适用于 Azure 的 Microsoft 反恶意软件是一种免费实时保护,可帮助识别并删除病毒、间谍软件和其他恶意软件。 当已知恶意软件或不需要的软件试图在 Azure 系统上安装自己或运行时,该服务会生成警报。
该解决方案构建于 Microsoft Security Essentials [MSE]、Microsoft Forefront Endpoint Protection、Microsoft System Center Endpoint Protection、Microsoft Intune 和 Microsoft Defender for Cloud 所用的同一个反恶意软件平台基础之上。 适用于 Azure 的 Microsoft 反恶意软件是一个针对应用程序和租户环境所提供的单一代理解决方案,可在在后台运行而无需人工干预。 可以根据应用程序工作负载的需求部署保护,包括基本安全默认配置或高级自定义配置,包括反恶意软件监视。
为应用程序部署并启用适用于 Azure 的 Microsoft 反恶意软件后,便可以使用以下几项核心功能:
- 实时保护 - 监视云服务和虚拟机上的活动,以检测和阻止恶意软件的执行。
- 计划的扫描 - 定期扫描以检测恶意软件(包括主动运行的程序)。
- 恶意软件消除 - 自动针对检测到的恶意软件采取措施,例如删除或隔离恶意文件以及清除恶意注册表项。
- 签名更新 - 自动安装最新的保护签名(病毒定义)以确保按预定的频率保持最新保护状态。
- Antimalware 引擎更新 - 自动更新 Microsoft Antimalware 引擎。
- Antimalware 平台更新 - 自动更新 Microsoft Antimalware 平台。
- 主动保护 - 向 Microsoft Azure 报告有关检测到的威胁和可疑资源的遥测元数据,确保对不断演变的威胁状况做出快速响应,并通过 Microsoft 主动保护系统 (MAPS) 启用实时同步特征交付。
- 示例报告 - 将示例提供并报告给 Microsoftt 反恶意软件服务,以帮助改善服务并实现故障排除。
- 排除项 - 允许应用程序和服务管理员配置文件、进程和驱动器的排除项。
- 恶意软件事件收集 -在操作系统事件日志中记录反恶意软件服务的运行状况、可疑活动及采取的补救措施,并将这些数据收集到客户的 Azure 存储帐户。
注意
还可以使用 Microsoft Defender for Cloud 部署 Microsoft Antimalware。
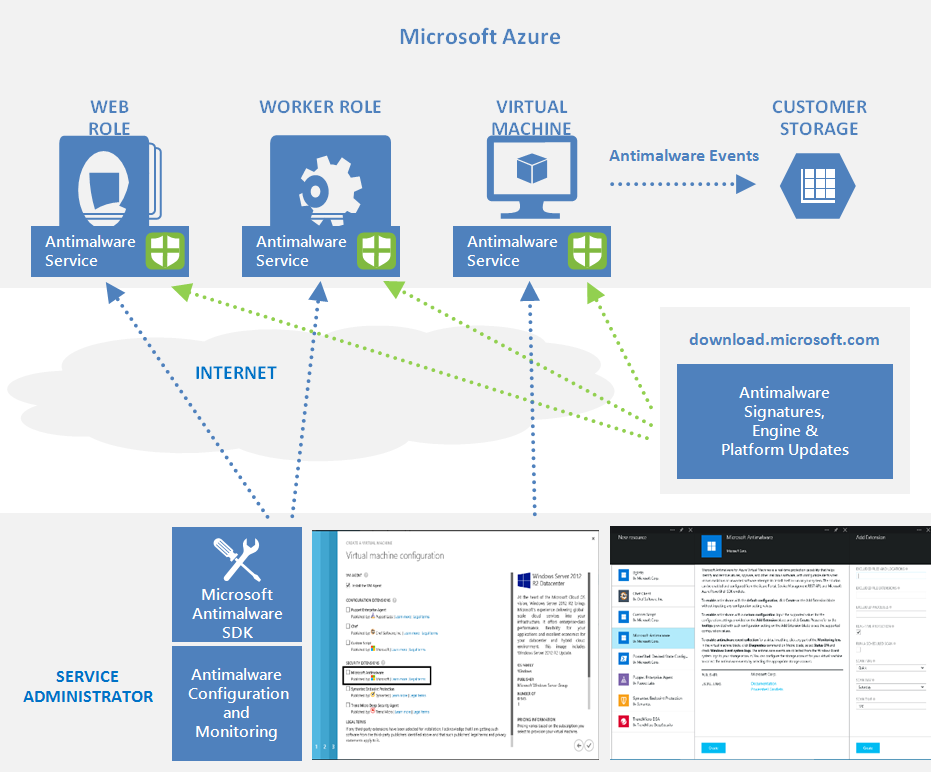
体系结构
