Azure 基于角色的访问控制(Azure RBAC) 是用于管理对 Azure 资源的访问的授权系统。 若要授予访问权限,请将角色分配给特定范围内的用户、组、服务主体或托管标识。 本文介绍如何使用 Azure 门户分配角色。
如果需要在 Microsoft Entra ID 中分配管理员角色,请参阅 向用户分配Microsoft Entra 角色。
先决条件
若要分配 Azure 角色,必须具有:
-
Microsoft.Authorization/roleAssignments/write权限,例如 基于角色的访问控制管理员 或 用户访问管理员
步骤 1:识别所需的范围
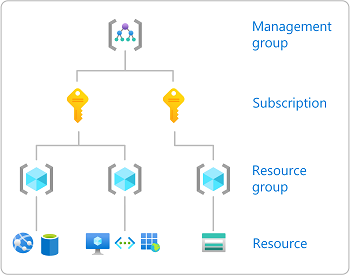
分配角色时,必须指定一个范围。 范围是访问权限适用于的资源集。 在 Azure 中,可以在范围从宽到窄的四个级别指定范围: 管理组、订阅、 资源组和资源。 有关详细信息,请参阅了解范围。
登录到 Azure 门户。
在顶部的“搜索”框中,搜索要授予对其的访问权限的范围。 例如,搜索“管理组”、“订阅”、“资源组”或某个特定资源。
