本文提供了使用 Azure Site Recovery 将 Azure 虚拟机从一个区域复制到另一个区域时的平台连接性的网络指南。
在您开始之前
了解 Site Recovery 如何为此方案提供灾难恢复。
典型网络基础结构
下图描绘了 Azure 虚拟机上运行的应用程序的典型 Azure 环境:
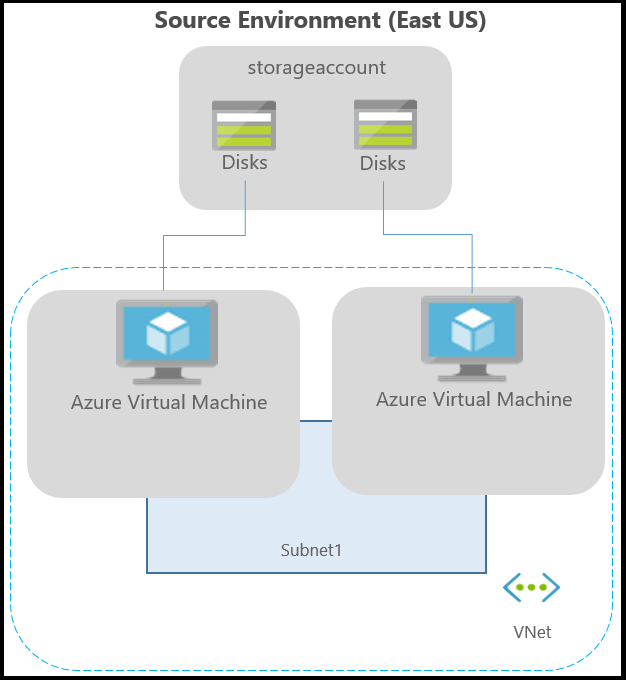
如果使用 Azure ExpressRoute 或从本地网络到 Azure 的 VPN 连接,则环境如下:
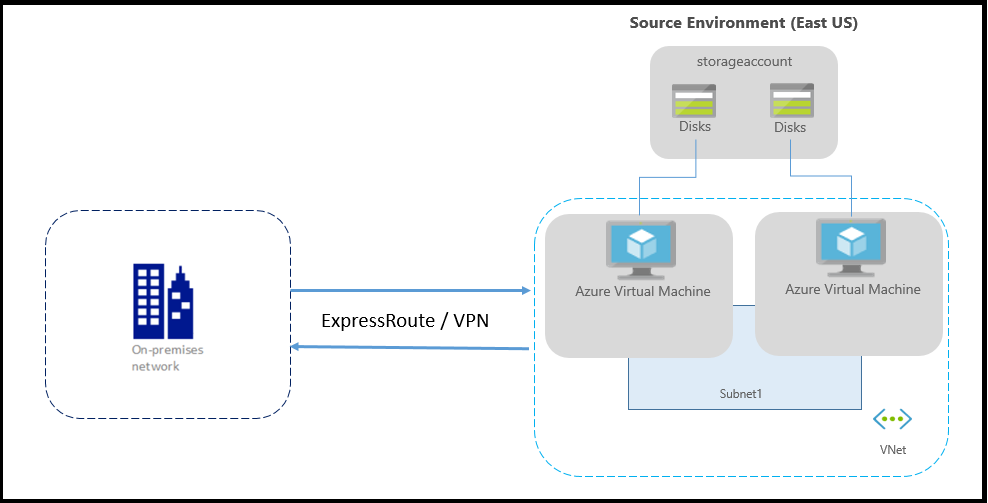
通常,网络使用防火墙和网络安全组 (NSG) 进行保护。 应使用服务标记来控制网络连接。 NSG 应允许多个服务标记来控制出站连接。
重要
Site Recovery 不支持使用经过身份验证的代理控制网络连接,并且无法启用复制。
注释
- 不应执行基于 IP 地址的筛选来控制出站连接。
- 不应在 Azure 路由表中添加 Azure Site Recovery IP 地址来控制出站连接。
URL 的出站连接
如果使用基于 URL 的防火墙代理来控制出站连接,请允许以下 Site Recovery URL:
| 网址 | 详细信息 |
|---|---|
| *.blob.core.chinacloudapi.cn | 必需,用于将数据从虚拟机写入到源区域中的缓存存储帐户。 如果知道虚拟机的所有缓存存储帐户,则可以允许访问特定存储帐户 URL(例如:cache1.blob.core.chinacloudapi.cn 和 cache2.blob.core.chinacloudapi.cn),而不是 *.blob.core.chinacloudapi.cn |
| login.chinacloudapi.cn | 对于 Site Recovery 服务 URL 的授权和身份验证而言是必需的。 |
| *.hypervrecoverymanager.windowsazure.cn | 必需,用于从虚拟机进行 Site Recovery 服务通信。 |
| *.servicebus.chinacloudapi.cn | 必需,用于从虚拟机写入 Site Recovery 监视和诊断数据。 |
| *.vault.azure.cn | 允许访问,以便通过门户为支持 ADE 的虚拟机启用复制 |
