Azure 专用链接是一项技术,允许你通过公开专用终结点,使用专用 IP 地址连接来连接 Azure 平台即服务产品。 使用 Azure 虚拟 WAN,可以在一个连接到任何虚拟中心的虚拟网络中部署专用终结点。 此专用链接提供了与连接到同一虚拟网络的任何其他虚拟 WAN 或分支的连接。
在您开始之前
本文中的步骤假定你部署了一个虚拟 WAN,其中包含一个或多个中心和至少两个连接到虚拟 WAN 的虚拟网络。
要创建新虚拟 WAN 和新中心,请使用以下文章中的步骤:
创建专用链接终结点
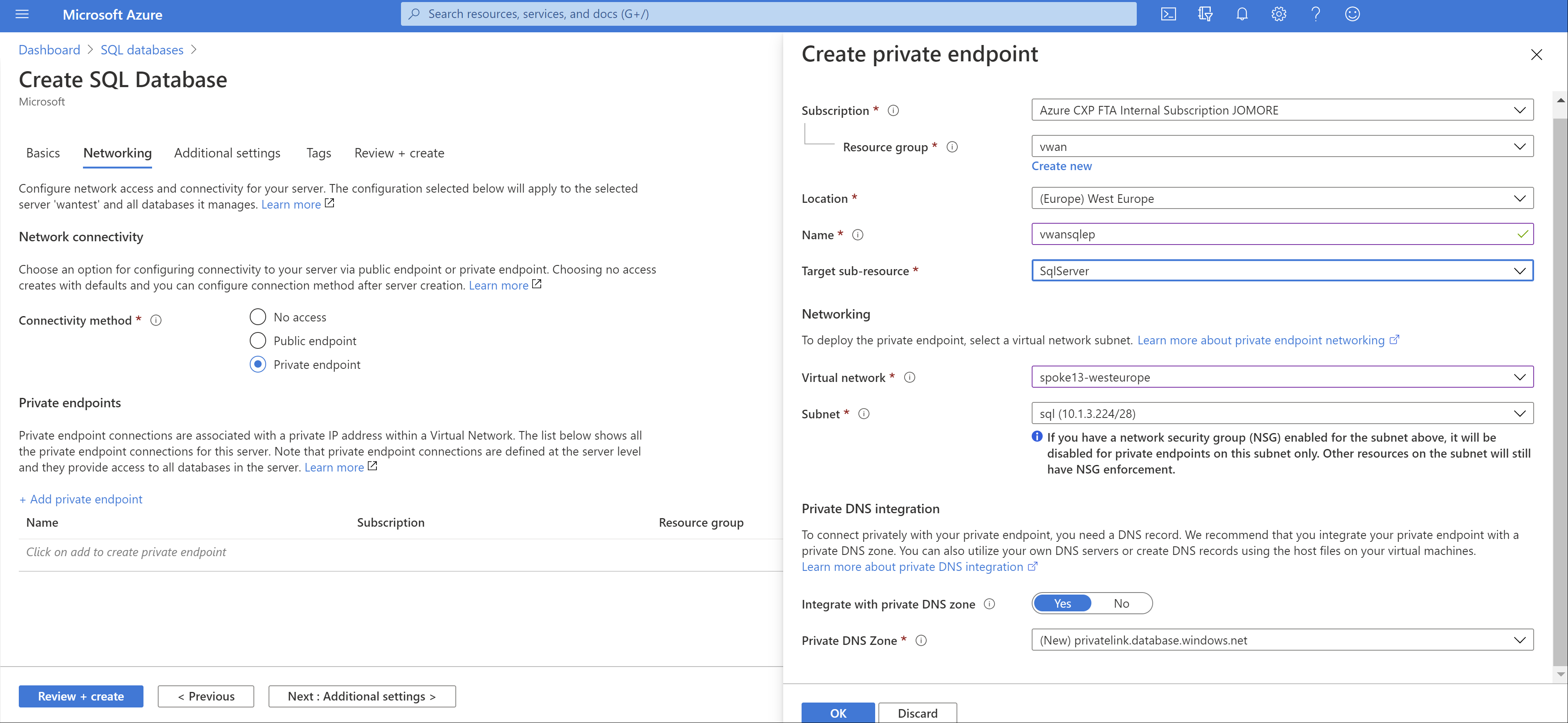
可以为许多不同服务创建专用链接终结点。 在此示例中,我们使用 Azure SQL 数据库。 有关如何为 Azure SQL 数据库创建专用终结点的详细信息,请参阅快速入门:使用 Azure 门户创建专用终结点。 下图显示了 Azure SQL 数据库的网络配置:
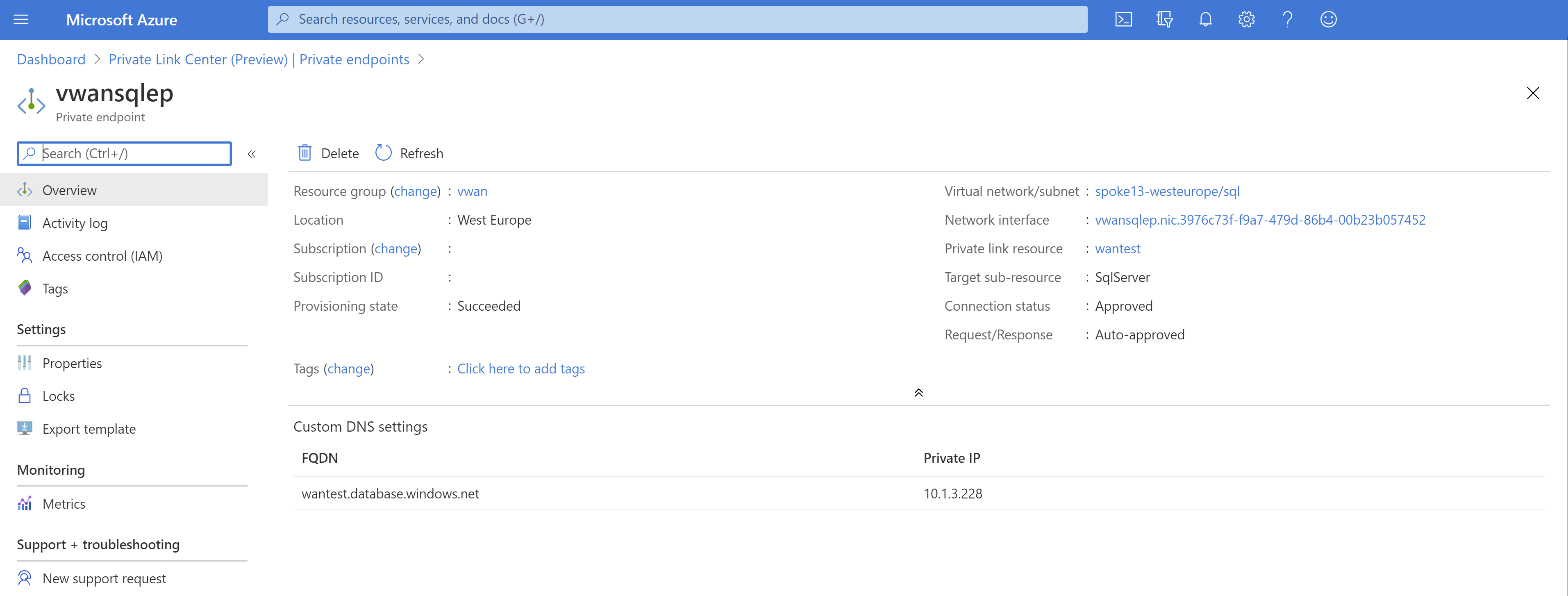
创建 Azure SQL 数据库之后,可以通过浏览专用终结点来验证专用终结点 IP 地址:
单击我们创建的专用终结点,应会看到其专用 IP 地址及其完全限定的域名(FQDN)。 专用终结点的 IP 地址应在 VNet 范围 (10.1.3.0/24) 内:
验证来自同一 VNet 的连接
在此示例中,我们验证了从安装了 MS SQL 工具的 Linux 虚拟机到 Azure SQL 数据库的连接。 第一步是在部署专用终结点的同一 VNet(10.1.3.0/24)中验证 DNS 解析是否正常工作,并将 Azure SQL 数据库完全限定的域名解析为专用 IP 地址:
nslookup wantest.database.chinacloudapi.cn
Server: 127.0.0.53
Address: 127.0.0.53#53
Non-authoritative answer:
wantest.database.chinacloudapi.cn canonical name = wantest.privatelink.database.chinacloudapi.cn.
Name: wantest.privatelink.database.chinacloudapi.cn
Address: 10.1.3.228
如您在上一输出中所见,FQDN wantest.database.chinacloudapi.cn 映射到 wantest.privatelink.database.chinacloudapi.cn,与专用终结点一起创建的专用 DNS 区域解析为专用 IP 地址 10.1.3.228。 查看专用 DNS 区域,以确认专用终结点映射到专用 IP 地址的 A 记录是否存在:
验证正确的 DNS 解析后,可以尝试连接到数据库:
query="SELECT CONVERT(char(15), CONNECTIONPROPERTY('client_net_address'));"
sqlcmd -S wantest.database.chinacloudapi.cn -U $username -P $password -Q "$query"
10.1.3.75
如你所见,我们使用的是一个特殊的 SQL 查询,该查询提供了 SQL 服务器从客户端看到的源 IP 地址。 在这种情况下,服务器会看到具有其专用 IP (10.1.3.75) 的客户端,这意味着流量从 VNet 直接流入专用终结点。
将变量 username 和 password 设置为与在 Azure SQL 数据库中定义的凭据匹配的值,从而使本指南中的示例生效。
从其他 VNet 连接
既然 Azure 虚拟 WAN 中的一个 VNet 可以连接到专用终结点,那么连接到虚拟 WAN 的所有其他 VNet 和分支就也可以访问该终结点。 你需要通过 Azure 虚拟 WAN 支持的任何模型(举两个例子,任意连接性方案或共享服务 VNet 方案)提供连接。
在 VNet 或分支与已部署专用终结点的 VNet 之间建立连接后,需要配置 DNS 解析:
- 如果从 VNet 连接到专用终结点,则可以使用通过 Azure SQL 数据库创建的同一专用区域。
- 如果从分支(站点到站点 VPN、点到站点 VPN 或 ExpressRoute)连接到专用终结点,则需要使用本地 DNS 解析。
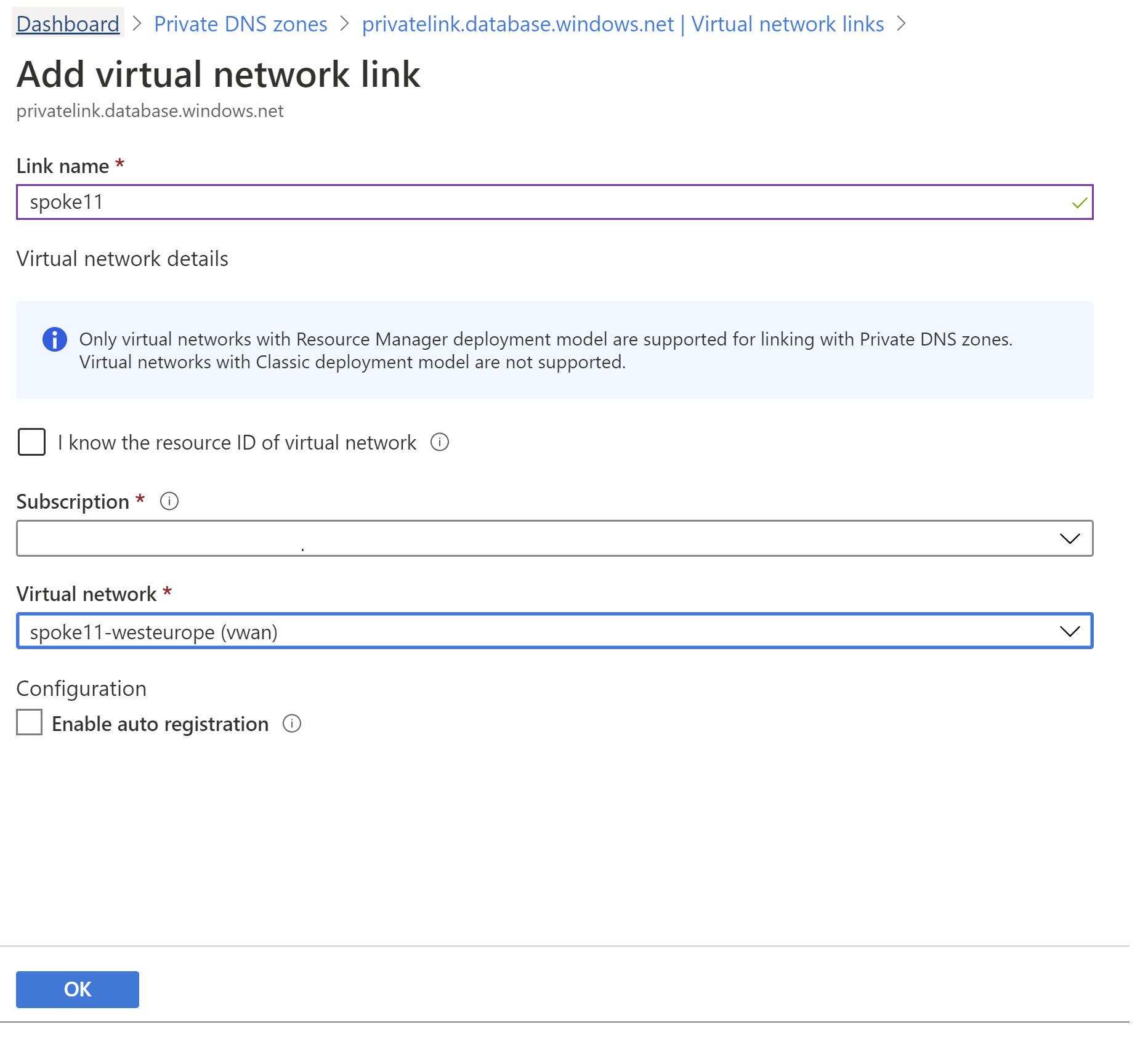
在此示例中,我们从其他 VNet 进行连接。 首先将专用 DNS 区域附加到这个新的 VNet,使其工作负荷能够将 Azure SQL 数据库完全限定的域名解析为专用 IP 地址。 此操作通过将专用 DNS 区域链接到新的 VNet 来完成:
现在,附加 VNet 中的任何虚拟机都应将 Azure SQL 数据库 FQDN 正确解析为专用链接的专用 IP 地址:
nslookup wantest.database.chinacloudapi.cn
Server: 127.0.0.53
Address: 127.0.0.53#53
Non-authoritative answer:
wantest.database.chinacloudapi.cn canonical name = wantest.privatelink.database.chinacloudapi.cn.
Name: wantest.privatelink.database.chinacloudapi.cn
Address: 10.1.3.228
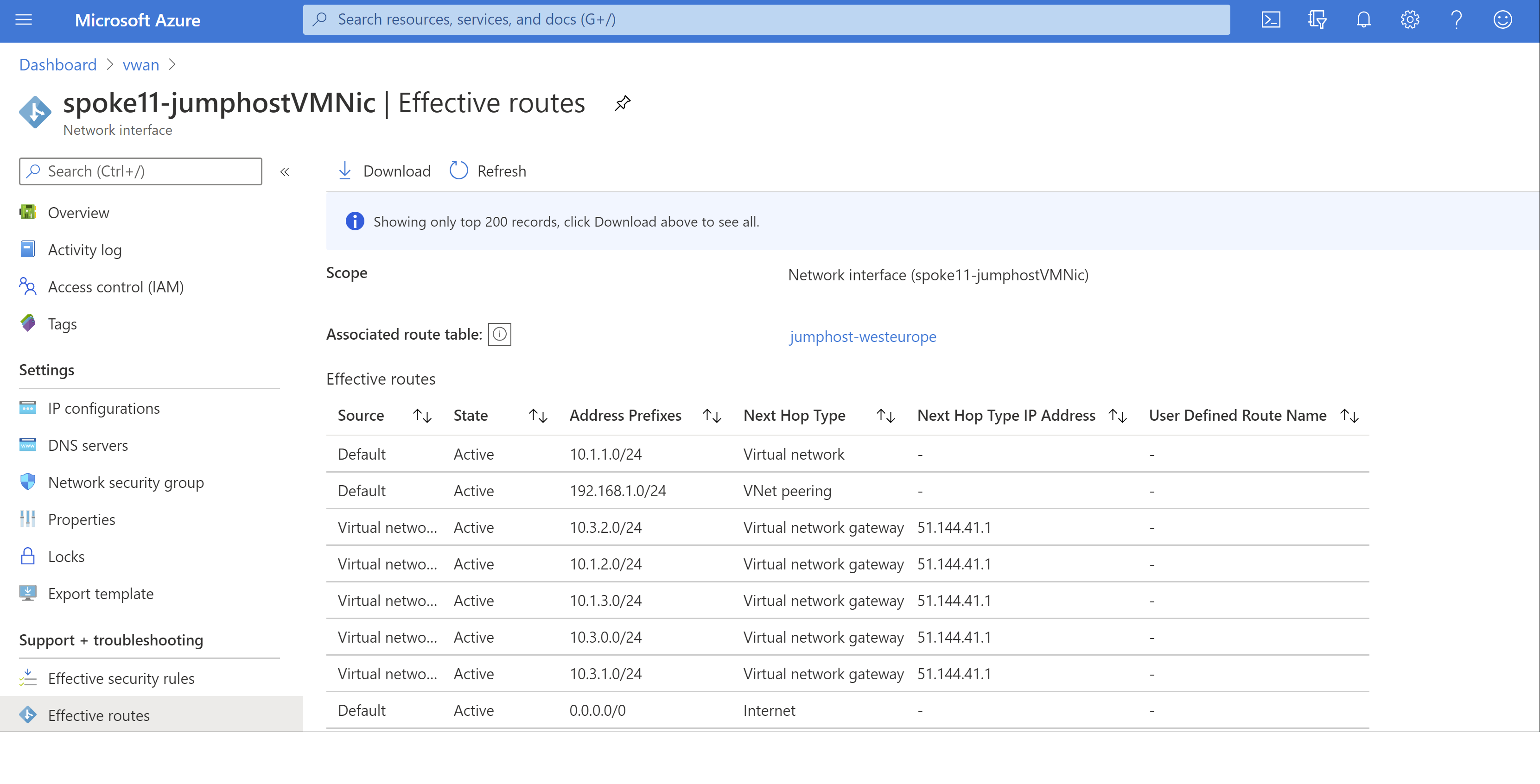
为了再次检查此 VNet (10.1.1.0/24) 是否已连接到配置了专用终结点的原始 VNet (10.1.3.0/24),可以验证 VNet 中任何虚拟机中的有效路由表:
如你所见,有一个路由指向由 Azure 虚拟 WAN 中的虚拟网络网关注入的 VNet 10.1.3.0/24。 现在,我们终于可以测试与数据库的连接了:
query="SELECT CONVERT(char(15), CONNECTIONPROPERTY('client_net_address'));"
sqlcmd -S wantest.database.chinacloudapi.cn -U $username -P $password -Q "$query"
10.1.1.75
在此示例中,我们已了解如何在附加到虚拟 WAN 的一个 VNet 中创建专用终结点,从而提供与虚拟 WAN 中其余 VNet 和分支的连接。
后续步骤
有关虚拟 WAN 的详细信息,请参阅常见问题解答。