单击该范围的特定资源。
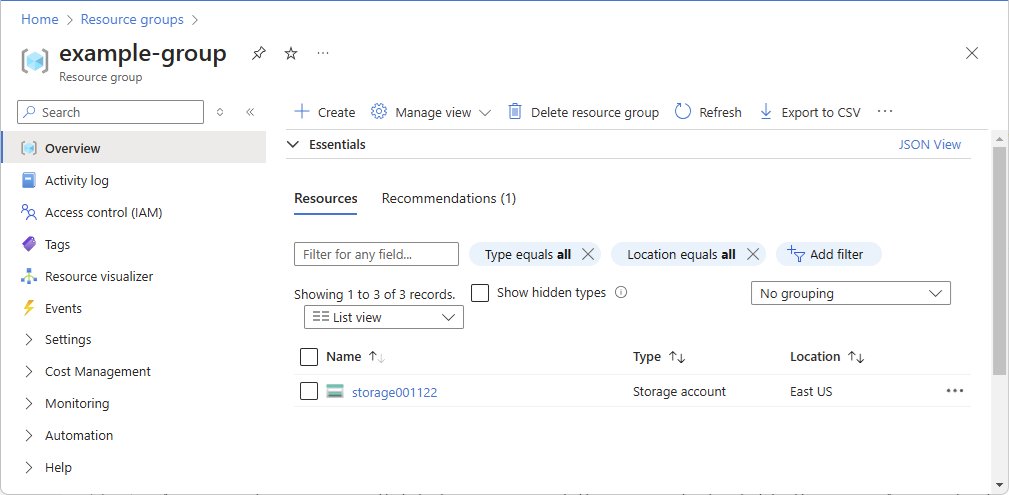
下面展示了一个示例资源组。
步骤 2:打开“添加角色分配”页面
“访问控制(IAM)”是一个页面,通常用于分配角色以授予对 Azure 资源的访问权限。 该功能也称为标识和访问管理 (IAM),会显示在 Azure 门户中的多个位置。
单击“访问控制(IAM)”。
下面显示了资源组的“访问控制(IAM)”页的示例。
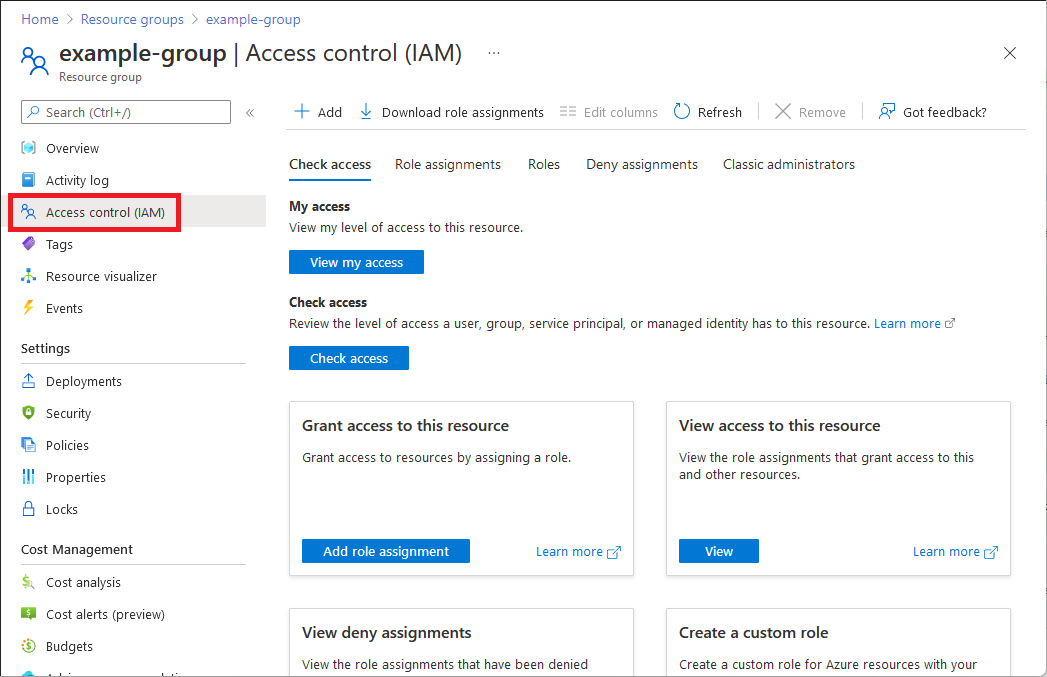
单击“角色分配”选项卡以查看在此范围内的角色分配。
单击添加>添加角色分配。
如果没有分配角色的权限,则将禁用“添加角色分配”选项。
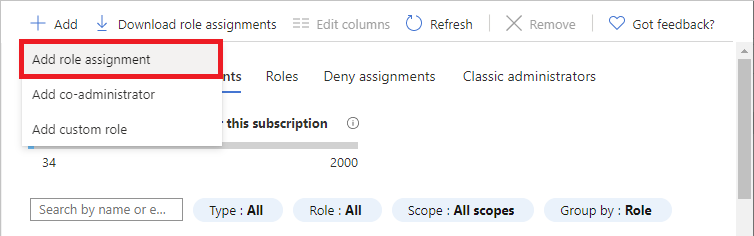
随即打开“添加角色分配”窗格。
步骤 3:选择合适的角色
要选择角色,请执行以下步骤:
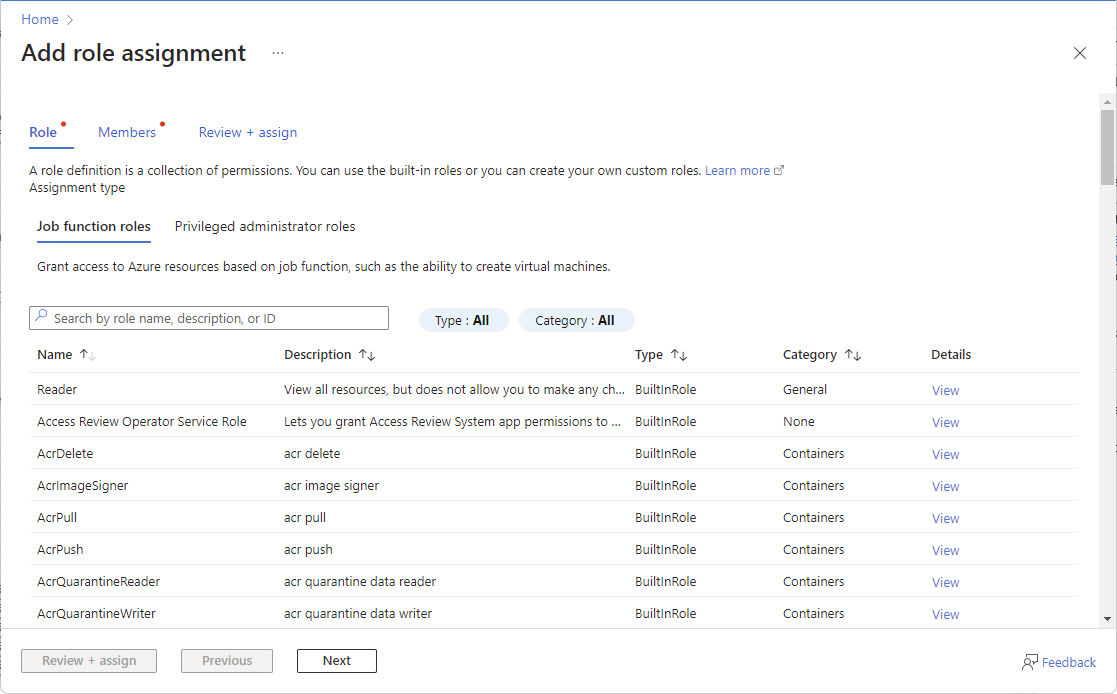
在“角色”选项卡上,选择要使用的角色。
