日志”。
在“网络观察程序 | 流日志”,选择“+ 创建”或“创建流日志”蓝色按钮。
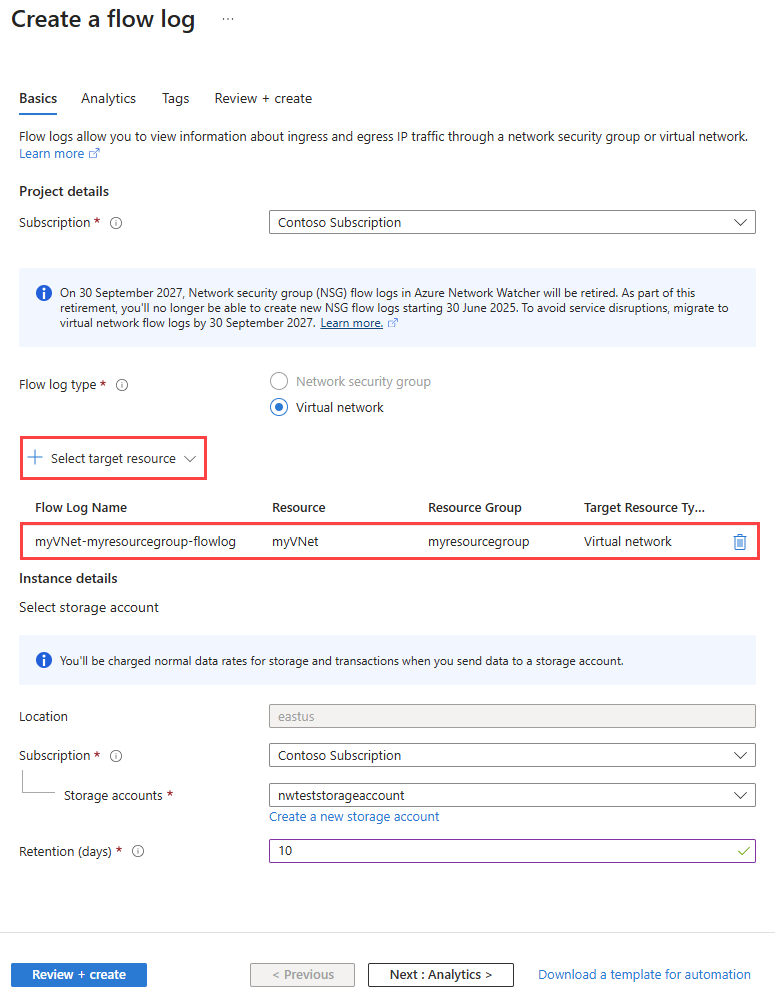
在 “创建流日志”中输入或选择以下值:
设置 价值 项目详细信息 Subscription 选择要记录的网络安全组的 Azure 订阅。 流日志类型 选择 “虚拟网络”。 虚拟网络 选择 “+ 选择目标资源”。
在 “选择虚拟网络”中,选择 myVNet。 然后选择“ 确认选择”。流日志名称 保留 myVNet-myresourcegroup-flowlog 的默认值。 实例详细信息 Subscription 选择存储帐户的 Azure 订阅。 存储帐户 选择在前面的步骤中创建的存储帐户。 保留期(天数) 输入 10 以将存储帐户中的流日志数据保留 10 天。 若要永久保留存储帐户中的流日志数据(直到将其删除),请输入 0。 有关存储定价的信息,请参阅 Azure 存储定价。 注释
Azure 门户在 NetworkWatcherRG 资源组中创建虚拟网络流日志。
选择“查看 + 创建”。
检查设置,然后选择创建。
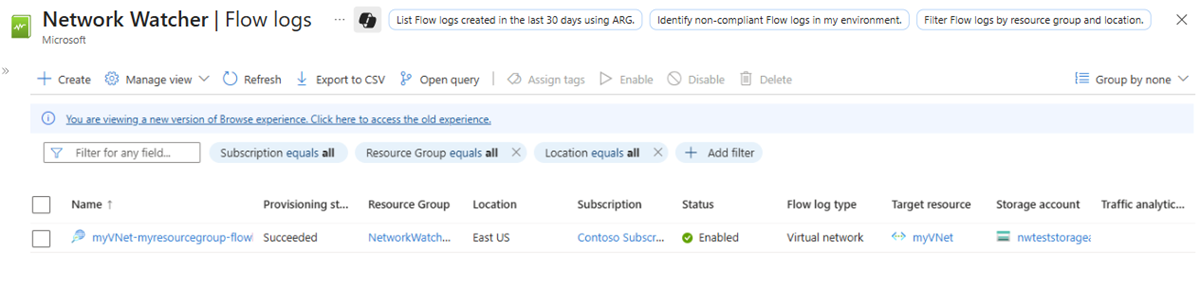
部署完成后,选择 “转到”资源 以确认在流日志页中创建并列出 流日志 。
返回到与 myVM 虚拟机的 RDP 会话。
打开 Microsoft Edge 并转到
www.bing.com。
下载流日志
在本部分中,转到之前选择的存储帐户,并下载在上一部分创建的流日志。
在门户顶部的搜索框中,输入“存储帐户”。 从搜索结果中选择“存储帐户”。
选择 nwteststorageaccount 或之前创建的存储帐户,然后选择用于存储日志。
在“数据存储”下,选择“容器”。
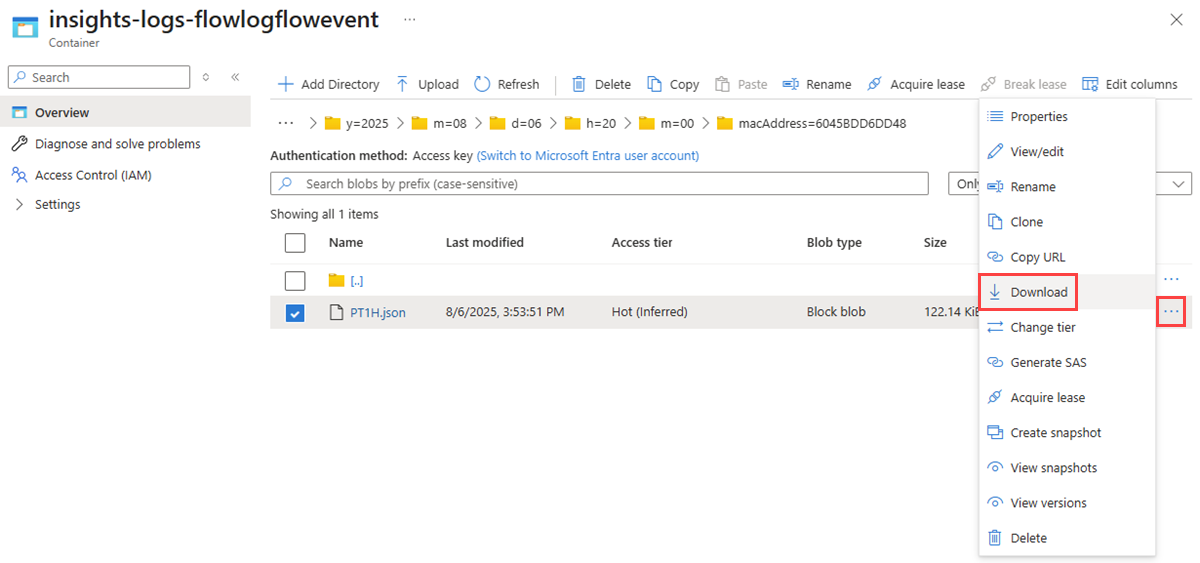
选择“insights-logs-flowlogflowevent”容器。
在容器中,导航文件夹层次结构,直到到达
PT1H.json要下载的文件。 虚拟网络流日志文件遵循以下路径:https://{storageAccountName}.blob.core.chinacloudapi.cn/insights-logs-flowlogflowevent/flowLogResourceID=/{subscriptionID}_NETWORKWATCHERRG/NETWORKWATCHER_{Region}_{ResourceName}-{ResourceGroupName}-FLOWLOGS/y={year}/m={month}/d={day}/h={hour}/m=00/macAddress={macAddress}/PT1H.json选择 