Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
You can use service tags to identify Azure Web PubSub traffic. A service tag represents a group of IP address prefixes. Web PubSub manages a service tag called AzureWebPubSub for both inbound and outbound traffic.
You can use a service tag to configure a network security group. Or, you can query the IP address prefixes by using the Service Tag Discovery API.
Outbound traffic
Endpoints of Web PubSub resources are guaranteed to be within IP ranges of the service tag AzureWebPubSub.
Access Web PubSub resources from a virtual network
You can allow outbound traffic from your network to Web PubSub by adding a new outbound network security rule.
In the portal, go to the network security group.
On the left menu, select Outbound security rules.
Select Add.
Select Destination, and then select Service Tag.
Select Destination service tag, and then select AzureWebPubSub.
For Destination port ranges, enter 443.
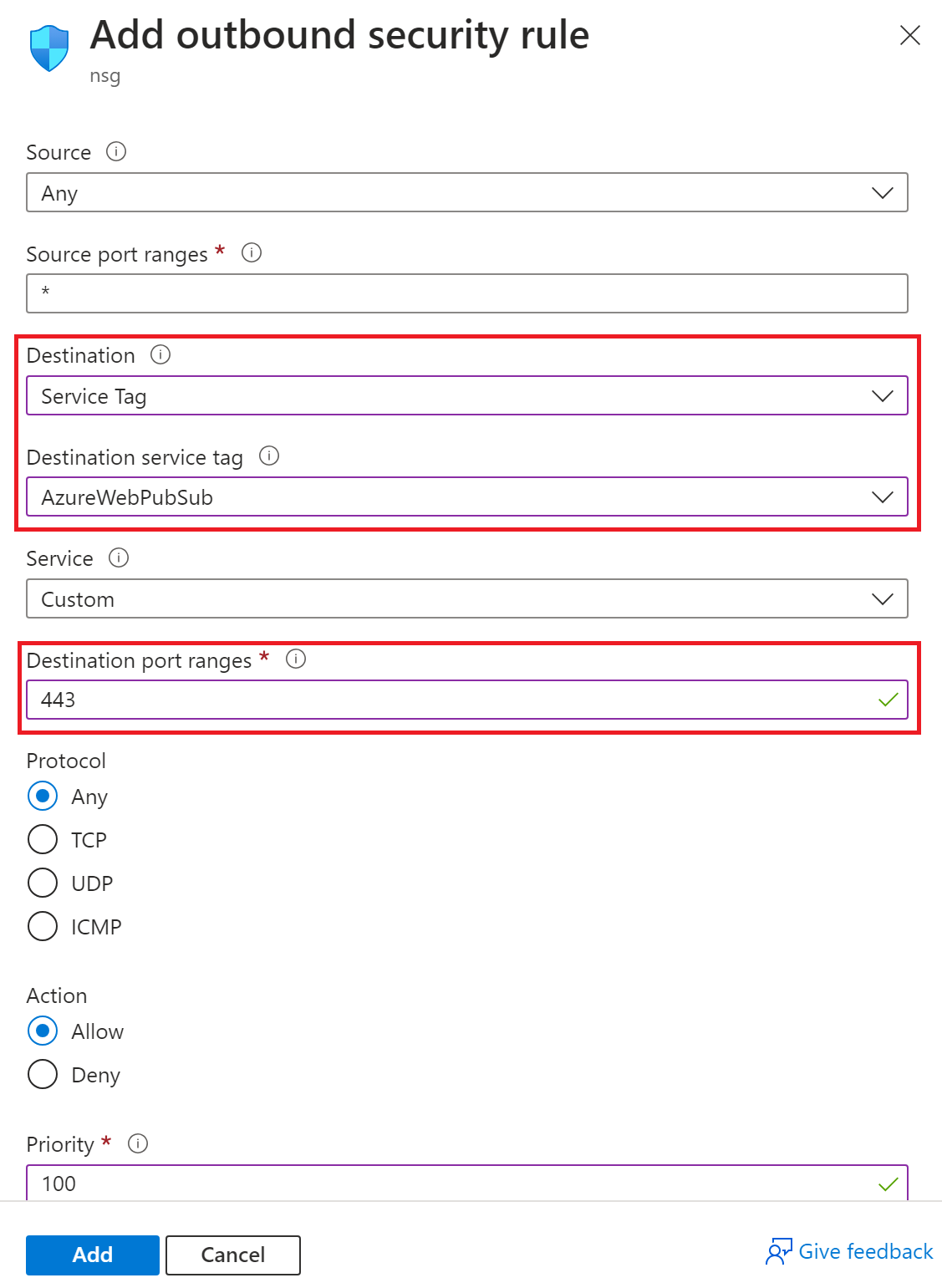
Update other fields as needed, and then select Add.
Inbound traffic
Azure Web PubSub can generate network traffic to your resource by using service tags. The source of traffic is guaranteed to be within IP ranges that are defined by the AzureWebPubSub service tag.
You can use service tags to control access to your Web PubSub resource if you:
- Use event handlers.