可按名称或说明搜索角色。 还可按类型和类别筛选角色。
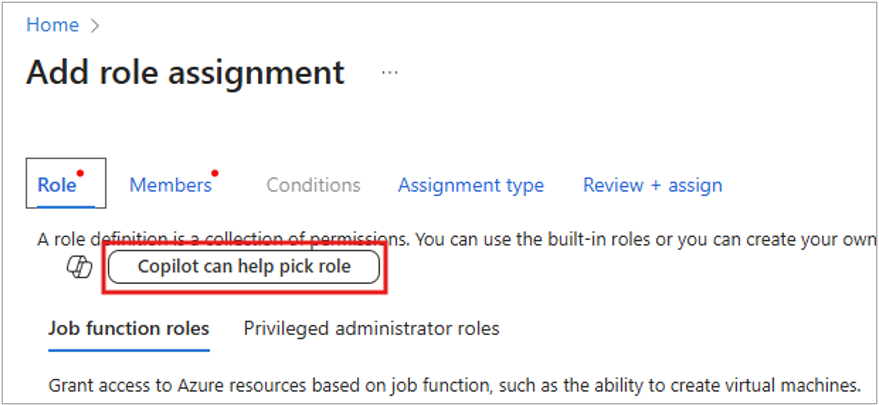
请注意,如果不确定需要分配哪个角色,现在可以使用 Copilot 来帮助选择适当的角色。 (有限预览版)。此功能正在分阶段部署,因此它可能尚未在租户中提供,或者界面可能看起来不同。
(可选)在“ 角色 ”选项卡中,单击 “Copilot”可以帮助选取角色 按钮。 此时将打开 Copilot 对话框。
在对话框中,可以添加描述性提示来告知 Copilot 你对角色的要求,以及需要授权用户执行哪些作,例如 ,“帮助我选择一个角色来部署和管理 Azure Functions”。或者 “如果希望用户管理和查看工作区,我应使用哪个角色?” 使用短语(如 “帮助我选择...”) 或 “我应该使用哪个角色...” 来帮助 Copilot 更清楚地了解你的意图,以便提供最佳结果。
根据提示的方向,Copilot 根据提供的要求建议一个角色或多个角色。 Copilot 要求你通过 “选择”权限进行确认。 然后,Copilot 根据所提供的标准推荐一个角色。 