本文介绍如何诊断虚拟机(VM)的网络流量筛选问题。 此过程涉及查看网络安全组(NSG)应用的有效安全规则。
使用 NSG 可以控制流入和流出 VM 的流量类型。 可将 NSG 关联到 Azure 虚拟网络中的子网和/或附加到 VM 的网络接口。 应用到网络接口的有效安全规则是网络接口关联的 NSG 规则和网络接口所在子网的 NSG 规则的综合。 不同 NSG 中的规则有时会相互冲突,并影响 VM 的网络连接。 可以查看 NSG 中对 VM 网络接口应用的所有有效安全规则。 如果不熟悉虚拟网络、网络接口或 NSG 的概念,请参阅虚拟网络概述、网络接口和网络安全组概述。
情景
尝试通过端口 80 从 Internet 连接到 VM,但连接失败。 若要确定为何无法从 Internet 访问端口 80,可以使用 Azure 门户、PowerShell 或 Azure CLI 查看网络接口的有效安全规则。
以下步骤假定您已有一个现有的 VM,并您希望查看其安全规则的有效性。 如果没有 VM,请先部署 Linux 或 Windows VM 以完成本文中的任务。 本文中的示例适用于名为 myVM 的 VM,其中包含名为 myVMVMNic 的网络接口。 VM 和网络接口位于名为 myResourceGroup 的资源组中,位于 中国东部 区域。 针对想要诊断其问题的 VM,相应地更改步骤中的值。
使用 Azure 门户诊断
在 Azure 门户顶部的搜索框中输入 VM 的名称。 当 VM 名称显示在搜索结果中时,请选择它。
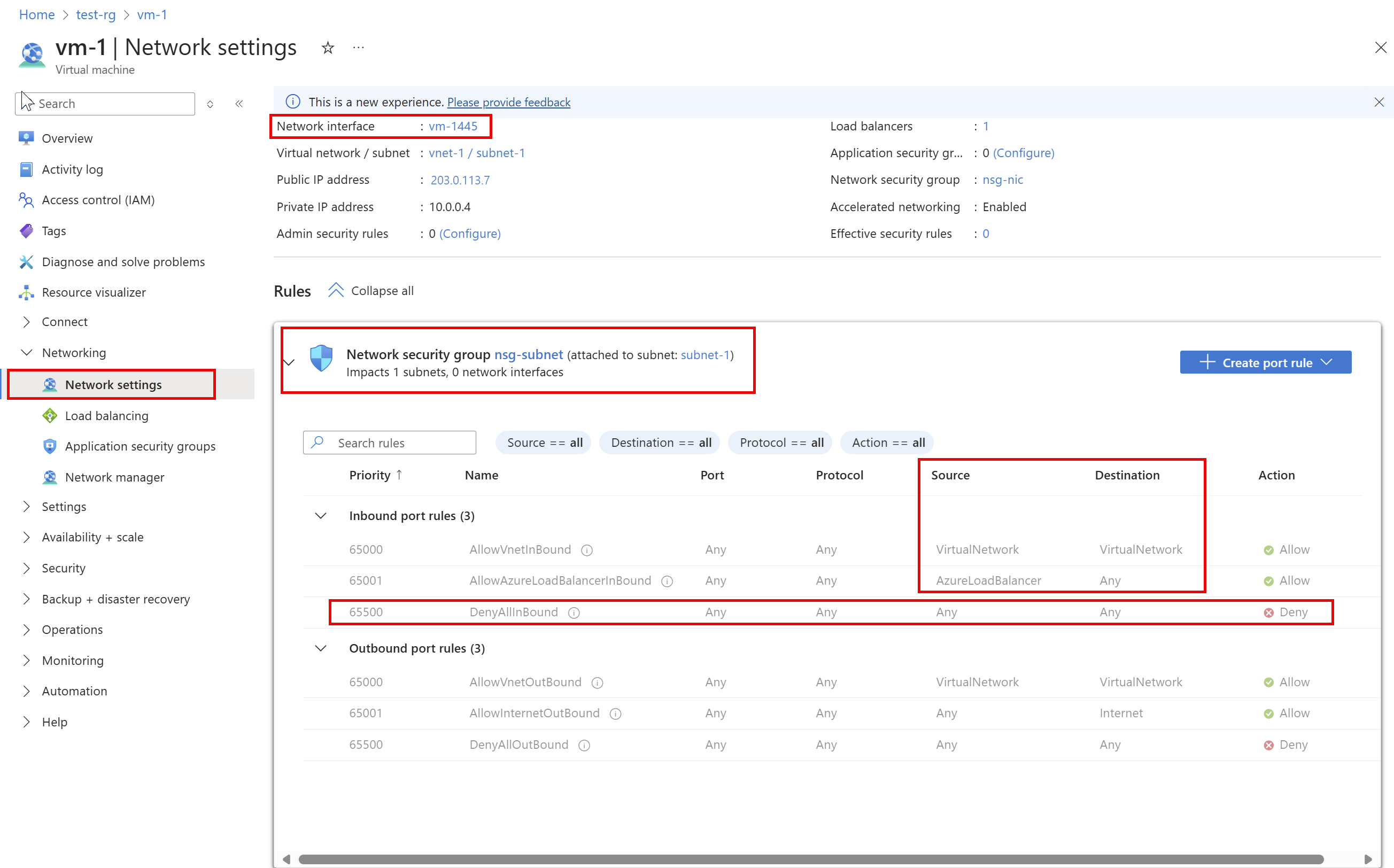
在左窗格中展开“网络”。 选择 “网络设置”。 下图显示了 VM 网络接口的网络安全组设置。
上图中列出的规则适用于名为 vm-1445 的网络接口。 可以看到,网络接口有来自两个不同的网络安全组的 入站端口规则 :
- nsg-subnet:与网络接口所属的子网相关联。
- nsg-nic:与名为 vm-1445 的 VM 中的网络接口相关联。
