Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Important
Attention: All Microsoft Sentinel features will be officially retired in Azure in China regions on August 18, 2026 per the announcement posted by 21Vianet.
Best practice guidance is provided throughout the technical documentation for Microsoft Sentinel. This article highlights some key guidance to use when deploying, managing, and using Microsoft Sentinel.
To get started with Microsoft Sentinel, see the deployment guide, which covers the high level steps to plan, deploy, and fine-tune your Microsoft Sentinel deployment. From that guide, select the provided links to find detailed guidance for each stage in your deployment.
Integrate Microsoft security services
Microsoft Sentinel is empowered by the components that send data to your workspace, and is made stronger through integrations with other Microsoft services. Any logs ingested into products, such as Microsoft Defender for Endpoint, and Microsoft Defender for Identity, allow these services to create detections, and in turn provide those detections to Microsoft Sentinel. Logs can also be ingested directly into Microsoft Sentinel to provide a fuller picture for events and incidents.
More than ingesting alerts and logs from other sources, Microsoft Sentinel also provides:
| Capability | Description |
|---|---|
| Threat detection | Threat detection capabilities with artificial intelligence, allowing you to build and present interactive visuals via workbooks, run playbooks to automatically act on alerts, integrate machine learning models to enhance your security operations, and ingest and fetch enrichment feeds from threat intelligence platforms. |
| Threat investigation | Threat investigation capabilities allowing you to visualize and explore alerts and entities, detect anomalies in user and entity behavior, and monitor real-time events during an investigation. |
| Data collection | Collect data across all users, devices, applications, and infrastructure, both on-premises and in multiple clouds. |
| Threat response | Threat response capabilities, such as playbooks that integrate with Azure services and your existing tools. |
| Partner integrations | Integrates with partner platforms using Microsoft Sentinel data connectors, providing essential services for SOC teams. |
Plan incident management and response process
The following image shows recommended steps in an incident management and response process.
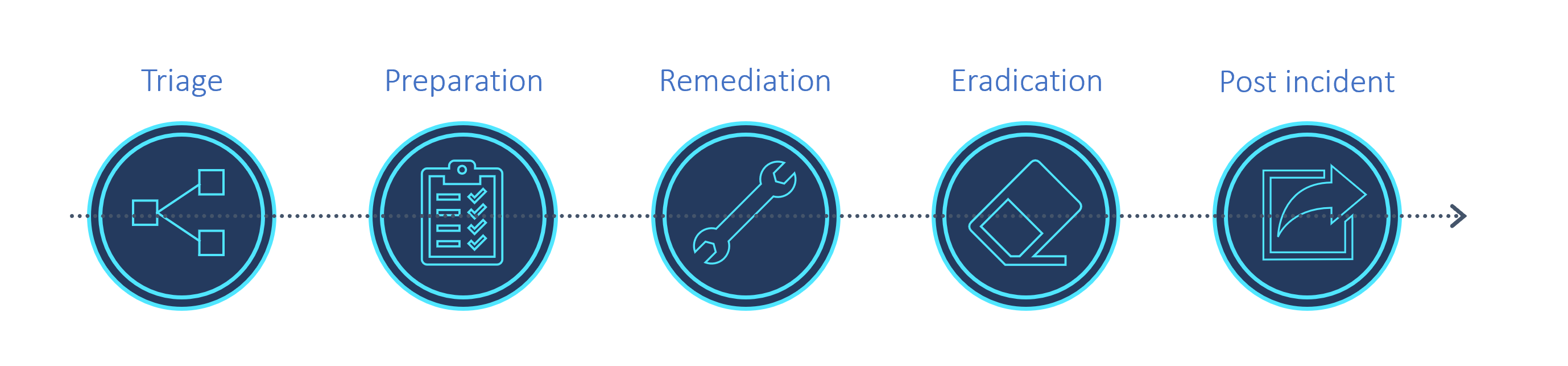
The following table provides high-level incident management and response tasks and related best practices. For more information, see Microsoft Sentinel incident investigation in the Azure portal.
| Task | Best practice |
|---|---|
| Review Incidents page | Review an incident on the Incidents page, which lists the title, severity, and related alerts, logs, and any entities of interest. You can also jump from incidents into collected logs and any tools related to the incident. |
| Use Incident graph | Review the Incident graph for an incident to see the full scope of an attack. You can then construct a timeline of events and discover the extent of a threat chain. |
| Review incidents for false positives | Use data about key entities, such as accounts, URLs, IP address, host names, activities, timeline to understand whether you have a false positive on hand, in which case you can close the incident directly. If you discover that the incident is a true positive, take action directly from the Incidents page to investigate logs, entities, and explore the threat chain. After you identified the threat and created a plan of action, use other tools in Microsoft Sentinel and other Microsoft security services to continue investigating. |
| Visualize information | Take a look at the Microsoft Sentinel overview dashboard to get an idea of the security posture of your organization. In addition to information and trends on the Microsoft Sentinel overview page, workbooks are valuable investigative tools. For example, use the Investigation Insights workbook to investigate specific incidents together with any associated entities and alerts. This workbook enables you to dive deeper into entities by showing related logs, actions, and alerts. |
| Hunt for threats | While investigating and searching for root causes, run built-in threat hunting queries and check results for any indicators of compromise. For more information, see Threat hunting in Microsoft Sentinel. |
| Use livestream | During an investigation, or after having taken steps to remediate and eradicate the threat, use livestream. Livestream allows you to monitor, in real time, whether there are any lingering malicious events, or if malicious events are still continuing. |
| Entity behavior | Entity behavior in Microsoft Sentinel allows users to review and investigate actions and alerts for specific entities, such as investigating accounts and host names. For more information, see: - Enable User and Entity Behavior Analytics (UEBA) in Microsoft Sentinel - Investigate incidents with UEBA data - Microsoft Sentinel UEBA enrichments reference |
| Watchlists | Use a watchlist that combines data from ingested data and external sources, such as enrichment data. For example, create lists of IP address ranges used by your organization or recently terminated employees. Use watchlists with playbooks to gather enrichment data, such as adding malicious IP addresses to watchlists to use during detection, threat hunting, and investigations. During an incident, use watchlists to contain investigation data, and then delete them when your investigation is done to ensure that sensitive data doesn't remain in view. For more information, see Watchlists in Microsoft Sentinel. |
Optimize data collection and ingestion
Review the Microsoft Sentinel data collection best practices, which include prioritizing data connectors, filtering logs, and optimizing data ingestion.
Make your Kusto Query Language queries faster
Review the Kusto Query Language best practices to make queries faster.