可以选择 角色,也可以要求 Copilot 推荐其他角色。 如果选择 “选择角色”,则返回到“ 添加角色分配 ”页,可在其中选择建议的角色并查看其详细信息。
如果要分配特权管理员角色,请选择“特权管理员角色”选项卡以选择角色。
有关使用特权管理员角色分配时的最佳做法,请参阅 Azure RBAC 最佳做法。
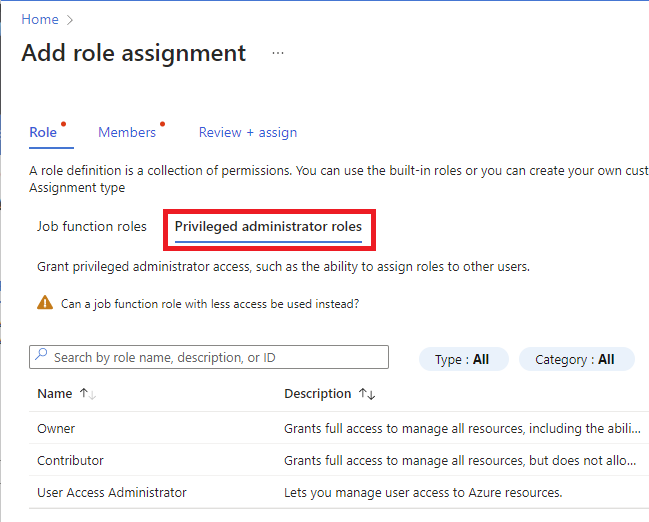
在“ 详细信息 ”列中,单击“ 视图 ”获取有关角色的更多详细信息。
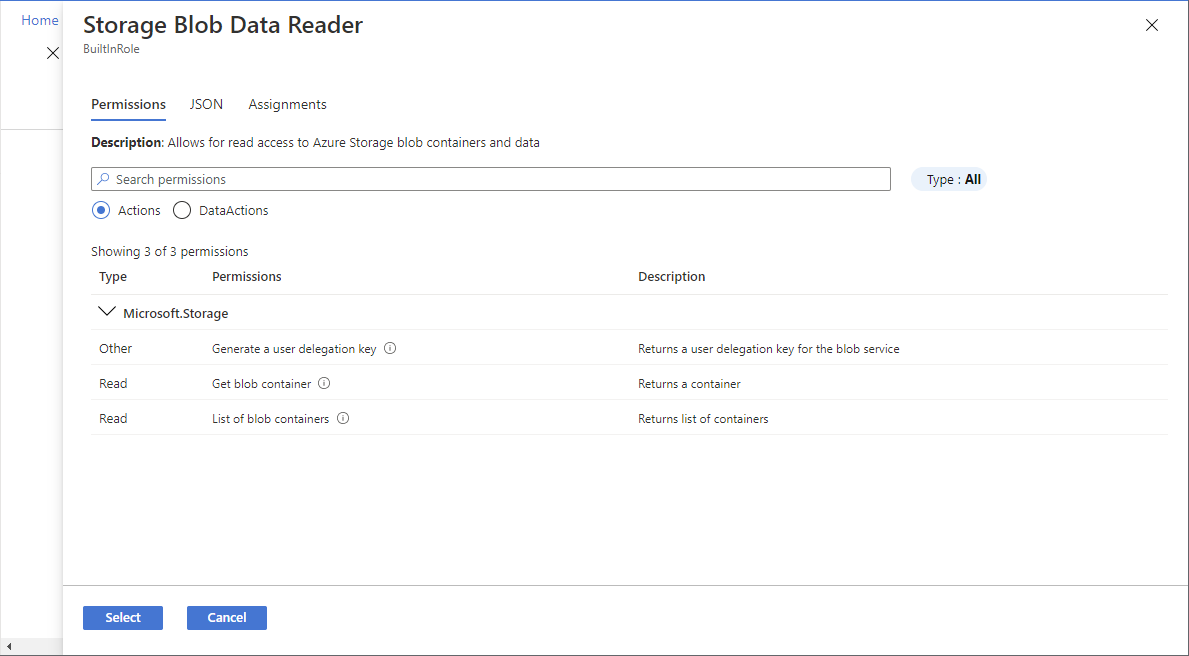
单击 “下一步” 。
步骤 4:选择需要访问权限的人员
要选择需要访问权限的人员,请执行以下步骤:
在“成员”选项卡上选择“用户、组或服务主体”,将所选角色分配给一个或多个 Microsoft Entra 用户、组或服务主体(应用程序)。
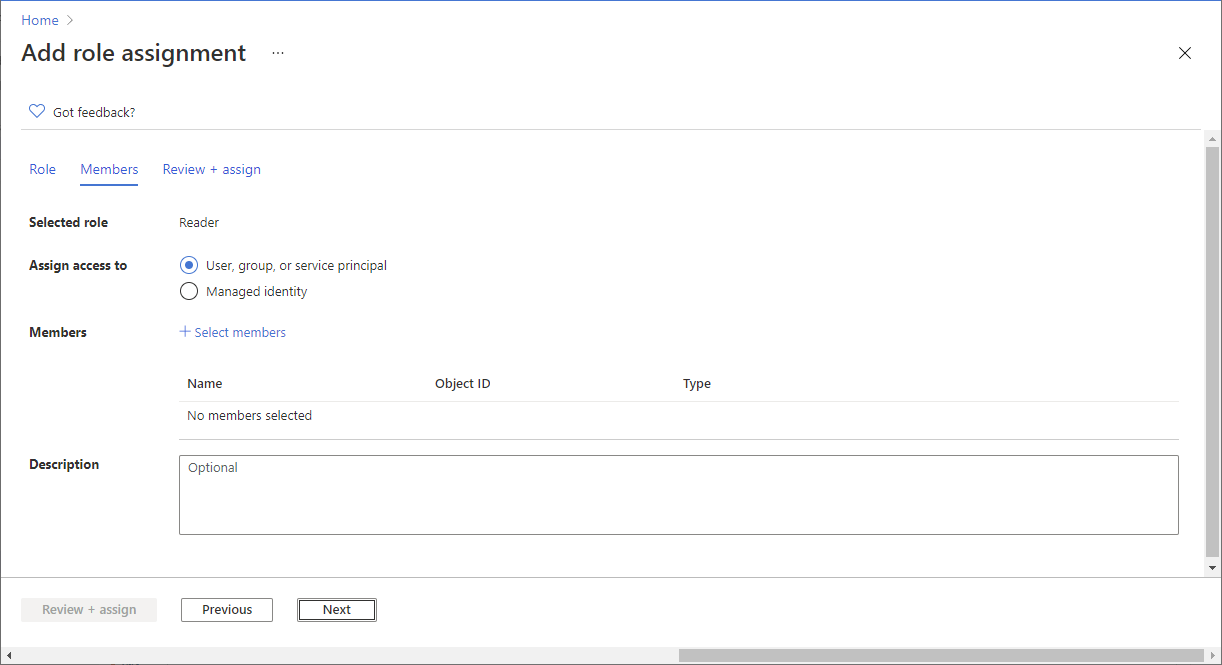
单击 “选择成员”。
查找并选择用户、组或服务主体。
可以在“选择”框中键入,以在目录中搜索显示名称或电子邮件地址。