如场景中所述,名为 DenyAllInBound 的规则阻止端口 80 从 Internet 与 VM 进行入站通信。 规则中为“源”列出了 0.0.0.0/0,其中包括 Internet。 没有其他具有更高优先级(较小的数字)的规则允许端口 80 入站。 若要允许通过端口 80 从 Internet 与 VM 进行入站通信,请参阅解决问题。 若要详细了解安全规则以及 Azure 如何应用这些规则,请参阅网络安全组。
在图片底部,还会看到 出站端口规则。 列出了网络接口的出站端口规则。
尽管图片中仅显示了每个 NSG 的四个入站规则,但 NSG 包含的规则可能远远超过四个。 在图片中,你会看到 VirtualNetwork 位于 Source 和 Destination 下,而 AzureLoadBalancer 位于 SOURCE 下。 VirtualNetwork 和 AzureLoadBalancer 是服务标记。 服务标记表示一组 IP 地址前缀,帮助最大程度地降低安全规则创建过程的复杂性。
若要查看有效的安全规则,请在虚拟机的网络设置中选择接口。 在继续作之前,请确保 VM 处于运行状态。
在网络接口的设置中,展开 “帮助”,然后选择“ 有效安全规则”。
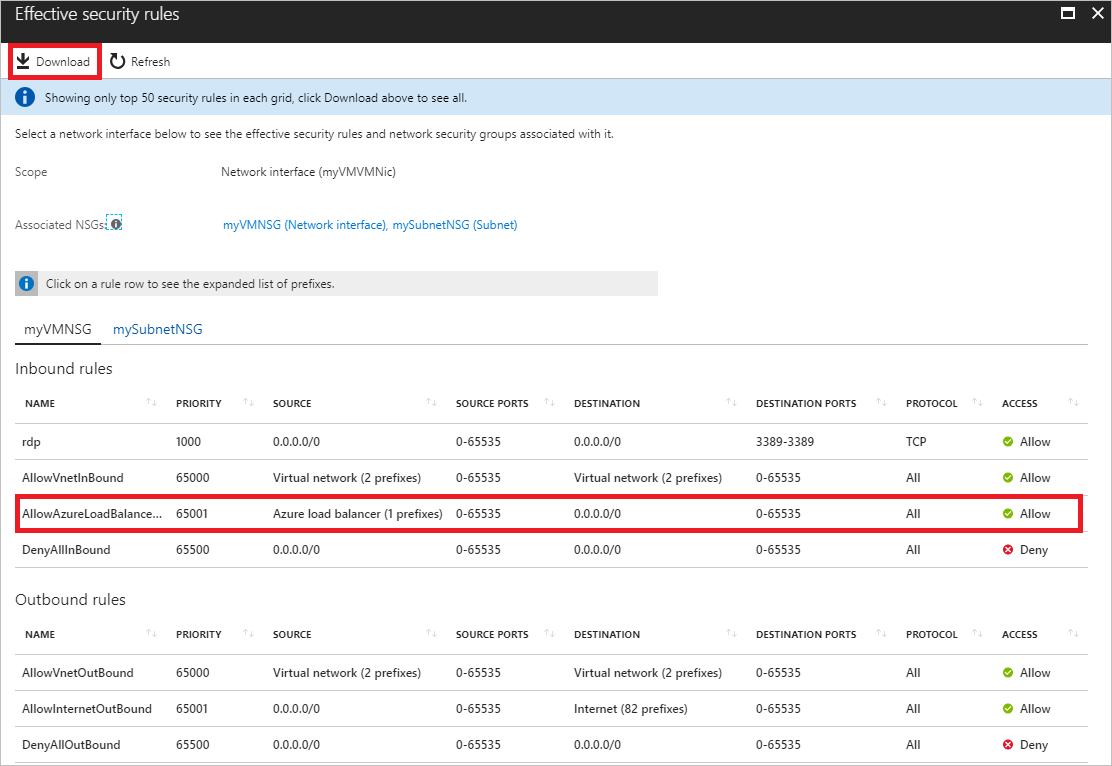
以下示例展示了示例网络接口vm-1445选择的有效安全规则。
列出的规则与步骤 3 中相同,不过,与网络接口和子网关联的 NSG 有不同的选项卡。 图片中只显示了前 50 个规则。 若要下载包含所有规则的 .csv 文件,请选择“下载”。
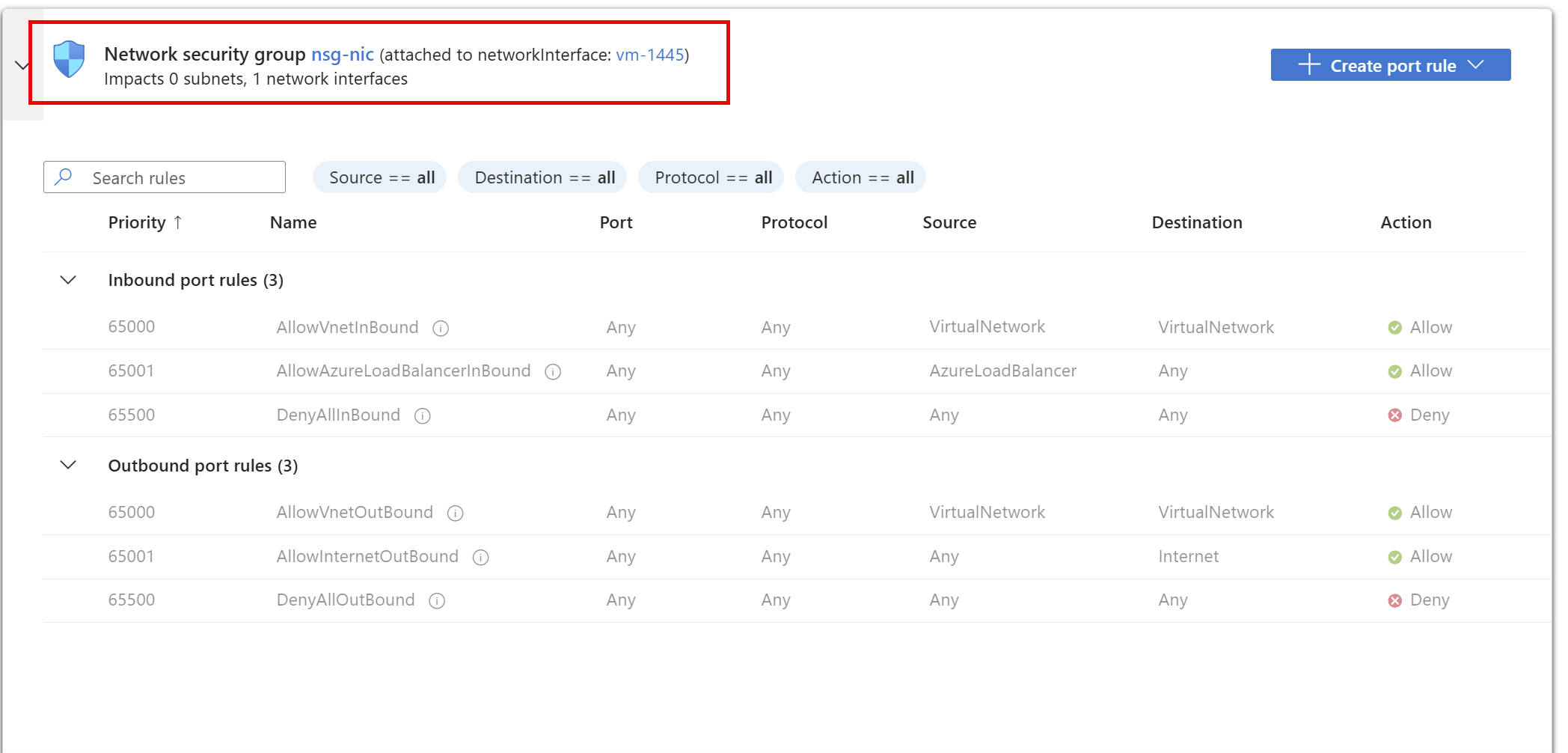
前面的步骤显示了名为 vm-1445 的网络接口的安全规则。 如果 VM 有两个网络接口,该怎么办? 本示例中的 VM 上附加了两个网络接口。 每个网络接口的有效安全规则可能不同。
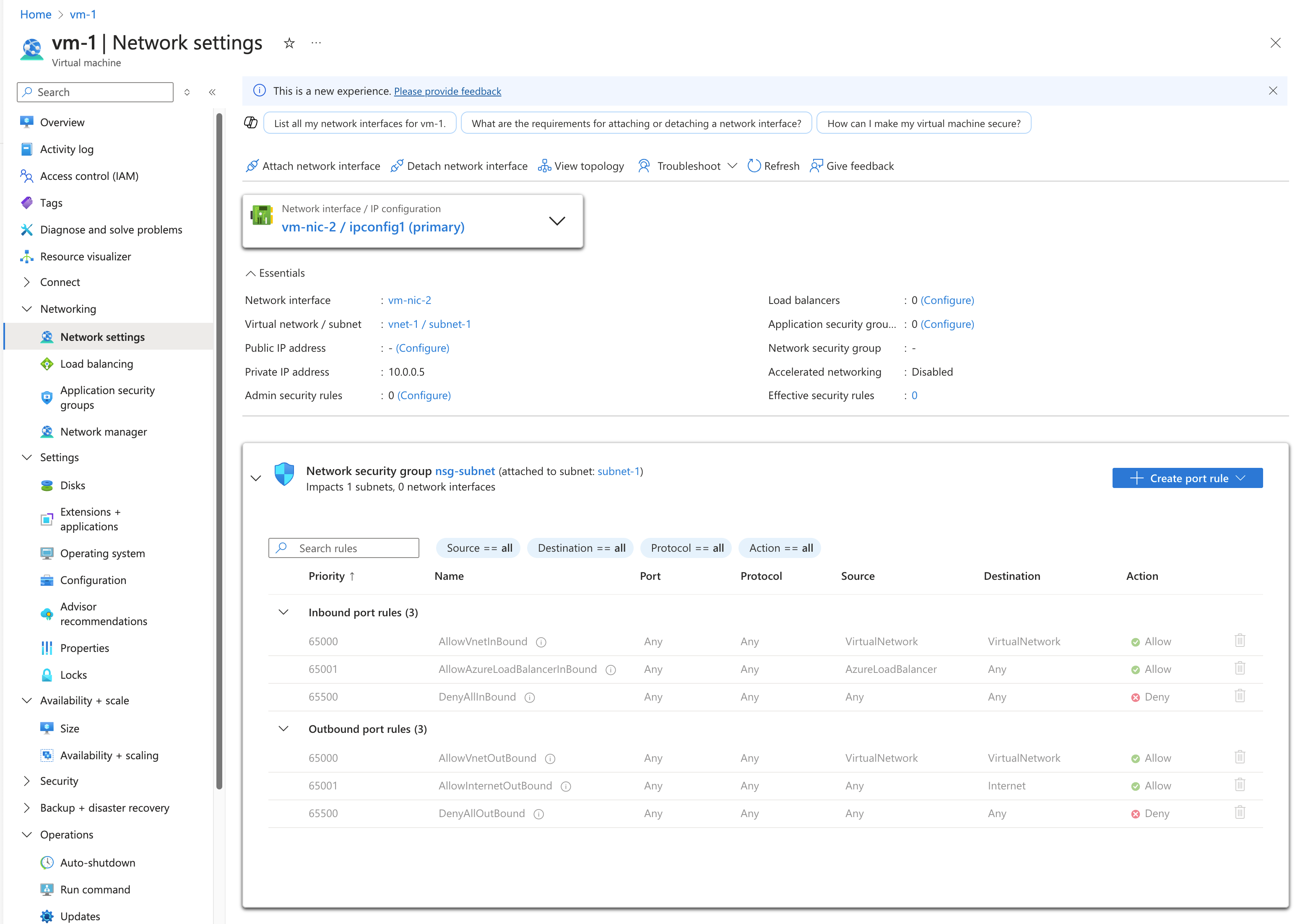
