使用 Azure 门户访问 Blob 数据时,门户会在后台对 Azure 存储发出请求。 可以使用 Microsoft Entra 帐户或存储帐户访问密钥对 Azure 存储请求进行授权。 门户会指示使用的是哪种方法,如果你有相应的权限,则门户还允许在这两种方法之间切换。
访问 Blob 数据所需的权限
你需要特定权限,具体取决于你在 Azure 门户中授权访问 Blob 数据的方式。 在大多数情况下,这些权限是通过 Azure 基于角色的访问控制 (Azure RBAC) 提供的。 有关 Azure RBAC 的详细信息,请参阅 什么是 Azure 基于角色的访问控制(Azure RBAC)?
使用帐户访问密钥
若要使用帐户访问密钥访问 blob 数据,你必须已分配到一个 Azure 角色,此角色包含 Azure RBAC 操作 Microsoft.Storage/storageAccounts/listkeys/action。 此 Azure 角色可以是内置角色,也可以是自定义角色。
以下内置角色(按权限从小到大排序)支持“Microsoft.Storage/storageAccounts/listkeys/action”:
尝试在 Azure 门户中访问 blob 数据时,首先会检查你是否被分配了具有 Microsoft.Storage/storageAccounts/listkeys/action 的角色。 如果你被分配了包含此操作的角色,则门户将使用帐户密钥来访问 blob 数据。 如果你没有包含此操作的角色,则门户会尝试使用你的 Microsoft Entra 帐户访问数据。
重要
在使用 Azure 资源管理器 ReadOnly 锁锁定了某个存储帐户时,不允许为该存储帐户执行列出密钥操作。 “列出密钥”是 POST 操作,并且在为该帐户配置了 ReadOnly 锁时,所有的 POST 操作都会被阻止 。 因此,当帐户被 ReadOnly 锁锁定时,用户必须使用 Microsoft Entra 凭据访问门户中的 blob 数据。 要了解如何使用 Microsoft Entra ID 访问门户中的 blob 数据,请参阅使用 Microsoft Entra 帐户。
注意
经典订阅管理员角色“服务管理员”和“共同管理员”具有 Azure 资源管理器所有者角色的等效权限。 “所有者”角色包含所有操作,其中包括 Microsoft.Storage/storageAccounts/listkeys/action,因此,拥有其中一种管理角色的用户也可以使用帐户密钥访问 Blob 数据。 有关详细信息,请参阅 Azure 角色、Microsoft Entra 角色和经典订阅管理员角色。
使用 Microsoft Entra 帐户
