我们建议使用 Azure 资源管理器锁锁定所有存储帐户,以防意外或恶意删除存储帐户。 有两种类型的 Azure 资源管理器资源锁:
- CannotDelete 锁可防止用户删除存储帐户,但允许读取和修改其配置。
- ReadOnly 锁可防止用户删除存储帐户或修改其配置,但允许读取配置。
有关 Azure 资源管理器锁的详细信息,请参阅锁定资源以防止更改。
注意
锁定存储帐户不会阻止对其中容器或 blob 执行的删除或覆盖操作。 有关如何保护 blob 数据的详细信息,请参阅数据保护概述。
配置 Azure 资源管理器锁
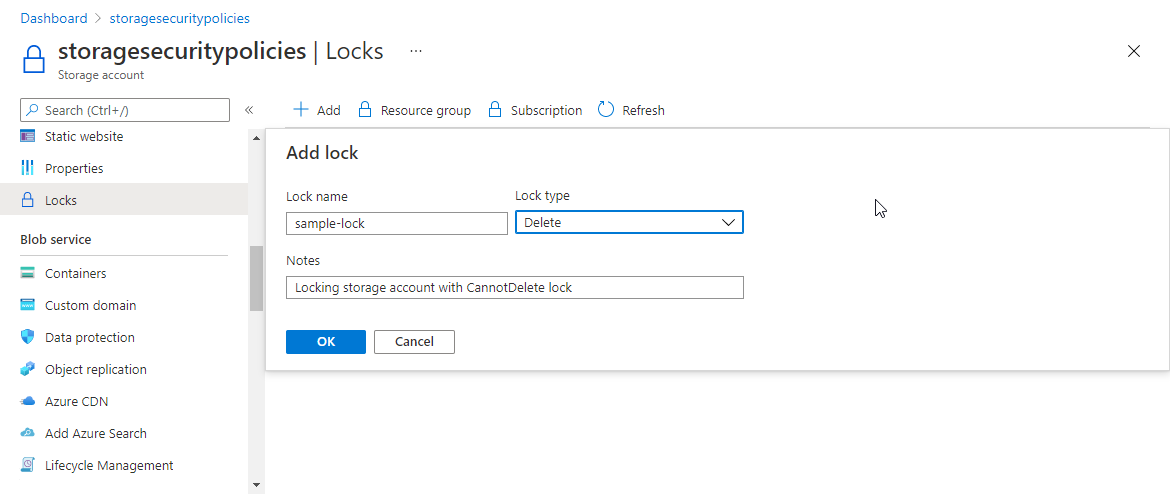
若要通过 Azure 门户配置存储帐户的锁,请执行以下步骤:
导航到 Azure 门户中的存储帐户。
在“设置”部分下,选择“锁”。
选择“添加”。
提供资源锁的名称,然后指定锁的类型。 如果需要,请添加有关锁的说明。
当 ReadOnly 锁有效时授权数据操作
将 ReadOnly 锁应用于存储帐户时,将阻止该存储帐户的列出密钥操作。 “列出密钥”操作是 HTTPS POST 操作,并且在为该帐户配置了 ReadOnly 锁时,所有 POST 操作都会被阻止。 “列出密钥”操作返回帐户访问密钥,然后可以使用这些密钥来读取和写入存储帐户中的任何数据。
如果在将锁应用于存储帐户时客户端拥有帐户访问密钥,则该客户端可以继续使用这些密钥来访问数据。 但是,无权访问密钥的客户端需要使用 Microsoft Entra 凭据来访问存储帐户中的 blob 或队列数据。
如果 Azure 门户的用户以前已使用帐户访问密钥访问了门户中的 blob 或队列数据,则在应用了 ReadOnly 锁时可能会影响这些用户。 应用锁后,门户用户需要使用 Microsoft Entra 凭据来访问门户中的 blob 或队列数据。 若要执行此操作,用户必须至少为其分配两个 RBAC 角色:至少 Azure 资源管理器读者角色,以及 Azure 存储数据访问角色之一。 有关详细信息,请参阅以下文章之一:
以前使用帐户密钥访问 Azure 文件中的数据或表服务的客户端可能变得无法访问。 最佳做法是,如果必须将 ReadOnly 锁应用于存储帐户,则将 Azure 文件和表服务工作负载移至未使用 ReadOnly 锁锁定的存储帐户。