若要查看 vm-nic-2 网络接口的规则,请选择它。 如以下示例所示,网络接口与其子网关联的规则与 vm-1445 网络接口相同,因为两个网络接口位于同一子网中。 将 NSG 关联到某个子网时,其规则将应用到该子网中的所有网络接口。
与 vm-1445 网络接口不同, vm-nic-2 网络接口没有与之关联的网络安全组。 每个网络接口和子网可以有零个或一个关联的 NSG。 关联到每个网络接口或子网的 NSG 可以相同或不同。 可将同一网络安全组关联到选定的任意数量的网络接口和子网。
尽管可以通过 VM 查看有效安全规则,您也可以通过特定对象查看有效安全规则。
使用 PowerShell 诊断
注释
建议使用 Azure Az PowerShell 模块与 Azure 交互。 请参阅安装 Azure PowerShell 以开始使用。 若要了解如何迁移到 Az PowerShell 模块,请参阅 将 Azure PowerShell 从 AzureRM 迁移到 Az。
可以通过从计算机运行 PowerShell 来运行命令。 如果在计算机上运行 PowerShell,需要 Azure PowerShell 模块 1.0.0 或更高版本。 在计算机上运行 Get-Module -ListAvailable Az,找到已安装的版本。 如果需要升级,请参阅安装 Azure PowerShell 模块。 如果在本地运行 PowerShell,则还需要运行 Connect-AzAccount -Environment AzureChinaCloud,以使用拥有所需权限的帐户登录到 Azure。
使用 Get-AzEffectiveNetworkSecurityGroup 获取网络接口的有效安全规则。 以下示例获取名为 vm-nic 的网络接口的有效安全规则,该网络接口位于名为 test-rg 的资源组中:
$Params = @{
NetworkInterfaceName = "vm-nic"
ResourceGroupName = "test-rg"
}
Get-AzEffectiveNetworkSecurityGroup @Params