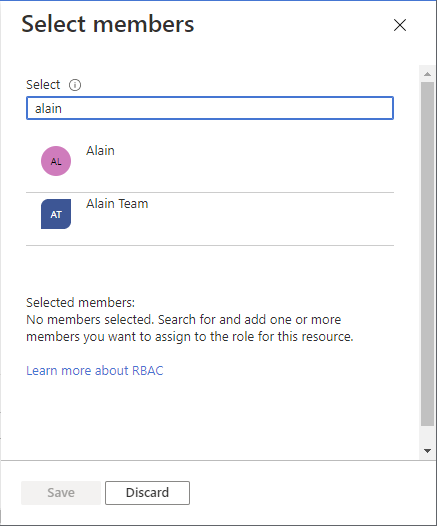
单击 “选择” ,将用户、组或服务主体添加到“成员”列表中。
要将所选角色分配给一个或多个托管标识,请选择“托管标识”。
单击 “选择成员”。
在“选择托管标识”窗格中,选择该类型是用户分配的托管标识还是系统分配的托管标识。
查找并选择托管标识。
对于系统分配的托管标识,你可以通过 Azure 服务实例选择托管标识。
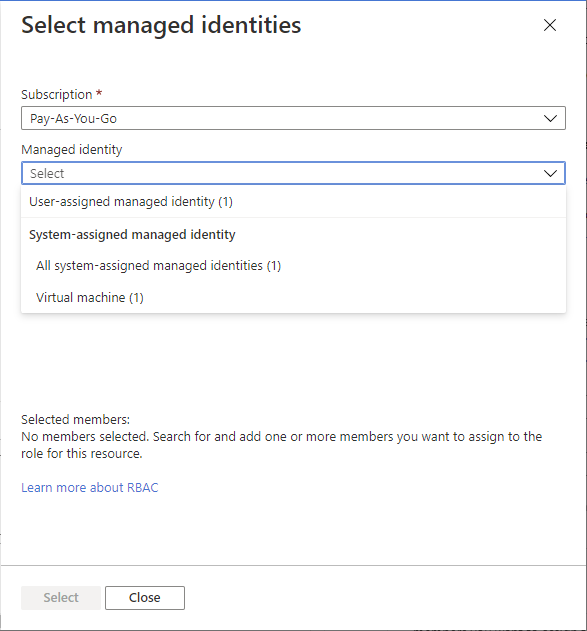
单击 “选择” 将托管标识添加到“成员”列表。
在“说明”文本框中,输入此角色分配的可选说明。
稍后,可以在“角色分配”列表中显示此说明。
单击 “下一步” 。
步骤 5:(可选)添加条件
如果所选角色支持使用条件,将会显示“条件”选项卡,你可选择向角色分配添加条件。 条件是可选择性地添加到角色分配中的一项额外检查,可提供更精细的访问控制。
“条件”选项卡看起来可能会有所不同,具体取决于所选角色。
存储条件
如果选择了以下之一的存储角色,请按照该部分的步骤进行操作。