PT1H.json 文件右侧的省略号 ... ,然后选择“ 下载”。
注释
可以使用 Azure 存储资源管理器从存储帐户访问和下载流日志。 有关详细信息,请参阅 存储资源管理器入门。
查看流日志
使用所选的文本编辑器打开下载 PT1H.json 的文件。 下面的示例是从下载 PT1H.json 的文件中提取的一个部分,其中显示了规则 DefaultRule_AllowInternetOutBound处理的流。
{
"time": "2025-08-06T20:39:33.3186341Z",
"flowLogGUID": "00000000-0000-0000-0000-000000000000",
"macAddress": "6045BDD6DD48",
"category": "FlowLogFlowEvent",
"resourceId": "/SUBSCRIPTIONS/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e//RESOURCEGROUPS/NETWORKWATCHERRG/PROVIDERS/MICROSOFT.NETWORK/NETWORKWATCHERS/NETWORKWATCHER_China East/FLOWLOGS/MYVNET-MYRESOURCEGROUP-FLOWLOG",
"flowLogVersion": 4,
"operationName": "FlowLogFlowEvent",
"flowRecords": {
"flows": [
{
"aclID": "00000000-0000-0000-0000-000000000000",
"flowGroups": [
{
"rule": "DefaultRule_AllowInternetOutBound",
"flowTuples": [
"1754512773,10.0.0.4,13.107.21.200,49982,443,6,O,C,NX,7,1158,12,8143"
]
}
]
}
]
}
}
flowTuples 的逗号分隔信息如下所示:
| 示例数据 | 代表哪些数据 | Explanation |
|---|---|---|
| 1754512773 | 时间戳 | 在 UNIX EPOCH 格式中发生流的时间戳。 在前面的示例中,日期转换为 2025 年 8 月 6 日 08:39:33 UTC/GMT。 |
| 10.0.0.4 | 源 IP 地址 | 流源自的源 IP 地址。 10.0.0.4 是之前创建的 VM 的专用 IP 地址。 |
| 13.107.21.200 | 目标 IP 地址 | 流的目标 IP 地址。13.107.21.200 是 IP 地址。www.bing.com 由于流量发往 Azure 外部,因此安全规则 DefaultRule_AllowInternetOutBound 处理流。 |
| 49982 | Source Port | 流源自的源端口。 |
| 443 | 目标端口 | 流的目标端口。 |
| 6 | 协议 | IANA 分配值中的流的第 4 层协议:6:TCP。 |
| O | 方向 | 流的方向。 O:出站。 |
| C | 流状态 | 流的状态。 C:继续持续流。 |
| NX | 流加密 | 连接未加密。 |
| 7 | 发送的数据包 | 自上次更新以来发送到目标的 TCP 数据包总数。 |
| 1158 | 发送的字节数 | 自上次更新以来从源发送到目标的 TCP 数据包字节总数。 数据包字节包括数据包标头和有效负载。 |
| 12 | 收到的数据包 | 自上次更新以来从目标接收的 TCP 数据包总数。 |
| 8143 | 接收的字节数 | 自上次更新以来从目标接收的 TCP 数据包字节总数。 数据包字节包括数据包标头和有效负载。 |
清理资源
不再需要时,请删除 myResourceGroup 资源组及其包含的所有资源:
在门户顶部的搜索框中,输入 myResourceGroup。 从搜索结果中选择 myResourceGroup 。
选择“删除资源组”。
在 “删除资源组”中,输入 myResourceGroup,然后选择“ 删除”。
选择 “删除 ”以确认删除资源组及其所有资源。
注释
NetworkWatcher_chinaeast/myVNet-myresourcegroup-flowlog 资源位于 NetworkWatcherRG 资源组中,但在删除 myVNet 虚拟网络后会删除它(通过删除 myResourceGroup 资源组)。