输出以 json 格式返回。 若要了解输出,请参阅解释命令输出。 仅当 NSG 已关联到网络接口和/或该网络接口所在的子网时,才返回输出。 VM 必须处于运行状态。 一台 VM 可能有多个应用了不同 NSG 的网络接口。 故障排除时,请针对每个网络接口运行该命令。
如果只知道 VM 名称,请使用以下命令列出附加到 VM 的所有网络接口 ID。
$Params = @{
Name = "vm-1"
ResourceGroupName = "test-rg"
}
$VM = Get-AzVM @Params
$VM.NetworkProfile
将会收到类似于以下示例的输出:
NetworkInterfaces
-----------------
{/subscriptions/<ID>/resourceGroups/myResourceGroup/providers/Microsoft.Network/networkInterfaces/vm-nic
在上一个输出中,网络接口名称为 vm-nic。
使用 Azure CLI 诊断
如果使用 Azure CLI 命令来完成本文中的任务,请运行 Azure Cloud Shell 中的命令,或从计算机运行 Azure CLI。 本文需要 Azure CLI 2.0.32 或更高版本。 运行 az --version 查找已安装的版本。 如果需要进行安装或升级,请参阅安装 Azure CLI。 如果在本地运行 Azure CLI,则还需要运行 az login,并使用拥有所需权限的帐户登录到 Azure。
使用 az network nic list-effective-nsg 获取网络接口的有效安全规则。 以下示例获取名为 vm-nic 的网络接口的有效安全规则,该网络接口位于名为 test-rg 的资源组中:
az network nic list-effective-nsg \
--name vm-nic \
--resource-group test-rg