如果要根据存储属性进一步优化角色分配,请单击“ 添加条件 ”。
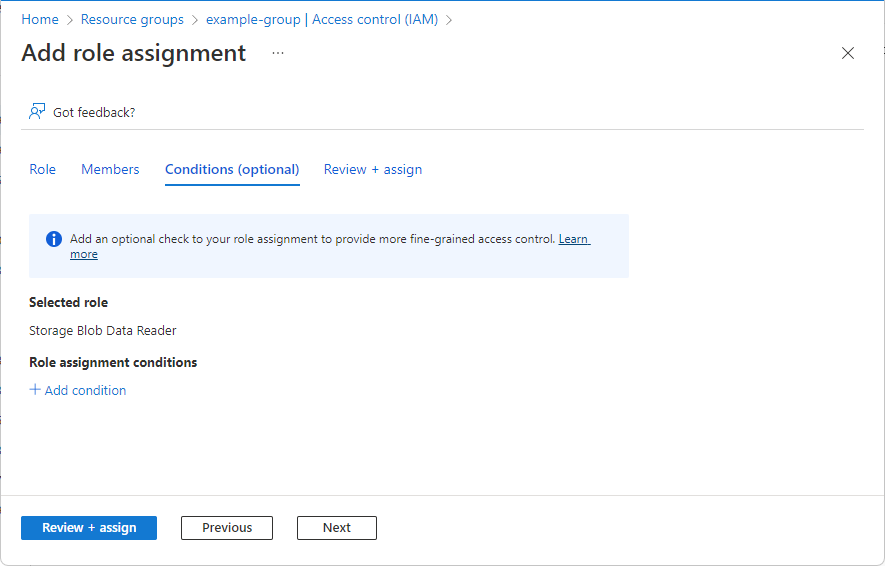
按照 添加或编辑 Azure 角色分配条件中的步骤进行。
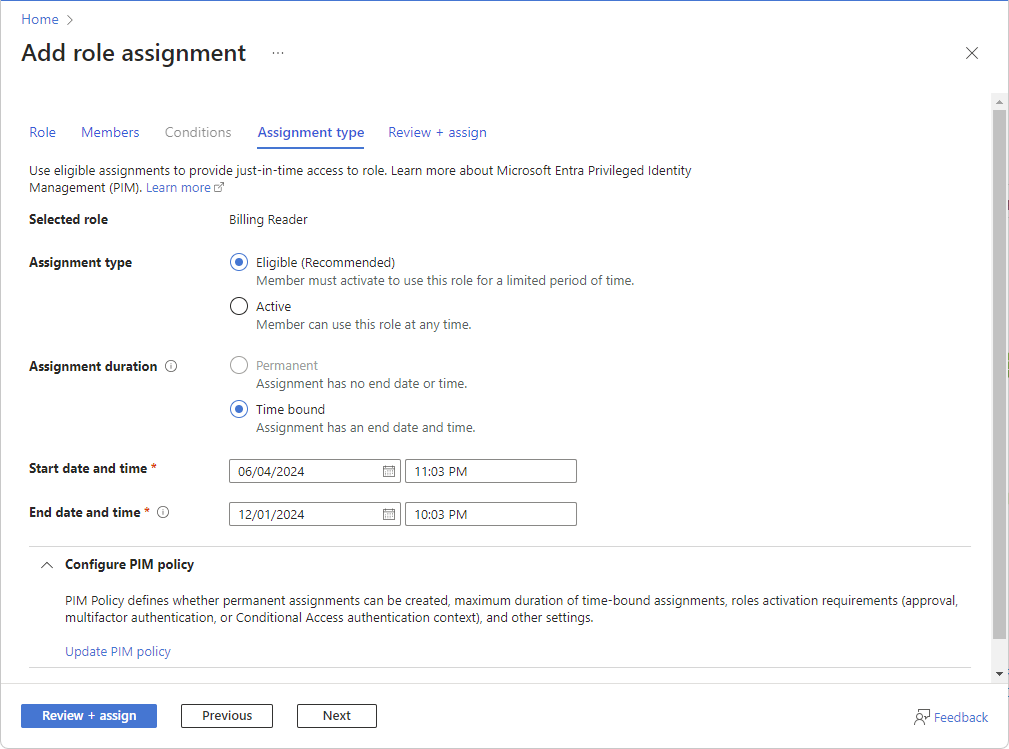
步骤 6:选择分配类型
如果你有 Microsoft Entra ID P2 或 Microsoft Entra ID 治理许可证,则会显示管理组、订阅和资源组范围的“分配类型”选项卡。 使用符合条件的分配提供对角色的实时访问权限。 具有符合条件和/或有时间限制的分配的用户必须具有有效的许可证。
如果不想使用 PIM 功能,请选择“活动”分配类型和“永久”分配持续时间选项。 这些设置创建一个角色分配,其中主体在角色中始终具有权限。
此功能正在分阶段部署,因此它可能在租户中尚不可用,或者你的界面可能看起来有所不同。
在“分配类型”选项卡上,选择“分配类型”。
- 合格 - 用户必须执行一项或多项操作才能使用该角色,例如执行多重身份验证检查、提供业务理由或请求指定审批人的批准。 无法为应用程序、服务主体或托管标识创建符合条件的角色分配,因为它们无法执行激活步骤。
