用于输出到 Azure Blob 存储的托管标识身份验证使流分析作业能够直接访问存储帐户,而不用使用连接字符串。 除了提高安全性以外,此功能还可让你将数据写入到 Azure 上的虚拟网络 (VNET) 中的存储帐户。
本文介绍如何通过 Azure 门户以及通过 Azure 资源管理器部署,为流分析作业的 Blob 输出启用托管标识。
使用 Azure 门户创建流分析作业
首先,创建 Azure 流分析作业的托管标识。
在 Azure 门户中,打开 Azure 流分析作业。
从左侧导航菜单中,选择“配置”下的“托管标识”。 然后,选中“使用系统分配的托管标识”旁的框,然后选择“保存”。
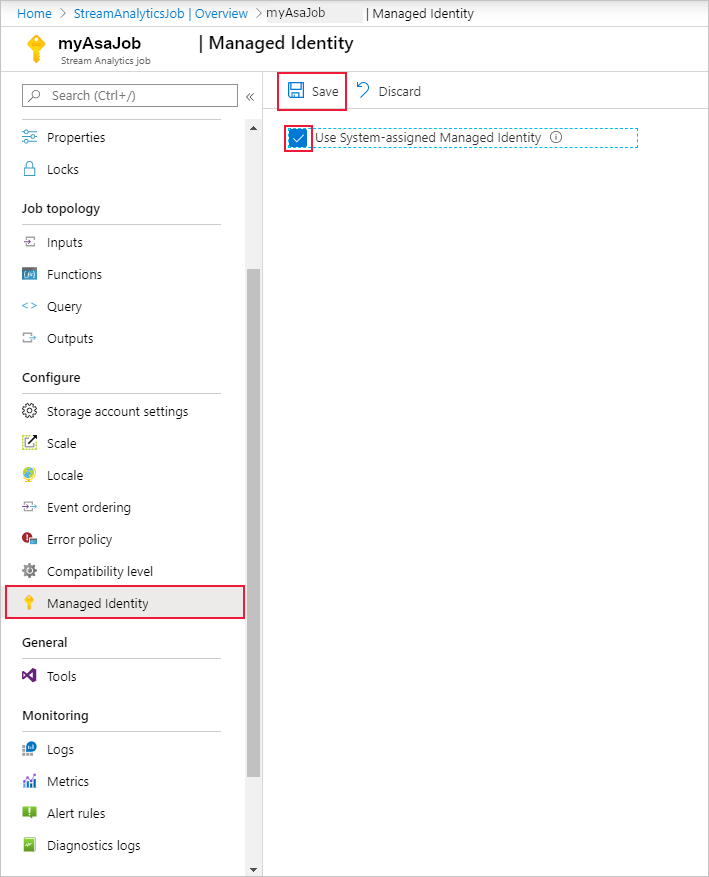
在 Microsoft Entra ID 中为流分析作业的标识创建服务主体。 新建标识的生命周期将由 Azure 管理。 删除流分析作业时,Azure 会自动删除关联的标识(即服务主体)。
保存配置后,服务主体的对象 ID (OID) 将列为主体 ID,如下所示:
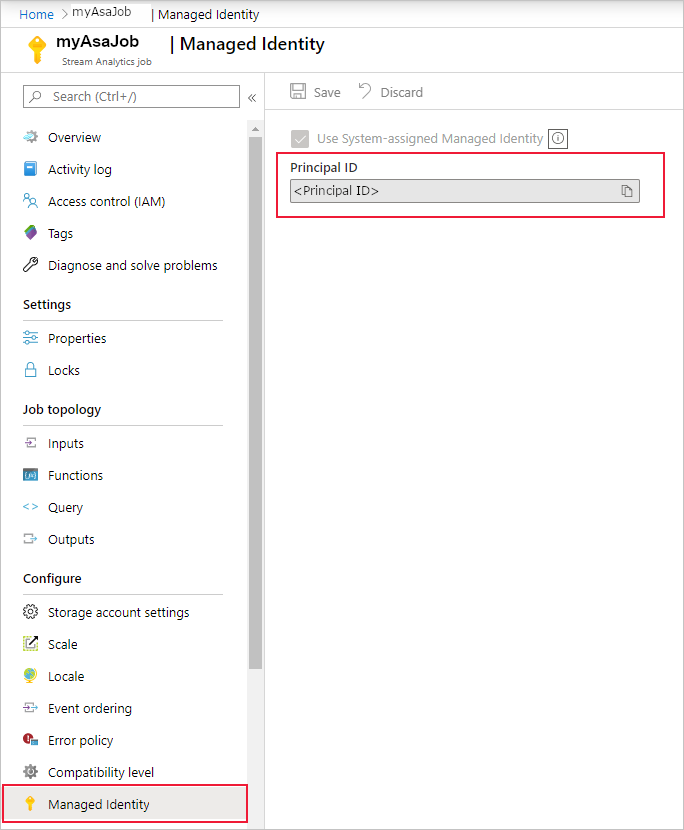
服务主体与流分析作业同名。 例如,如果作业的名称是
MyASAJob,则服务主体的名称也是MyASAJob。
Azure 资源管理器部署
使用 Azure 资源管理器可以完全自动化流分析作业的部署。 可以使用 Azure PowerShell 或 Azure CLI 部署资源管理器模板。 以下示例使用 Azure CLI。
可以通过在资源管理器模板的 resource 节中包含以下属性,来创建带有托管标识的 Microsoft.StreamAnalytics/streamingjobs 资源:
"Identity": { "Type": "SystemAssigned", },此属性告知 Azure 资源管理器为流分析作业创建和管理标识。 以下示例资源管理器模板部署一个启用了托管标识的流分析作业,以及一个使用托管标识的 Blob 输出接收器:
{ "$schema": "http://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json#", "contentVersion": "1.0.0.0", "resources": [ { "apiVersion": "2017-04-01-preview", "name": "MyStreamingJob", "location": "[resourceGroup().location]", "type": "Microsoft.StreamAnalytics/StreamingJobs", "identity": { "type": "systemAssigned" }, "properties": { "sku": { "name": "standard" }, "outputs":[ { "name":"output", "properties":{ "serialization": { "type": "JSON", "properties": { "encoding": "UTF8" } }, "datasource":{ "type":"Microsoft.Storage/Blob", "properties":{ "storageAccounts": [ { "accountName": "MyStorageAccount" } ], "container": "test", "pathPattern": "segment1/{date}/segment2/{time}", "dateFormat": "yyyy/MM/dd", "timeFormat": "HH", "authenticationMode": "Msi" } } } } ] } } ] }可使用以下 Azure CLI 命令将上述作业部署到资源组 ExampleGroup:
az deployment group create --resource-group ExampleGroup -template-file StreamingJob.json创建作业后,可以使用 Azure 资源管理器检索该作业的完整定义。
az resource show --ids /subscriptions/{SUBSCRIPTION_ID}/resourceGroups/{RESOURCE_GROUP}/providers/Microsoft.StreamAnalytics/StreamingJobs/{RESOURCE_NAME}以上命令将返回如下所示的响应:
{ "id": "/subscriptions/{SUBSCRIPTION_ID}/resourceGroups/{RESOURCE_GROUP}/providers/Microsoft.StreamAnalytics/streamingjobs/{RESOURCE_NAME}", "identity": { "principalId": "{PRINCIPAL_ID}", "tenantId": "{TENANT_ID}", "type": "SystemAssigned", "userAssignedIdentities": null }, "kind": null, "location": "China North", "managedBy": null, "name": "{RESOURCE_NAME}", "plan": null, "properties": { "compatibilityLevel": "1.0", "createdDate": "2019-07-12T03:11:30.39Z", "dataLocale": "en-US", "eventsLateArrivalMaxDelayInSeconds": 5, "jobId": "{JOB_ID}", "jobState": "Created", "jobStorageAccount": null, "jobType": "Cloud", "outputErrorPolicy": "Stop", "package": null, "provisioningState": "Succeeded", "sku": { "name": "Standard" } }, "resourceGroup": "{RESOURCE_GROUP}", "sku": null, "tags": null, "type": "Microsoft.StreamAnalytics/streamingjobs" }请记下作业定义中的 principalId,它用于在 Microsoft Entra ID 中标识该作业的托管标识,并将在下一步骤中用于授予对存储帐户的访问权限。
创建作业后,请参阅本文的为流分析作业授予对存储帐户的访问权限部分。
