本文帮助了解如何利用 S2S VPN 连接的 IPsec/IKE 策略将基于路由的 Azure VPN 网关配置为连接到多个基于策略的本地 VPN 设备。 本文中的其他步骤使用 Azure PowerShell。
关于基于策略的 VPN 网关和基于路由的 VPN 网关
基于策略与基于路由的 VPN 设备的差异体现在如何在连接上设置 IPsec 流量选择器:
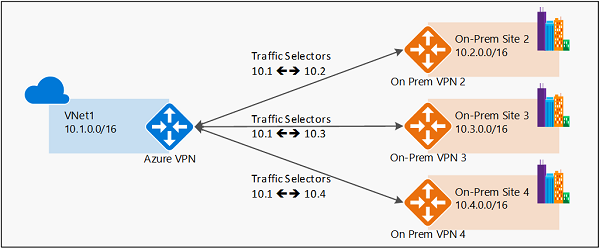
- 基于策略的 VPN 设备使用两个网络的前缀组合来定义如何通过 IPsec 隧道加密/解密流量。 它通常基于执行数据包筛选的防火墙设备。 IPsec 隧道加密和解密将添加到数据包筛选及处理引擎。
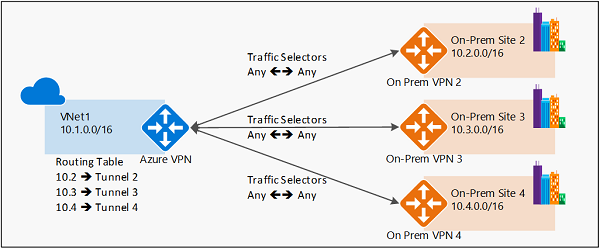
- 基于路由的 VPN 设备使用任意到任意(通配)流量选择器,允许路由/转发表将流量定向到不同的 IPsec 隧道。 它通常基于路由器平台,在此平台中,每个 IPsec 隧道建模为网络接口或 VTI(虚拟隧道接口)。
下图突出显示了这两种模型:
基于策略的 VPN 示例
基于路由的 VPN 示例
Azure 对基于策略的 VPN 的支持
目前,Azure 支持两种模式的 VPN 网关:基于路由的 VPN 网关和基于策略的 VPN 网关。 它们基于不同的内部平台,因而规格也不同。 有关网关、吞吐量和连接的详细信息,请参阅关于 VPN 网关设置。
| 网关 VPN 类型 | 网关 SKU | 支持的 IKE 版本 |
|---|---|---|
| 基于策略的网关 | 基本 | IKEv1 |
| 基于路由的网关 | 基本 | IKEv2 |
| 基于路由的网关 | VpnGw1, VpnGw2, VpnGw3, VpnGw4, VpnGw5 | IKEv1 和 IKEv2 |
| 基于路由的网关 | VpnGw1AZ、VpnGw2AZ、VpnGw3AZ、VpnGw4AZ、VpnGw5AZ | IKEv1 和 IKEv2 |
以前,在使用基于策略的 VPN 时,只能使用基于策略的 VPN 网关基本 SKU,并且只能连接到 1 个本地 VPN/防火墙设备。 现在,使用自定义 IPsec/IKE 策略,可以使用基于路由的 VPN 网关并连接到多个基于策略的 VPN/防火墙设备。 要使用基于路由的 VPN 网关建立基于策略的 VPN 连接,请将基于路由的 VPN 网关配置为使用带有选项“PolicyBasedTrafficSelectors”的基于前缀的流量选择器。
注意事项
若要启用此连接,基于策略的本地 VPN 设备必须支持 IKEv2,才能连接到基于路由的 Azure VPN 网关。 请查看 VPN 设备规格。
通过基于策略的 VPN 设备采用此机制进行连接的本地网络只能连接到 Azure 虚拟网络;不能经由相同的 Azure VPN 网关传输到其他本地网络或虚拟网络。
配置选项是自定义 IPsec/IKE 连接策略的一部分。 如果启用基于策略的流量选择器选项,则必须指定完整的策略(IPsec/IKE 加密和完整性算法、密钥强度和 SA 生存期)。
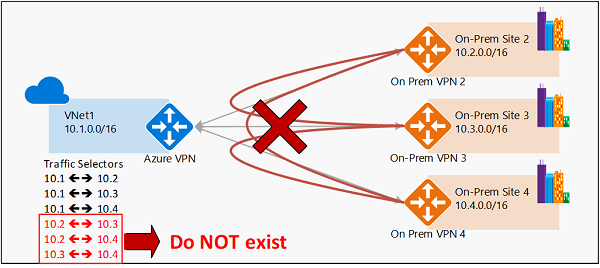
下图展示了经由 VPN 网关的传输路由为何无法适用于基于策略的选项:
如图所示,针对每个本地网络前缀,Azure VPN 网关都有来自虚拟网络的流量选择器,而交叉连接前缀却没有。 例如,本地站点 2、站点 3 和站点 4 可以分别与 VNet1 通信,但不能经由 Azure VPN 网关相互连接。 该图显示若采用此配置,交叉连接流量选择器在 Azure VPN 网关中不可用。
Workflow
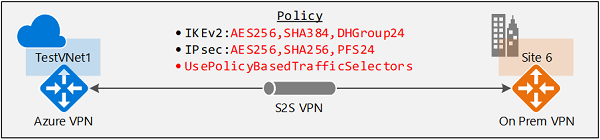
本文中的说明采用为 S2S 或 VNet 到 VNet 的连接配置 IPsec/IKE 策略中所述的示例,建立 S2S VPN 连接。 下图显示了此特点:
要启用连接,请使用以下工作流:
- 为跨界连接创建虚拟网络、VPN 网关和本地网关。
- 创建 IPsec/IKE 策略。
- 创建 S2S 或 VNet 到 VNet 连接时应用该策略,并在连接上启用基于策略的流量选择器。
- 如果已创建连接,则可以在现有连接上应用或更新策略。
启用基于策略的流量选择器
此部分介绍如何在连接上启用基于策略的流量选择器。 确保已通读“配置 IPsec/IKE 策略”一文的第 3 部分。 本文中的步骤使用相同的参数。
创建虚拟网络、VPN 网关和本地网关
连接到订阅 使用 Connect-AzAccount -Environment AzureChinaCloud cmdlet 登录。
声明变量。 在本练习中,我们使用以下变量:
$Sub1 = "<YourSubscriptionName>" $RG1 = "TestPolicyRG1" $Location1 = "China North" $VNetName1 = "TestVNet1" $FESubName1 = "FrontEnd" $BESubName1 = "Backend" $GWSubName1 = "GatewaySubnet" $VNetPrefix11 = "10.11.0.0/16" $VNetPrefix12 = "10.12.0.0/16" $FESubPrefix1 = "10.11.0.0/24" $BESubPrefix1 = "10.12.0.0/24" $GWSubPrefix1 = "10.12.255.0/27" $GWName1 = "VNet1GW" $GW1IPName1 = "VNet1GWIP1" $GW1IPconf1 = "gw1ipconf1" $Connection16 = "VNet1toSite6" $LNGName6 = "Site6" $LNGPrefix61 = "10.61.0.0/16" $LNGPrefix62 = "10.62.0.0/16" $LNGIP6 = "131.107.72.22"创建资源组。
New-AzResourceGroup -Name $RG1 -Location $Location1使用以下示例创建具有三个子网的虚拟网络 TestVNet1 和 VPN 网关。 如果想替换值,务必始终将网关子网特意命名为“GatewaySubnet”。 如果命名为其他名称,网关创建会失败。
$fesub1 = New-AzVirtualNetworkSubnetConfig -Name $FESubName1 -AddressPrefix $FESubPrefix1 $besub1 = New-AzVirtualNetworkSubnetConfig -Name $BESubName1 -AddressPrefix $BESubPrefix1 $gwsub1 = New-AzVirtualNetworkSubnetConfig -Name $GWSubName1 -AddressPrefix $GWSubPrefix1 New-AzVirtualNetwork -Name $VNetName1 -ResourceGroupName $RG1 -Location $Location1 -AddressPrefix $VNetPrefix11,$VNetPrefix12 -Subnet $fesub1,$besub1,$gwsub1 $gw1pip1 = New-AzPublicIpAddress -Name $GW1IPName1 -ResourceGroupName $RG1 -Location $Location1 -AllocationMethod Dynamic $vnet1 = Get-AzVirtualNetwork -Name $VNetName1 -ResourceGroupName $RG1 $subnet1 = Get-AzVirtualNetworkSubnetConfig -Name "GatewaySubnet" -VirtualNetwork $vnet1 $gw1ipconf1 = New-AzVirtualNetworkGatewayIpConfig -Name $GW1IPconf1 -Subnet $subnet1 -PublicIpAddress $gw1pip1 New-AzVirtualNetworkGateway -Name $GWName1 -ResourceGroupName $RG1 -Location $Location1 -IpConfigurations $gw1ipconf1 -GatewayType Vpn -VpnType RouteBased -GatewaySku VpnGw1 New-AzLocalNetworkGateway -Name $LNGName6 -ResourceGroupName $RG1 -Location $Location1 -GatewayIpAddress $LNGIP6 -AddressPrefix $LNGPrefix61,$LNGPrefix62
创建采用 IPsec/IKE 策略的 S2S VPN 连接
创建 IPsec/IKE 策略。
重要
需创建 IPsec/IKE 策略,才能对连接启用“UsePolicyBasedTrafficSelectors”选项。
下面的示例使用以下算法和参数创建 IPsec/IKE 策略:
- IKEv2:AES256、SHA384、DHGroup24
- IPsec:AES256、SHA256、PFS 无、SA 生存期 14400 秒和 102400000KB
$ipsecpolicy6 = New-AzIpsecPolicy -IkeEncryption AES256 -IkeIntegrity SHA384 -DhGroup DHGroup24 -IpsecEncryption AES256 -IpsecIntegrity SHA256 -PfsGroup None -SALifeTimeSeconds 14400 -SADataSizeKilobytes 102400000使用基于策略的流量选择器和 IPsec/IKE 策略创建 S2S VPN 连接,并应用在上一步创建的 IPsec/IKE 策略。 请注意其他参数“-UsePolicyBasedTrafficSelectors $True”可对连接启用基于策略的流量选择器。
$vnet1gw = Get-AzVirtualNetworkGateway -Name $GWName1 -ResourceGroupName $RG1 $lng6 = Get-AzLocalNetworkGateway -Name $LNGName6 -ResourceGroupName $RG1 New-AzVirtualNetworkGatewayConnection -Name $Connection16 -ResourceGroupName $RG1 -VirtualNetworkGateway1 $vnet1gw -LocalNetworkGateway2 $lng6 -Location $Location1 -ConnectionType IPsec -UsePolicyBasedTrafficSelectors $True -IpsecPolicies $ipsecpolicy6 -SharedKey 'AzureA1b2C3'完成这些步骤后,S2S VPN 连接将使用定义的 IPsec/IKE 策略,并对连接启用基于策略的流量选择器。 可重复这些步骤,从同一 Azure VPN 网关添加更多连接到其他基于策略的本地 VPN 设备。
更新基于策略的流量选择器
此部分介绍如何对现有 S2S VPN 连接更新基于策略的流量选择器选项。
获取连接资源。
$RG1 = "TestPolicyRG1" $Connection16 = "VNet1toSite6" $connection6 = Get-AzVirtualNetworkGatewayConnection -Name $Connection16 -ResourceGroupName $RG1查看基于策略的流量选择器选项。 以下行显示连接是否使用了基于策略的流量选择器:
$connection6.UsePolicyBasedTrafficSelectors如果行返回“True”,则表示对连接配置了基于策略的流量选择器;否则返回“False”。
获取连接资源后,可以启用或禁用连接上基于策略的流量选择器。
启用
下面的示例启用了基于策略的流量选择器选项,但未改变 IPsec/IKE 策略:
$RG1 = "TestPolicyRG1" $Connection16 = "VNet1toSite6" $connection6 = Get-AzVirtualNetworkGatewayConnection -Name $Connection16 -ResourceGroupName $RG1 Set-AzVirtualNetworkGatewayConnection -VirtualNetworkGatewayConnection $connection6 -UsePolicyBasedTrafficSelectors $True禁用
下面的示例禁用了基于策略的流量选择器选项,但未改变 IPsec/IKE 策略:
$RG1 = "TestPolicyRG1" $Connection16 = "VNet1toSite6" $connection6 = Get-AzVirtualNetworkGatewayConnection -Name $Connection16 -ResourceGroupName $RG1 Set-AzVirtualNetworkGatewayConnection -VirtualNetworkGatewayConnection $connection6 -UsePolicyBasedTrafficSelectors $False
后续步骤
连接完成后,即可将虚拟机添加到虚拟网络。 请参阅 创建虚拟机 以获取相关步骤。
有关自定义 IPsec/IKE 策略的详细信息,请参阅为 S2S VPN 或 VNet 到 VNet 的连接配置 IPsec/IKE 策略。