输出以 json 格式返回。 若要了解输出,请参阅解释命令输出。 仅当 NSG 已关联到网络接口和/或该网络接口所在的子网时,才返回输出。 VM 必须处于运行状态。 一台 VM 可能有多个应用了不同 NSG 的网络接口。 故障排除时,请针对每个网络接口运行该命令。
如果只知道 VM 名称,请使用以下命令列出附加到 VM 的所有网络接口 ID。
az vm show \
--name vm-1 \
--resource-group test-rg
在返回的输出中,将会看到类似于以下示例的信息:
"networkProfile": {
"additionalProperties": {},
"networkInterfaces": [
{
"additionalProperties": {},
"id": "/subscriptions/<ID>/resourceGroups/test-rg/providers/Microsoft.Network/networkInterfaces/vm-nic",
"primary": true,
"resourceGroup": "test-rg"
},
在上一个输出中,网络接口名称为 vm-nic
解释命令输出
无论使用 PowerShell 还是 Azure CLI 诊断问题,都会收到包含以下信息的输出:
- NetworkSecurityGroup:网络安全组的 ID。
- 关联:指示网络安全组是链接到 NetworkInterface 还是 子网。 如果在运行命令之前 NSG 的关联状态发生更改,请等待几秒钟,让输出反映更新。
- EffectiveSecurityRules:创建安全规则中详细解释了每个属性。 带有 defaultSecurityRules/ 前缀的规则名称是每个 NSG 中存在的默认安全规则。 以 securityRules/ 开头的规则名称是用户创建的规则。 为 destinationAddressPrefix 或 sourceAddressPrefix 属性指定服务标记(例如 Internet、VirtualNetwork 和 AzureLoadBalancer)的规则也包含 expandedDestinationAddressPrefix 属性的值。 expandedDestinationAddressPrefix 属性列出服务标记表示的所有地址前缀。