适用于 Azure 的反恶意软件Microsoft由多个组件组成:
- Microsoft反恶意软件客户端和服务
- 反恶意软件经典部署模型
- 反恶意软件 PowerShell cmdlet
- Azure 诊断扩展
平台支持和部署
虚拟机:
- 默认情况下未安装
- 通过 Azure 门户或 Visual Studio 虚拟机配置作为可选安全扩展提供
- 在 Windows Server 2008 R2、Windows Server 2012 和 Windows Server 2012 R2 上受支持
- 不支持 Windows Server 2008 和 Linux 操作系统
云服务:
- 安装时默认在所有受支持的 Azure 客体操作系统上为禁用状态
- 需要显式激活来保护云服务
Azure 应用服务:
- 在托管基于 Windows 的 Web 应用的基础服务上启用
- 仅限于保护 Azure 应用服务基础结构,而不是客户内容
- 不足以实现完整的 Web 应用程序安全性
注意
Microsoft Defender 防病毒是 Windows Server 2016 及更高版本中启用的内置反恶意软件。 Azure VM 反恶意软件扩展仍可通过 Microsoft Defender 防病毒添加到 Windows Server 2016 及更高版本的 Azure VM。 在此方案中,该扩展应用Microsoft Defender 防病毒要使用的任何可选 配置策略 。 该扩展不会部署任何其他反恶意软件服务。 有关 Microsoft Defender 防病毒的详细信息,请参阅 代码示例,以便为 Azure 启用和配置 Microsoft 反恶意软件。
Microsoft 反恶意软件工作流
Azure 服务管理员可以使用以下选项,针对虚拟机和云服务通过默认或自定义配置来启用 Azure 的反恶意软件:
- 虚拟机 – 在Azure 门户中的“安全扩展”下
- 虚拟机 – 在服务器资源管理器中使用 Visual Studio 虚拟机配置
- 虚拟机和云服务 – 使用反恶意软件经典部署模型
- 虚拟机和云服务 – 使用反恶意软件 PowerShell cmdlet
Azure 门户或 PowerShell cmdlet 将反恶意软件扩展包文件推送到 Azure 系统中的预定固定位置。 Azure 来宾代理(或结构代理)启动反恶意软件扩展,并将提供的反恶意软件配置设置应用为输入。 此步骤以默认或自定义配置设置来启用反恶意软件服务。 若未提供任何自定义配置,则以默认配置设置来启用反恶意软件服务。 有关反恶意软件配置的详细信息,请参阅 代码示例,以启用和配置适用于 Azure 的反恶意软件Microsoft。