为流分析作业授予对存储帐户的访问权限
可以选择为流分析作业授予两种级别的访问权限:
- 容器级访问权限:使用此选项可为作业授予对现有特定容器的访问权限。
- 帐户级访问权限:使用此选项可为作业授予对存储帐户的一般访问权限,包括创建新容器的能力。
除非你需要作业代表你创建容器,否则应选择“容器级访问权限”,因为此选项将为作业授予所需的最低访问权限级别。 下面将会解释这两个选项在 Azure 门户和命令行中的用法。
注释
由于全局复制或缓存延迟,在撤销或授予权限时可能会有延迟。 更改应在 8 分钟内反映出来。
通过 Azure 门户授予访问权限
容器级访问权限
导航到存储帐户中的容器配置窗格。
选择“访问控制(IAM)”。
选择添加>添加角色分配以打开添加角色分配页面。
分配以下角色。 有关详细步骤,请参阅使用 Azure 门户分配 Azure 角色。
设置 价值 角色 存储 Blob 数据参与者 将访问权限分配到 用户、组或服务主体 成员 <流分析作业的名称> 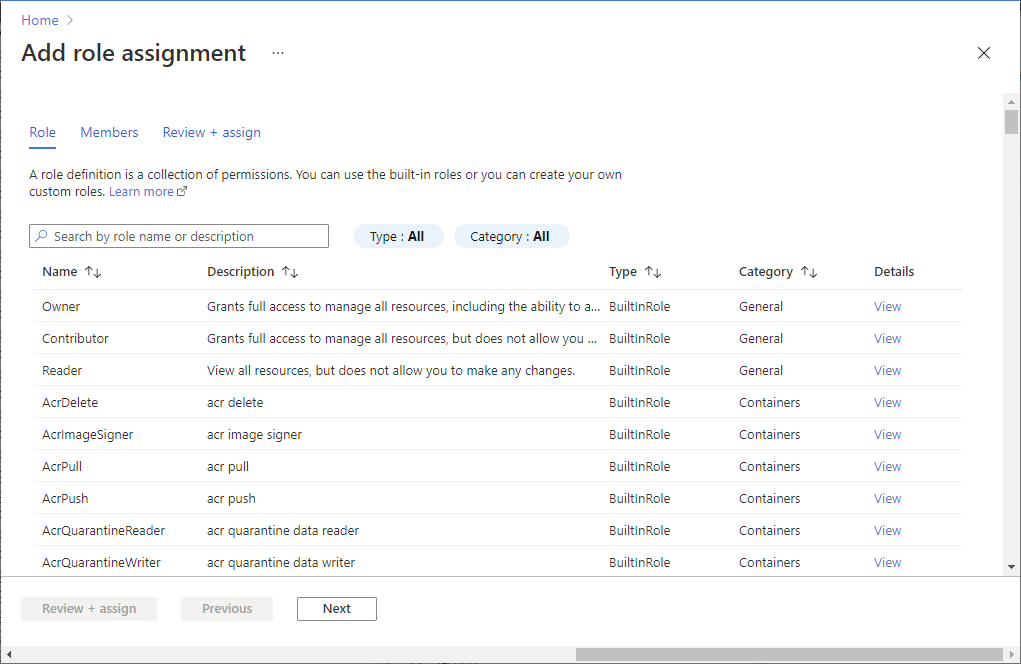
帐户级访问权限
访问您的存储帐户。
选择“访问控制(IAM)”。
选择添加>添加角色分配以打开添加角色分配页面。
分配以下角色。 有关详细步骤,请参阅使用 Azure 门户分配 Azure 角色。
设置 价值 角色 存储 Blob 数据参与者 将访问权限分配到 用户、组或服务主体 成员 <流分析作业的名称> 
通过命令行授予访问权限
容器级访问权限
若要授予对特定容器的访问权限,请使用 Azure CLI 运行以下命令:
az role assignment create --role "Storage Blob Data Contributor" --assignee <principal-id> --scope /subscriptions/<subscription-id>/resourcegroups/<resource-group>/providers/Microsoft.Storage/storageAccounts/<storage-account>/blobServices/default/containers/<container-name>
帐户级访问权限