当 NSG 同时链接到网络接口和子网时,输出中会出现重复的规则。 默认规则和 NSG 之间共享的任何自定义规则都会导致这些重复项。
如场景中所述,名为 defaultSecurityRules/DenyAllInBound 的规则阻止端口 80 从 Internet 与 VM 进行入站通信。 其他更高优先级(较小的数字)的规则都不允许通过端口 80 从 Internet 进行入站通信。
解决问题
可以使用 Azure 门户、PowerShell 或 Azure CLI 诊断方案中描述的问题。 解决方案是创建具有以下属性的网络安全规则:
| 资产 | 价值 |
|---|---|
| 来源 | 任意 |
| 源端口范围 | 任意 |
| 目的地 | VM 的 IP 地址、IP 地址范围,或子网中的所有地址。 |
| 目标端口范围 | 80 |
| 协议 | TCP |
| 行动 | 允许 |
| 优先度 | 100 |
| 名称 | 允许-HTTP-All |
创建规则后,允许从 Internet 入站端口 80,因为它的优先级高于默认的 DenyAllInBound 规则。 如果 NSG 同时与网络接口和子网相关联,请在这两个 NSG 中创建相同的规则。 了解如何创建安全规则。
当 Azure 处理入站流量时,它会处理与子网关联的 NSG 中的规则(如果有关联的 NSG),然后处理与网络接口关联的 NSG 中的规则。 如果存在与网络接口和子网关联的 NSG,则必须在两个 NSG 中打开该端口,以便流量到达 VM。 为便于解决管理和通信问题,我们建议将 NSG 关联到子网,而不要关联到单个网络接口。 如果子网中的 VM 需要不同的安全规则,可使网络接口成为应用程序安全组 (ASG) 的成员,并将某个 ASG 指定为安全规则的源和目标。 详细了解应用程序安全组。