初始化后,Microsoft反恶意软件客户端会自动从 Internet 检索最新的保护引擎和签名定义,并将其应用到 Azure 系统。 服务将所有活动记录到“Microsoft反恶意软件”事件源下的作系统事件日志。 这些日志包括有关以下内容的信息:
- 客户健康状态
- 保护和修正活动
- 配置更改
- 引擎和签名定义更新
- 其他运营事件
可以为云服务或虚拟机启用反恶意软件监视,以便将生成的反恶意软件事件日志事件写入 Azure 存储帐户。 反恶意软件服务使用 Azure 诊断扩展将 Azure 系统中的反恶意软件事件收集到客户 Azure 存储帐户中的表内。
本文档的“反恶意软件部署方案”部分介绍了上述方案支持的部署工作流,包括配置步骤和选项。
注意
不过,可以使用 PowerShell/API 和 Azure 资源管理器模板来部署带有 Microsoft 反恶意软件扩展的虚拟机扩展集。 若要在已运行的虚拟机上安装扩展,可以使用示例 Python 脚本 vmssextn.py。 此脚本获取规模集上的现有扩展配置,并将扩展添加到 Azure 虚拟机规模集上现有扩展的列表。
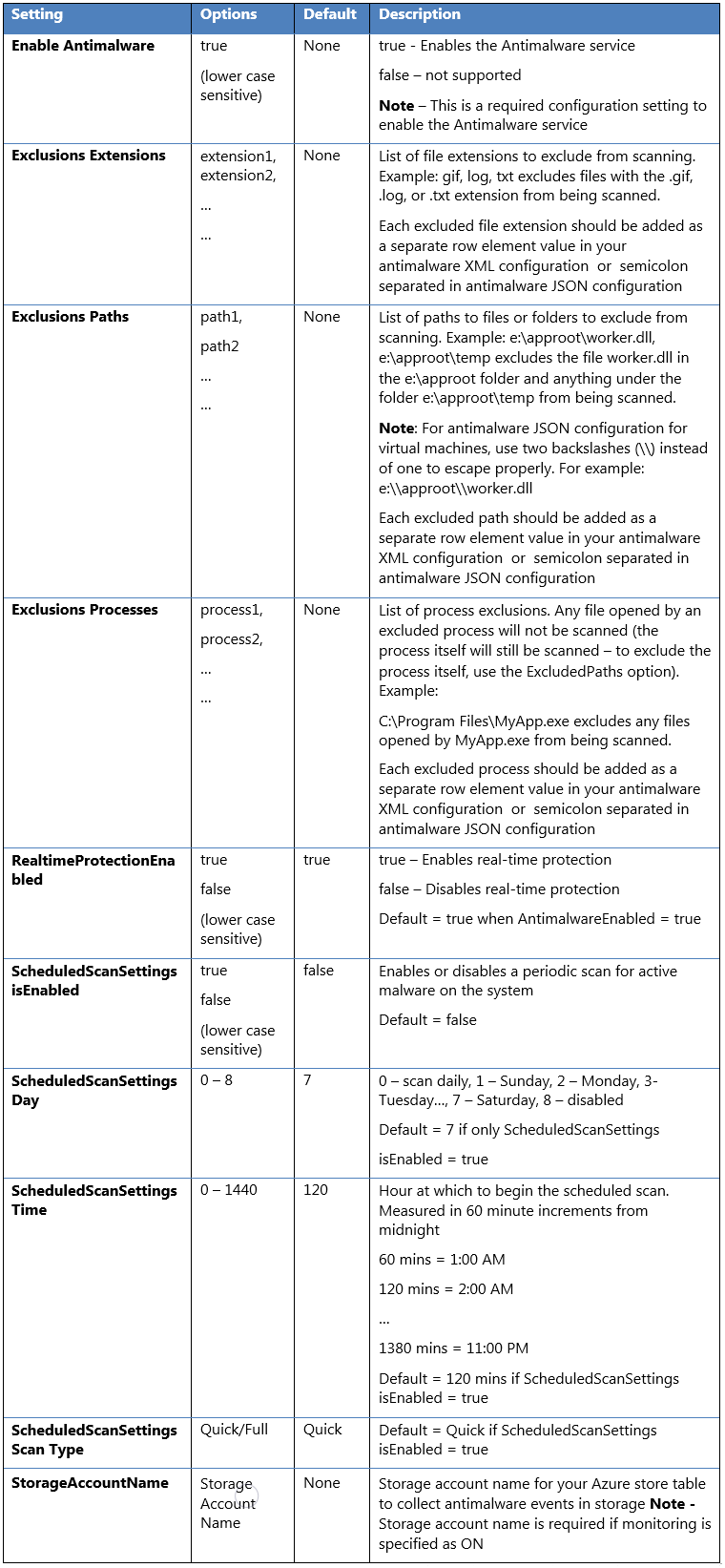
默认和自定义的反恶意软件配置
如果未提供自定义配置设置,会应用默认的配置设置以启用适用于 Azure 云服务或虚拟机的反恶意软件。 默认配置设置已预先优化,以便在 Azure 环境中运行。 或者,可以根据 Azure 应用程序或服务部署的需要自定义这些默认配置设置,并将其应用到其他部署方案。
下表汇总了反恶意软件服务可用的配置设置。 标有“默认”的列下面标记了默认配置设置。
反恶意软件部署方案
本部分介绍启用和配置反恶意软件的方案,包括监视 Azure 云服务和虚拟机。
虚拟机 - 启用和配置反恶意软件
使用 Azure 门户创建 VM 时部署
在预配虚拟机时,可按照以下步骤使用 Azure 门户来启用和配置 Azure 虚拟机的 Microsoft 反恶意软件:
- 登录 Azure 门户。
- 若要创建新的虚拟机,请导航到“虚拟机”,选择“添加”,然后选择“Windows Server”。
- 选择要使用的 Windows Server 版本。
- 选择“创建”。

- 提供“名称”、“用户名”和“密码”,然后创建新资源组或选择现有的资源组。
- 选择“确定”。
- 选择 VM 大小。
- 在下一部分,根据需要做出相应的选择,然后选择“扩展”部分。
- 选择“添加扩展”