| *.azure-automation.cn | 允许通过门户为复制项启用移动代理自动升级 |
使用服务标记的出站连接
除了控制 URL 之外,还可使用服务标记来控制连接性。 为此,必须先在 Azure 中创建网络安全组。 创建后,需要使用现有的服务标记并创建 NSG 规则来允许访问 Azure Site Recovery 服务。
与使用 IP 地址来控制连接性相比,使用服务标记来控制连接性的优点是,不会硬性依赖于特定 IP 地址来保持与服务的连接。 在这种情况下,如果我们的服务之一的 IP 地址发生更改,则正为你的计算机进行的复制不会受到影响。 然而,依赖于硬编码 IP 地址会导致复制状态变为“严重”,使系统面临风险。 另外,服务标记可确保实现比硬编码 IP 地址更好的安全性、稳定性和复原能力。
使用 NSG 来控制出站连接时,需要允许这些服务标记。
- 对于源区域中的存储帐户:
- 为源区域创建基于存储服务标记的 NSG 规则。
- 允许这些地址,以便将数据从虚拟机写入到缓存存储帐户。
- 创建一个基于 Microsoft Entra 服务标记的 NSG 规则,以允许访问与 Microsoft Entra ID 对应的所有 IP 地址
- 为目标地区创建一个基于事件中心服务标记的 NSG 规则,以允许对 Site Recovery 的监控访问。
- 创建基于 AzureKeyVault 服务标记的 NSG 规则。 仅在通过门户为支持 ADE 的虚拟机启用复制时才需要这样做。
- 创建基于 GuestAndHybridManagement 服务标记的 NSG 规则。 仅在通过门户为复制项启用移动代理自动升级时才需要这样做。
- 在生产 NSG 中创建所需的 NSG 规则之前,建议先在测试 NSG 中创建这些规则,并确保没有任何问题。
NSG 配置示例
此示例演示如何为要复制的虚拟机配置 NSG 规则。
- 如果使用 NSG 规则控制出站连接,请对所有必需的 IP 地址范围使用端口 443 的“允许 HTTPS 出站”规则。
- 该示例假定虚拟机源位置为“中国东部”,目标位置为“中国北部”。
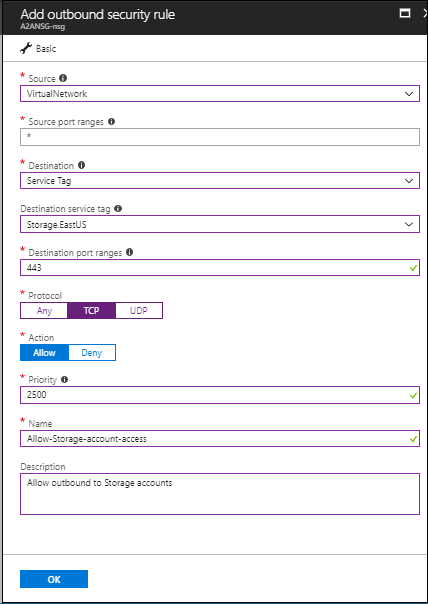
NSG 规则 - 中国东部
为 NSG 上的“存储”创建出站 HTTPS (443) 安全规则,如以下屏幕截图所示:
基于 NSG 规则为“AzureActiveDirectory”创建出站 HTTPS (443) 安全规则,如以下屏幕截图所示:
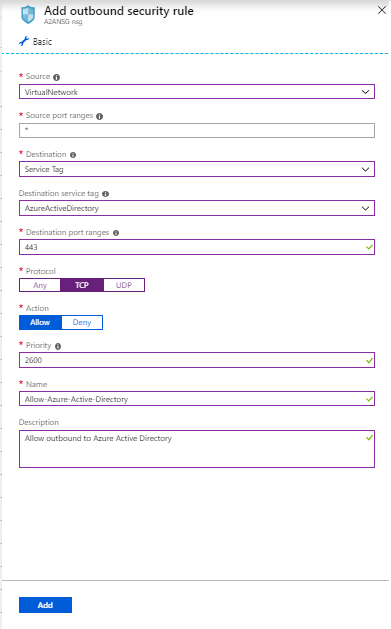
与安全规则类似,为对应于目标位置的 NSG 上的“EventHub”创建出站 HTTPS (443) 安全规则。 这样就可以访问 Site Recovery 监视功能。
NSG 规则 - 中国北部
必须创建这些规则,才能在故障转移后启用从目标区域到源区域的复制:
为 NSG 上的“存储”创建出站 HTTPS (443) 安全规则。
基于 NSG 规则为“AzureActiveDirectory”创建出站 HTTPS (443) 安全规则。
与安全规则类似,为与源位置对应的 NSG 上的“EventHub”创建出站 HTTPS (443) 安全规则。 这样就可以访问 Site Recovery 监视功能。
网络虚拟设备配置
如果使用网络虚拟设备 (NVA) 控制来自虚拟机的出站网络流量,则设备可能在所有复制流量通过 NVA 的情况下受到限制。 建议在虚拟网络中为“存储”创建一个网络服务终结点,这样复制流量就不会经过 NVA。
为存储创建网络服务终结点
可在虚拟网络中为“存储”创建一个网络服务终结点,这样复制流量就不会离开 Azure 边界。
选择 Azure 虚拟网络并选择“服务终结点”。
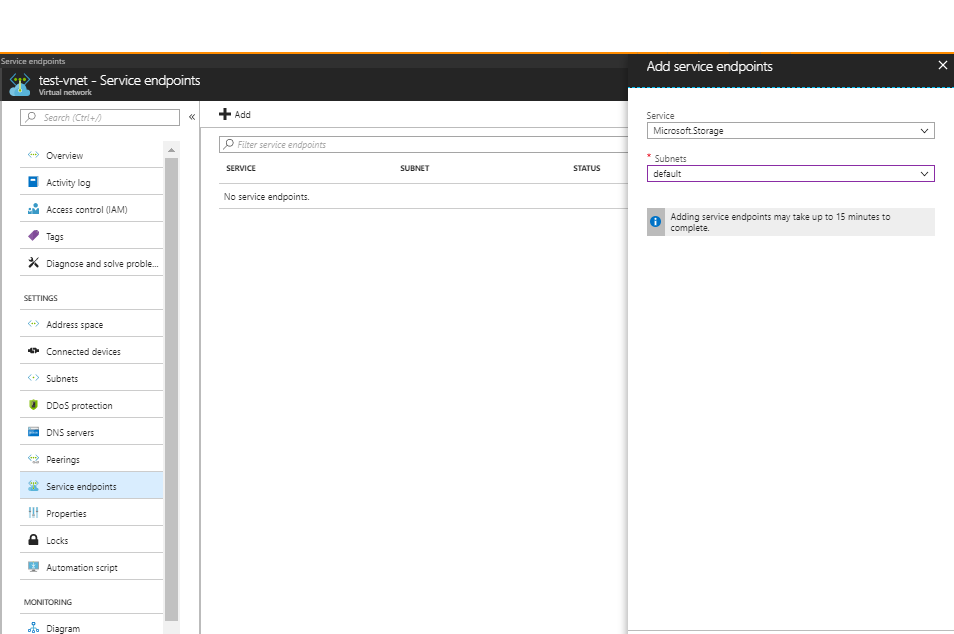
选择“添加”,“添加服务终结点”选项卡随即打开。
选择“服务”下的“Microsoft.Storage”和“子网”字段下的所需子网,然后选择“添加”。
注释
如果你使用的是启用了防火墙的缓存存储帐户或目标存储帐户,请确保“允许受信任的 Azure 服务”。 同时,确保允许访问至少一个源 Vnet 子网。
强制隧道
对 0.0.0.0/0 地址前缀,可将 Azure 默认系统路由重写为自定义路由,并将 VM 流量转换为本地网络虚拟设备 (NVA),但不建议对 Site Recovery 复制使用此配置。 如果使用自定义路由,则应在虚拟网络中为“存储”创建一个虚拟网络服务终结点,这样复制流量就不会离开 Azure 边界。
后续步骤
- 复制 Azure 虚拟机,开始对工作负荷进行保护。
- 详细了解为 Azure 虚拟机故障转移保留 IP 地址。
- 详细了解使用 ExpressRoute 的 Azure 虚拟机的灾难恢复。