- Use event listeners.
- Use a Key Vault secret reference in
Event handler endpoints in a virtual network
You can configure a network security group to allow inbound traffic to a virtual network.
In the Azure portal, go to the network security group.
On the left menu, select Inbound security rules.
Select Add.
Select Source, and then select Service Tag.
Select Source service tag, and then select AzureWebPubSub.
For Source port ranges, enter *.
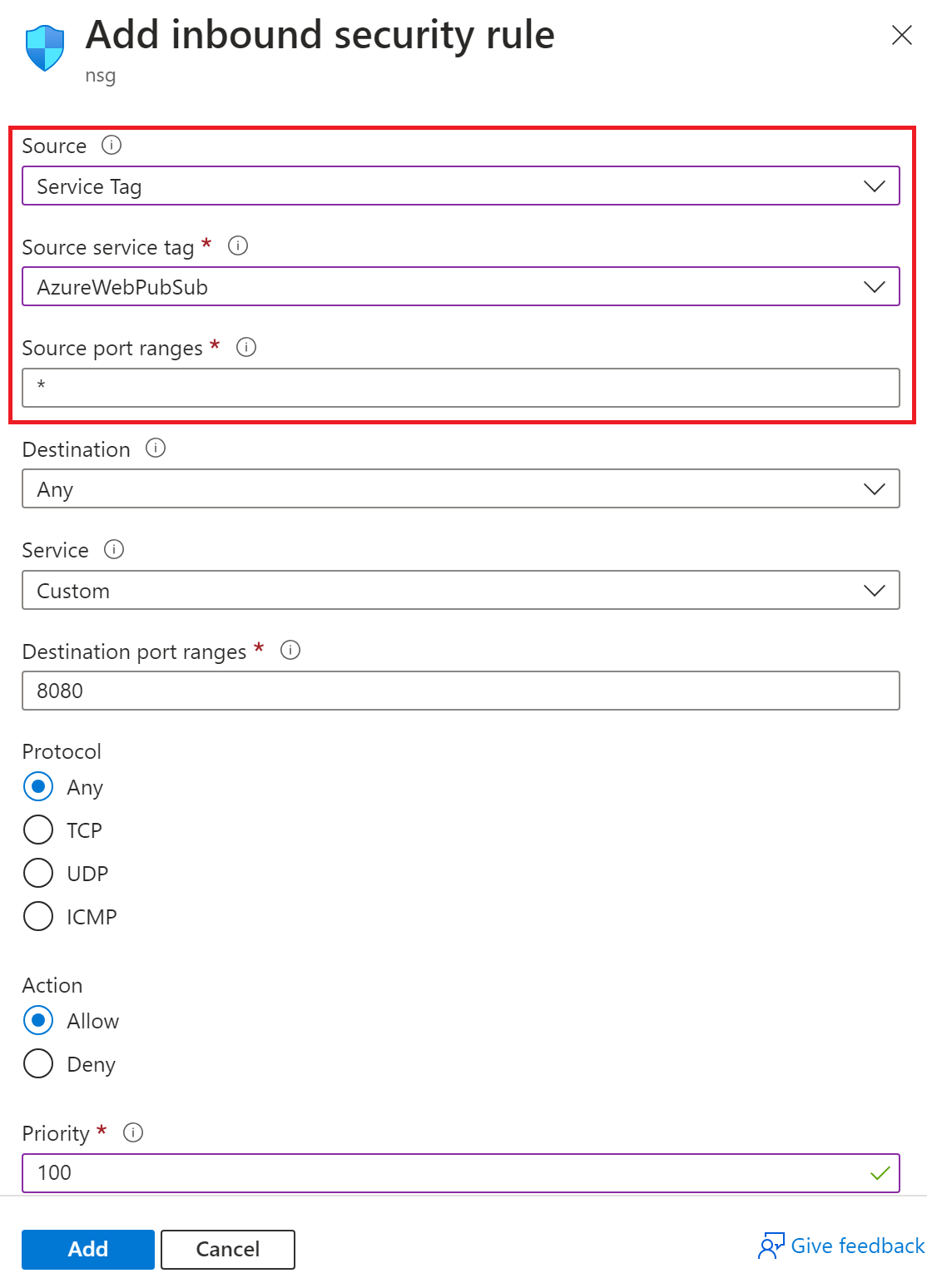
Update other settings as needed.
Select Add.
Note
Azure Web PubSub is a shared service. By allowing the AzureWebPubSub service tag or its associated IP address prefixes, you also allow traffic from other resources, even if they belong to other customers. Make sure that you implement appropriate authentication on your endpoints.
Event handler endpoints for Azure Functions
For an Azure Functions app, you can use a service tag-based rule to manage event handler endpoints securely.
Alternatively, you can use shared private endpoints for increased security. Shared private endpoints are dedicated to your resources. No traffic from other resources can access your endpoints.
Azure Event Hubs and Azure Key Vault access
For Azure Event Hubs and Azure Key Vault resources, we recommend that you use shared private endpoints to help you maintain the highest level of security.