若要授予对整个帐户的访问权限,请使用 Azure CLI 运行以下命令:
az role assignment create --role "Storage Blob Data Contributor" --assignee <principal-id> --scope /subscriptions/<subscription-id>/resourcegroups/<resource-group>/providers/Microsoft.Storage/storageAccounts/<storage-account>
创建 blob 输入或输出
现在已经配置了托管标识,可以将 blob 资源作为输入或输出添加到流分析作业了。
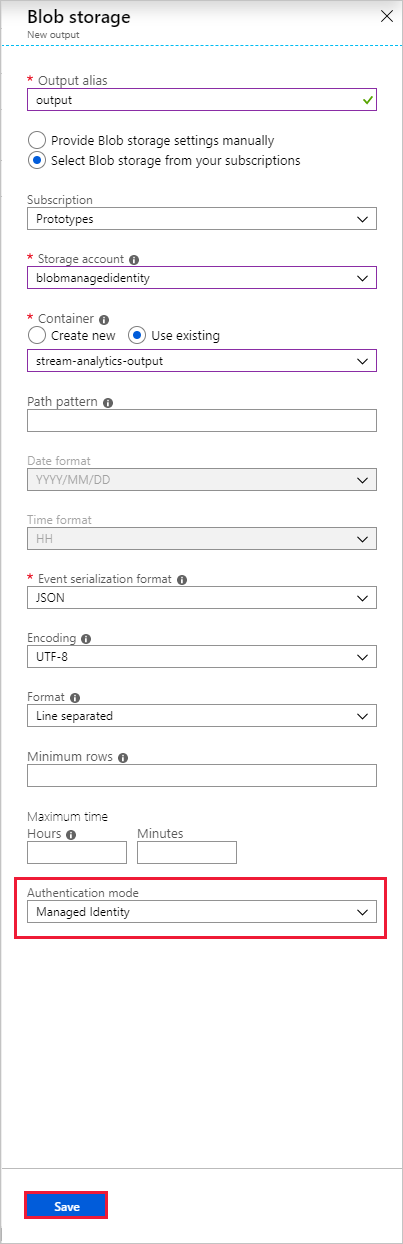
在 Azure Blob 存储输出接收器的输出属性窗口中,选择“身份验证模式”下拉列表并选择“托管标识”。 有关其他输出属性的信息,请参阅了解 Azure 流分析的输出。 完成后,单击“ 保存”。
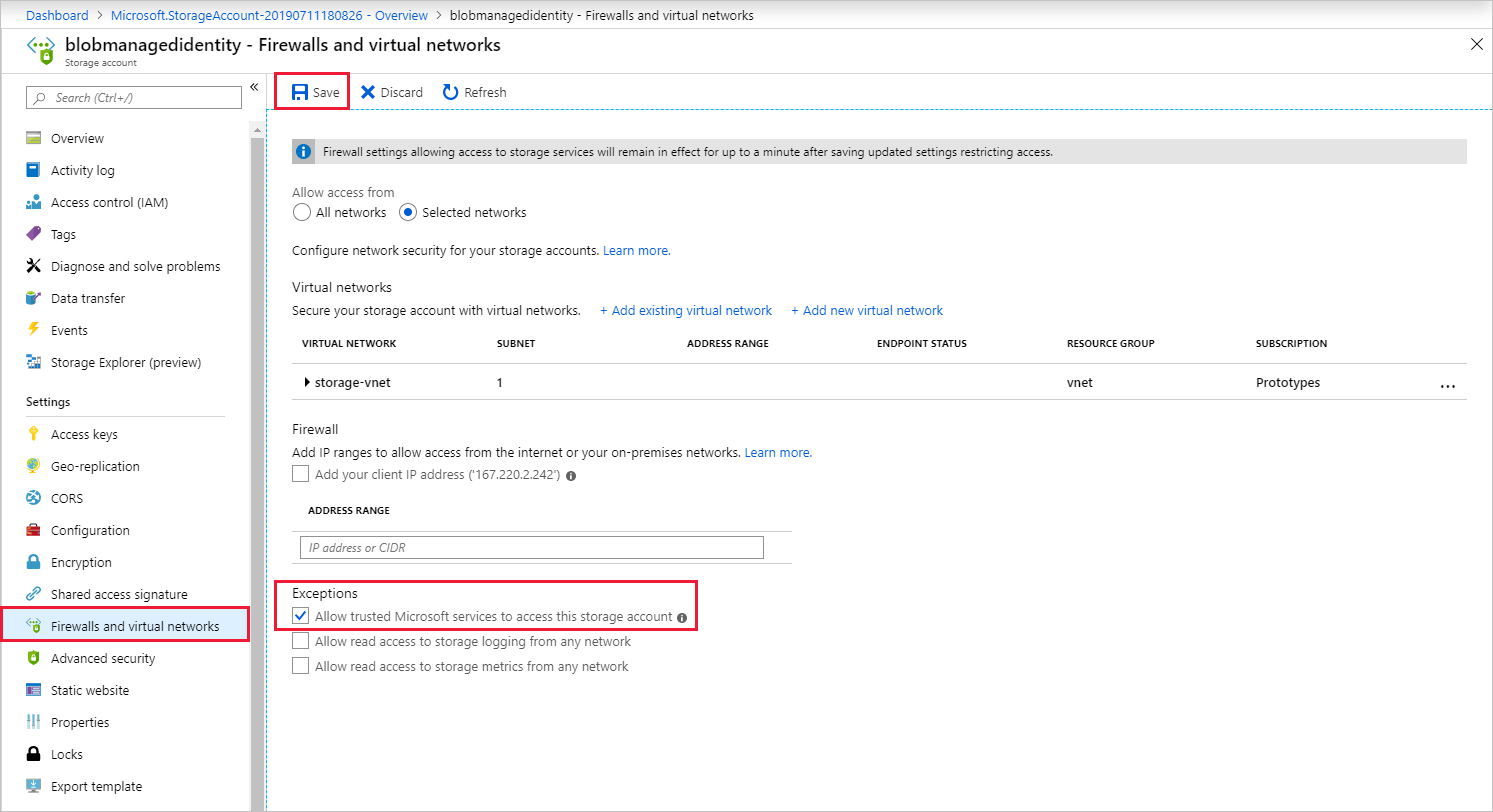
启用 VNET 访问权限
配置存储帐户的防火墙和虚拟网络时,可以视需要允许来自其他受信任 Microsoft 服务的网络流量。 当流分析使用托管标识进行身份验证时,它会提供该请求源自受信任服务的证明。 下面是有关启用此 VNET 访问权限例外的说明。
- 在存储帐户的配置窗格中导航到“防火墙和虚拟网络”窗格。
- 确保启用“允许受信任的 Microsoft 服务访问此存储帐户”选项。
- 如果已启用此选项,请单击“保存”。
删除托管标识
仅当删除流分析作业后,才会删除为该作业创建的托管标识。 如果不删除作业,则无法删除其托管标识。 如果不想再使用托管标识,可以更改对输出的身份验证方法。 在删除作业之前,托管标识会始终存在,如果决定再次使用托管标识身份验证,将再次使用该标识。
局限性
下面是此功能的当前限制:
经典 Azure 存储帐户。
没有 Microsoft Entra ID 的 Azure 帐户。
不支持多租户访问。 为给定流分析作业创建的服务主体必须驻留在创建了该作业的同一 Microsoft Entra 租户中,并且不得用于驻留在其他 Microsoft Entra 租户中的资源。