Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Azure Data Explorer clusters are designed to be accessible using public URLs. Anyone with valid identity on a cluster can access it from any location. As an organization, securing data may be one your highest priority tasks. As such, you may want to limit and secure access to your cluster, or even only allow access to your cluster through your private virtual network. To achieve this goal, use:
The following section explains how to secure your cluster using private endpoints.
Private endpoint
A private endpoint is a network interface that uses private IP addresses from your virtual network. This network interface connects you privately and securely to your cluster powered by Azure Private Link. By enabling a private endpoint, you're bringing the service into your virtual network.
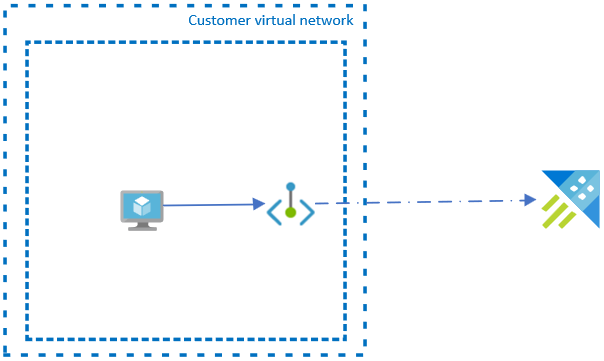
To successfully deploy your cluster into a private endpoint, you only require a set of private IP addresses.
Network security features with private endpoints
The following table shows how network security related features can be implemented using a private endpoint:
| Feature | Private endpoint |
|---|---|
| Inbound IP address filtering | Manage public access |
| Transitive access to other services (Storage, Event Hubs, etc.) | Create a managed private endpoint |
| Restricting outbound access | Use Callout policies or the AllowedFQDNList |