- 在“新建资源”下,选择“Microsoft 反恶意软件”。
- 选择“创建”
- 在“安装扩展”部分,可以配置文件、位置和进程排除项,及其他扫描选项。 选择“确定”。
- 选择“确定”。
- 返回“设置”部分,选择“确定”。
- 在“创建”屏幕中选择“确定”。
有关部署适用于 Windows 的反恶意软件 VM 扩展,请参阅此 Azure 资源管理器模板。
使用 Visual Studio 虚拟机配置进行部署
若要使用 Visual Studio 启用和配置 Microsoft 反恶意软件服务,请执行以下操作:
在 Visual Studio 中连接到 Microsoft Azure。
在“服务器资源管理器”的“虚拟机”节点中选择自己的虚拟机。
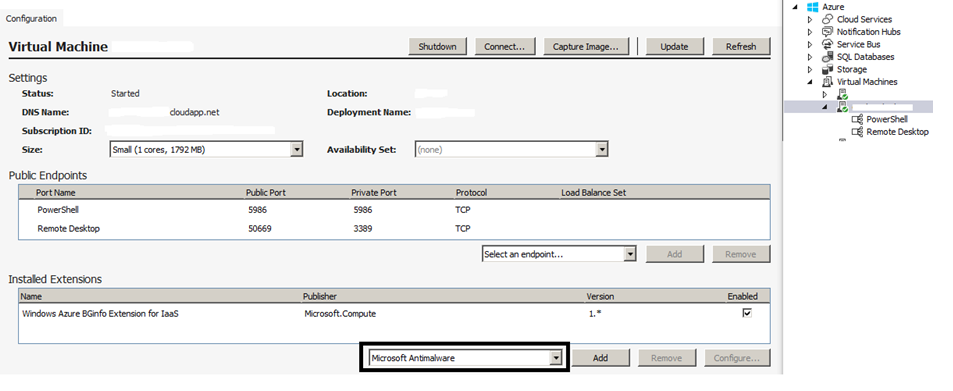
右键单击“配置”查看虚拟机配置页
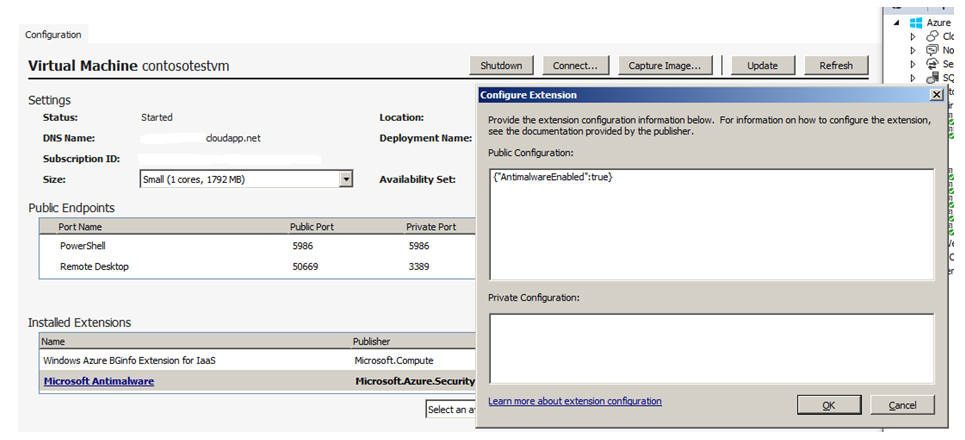
从“已安装的扩展”下的下拉列表中选择Microsoft反恶意软件扩展,然后选择“添加”以使用默认反恶意软件配置进行配置。
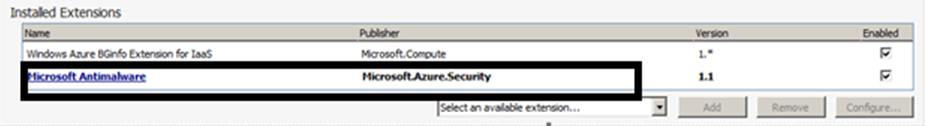
若要自定义默认的反恶意软件配置,请在已安装的扩展列表中选择“突出显示”反恶意软件扩展“,然后选择” 配置”。
将默认反恶意软件配置替换为 公共配置 文本框中支持的 JSON 格式的自定义配置,然后选择“确定”。
选择“ 更新 ”按钮,将配置更新推送到虚拟机。
注意
反恶意软件的 Visual Studio 虚拟机配置仅支持 JSON 格式配置。 有关示例配置的详细信息,请参阅 代码示例以启用和配置适用于 Azure 的反恶意软件Microsoft。
使用 PowerShell cmdlet 进行部署
Azure 应用程序或服务可以使用 PowerShell cmdlet 来启用和配置适用于 Azure 虚拟机的 Microsoft 反恶意软件。
若要使用 PowerShell cmdlet 来启用和配置 Microsoft 反恶意软件,请执行以下操作:
- 设置 PowerShell 环境 - 请参考 https://github.com/Azure/azure-powershell 处的文档
- 使用
Set-AzureVMMicrosoftAntimalwareExtensioncmdlet 为虚拟机启用和配置Microsoft反恶意软件。
注意
反恶意软件的 Azure 虚拟机配置仅支持 JSON 格式配置。 有关示例配置的详细信息,请参阅 代码示例以启用和配置适用于 Azure 的反恶意软件Microsoft。
