Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Use the entitlement management feature to manage the identity and access lifecycle. You can automate access request workflows, access assignments, reviews, and expiration. Delegated non-admins use entitlement management to create access packages that external users, from other organizations, can request access to. One and multistage approval workflows are configurable to evaluate requests, and provision users for time-limited access with recurring reviews. Use entitlement management for policy-based provisioning and deprovisioning of external accounts.
Learn more:
Before you begin
This article is number 6 in a series of 10 articles. We recommend you review the articles in order. Go to the Next steps section to see the entire series.
Enable entitlement management
The following key concepts are important to understand for entitlement management.
Access packages
An access package is the foundation of entitlement management: groupings of policy-governed resources for users to collaborate on a project or do other tasks. For example, an access package might include:
- Access to SharePoint sites
- Enterprise applications, including your custom in-house and software as a service (SaaS) apps, like Salesforce
- Microsoft Teams
- Microsoft 365 Groups
Catalogs
Access packages reside in catalogs. When you want to group related resources and access packages and delegate their management, you create a catalog. First, you add resources to a catalog, and then you can add resources to access packages. For example, you can create a finance catalog, and delegate its management to a member of the finance team. That person can add resources, create access packages, and manage access approval.
Learn more:
- Create and manage a catalog of resources in entitlement management
- Delegation and roles in entitlement management
- Add resources to a catalog
The following diagram shows a typical governance lifecycle of an external user gaining access to an access package, with an expiration.
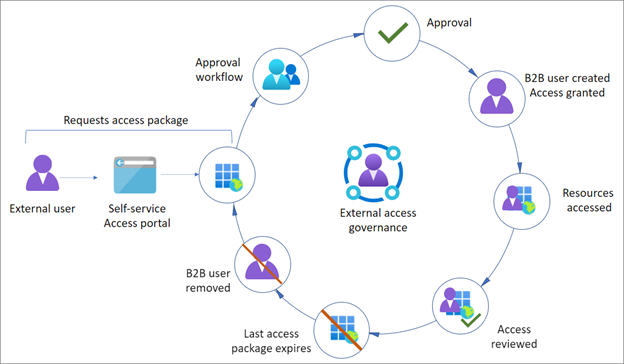
Self-service external access
You can make access packages available, through the Microsoft Entra My Access portal, to enable external users to request access. Policies determine who can request an access package. See, Request access to an access package in entitlement management.
You specify who is allowed to request the access package:
- Connected organizations
- Configured connected organizations
- Users from organizations
- Member or guest users in your tenant
Approvals
Access packages can include mandatory approval for access. Approvals can be single or multistage and are determined by policies. If internal and external users need to access the same package, you can set up access policies for categories of connected organizations, and for internal users.
Important
Implement approval processes for external users.
Expiration
Access packages can include an expiration date or a number of days you set for access. When the access package expires, and access ends, the B2B Guest User object representing the user can be deleted or blocked from signing in. We recommend you enforce expiration on access packages for external users. Not all access packages have expirations.
Important
For packages without expiration, perform regular access reviews.
Access reviews
Access packages can require periodic access reviews, which require the package owner or a designee to attest to the continued need for users' access. See, Manage guest access with access reviews.
Before you set up your review, determine the following criteria:
- Who
- Criteria for continued access
- Reviewers
- How often
- Built-in options are monthly, quarterly, BI-annually, or annually
- We recommend quarterly, or more frequent, reviews for packages that support external access
Important
Access package reviews examine access granted through entitlement management. Set up other processes to review access to external users, outside entitlement management.
Learn more: Plan a Microsoft Entra access reviews deployment.
Using entitlement management automation
- Working with the Microsoft Entra entitlement management API
accessPackageresource type- Microsoft Entra access reviews
connectedOrganizationresource typeentitlementManagementSettingsresource type
External access governance recommendations
Best practices
We recommend the following practices to govern external access with entitlement management.
- For projects with one or more business partners, create and use access packages to onboard and provide access to resources.
- If you have B2B users in your directory, you can assign them to access packages.