如果仍然遇到通信问题,请参阅 “注意事项 ”和更多诊断。
注意事项
排查连接问题时,请注意以下几点:
默认安全规则阻止来自 Internet 的入站访问,只允许来自虚拟网络的入站流量。 若要允许来自 Internet 的入站流量,请添加优先级高于默认规则的安全规则。 详细了解默认安全规则,或如何添加安全规则。
对于对等虚拟网络,默认情况下,VIRTUAL_NETWORK 服务标记会自动扩展,以包含对等虚拟网络的前缀。 若要排查与虚拟网络对等连接相关的任何问题,可以查看 ExpandedAddressPrefix 列表中的前缀。 详细了解虚拟网络对等互连和服务标签。
当 NSG 与 VM 的网络接口或子网关联时,Azure 才显示网络接口的有效安全规则。 此外,VM 必须处于运行状态。
如果网络接口或子网缺少关联的 NSG,则当 VM 具有 公共 IP 地址时,所有端口都保持打开状态进行入站和出站访问。 此配置允许从任意位置进行不受限制的访问。 若要保护 VM,请将 NSG 应用于托管网络接口的子网(如果具有公共 IP 地址)。
更多诊断
- 若要运行快速测试来确定是否允许传入或传出 VM 的流量,请使用 Azure 网络观察程序的 IP 流验证功能。 IP 流验证会告知是允许还是拒绝了流量。 如果被拒绝,IP 流验证会告知哪个安全规则拒绝了流量。
- 如果没有安全规则导致 VM 的网络连接失败,则问题可能是:
- VM 操作系统中运行的防火墙软件
- 为虚拟设备或本地流量配置的路由。 Internet 流量可以通过强制隧道重定向到本地网络。 如果通过强制隧道将 Internet 流量定向到虚拟设备或本地,可能无法从 Internet 连接到 VM。 若要了解如何诊断可能导致流量流出 VM 的路由问题,请参阅 诊断虚拟机网络流量路由问题。
后续步骤
- 了解网络安全组和安全规则的所有任务、属性和设置。
- 了解 VM 的默认安全规则、服务标记,以及 Azure 如何处理入站和出站流量的安全规则。