使用 PowerShell cmdlet 启用和配置反恶意软件
Azure 应用程序或服务可以使用 PowerShell cmdlet 来启用和配置适用于 Azure 云服务的 Microsoft 反恶意软件。 Microsoft 反恶意软件以禁用状态安装在云服务平台中,需要 Azure 应用程序执行某个操作来启用它。
若要使用 PowerShell cmdlet 来启用和配置 Microsoft 反恶意软件,请执行以下操作:
- 设置 PowerShell 环境 - 请参考 https://github.com/Azure/azure-powershell 处的文档
- 使用
Set-AzureServiceExtensioncmdlet 为云服务启用和配置Microsoft反恶意软件。
有关示例 PowerShell 命令的详细信息,请参阅 代码示例来启用和配置适用于 Azure 的反恶意软件Microsoft。
云服务和虚拟机 - 使用 PowerShell cmdlet 进行配置
Azure 应用程序或服务可以使用 PowerShell cmdlet 来检索适用于云服务和虚拟机的 Microsoft 反恶意软件配置。
若要使用 PowerShell cmdlet 来检索 Microsoft 反恶意软件配置,请执行以下操作:
- 设置 PowerShell 环境 - 请参考 https://github.com/Azure/azure-powershell 处的文档
-
对于虚拟机:使用
Get-AzureVMMicrosoftAntimalwareExtensioncmdlet 获取反恶意软件配置。 -
对于云服务:使用
Get-AzureServiceExtensioncmdlet 获取反恶意软件配置。
示例
使用 PowerShell cmdlet 删除反恶意软件配置
Azure 应用程序或服务可以通过从云服务或虚拟机中卸载相关的扩展来完全删除Microsoft反恶意软件保护。 此过程同时删除反恶意软件保护和关联的监视设置,完全停止针对指定资源的恶意软件保护和事件收集。
若要使用 PowerShell cmdlet 删除 Microsoft 反恶意软件,请执行以下操作:
- 设置 PowerShell 环境 - 请参考 https://github.com/Azure/azure-powershell 处的文档
-
对于虚拟机:使用
Remove-AzureVMMicrosoftAntimalwareExtensioncmdlet。 -
对于云服务: 使用