- You can assign access in the Azure portal or with Microsoft Graph
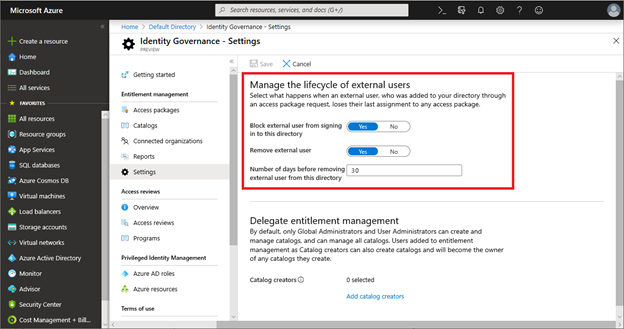
Identity Governance - Settings
Use Identity Governance - Settings to remove users from your directory when their access packages expire. The following settings apply to users onboarded with entitlement management.
Delegate catalog and package management
You can delegate catalog and package management to business owners, who have more information on who should access. See, Delegation and roles in entitlement managements
Enforce access package expiration
You can enforce access expiration for external users. See, Change lifecycle settings for an access package in entitlement management.
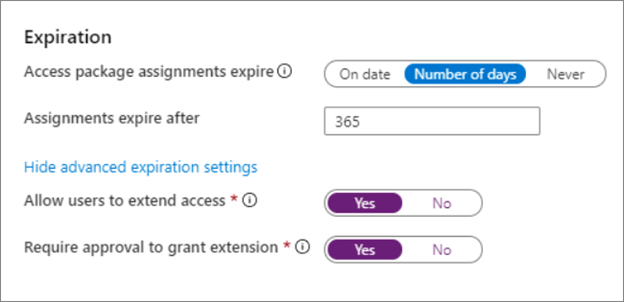
- For the end date of a project-based access package, use On date to set the date.
- Otherwise we recommend expiration to be no longer 365 days, unless it's a multiyear project
- Allow users to extend access
- Require approval to grant the extension
Enforce guest-access package reviews
You can enforce reviews of guest-access packages to avoid inappropriate access for guests. See, Manage guest access with access reviews.
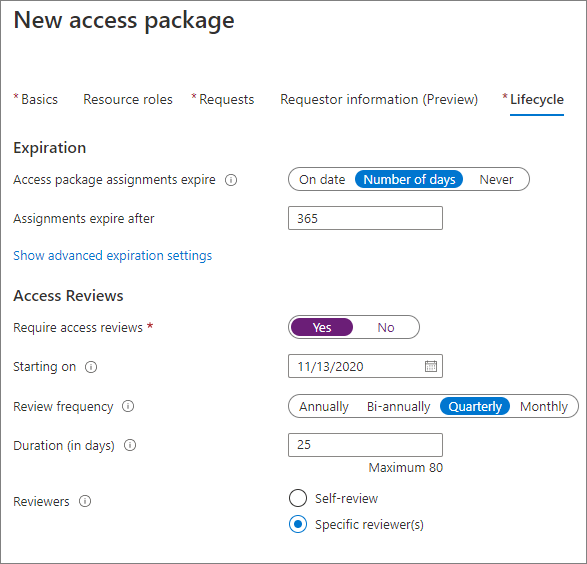
- Enforce quarterly reviews
- For compliance-related projects, set the reviewers to be reviewers, rather than self-review for external users.
- You can use access package managers as reviewers
- For less sensitive projects, users self-reviewing reduces the burden to remove access from users no longer with the organization.
Learn more: Govern access for external users in entitlement management
Next steps
Use the following series of articles to learn about securing external access to resources. We recommend you follow the listed order.
Determine your security posture for external access with Microsoft Entra ID
Discover the current state of external collaboration in your organization
Secure external access with groups in Microsoft Entra ID and Microsoft 365
Transition to governed collaboration with Microsoft Entra B2B collaboration
Manage external access with Microsoft Entra entitlement management (You're here)
Manage external access to resources with Conditional Access policies
Control external access to resources in Microsoft Entra ID with sensitivity labels
Convert local guest accounts to Microsoft Entra B2B guest accounts