要使用 Microsoft Entra 帐户从 Azure 门户访问 blob 数据,必须满足以下两个条件:
- 你拥有可提供 blob 数据访问权限的内置角色或自定义角色。
- 你至少拥有 Azure 资源管理器读取者角色,该角色的权限范围为存储帐户或更高级别。 “读取者”角色授予限制性最高的权限,但也接受可授予存储帐户管理资源访问权限的其他 Azure 资源管理器角色。
Azure 资源管理器“读取者”角色允许用户查看存储帐户资源,但不允许修改这些资源。 该角色不提供对 Azure 存储中的数据的读取权限,而只提供对帐户管理资源的读取权限。 “读者”角色是必需的,以便用户可以导航到 Azure 门户中的 blob 容器。
有关支持访问 Blob 数据的内置角色的信息,请参阅使用 Microsoft Entra ID 授权访问 Blob。
自定义角色能够支持内置角色所提供的相同权限的不同组合。 若要详细了解如何创建 Azure 自定义角色,请参阅 Azure 自定义角色和了解 Azure 资源的角色定义。
在 Azure 门户中导航到 Blob
若要在门户中查看 blob 数据,请导航到存储帐户的“概述”,然后选择“Blob”对应的链接。 或者,可以在菜单中导航到“容器”部分。
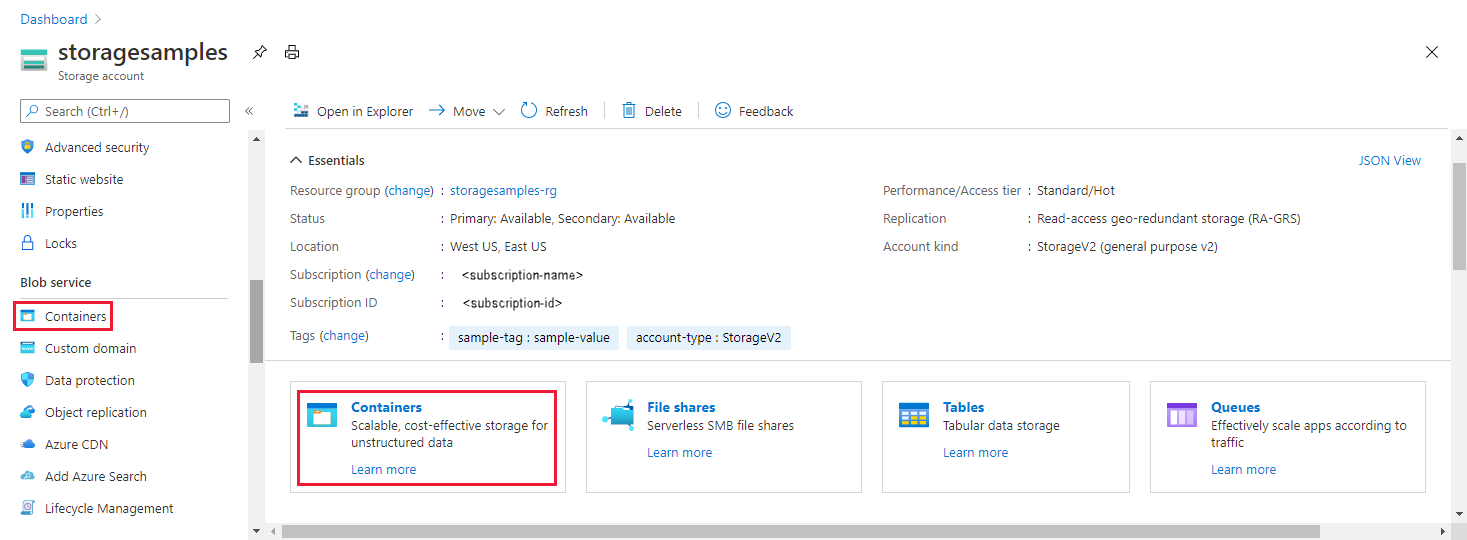
确定当前的身份验证方法
导航到容器时,Azure 门户会指示当前是使用帐户访问密钥还是使用 Microsoft Entra 帐户进行身份验证。
使用帐户访问密钥进行身份验证
如果使用帐户访问密钥进行身份验证,则会在门户中看到“访问密钥”已指定为身份验证方法:
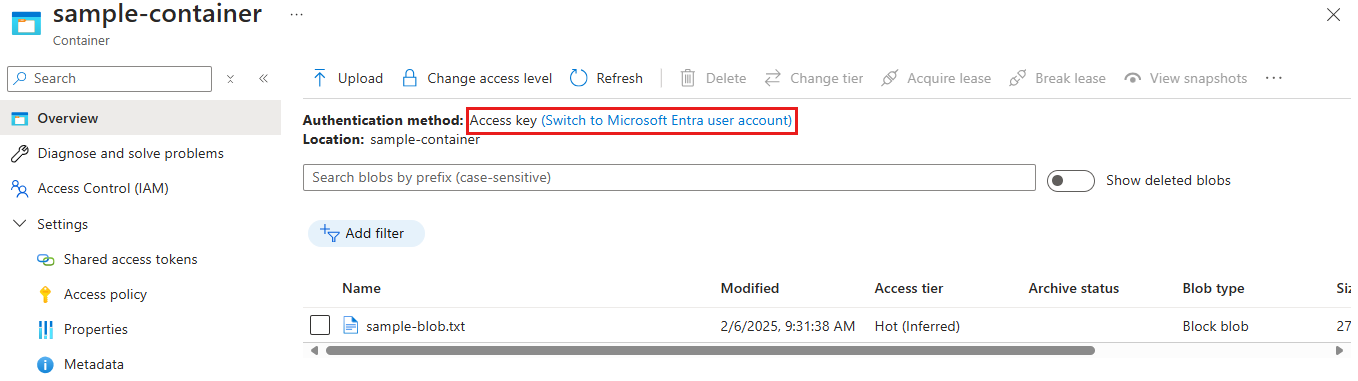
若要改用 Microsoft Entra 帐户,请选择图中突出显示的链接。 如果你通过分配给你的 Azure 角色获得了相应的权限,则可以继续访问。 如果没有正确的权限,则会看到错误消息,列表中不会显示任何 Blob。
选择“切换为访问密钥”链接,以再次使用访问密钥进行身份验证。
使用 Microsoft Entra 帐户进行身份验证
如果使用 Microsoft Entra 帐户进行身份验证,则会在门户中看到“Microsoft Entra 用户帐户”已指定为身份验证方法:
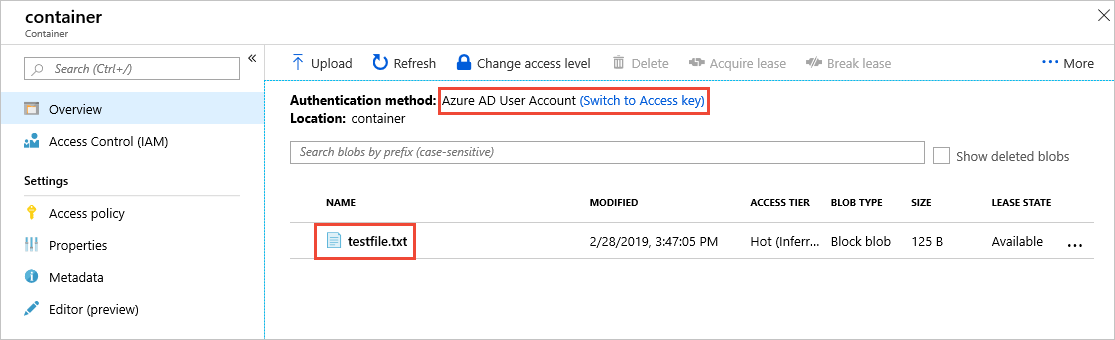
若要改用帐户访问密钥,请选择图中突出显示的链接。 如果你有权访问帐户密钥,则可以继续访问。 如果无权访问帐户密钥,则会看到错误消息,列表中不会显示任何 Blob。
选择“切换到 Microsoft Entra 用户帐户”链接,以再次使用 Microsoft Entra 帐户进行身份验证。