- 活动 - 用户无需执行任何作才能使用该角色。
根据设置,对于 工作分配持续时间,请选择 “永久 ”或 “时间限制”。
如果希望始终允许成员激活或使用角色,请选择“永久”。 选择时限来指定开始和结束日期。 如果 PIM 策略不允许创建永久分配,则此选项可能会被禁用。
如果选择了“限时”,请设置“开始日期和时间”以及“开始日期和时间”来指定何时允许用户激活或使用角色。
可以设置将来的开始日期。 允许的最长合格持续时间取决于 Privileged Identity Management (PIM) 政策。
(可选)使用“配置 PIM 策略”来配置过期选项、角色激活要求(批准、多重身份验证或条件访问身份验证上下文)和其他设置。
选择“更新 PIM 策略”链接时,系统将显示 PIM 页面。 选择“设置”,为角色配置 PIM 策略。 有关详细信息,请参阅在 Privileged Identity Management 中配置 Azure 资源角色设置。
单击 “下一步” 。
步骤 7:分配角色
在“查看 + 分配”选项卡上,查看角色分配设置。
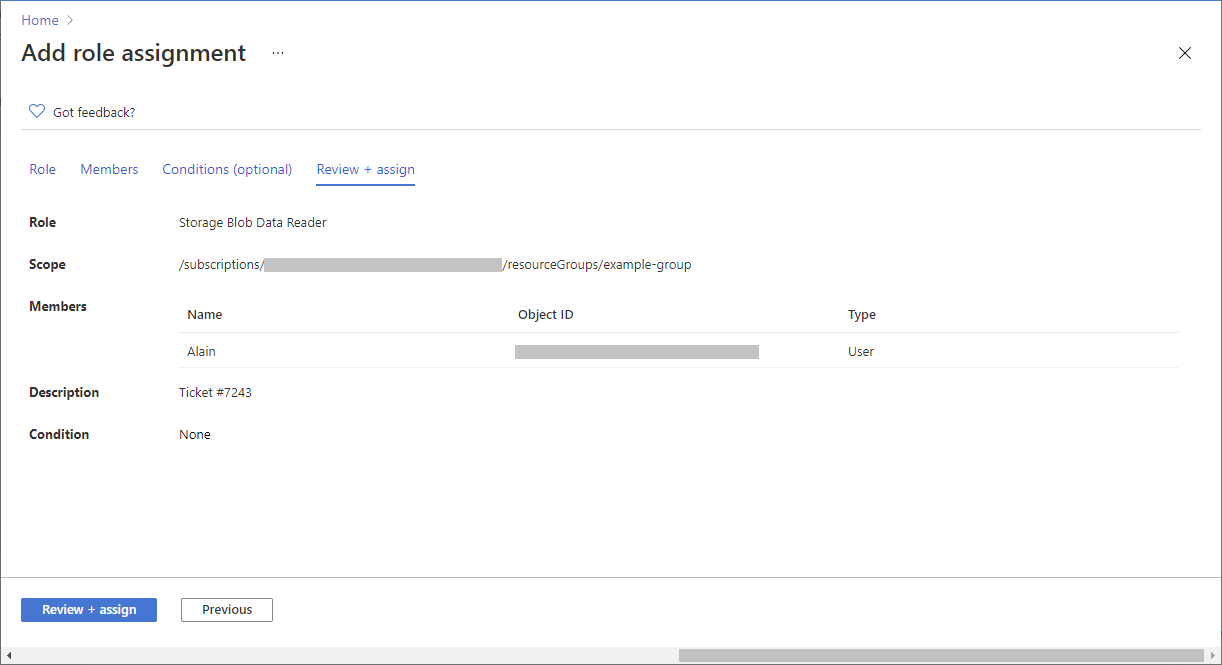
单击“ 查看 + 分配 ”以分配角色。
片刻之后,会在所选范围内为安全主体分配角色。
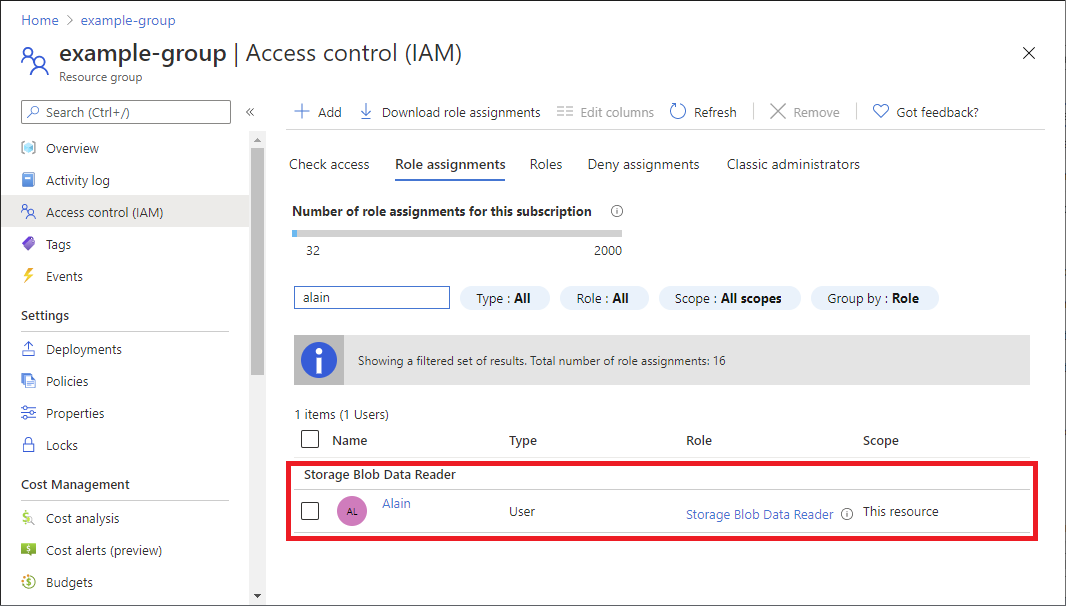
如果未看到角色分配的说明,请单击 “编辑列 ”以添加 “说明 ”列。
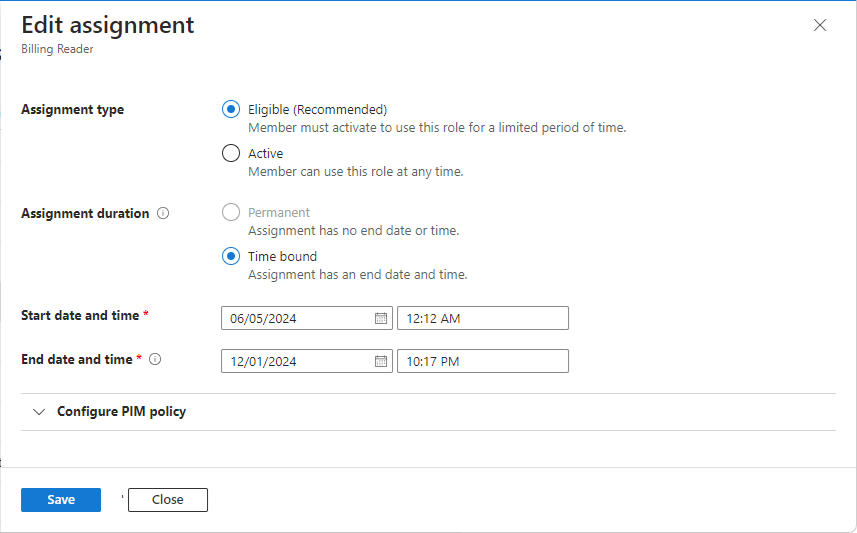
编辑分配
如果你拥有 Microsoft Entra ID P2 或 Microsoft Entra ID Governance 许可证,则可以编辑角色分配类型设置。
在 “访问控制”(IAM) 页上,单击“ 角色分配 ”选项卡以查看此范围的角色分配。
查找要编辑的角色分配。
在 “状态 ”列中,单击链接,例如 “符合条件的时间限制 ”或 “活动永久”。
系统会显示“编辑分配”窗格,你可以在其中更新角色分配类型设置。 窗格可能需要一些时间才能打开。
完成后,单击“保存”。
系统可能需要一段时间才能处理更新并将其反映在门户中。