Remove-AzureServiceExtensioncmdlet。
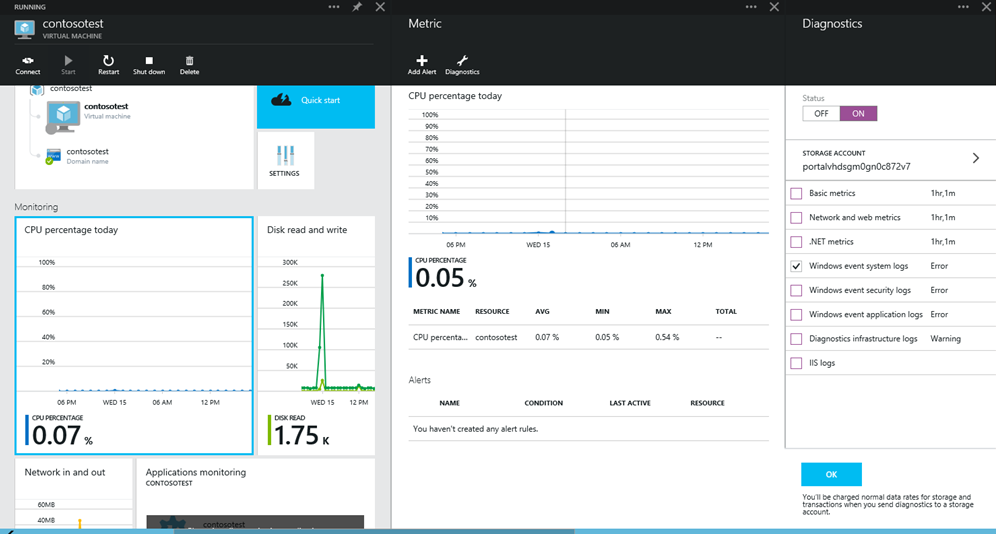
若要使用 Azure 预览门户来启用适用于虚拟机的反恶意软件事件收集,请执行以下操作:
- 在“虚拟机详细信息”页中选择“监视”部分的任何部分。
- 在“指标”部分选择“诊断”命令。
- 选择 状态设为“开启”,并勾选 Windows 事件系统的选项。
- 可以取消选中列表中的所有其他选项,或者根据应用程序服务的需要将它们保持启用状态。
- 将在 Azure 存储帐户中捕获“错误”、“警告”、“信息”等反恶意软件事件类别。
反恶意软件事件将从 Windows 事件系统日志收集到 Azure 存储帐户中。 可以通过选择相应的存储帐户,为虚拟机配置存储帐户以收集反恶意软件事件。
使用 Azure 资源管理器 VM 的 PowerShell cmdlet 启用和配置反恶意软件
要使用 PowerShell cmdlet 为 Azure 资源管理器 VM 启用和配置 Microsoft Antimalware,请执行以下操作:
- 使用 GitHub 上的此文档设置 PowerShell 环境。
- 使用 Set-AzVMExtension cmdlet 为 VM 启用和配置 Microsoft Antimalware。
可以使用以下代码示例:
使用 PowerShell cmdlet 启用和配置 Azure 云服务扩展支持(CS-ES) 的反恶意软件
若要使用 PowerShell cmdlet 来启用和配置 Microsoft 反恶意软件,请执行以下操作:
- 设置 PowerShell 环境 - 请参考 https://github.com/Azure/azure-powershell 处的文档
- 使用 New-AzCloudServiceExtensionObject cmdlet 来启用和配置适用于云服务 VM 的 Microsoft Antimalware。
以下代码示例可用:
使用 PowerShell cmdlet 启用和配置适用于 Azure Arc 启用的服务器的反恶意软件
若要使用 PowerShell cmdlet 为已启用 Azure Arc 的服务器启用和配置 Microsoft Antimalware,请执行以下操作:
- 使用 GitHub 上的此文档设置 PowerShell 环境。
- 使用 New-AzConnectedMachineExtension cmdlet 为已启用 Arc 的服务器启用和配置 Microsoft Antimalware。
可以使用以下代码示例: