Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
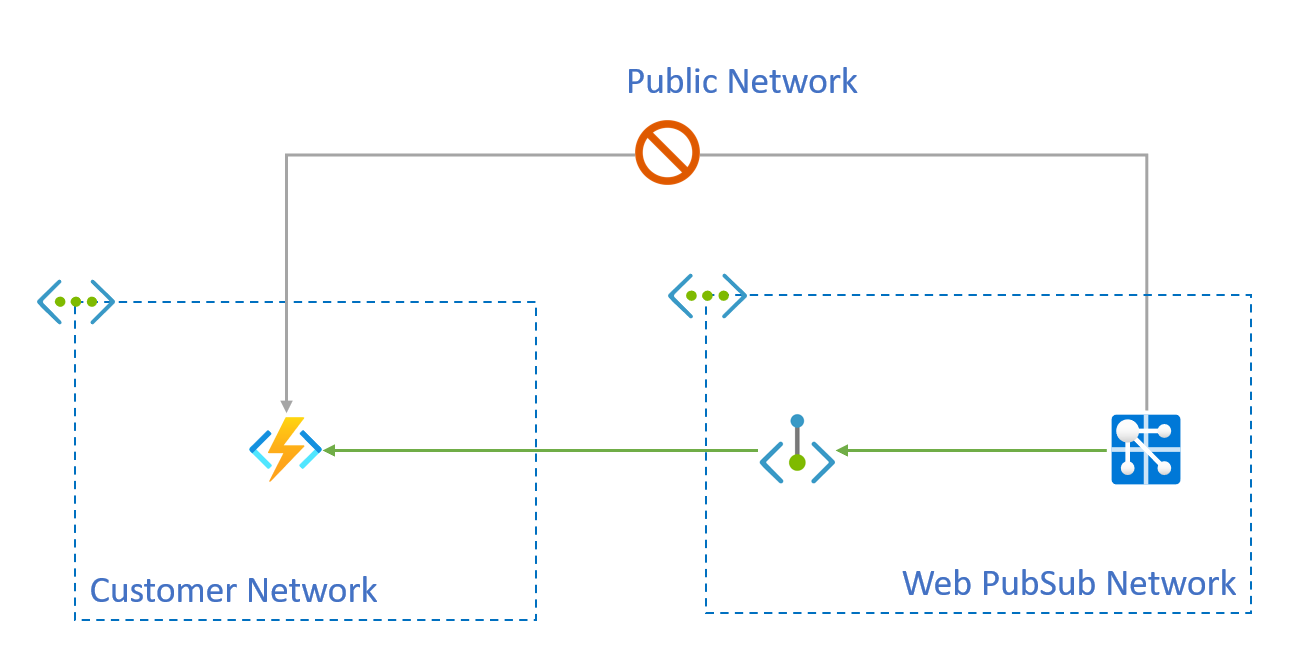
If you're using an event handler in Azure Web PubSub, you might have outbound traffic to upstream endpoints backed by Azure Web Apps or Azure Functions. To secure such outbound traffic, you can create an outbound private endpoint connection in your Web PubSub services to reach these endpoints in a private way.
This article shows you how to configure your Web PubSub resource to send event handler traffic to Azure Functions privately instead of through a public network.
This outbound method is subject to the following requirements:
- The upstream endpoint must be deployed by using Azure App Service or Azure Functions.
- The Web PubSub resource must be on the Standard tier or the Premium tier.
- An Azure App Service or an Azure Functions resource must be created by choosing a specific tier to create the resource. For more information, see Use private endpoints for Azure Web App.
Private endpoints of secured resources that are created by using Azure Web PubSub APIs are called shared private link resources. You're "sharing" access to a resource, such as an Azure Functions resource, that is integrated with Azure Private Link. These private endpoints are created inside the Web PubSub service execution environment and aren't directly visible to you.
Prerequisites
- An Azure account with an active subscription. Create a trial subscription.
- An Azure Web PubSub instance.
- An Azure Functions resource.
Note
The examples in this article use the following values:
- The resource ID of this Azure Web PubSub resource is
_/subscriptions//00000000-0000-0000-0000-000000000000/resourceGroups/contoso/providers/Microsoft.SignalRService/webPubSub/contoso-webpubsub. - The resource ID of the Azure Functions network resource is
_/subscriptions//00000000-0000-0000-0000-000000000000/resourceGroups/contoso/providers/Microsoft.Web/sites/contoso-func.
To use the steps in the following examples, replace these values with your own subscription ID, the name of your Web PubSub resource, and the name of your Azure Functions resource.
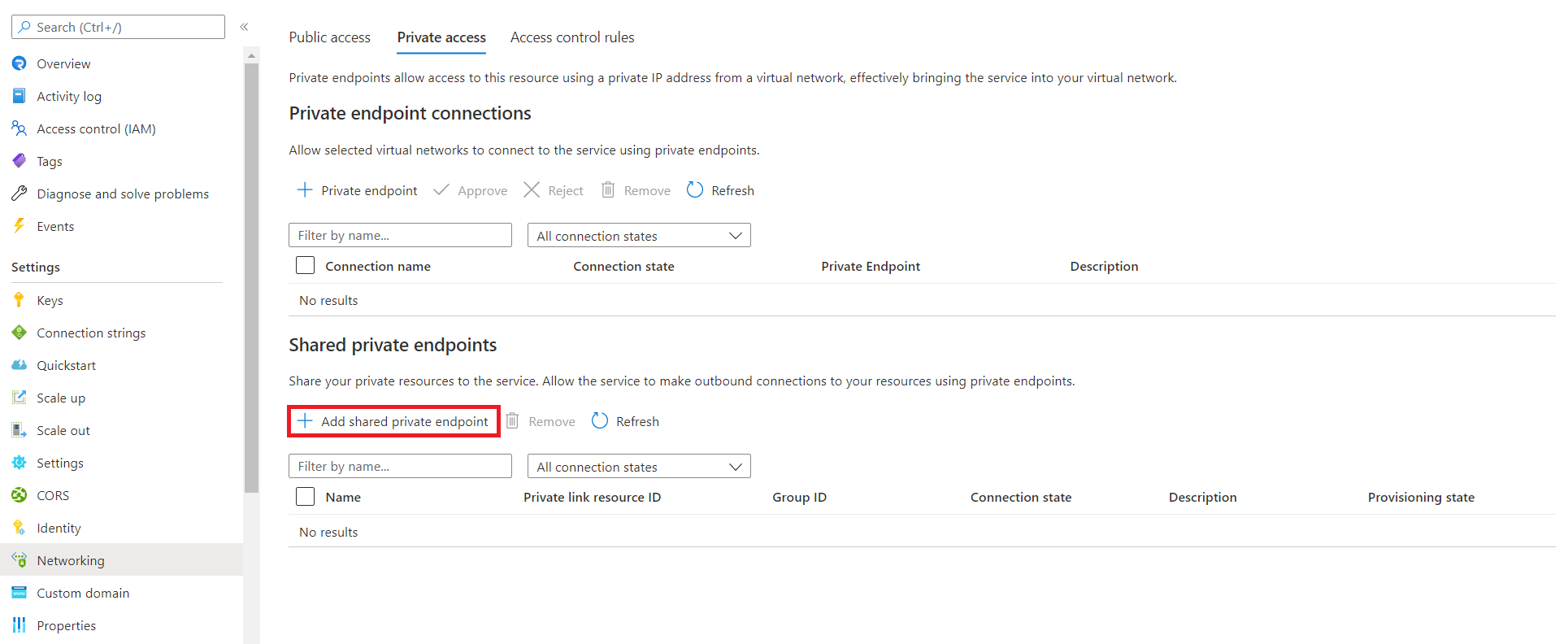
Create a shared private link resource to a function
In the Azure portal, go to your Azure Web PubSub resource.
On the left menu, select Networking.
Select Private access.
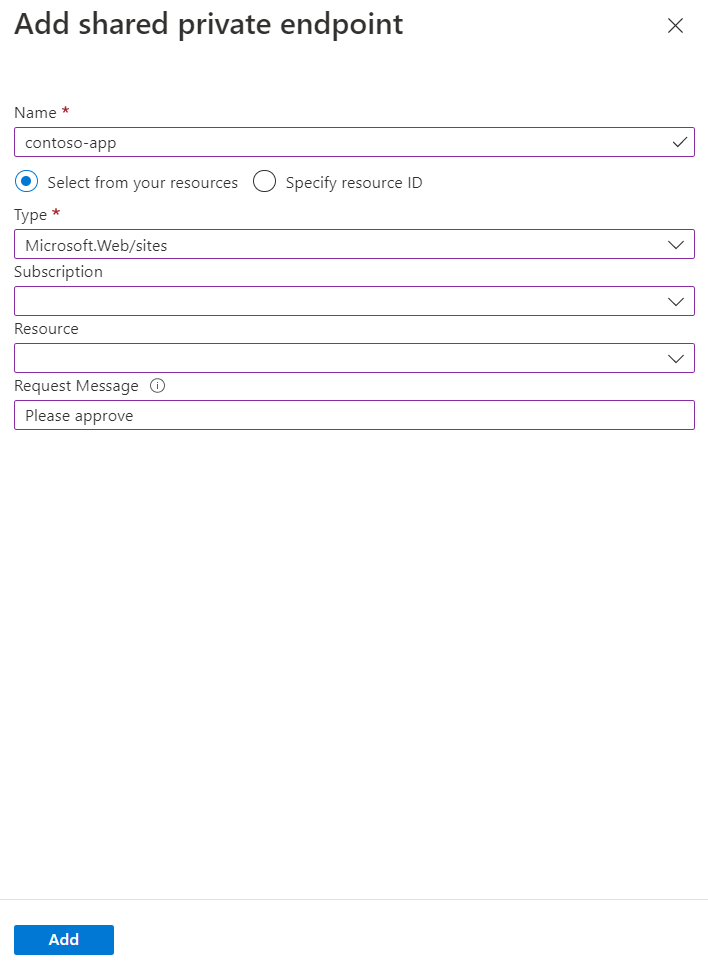
Select Add shared private endpoint.
Enter a name for the shared private endpoint.
To set your target linked sources, either choose Select from your resources or enter your resource ID in Specify resource ID.
Optionally, you can enter text in Request message to send a request to the target resource owner.
Select Add.
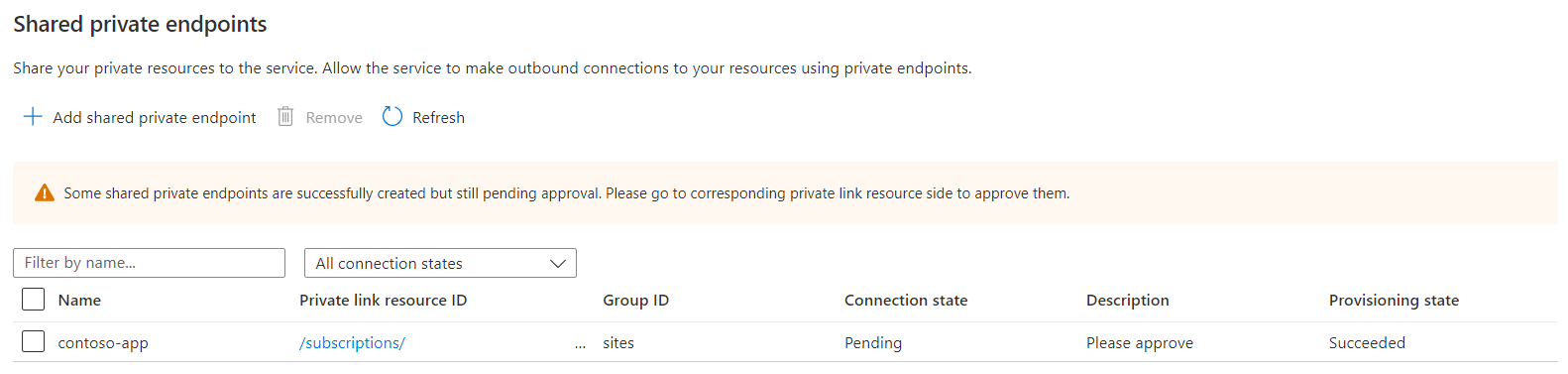
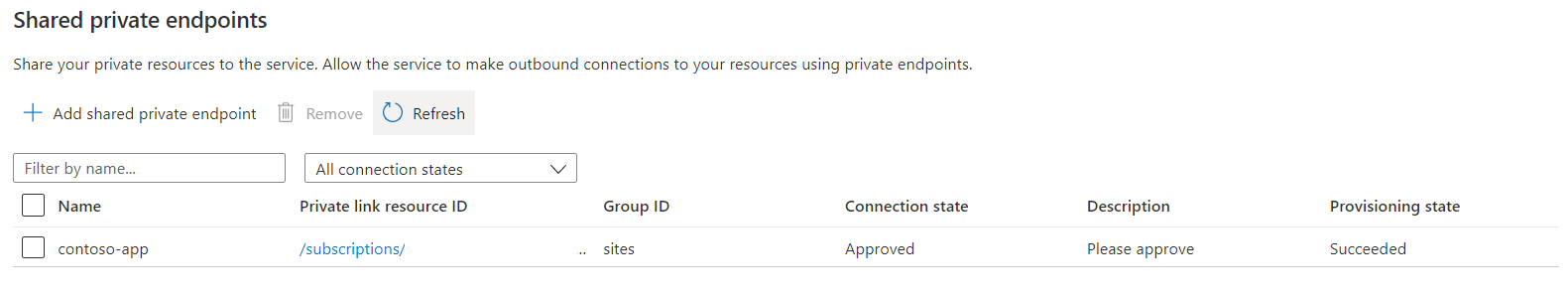
The value for Provisioning state in the shared private endpoint resource is Succeeded. Connection state is Pending until the endpoint is approved at the target resource.
Approve the private endpoint connection for the function
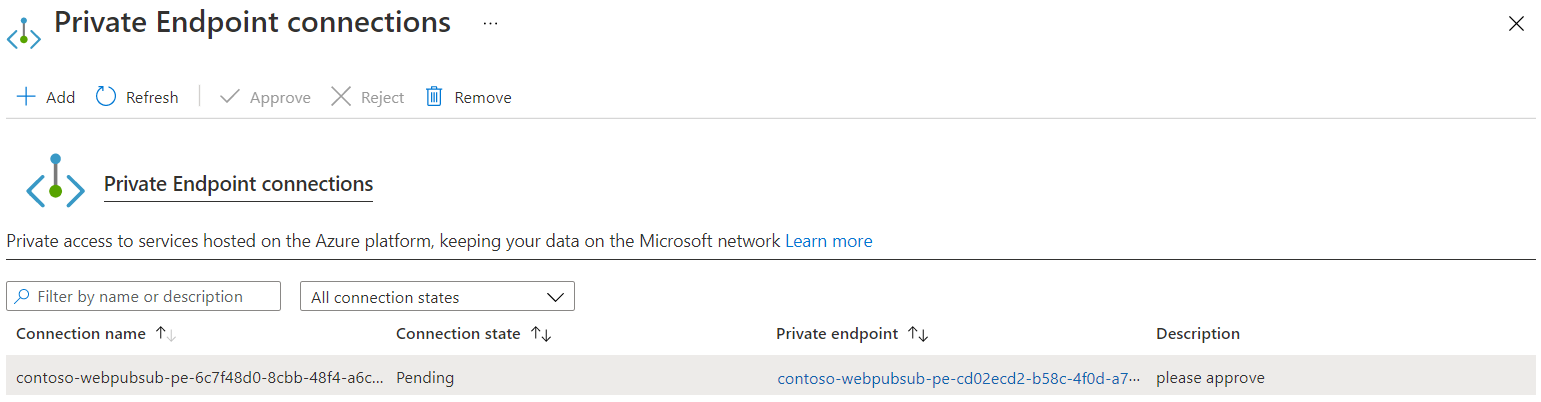
When the shared private endpoint connection has a Pending status, the connection request must be approved at the target resource.
Important
After the private endpoint connection is approved, the function is no longer accessible from a public network. You might need to create other private endpoints in your own virtual network to access the function endpoint.
- In the Azure portal, go to your Azure Functions app.
- On the left menu, select Networking.
- Under Inbound Traffic, select Private endpoints.
- Select the pending connection that you created in your Web PubSub resource.
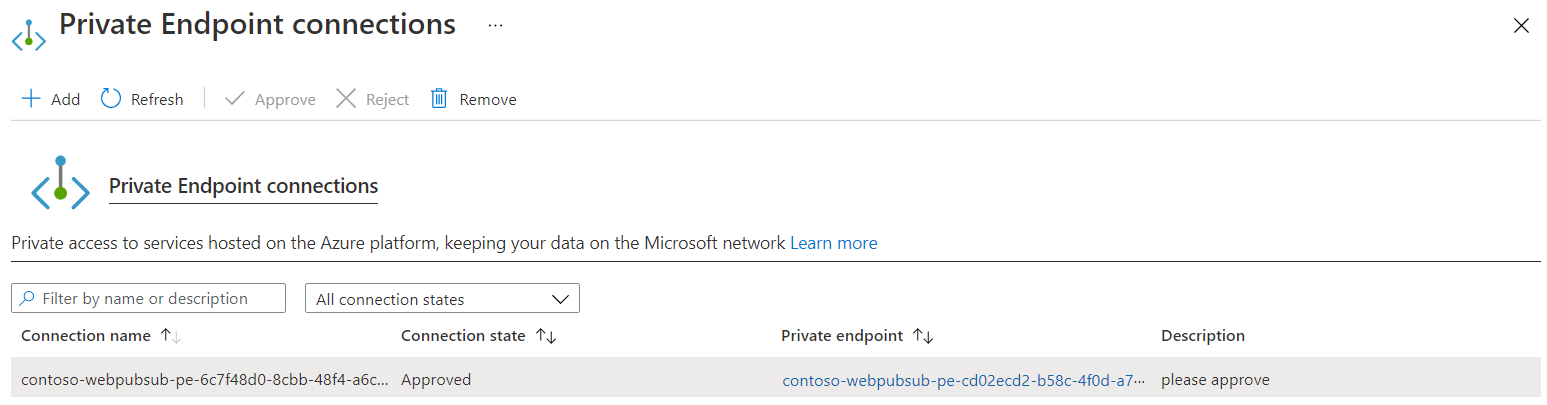
- Select Approve, and then select Yes to confirm.
You can select Refresh to check the status. It might take a few minutes for the status Connection state to update to Approved.
Query the status of the shared private link resource
It takes a few minutes for the approval to be reflected in Web PubSub. You can check the state by using either the Azure portal or the Azure CLI.
At this point, the private endpoint between Azure Web PubSub and Azure Functions is established.
Verify that upstream calls are from a private IP address
When the private endpoint is set up, you can verify that incoming calls are from a private IP address by checking the X-Forwarded-For header for upstream calls.